祖冲之密码算法结构
总体布局
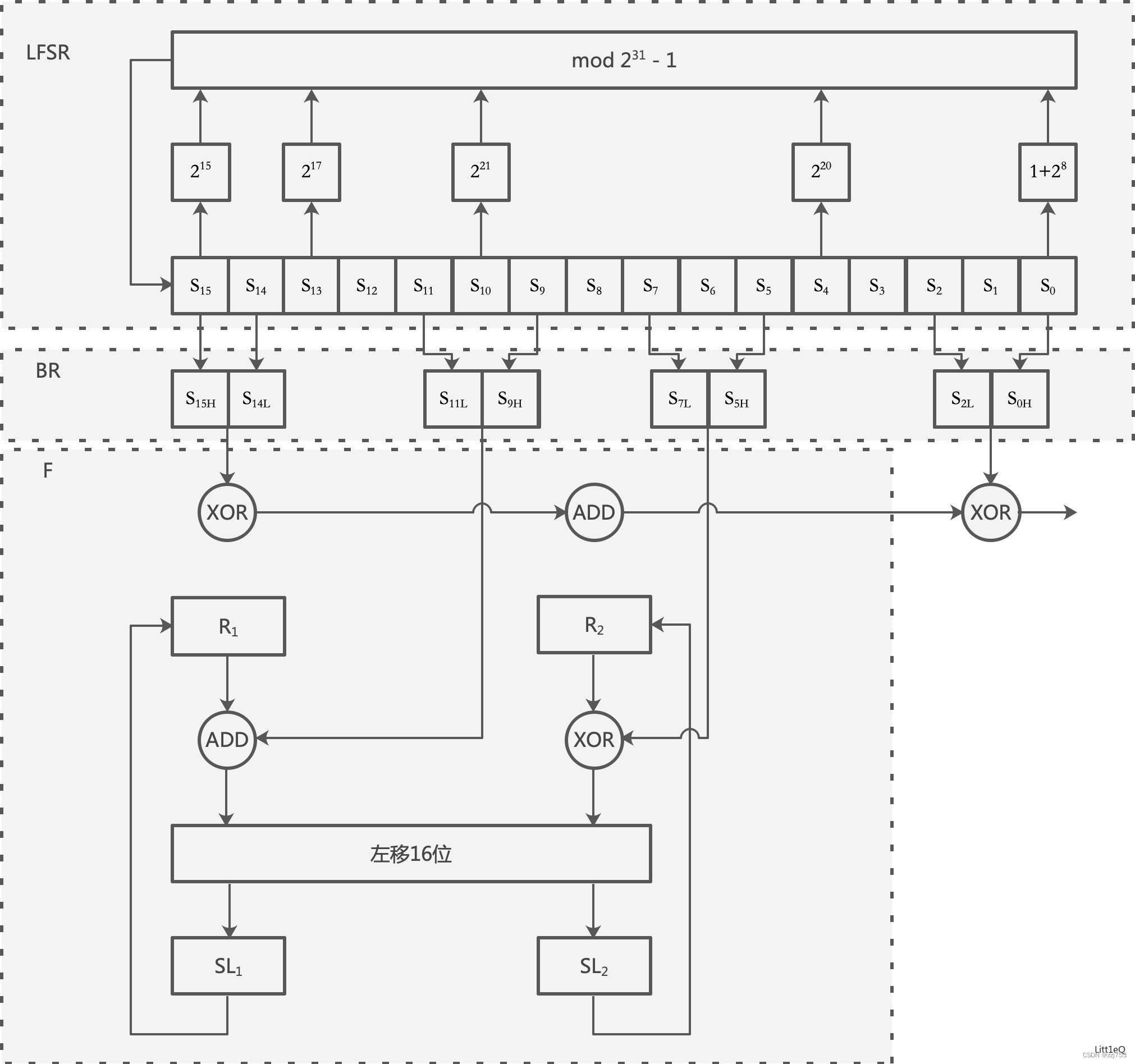
祖冲之加密由上层的线性反馈移位寄存器(LFSR)和中层的比特重组(BR)以及下层的非线性函数F组成。
线性反馈移位寄存器的输出作为比特重组的输入,比特重组的输出供下层的F函数输出密钥。
线性反馈移位寄存器
线性反馈移位寄存器由16个31比特寄存器单元变量s0,s1…s15组成,以有限域(
)上的16次本原多项式为连接多项式。连接多项式为:
线性反馈移位寄存器有两种运行模式,分别为初始化模式和工作模式:
初始化模式LFSR计算如下:
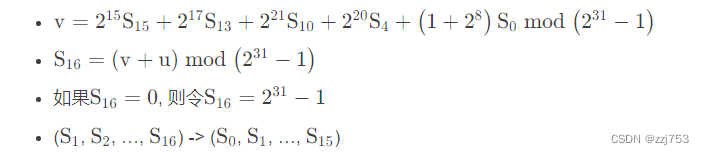
其中u是非线性函数F的32比特输出W通过舍弃最低位比特得到的。
工作模式LFSR计算如下:
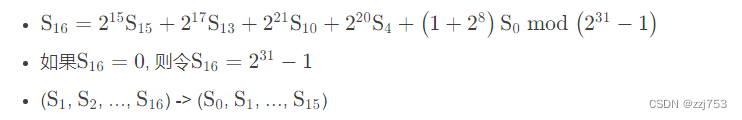
比特重组
比特重组从LFSR的寄存器单元中抽取128比特组成4个32比特字X0,X1,X2,X3。比特重组的具体计算过程如下:
其中||表示两个字符首尾相连,HL的角标表示高位和低位。比如X0为S15的高位和S14的低位首尾相连。
非线性函数
非线性函数的内部包含了2个32比特存储单元R1R2,F的输入为来自比特重组的3个32比特字X0,X1,X2,输出为一个32比特字W。因此,非线性函数F是一个把96比特压缩为32比特的一个非线性压缩函数。函数的计算过程如下: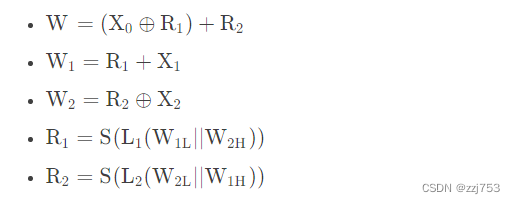
值得注意的是这里提到的加法为mod
加法。W,R1,R2为三个全局变量。
这里的S表示S盒变换,这里的S盒由4个并置的8进8出的S盒组成,且S0=S2,S1=S3,于是有:S=(S0,S1,S0,S1)
下图为S0,S1: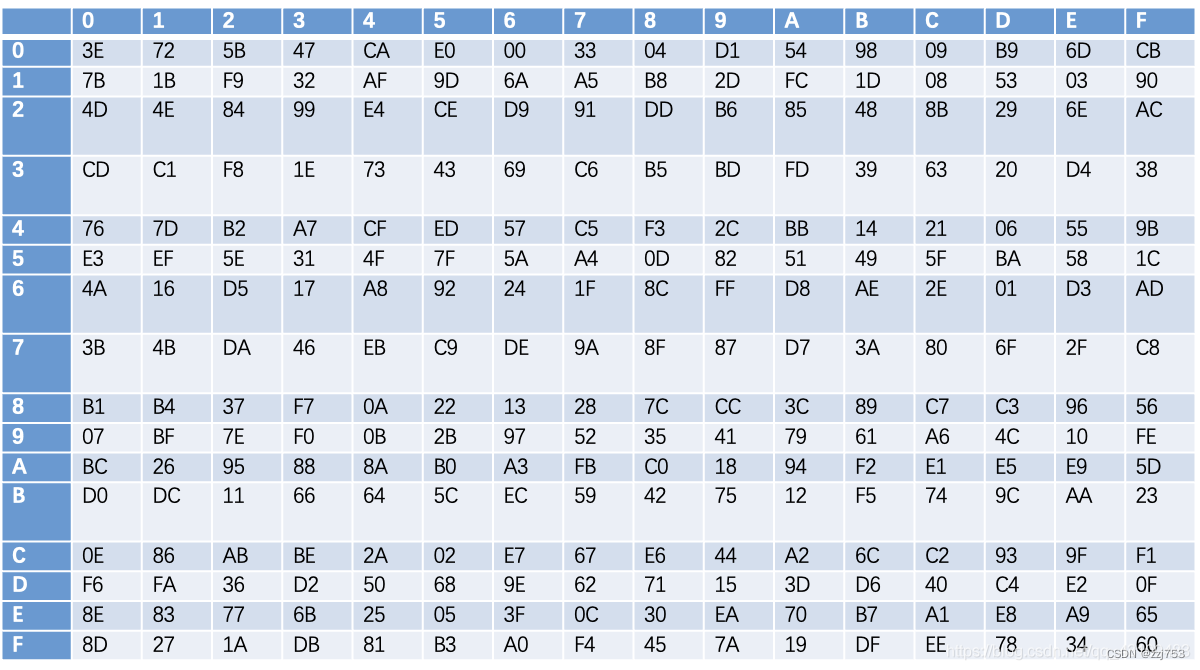
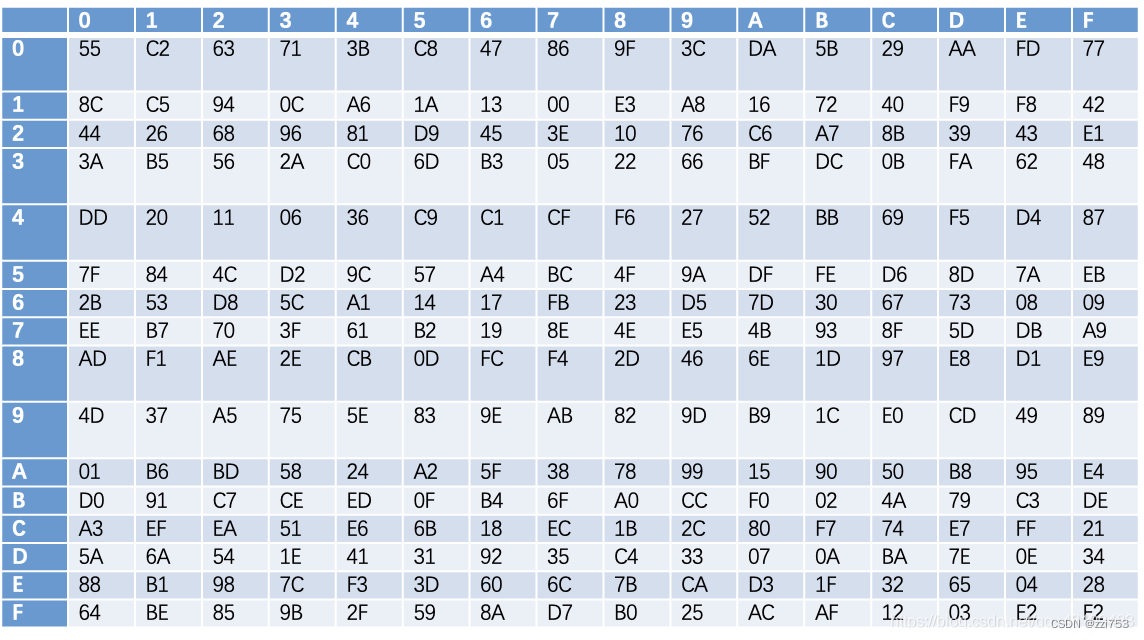
比如输入的8个比特位转换为16进制为A2,输入进入S0,那么输出就为第A行第2列对应的十六进制数95,转换为二进制为10010101。
上式中的L1L2为线性变换,定义如下: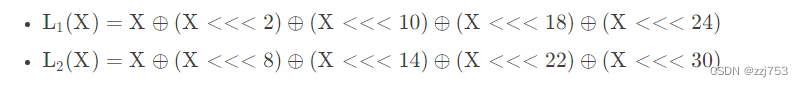
其中x>>>n表示把x循环右移n位。
密钥装入
密钥装入将128比特的初始密钥KEY和128比特的初始向量IV扩展为16个31比特字作为LFSR寄存器单元变量的初始状态。
设 KEY=K0||K1||…K15 ,每个Ki为8比特字节,IV以此类推。
设D为240比特常量,可分成16个15比特的子串: D=D0||D1||…||D15,每个子串分别为:
0x44D7, 0x26BC, 0x626B, 0x135E, 0x5789, 0x35E2, 0x7135, 0x09AF,
