文章目录
图片隐写基础1
题目地址 : https://ce.pwnthebox.com/challenges?type=1&diff=easy&id=92
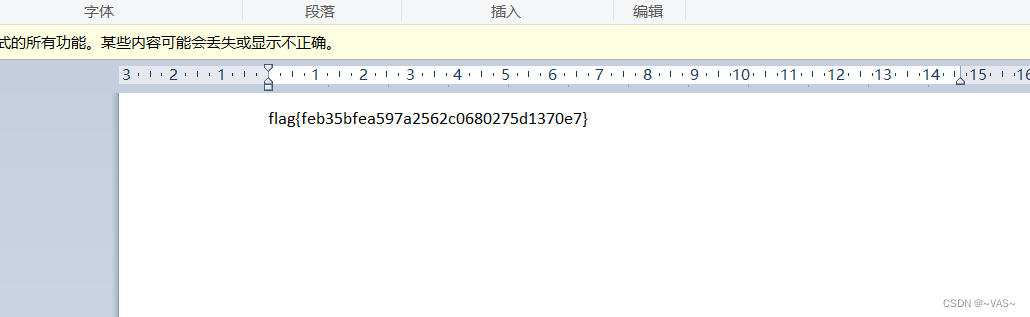
010editor发现flag.docx,用binwalk分解
图片隐写基础2
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=1&diff=easy&id=93
binwalk分解无果猜测是lsb但是也没有可疑之处,尝试修改图片高宽
import binascii
import struct
import sys
file=input("图片地址:")
fr =open(file,'rb').read()
data =bytearray(fr[0x0c:0x1d])
crc32key =eval('0x'+str(binascii.b2a_hex(fr[0x1d:0x21]))[2:-1])#原来的代码: crc32key = eval(str(fr[29:33]).replace('\\x','').replace("b'",'0x').replace("'",''))
n =4095for w inrange(n):
