💥💥💞💞欢迎来到本博客❤️❤️💥💥
*🏆博主优势:🌞🌞🌞*博客内容尽量做到思维缜密,逻辑清晰,为了方便读者。
⛳️座右铭:行百里者,半于九十。
📋📋📋本文目录如下:🎁🎁🎁
💥1 概述
文章来源:

本文介绍并演示了对 Kirchhoff-Law-Johnson-Noise(KLJN)安全密钥交换方案的四种新的统计攻击。这些攻击利用了在Alice/Bob站点的受损随机数生成器。探讨了Alice/Bob以及Eve探测噪声之间的部分相关性情况,也就是说,Eve对Alice和Bob的噪声的了解是受限的但不为零。我们探讨了Eve部分了解Alice和Bob随机数生成器的双边情况。结果表明,在这种情况下,Eve可以利用她的探测噪声和导线中测量的电压噪声之间的最高互相关来破解安全密钥比特。她还可以通过她的噪声电压和她评估的Alice/Bob噪声电压之间的最高互相关来破解安全密钥比特。然后我们探讨了Eve只对Alice的随机数生成器有部分了解的单边情况,因此只有Alice和Eve的噪声相关。在这种情况下,Eve仍然可以破解安全密钥比特,但是为了获得足够低的错误概率,她需要利用整个比特交换周期进行攻击。与其他协议类似,KLJN密钥交换方案的安全性要求随机数生成器的输出对Eve来说是真正随机的。
本文介绍并演示了针对基尔霍夫-洛-约翰逊噪声(KLJN)安全密钥交换方案的两种新攻击。这些攻击基于安全性受损的随机数生成器。首先,我们探讨了Eve知晓Alice和Bob随机数生成器的种子的情况。我们展示了在这种情况下,即使她的电流和电压测量只有单比特分辨率,Eve也能在比特交换周期的一小部分时间内破解安全密钥比特。在第二次攻击中,我们探讨了Eve只知道Alice随机数生成器种子的情况。我们展示了在这种情况下,Eve仍然可以破解安全密钥比特,但她需要利用整个比特交换周期进行攻击。详细文章见第4部分。
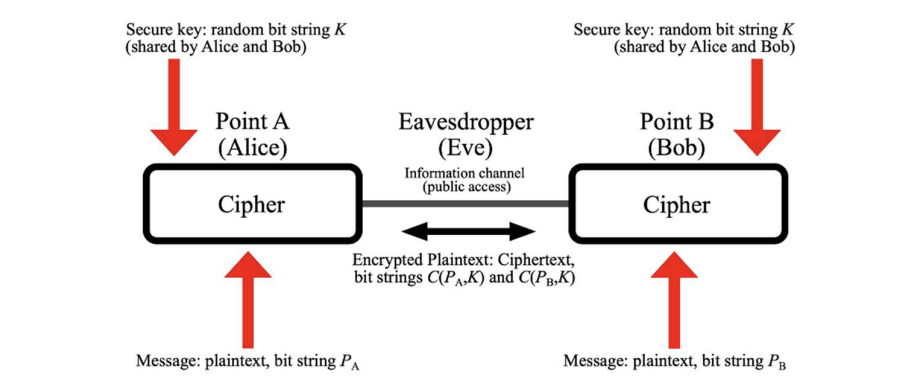

📚****2 运行结果