0x4D78, 0x2F13, 0x6BC4, 0x1AF1, 0x5E26, 0x3C4D, 0x789A, 0x47AC
将上述三个子串依次拼接,即:
Si = Ki || Di || IVi
算法运行
初始化阶段
首先将初始的密钥装入线性反馈移位寄存器中作为初态,并置R1,R2全为0,然后执行下述操作32次:
1.比特重组
2.W=F(X0,X1,X2)
3.LFSR初始化
工作阶段
首先执行下列过程一次,并将F的输出W舍弃:
1.比特重组
2.F(X0,X1,X2)
3.LFSR工作模式
然后进入密钥输出阶段:
1.比特重组
2.Z=F(X0,X1,X2)
X3
3.LFSR工作模式
话不多说上代码:
import math
S0=[[0x3e,0x72,0x5b,0x47,0xca,0xe0,0x00,0x33,0x04,0xd1,0x54,0x98,0x09,0xb9,0x6d,0xcb],[0x7b,0x1b,0xf9,0x32,0xaf,0x9d,0x6a,0xa5,0xb8,0x2d,0xfc,0x1d,0x08,0x53,0x03,0x90],[0x4d,0x4e,0x84,0x99,0xe4,0xce,0xd9,0x91,0xdd,0xb6,0x85,0x48,0x8b,0x29,0x6e,0xac],[0xcd,0xc1,0xf8,0x1e,0x73,0x43,0x69,0xc6,0xb5,0xbd,0xfd,0x39,0x63,0x20,0xd4,0x38],[0x76,0x7d,0xb2,0xa7,0xcf,0xed,0x57,0xc5,0xf3,0x2c,0xbb,0x14,0x21,0x06,0x55,0x9b],[0xe3,0xef,0x5e,0x31,0x4f,0x7f,0x5a,0xa4,0x0d,0x82,0x51,0x49,0x5f,0xba,0x58,0x1c],[0x4a,0x16,0xd5,0x17,0xa8,0x92,0x24,0x1f,0x8c,0xff,0xd8,0xae,0x2e,0x01,0xd3,0xad],[0x3b,0x4b,0xda,0x46,0xeb,0xc9,0xde,0x9a,0x8f,0x87,0xd7,0x3a,0x80,0x6f,0x2f,0xc8],[0xb1,0xb4,0x37,0xf7,0x0a,0x22,0x13,0x28,0x7c,0xcc,0x3c,0x89,0xc7,0xc3,0x96,0x56],[0x07,0xbf,0x7e,0xf0,0x0b,0x2b,0x97,0x52,0x35,0x41,0x79,0x61,0xa6,0x4c,0x10,0xfe],[0xbc,0x26,0x95,0x88,0x8a,0xb0,0xa3,0xfb,0xc0,0x18,0x94,0xf2,0xe1,0xe5,0xe9,0x5d],[0