width =bytearray(struct.pack('>i', w))for h inrange(n):
height =bytearray(struct.pack('>i', h))for x inrange(4):
data[x+4]= width[x]
data[x+8]= height[x]
crc32result = binascii.crc32(data)&0xffffffffif crc32result == crc32key:print(width,height)
newpic =bytearray(fr)for x inrange(4):
newpic[x+16]= width[x]
newpic[x+20]= height[x]
fw =open(file+'.png','wb')
fw.write(newpic)
fw.close
sys.exit()

struct
与上题同理,爆破crc高度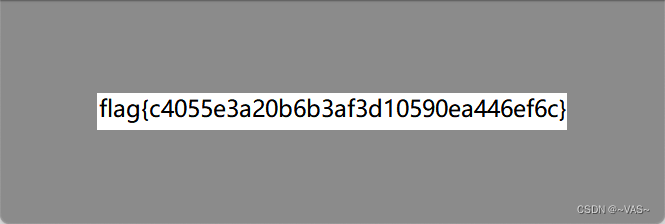
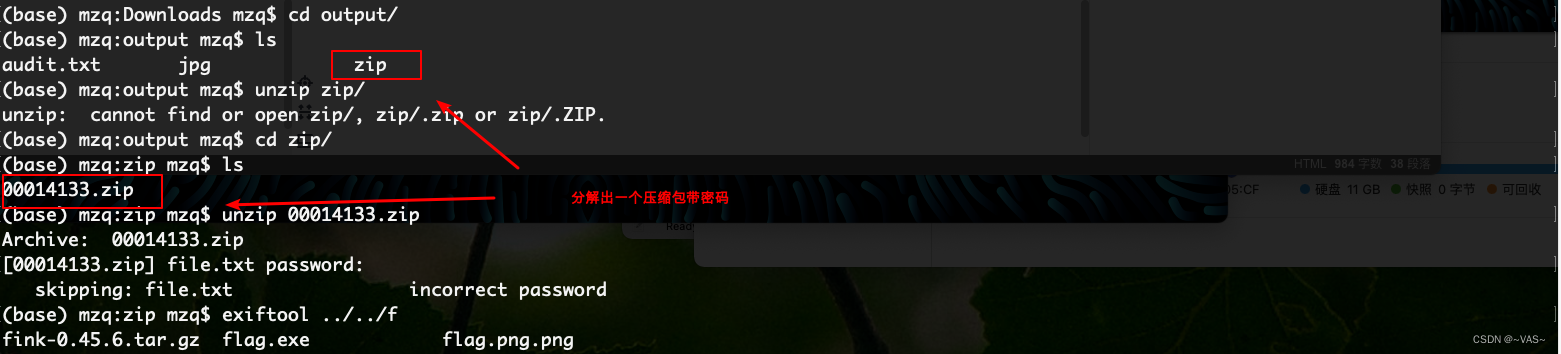
第四扩展FS