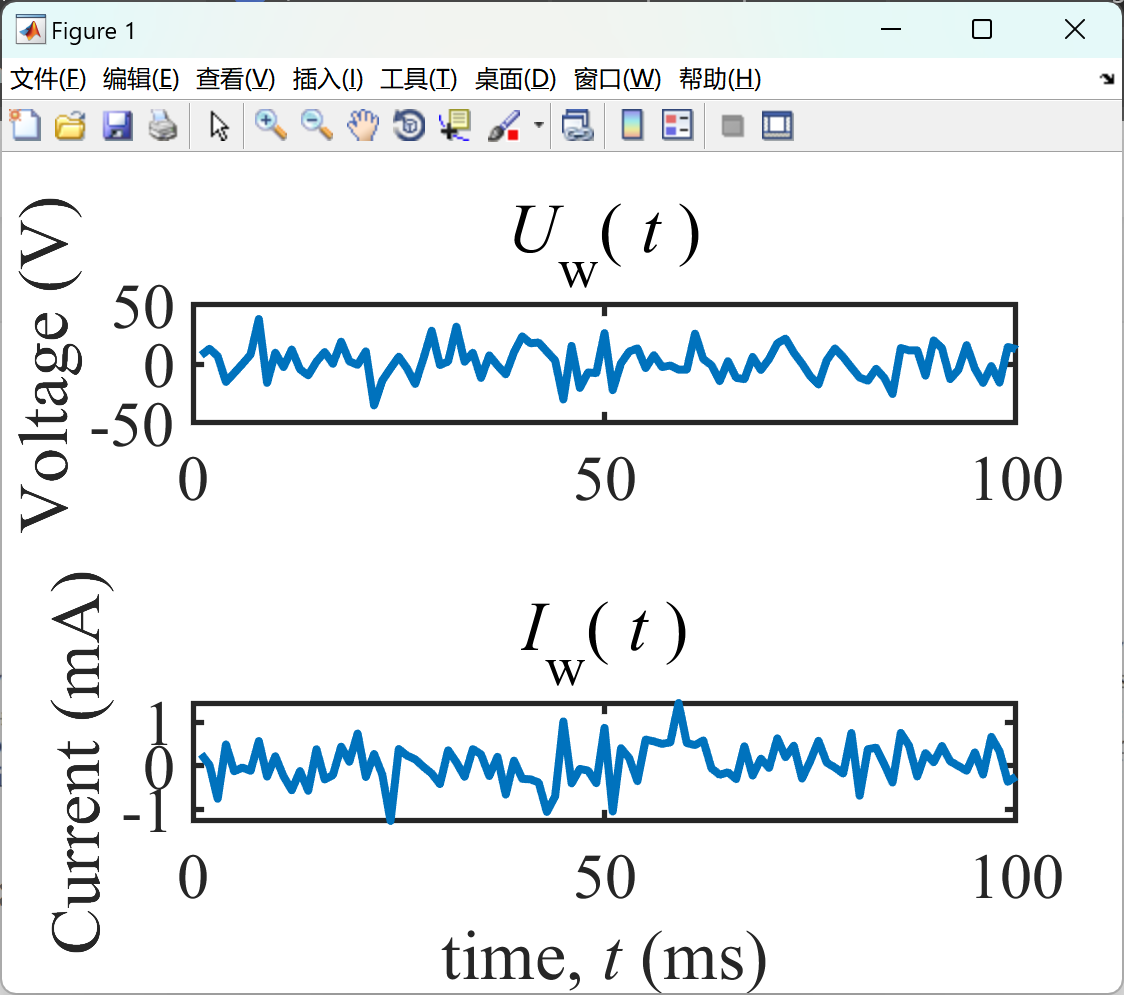
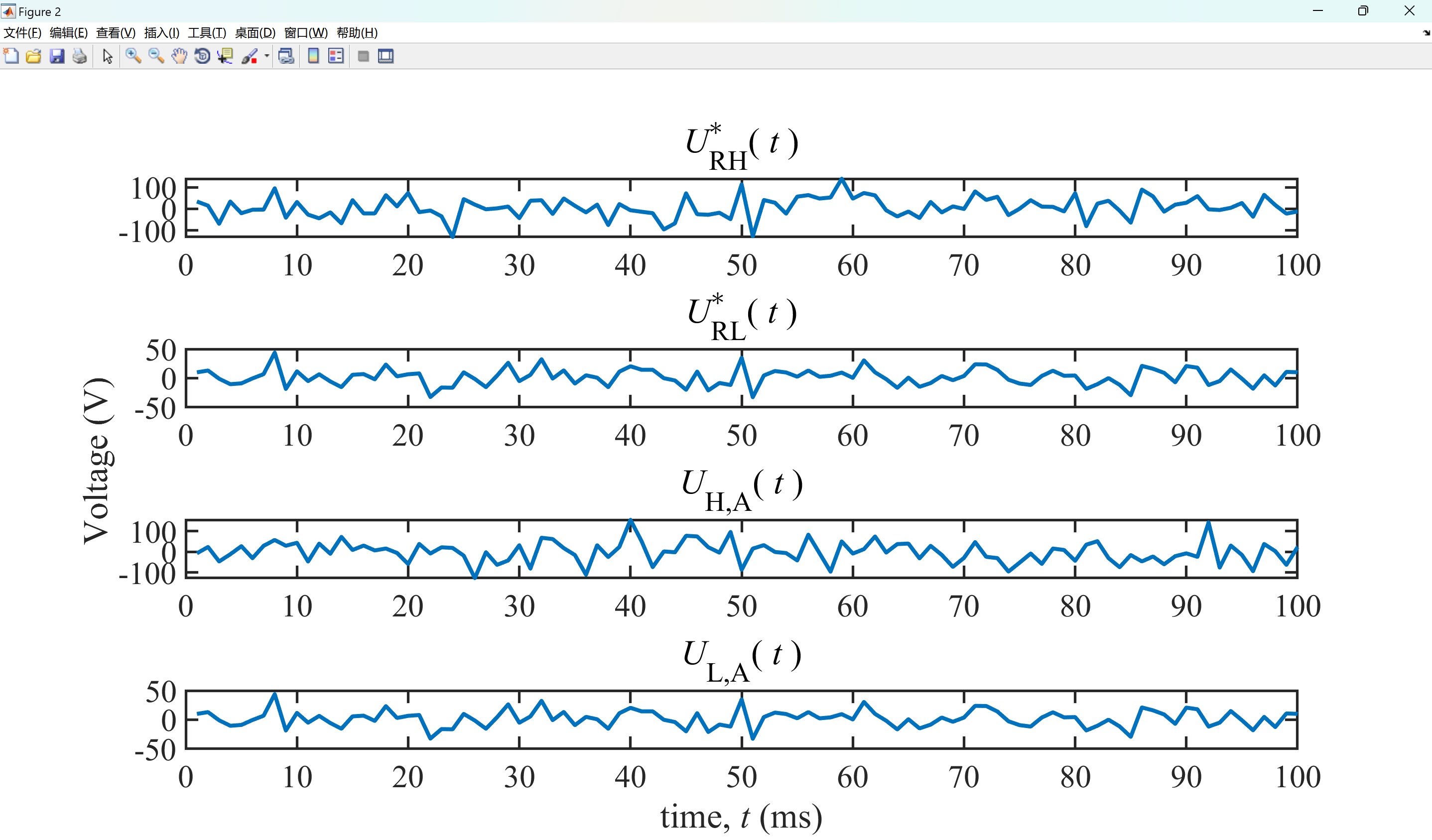
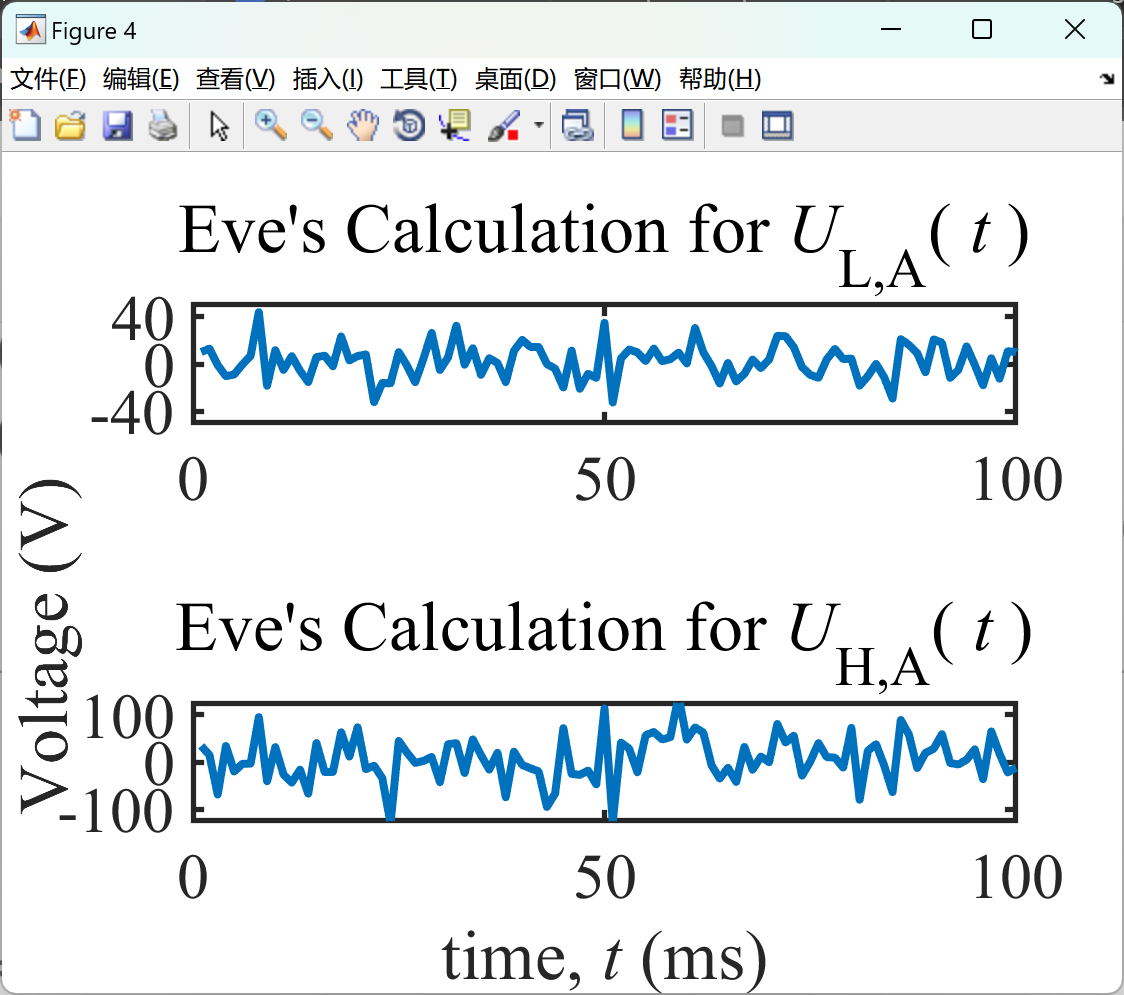
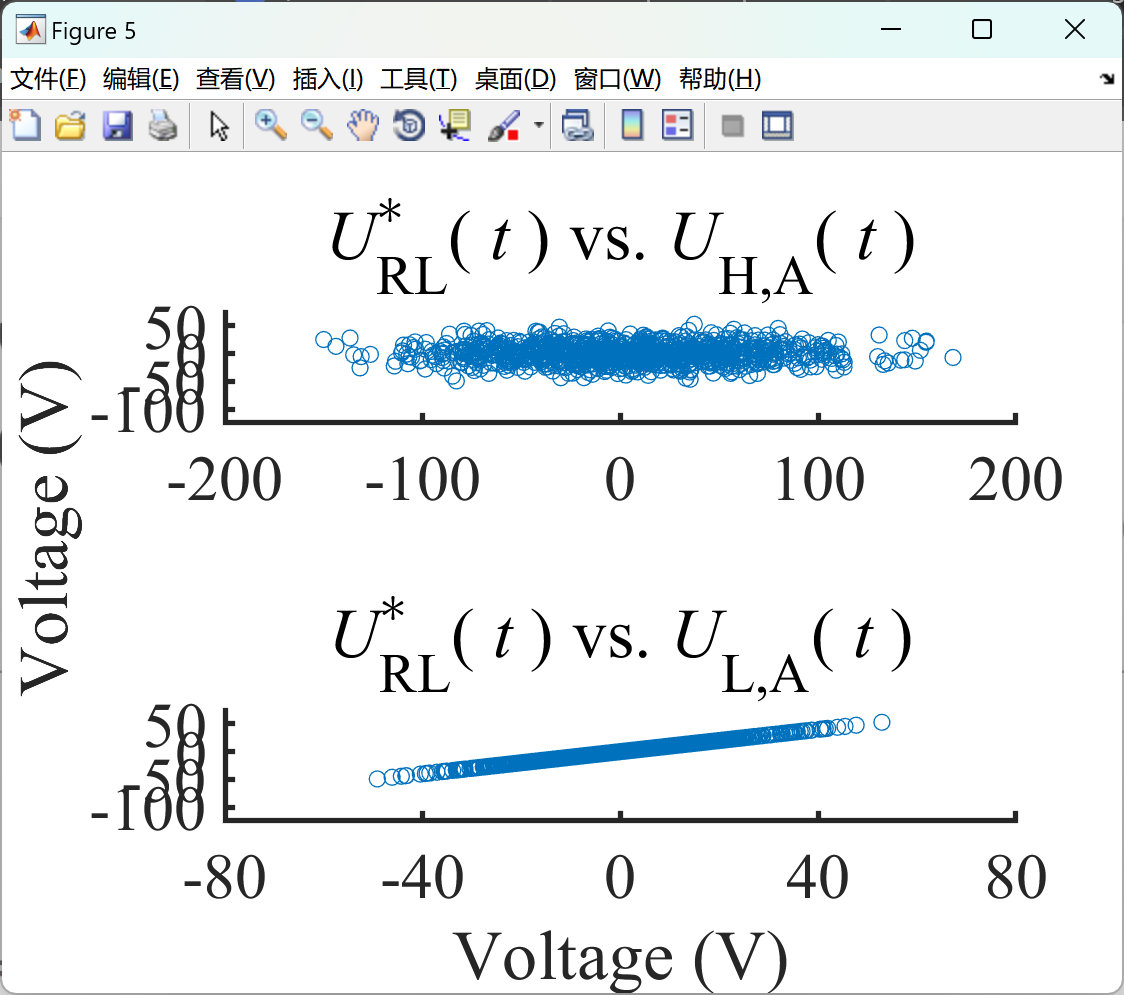
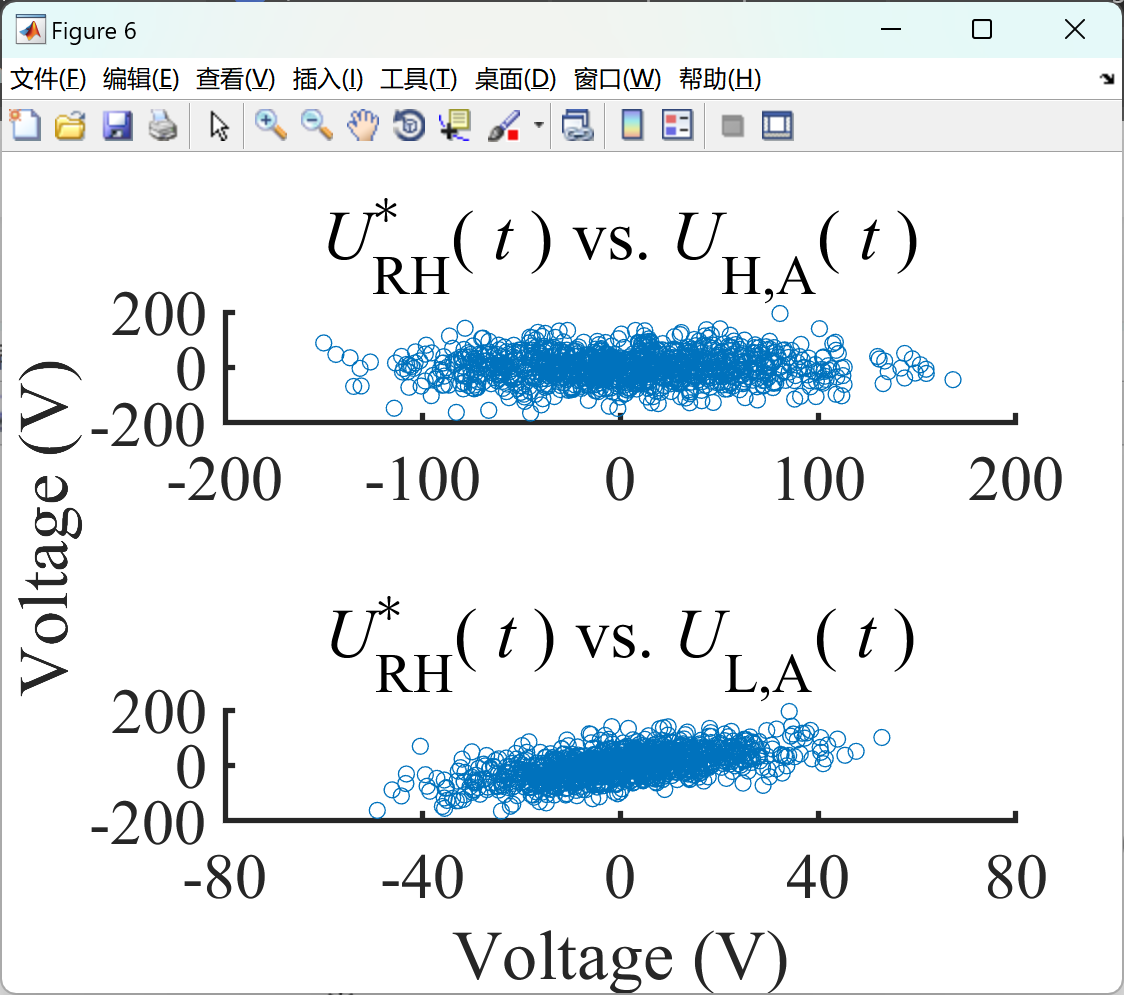
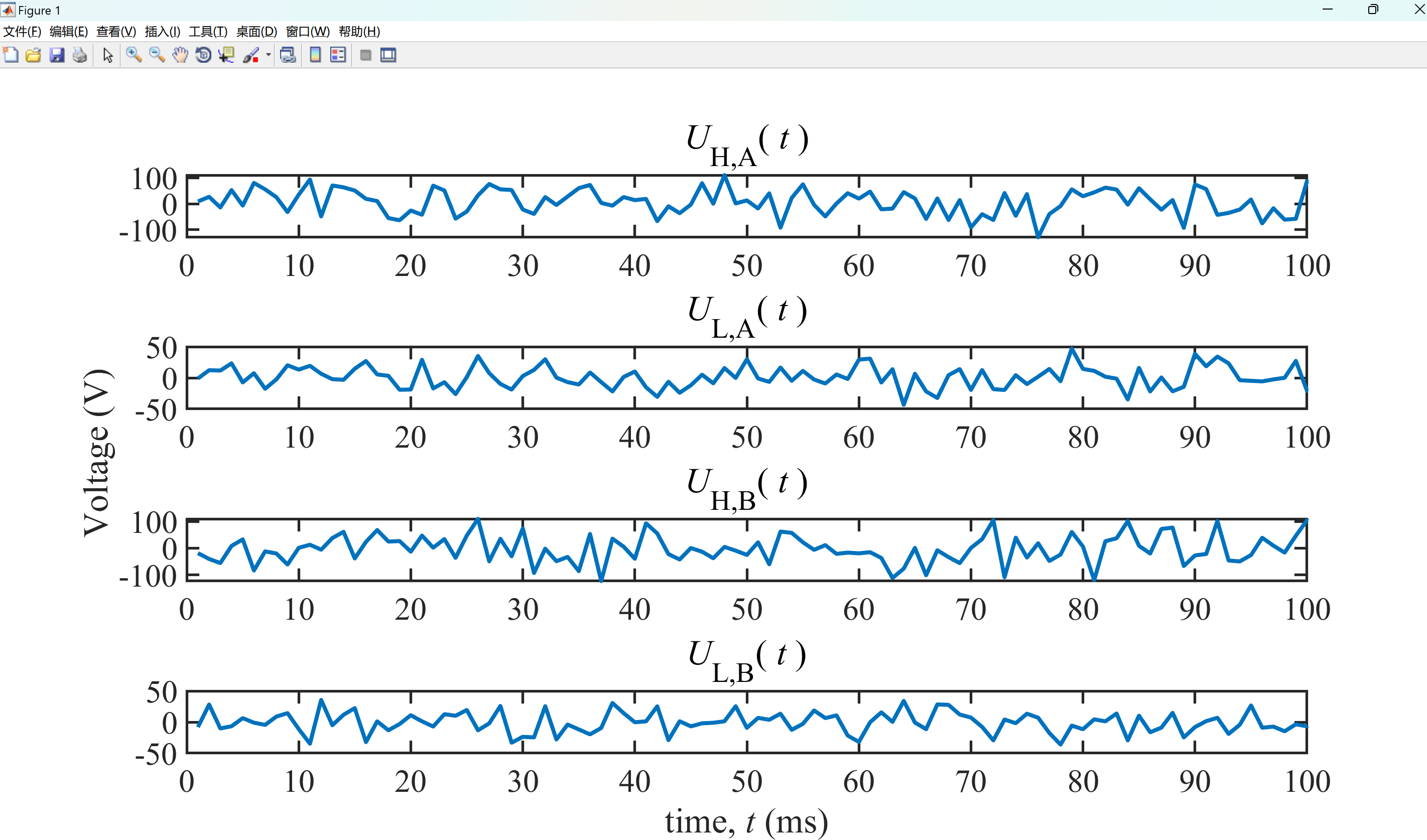

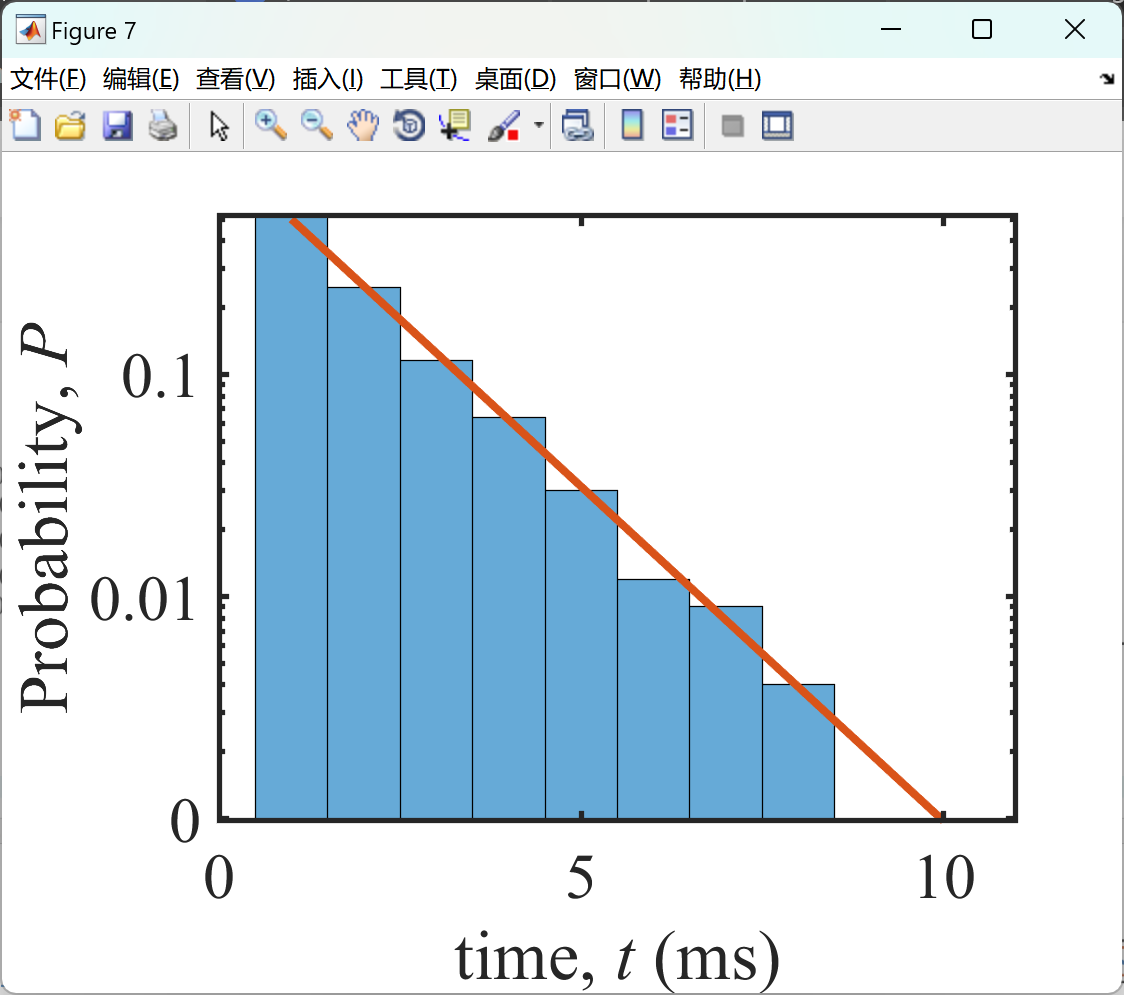
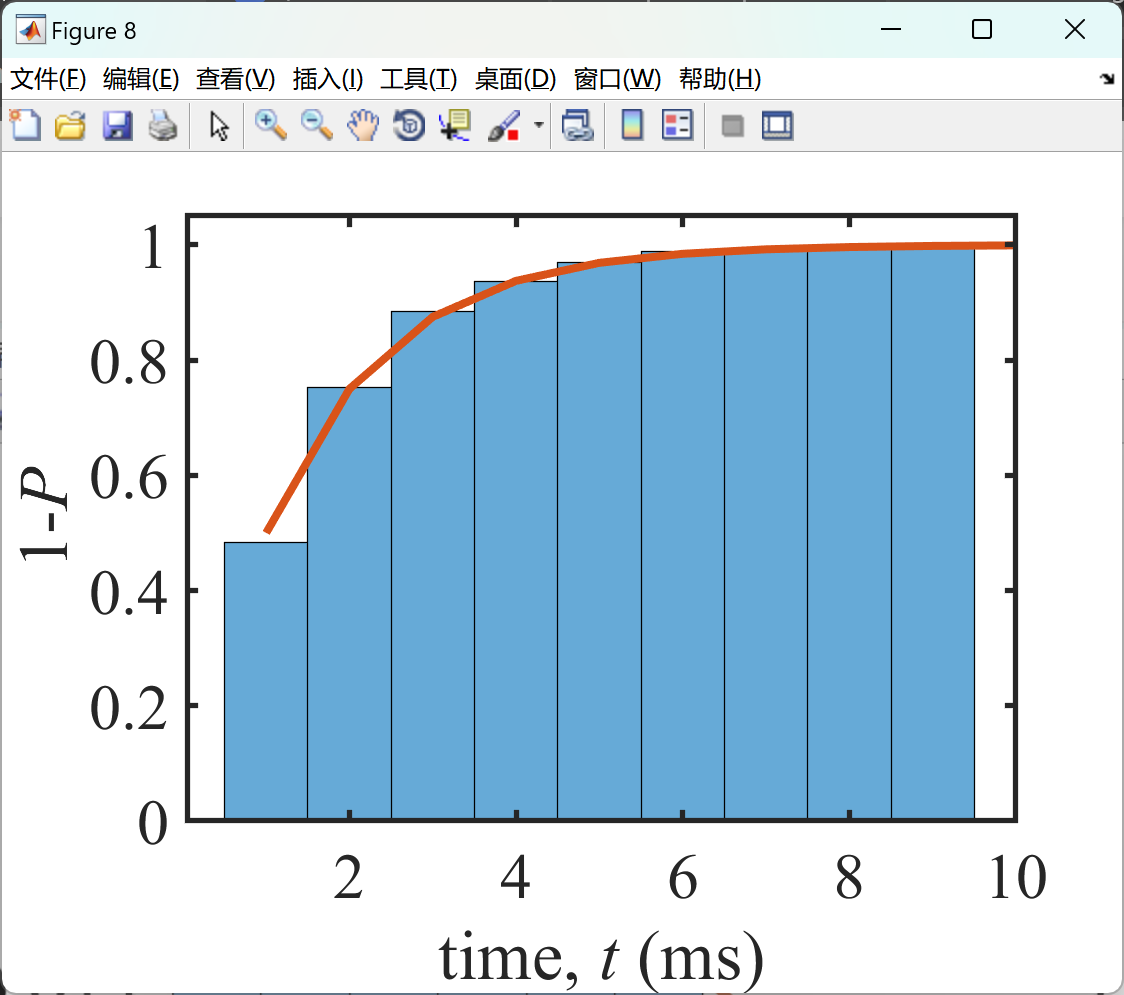




部分代码:
%multimeter's bits of resolution
N = 1;
Nvector = 1:1:N;
%if key(1) == RH && key(2) == RH
% range = max(HH)-min(HH);