xd0,0xdc,0x11,0x66,0x64,0x5c,0xec,0x59,0x42,0x75,0x12,0xf5,0x74,0x9c,0xaa,0x23],[0x0e,0x86,0xab,0xbe,0x2a,0x02,0xe7,0x67,0xe6,0x44,0xa2,0x6c,0xc2,0x93,0x9f,0xf1],[0xf6,0xfa,0x36,0xd2,0x50,0x68,0x9e,0x62,0x71,0x15,0x3d,0xd6,0x40,0xc4,0xe2,0x0f],[0x8e,0x83,0x77,0x6b,0x25,0x05,0x3f,0x0c,0x30,0xea,0x70,0xb7,0xa1,0xe8,0xa9,0x65],[0x8d,0x27,0x1a,0xdb,0x81,0xb3,0xa0,0xf4,0x45,0x7a,0x19,0xdf,0xee,0x78,0x34,0x60]]
S1=[[0x55,0xc2,0x63,0x71,0x3b,0xc8,0x47,0x86,0x9f,0x3c,0xda,0x5b,0x29,0xaa,0xfd,0x77],[0x8c,0xc5,0x94,0x0c,0xa6,0x1a,0x13,0x00,0xe3,0xa8,0x16,0x72,0x40,0xf9,0xf8,0x42],[0x44,0x26,0x68,0x96,0x81,0xd9,0x45,0x3e,0x10,0x76,0xc6,0xa7,0x8b,0x39,0x43,0xe1],[0x3a,0xb5,0x56,0x2a,0xc0,0x6d,0xb3,0x05,0x22,0x66,0xbf,0xdc,0x0b,0xfa,0x62,0x48],[0xdd,0x20,0x11,0x06,0x36,0xc9,0xc1,0xcf,0xf6,0x27,0x52,0xbb,0x69,0xf5,0xd4,0x87],[0x7f,0x84,0x4c,0xd2,0x9c,0x57,0xa4,0xbc,0x4f,0x9a,0xdf,0xfe,0xd6,0x8d,0x7a,0xeb],[0x2b,0x53,0xd8,0x5c,0xa1,0x14,0x17,0xfb,0x23,0xd5,0x7d,0x30,0x67,0x73,0x08,0x09],[0xee,0xb7,0x70,0x3f,0x61,0xb2,0x19,0x8e,0x4e,0xe5,0x4b,0x93,0x8f,0x5d,0xdb,0xa9],[0xad,0xf1,0xae,0x2e,0xcb,0x0d,0xfc,0xf4,0x2d,0x46,0x6e,0x1d,0x97,0xe8,0xd1,0xe9],[0x4d,0x37,0xa5,0x75,0x5e,0x83,0x9e,0xab,0x82,0x9d,0xb9,0x1c,0xe0,0xcd,0x49,0x89],[0x01,0xb6,0xbd,0x58,0x24,0xa2,0x5f,0x38,0x78,0x99,0x15,0x90,0x50,0xb8,0x95,0xe4],[0xd0,0x91,0xc7,0xce,0xed,0x0f,0xb4,0x6f,0xa0,0xcc,0xf0,0x02,0x4a,0x79,0xc3,0xde],[0xa3,0xef,0xea,0x51,0xe6,0x6b,0x18,0xec,0x1b,0x2c,0x80,0xf7,0x74,0xe7,0xff,0x21],[0x5a,0x6a,0x54,0x1e,0x41,0x31,0x92,0x35,0xc4,0x33,0x07,0x0a,0xba,0x7e,0x0e,0x34],[0x88,0xb1,0x98,0x7c,0xf3,0x3d,0x60,0x6c,0x7b,0xca,0xd3,0x1f,0x32,0x65,0x04,0x28],[0x64,0xbe,0x85,0x9b,0x2f,0x59,0x8a,0xd7,0xb0,0x25,0xac,0xaf,0x12,0x03,0xe2,0xf2]]
D=[0x44d7,0x26bc,0x626b,0x135e,0x5789,0x35e2,0x7135,0x09af,0x4d78,0x2f13,0x6bc4,0x1af1,0x5e26,0x3c4d,0x789a,0x47ac]
S=[0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0]
Key_result=[]
X=[0,0,0,0]
R1=0
R2=0
W=0
m32=pow(2,32)defBitReconstruction():#比特重组
X[0]=add2(S[15],S[14])
X[1]=add(S[11],S[9])
X[2]=add(S[7],S[5])
X[3]=add(S[2],S[0])defH(X):#取字符串高位
bits=(X>>15)&0xffffreturn bits
defL(X):#取字符串低位
bits = X &0xffffreturn bits
defadd(W1,W2):#W1L||W2H
W1l=L(W1)<<16
W2h=H(W2)all=W1l|W2h
returnalldefadd2(W1,W2):#W1H||W2L
W1h = H(W1)<<16
W2l = L(W2)all=W1h|W2l
returnalldefLFSRWithInitMode(u):#初始化模式
v=(2**15*S[15]+2**17*S[13]+2**21*S[10]+2**20*S[4]+(1+2**8)*S[0])%(2**31-1)
S.append((v+u)%(2**31-1))if S[16]==0:
S[16]=2**31-1