%elseif key(1) == RL && key(2) == RL
% range = max(LL)-min(LL);
%elseif key(1) == RH && key(2) == RL
% range = max(HL)-min(HL);
%elseif key(1) == RL && key(2) == RH
% range = max(LH)-min(LH);
%else
% disp('Not a valid key');
% return;
%end
%resolution = 2*range/2^N;
%let's take the n-sample average for how many times Eve guesses correctly
%for each bit of resolution
%the structure is, for a matrix of i rows and j columns, the j index will
%represent the bits of resolution, and the i index will represent the ith
%sample value. n-sample averaging will be used.
nsamples = 1000; %Occurrences
averageuesses = zeros(nsamples,N-min(Nvector)+1);
averageLL = zeros(nsamples,N-min(Nvector)+1);
averageHL = zeros(nsamples,N-min(Nvector)+1);
averageLH = zeros(nsamples,N-min(Nvector)+1);
guessrecord = zeros(N,length(nsamples));
guessrecord_twocases = zeros(N,length(nsamples));
%Why not use Shah's noise?
fileID = fopen('shah_GBLWN_Entire_RNG.txt','r');
%noise = fscanf(fileID,'%f');
%noise = noise';
for x = 1:1:N
for j = 1:1:nsamples
%set RNG noise voltages, each with a different seed
UAH = randn(1,n)*sqrt(4*k*Teff*RH*fB);
UBH = randn(1,n)*sqrt(4*k*Teff*RH*fB);
UAL = randn(1,n)*sqrt(4*k*Teff*RL*fB);
UBL = randn(1,n)*sqrt(4*k*Teff*RL*fB);
%Why not use Shah's noise?
%UAH = noise((4*n*(j-1)+1):1:(4*j-3)*n);