S.pop(0)defLFSRWithWorkMode():#工作模式
S.append((2**15* S[15]+2**17* S[13]+2**21* S[10]+2**20* S[4]+(1+2**8)* S[0])%(2**31-1))if S[16]==0:
S[16]=2**31-1
S.pop(0)defF(X0,X1,X2):#非线性函数Fglobal R1,R2,W
W=mod32(X0 ^ R1,R2)
W1=mod32(R1,X1)
W2=R2 ^ X2
R1=S_(L1(((W1<<16)|(W2>>16))&0xffffffff))
R2=S_(L2(((W2<<16)|(W1>>16))&0xffffffff))defmod32(R,X):#模32加return(R + X)%m32
defL1(X):#32比特线性变换return X ^ rot(X ,2)^ rot(X ,10)^ rot(X ,18)^ rot(X ,24)&0xffffffffdefL2(X):return X ^ rot(X ,8)^ rot(X ,14)^ rot(X ,22)^ rot(X ,30)&0xffffffffdefS_(X):#s盒
bit8=[0,0,0,0]
result=[0,0,0,0]
bit8[0]=X>>24&0xff
bit8[1]=(X>>16)&0xff
bit8[2]=(X>>8)&0xff
bit8[3]=X&0xff#s盒由四个8输入8输出的的s盒组成,每个小s盒运行的规律为:输入一个8bit数据,前四位bit数据对应一个行值#后4位bit对应一个列值,由确定的行和列值得出一个新的8bit数据作为加密后的数据(在表中体现为十六进制)for i inrange(4):
row = bit8[i]>>4
nuw = bit8[i]&0xfif i ==0or i==2:
result[i]=S0[row][nuw]else:
result[i]=S1[row][nuw]
ans =(result[0]<<24)|(result[1]<<16)|(result[2]<<8)| result[3]return ans
defrot(X,i):#循环位移return((X<<i)&0xffffffff)|(X>>(32-i))definitialize(key,iv):#密钥装入和初始化global R1, R2, W,S
for i inrange(16):
S[i]=(key[i]<<23)|(D[i]<<8)| iv[i]print('初始化之前线性移位寄存器基本状态为:')
print_S()#打印线性移位寄存器的基本状态for i inrange(32):#初始化阶段
BitReconstruction()
F(X[0], X[1], X[2])
LFSRWithInitMode(W >>1)#print_status()defcalculate():#计算阶段
BitReconstruction()
F(X[0], X[1], X[2])
LFSRWithWorkMode()for i inrange(keylen):
BitReconstruction()
F(X[0], X[1], X[2])
Key_result.append(W^X[3])
LFSRWithWorkMode()#print_status()#打印状态defprint_S():#打印初始的s0-s15for i inrange(16):if i==8:print()print('S'+str(i)+':\033[1;32m'+hex(S[i]).replace('0x','')+'\033[0m ',end='')print()defprint_status():#打印xrws[15]的状态for i inrange(4):print('X'+str(i)+':\033[1;31m'+hex(X[i]).replace('0x','')+'\033[0m ', end='')print('R1'+':\033[1;34m'+hex(R1).replace('0x','')+'\033[0m ', end='')print('R2'+':\033[1;34m'+hex(R2).replace('0x','')+'\033[0m ', end='')print('W'+':\033[1;35m'+hex(W).replace('0x','')+'\033[0m ', end='')print('S15'+':\033[1;36m'+hex(S[15]).replace('0x','')+'\033[0m ', end='')print()defprint_key():#打印密钥for i inrange(keylen):print('KEY'+str(i)+':\033[1;36m'+hex(Key_result[i]).replace('0x','')+'\033[0m ', end='')if __name__ =='__main__':#避免输入麻烦,初始密钥和iv给定
key=[0x3d,0x4c,0x4b,0xe9,0x6a,0x82,0xfd,0xae,0xb5,0x8f,0x64,0x1d,0xb1,0x7b,0x45,0x5b]
iv=[0x84,0x31,0x9a,0xa8,0xde,0x69,0x15,0xca,0x1f,0x6b,0xda,0x6b,0xfb,0xd8,0xc7,0x66]
initialize(key,iv)#print_S()
keylen=int(input("请输入您需要生成的密钥个数:"))
calculate()
print_key()
版权归原作者 zzj753 所有, 如有侵权,请联系我们删除。