%UAH = (UAH/rms(UAH))*sqrt(4*k*Teff*RH*fB);
%UBH = noise(((4*j-3)*n+1):1:(4*j-2)*n);
%UBH = (UBH/rms(UBH))*sqrt(4*k*Teff*RH*fB);
%UAL = noise(((4*j-2)*n+1):(4*j-1)*n);
%UAL = (UAL/rms(UAL))*sqrt(4*k*Teff*RL*fB);
%UBL = noise(((4*j-1)*n+1):1:4*j*n);
%UBL = (UBL/rms(UBL))*sqrt(4*k*Teff*RL*fB);
%let's have another set of noises just for the histogram
UAHhist = randn(1,n);
UAHhist = (UAHhist/rms(UAHhist))*sqrt(4*k*Teff*RH*fB);
UBHhist = randn(1,n);
UBHhist = (UBHhist/rms(UBHhist))*sqrt(4*k*Teff*RH*fB);
UALhist = randn(1,n);
UALhist = (UALhist/rms(UALhist))*sqrt(4*k*Teff*RL*fB);
UBLhist = randn(1,n);
UBLhist = (UBLhist/rms(UBLhist))*sqrt(4*k*Teff*RL*fB);
if key(1) == RH && key(2) == RH
UA = UAH;
UB = UBH;
elseif key(1) == RL && key(2) == RL
🎉3**** 参考文献****
文章中一些内容引自网络,会注明出处或引用为参考文献,难免有未尽之处,如有不妥,请随时联系删除。

🌈4 Matlab代码、数据、文章
版权归原作者 然哥爱编程 所有, 如有侵权,请联系我们删除。