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=1&diff=medium&id=444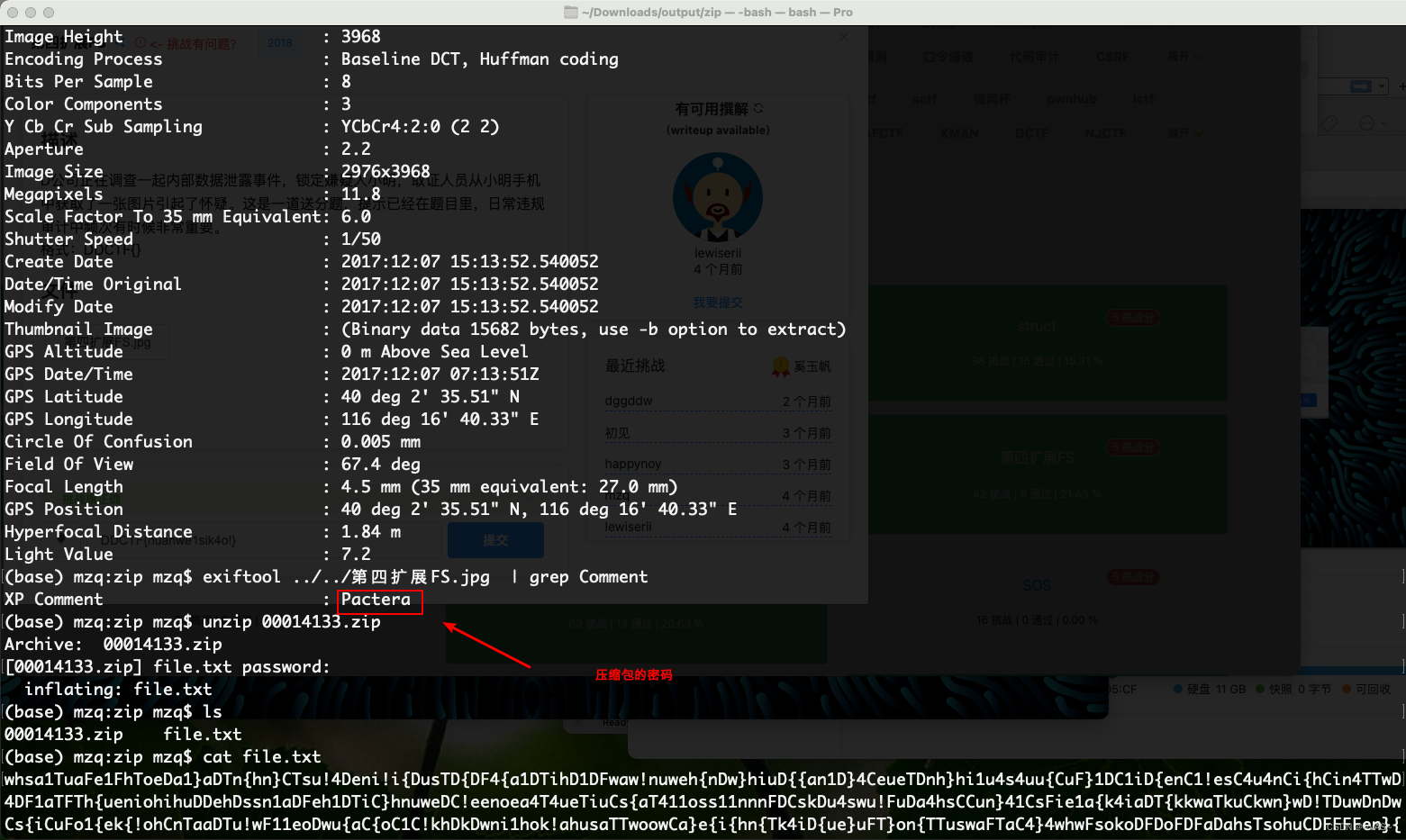
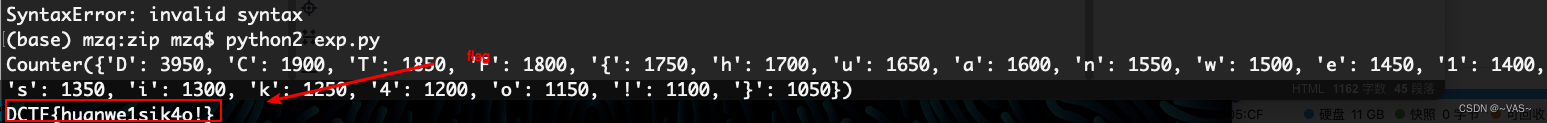
词频分析脚本
from collections import Counter
f=open('file.txt','r')
f_read=f.read()print Counter(f_read)
a=sorted(Counter(f_read).items(),key=lambda d:d[1],reverse=1)print''.join([i[0]for i in a])
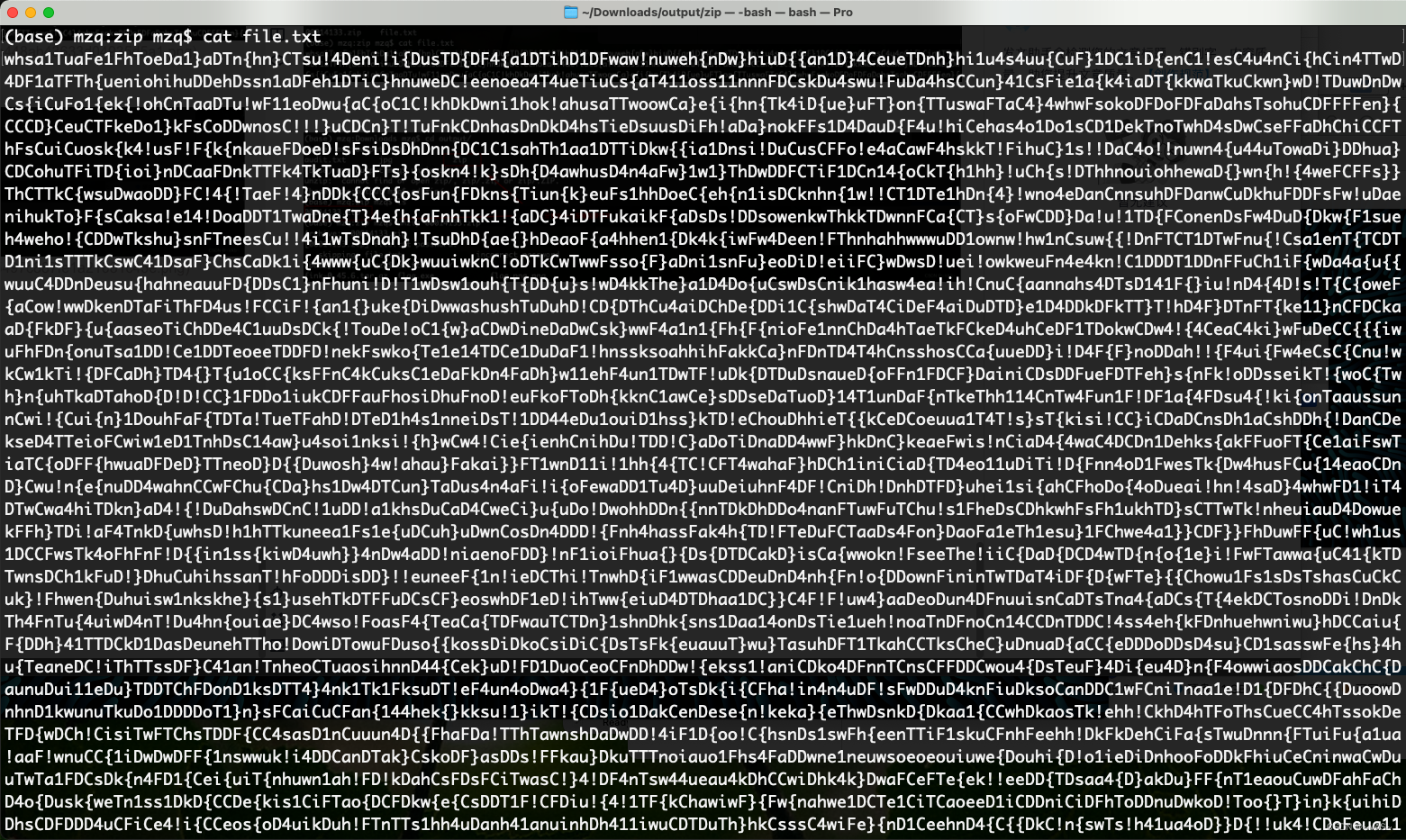
LSB3
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=3&diff=medium&id=182
lsb隐写
X-man-Keyword
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=5&diff=easy&id=549
keyword:
lovekfc

lsb检测到是用隐写数据的是有密码加密的所以zsteg才看不到
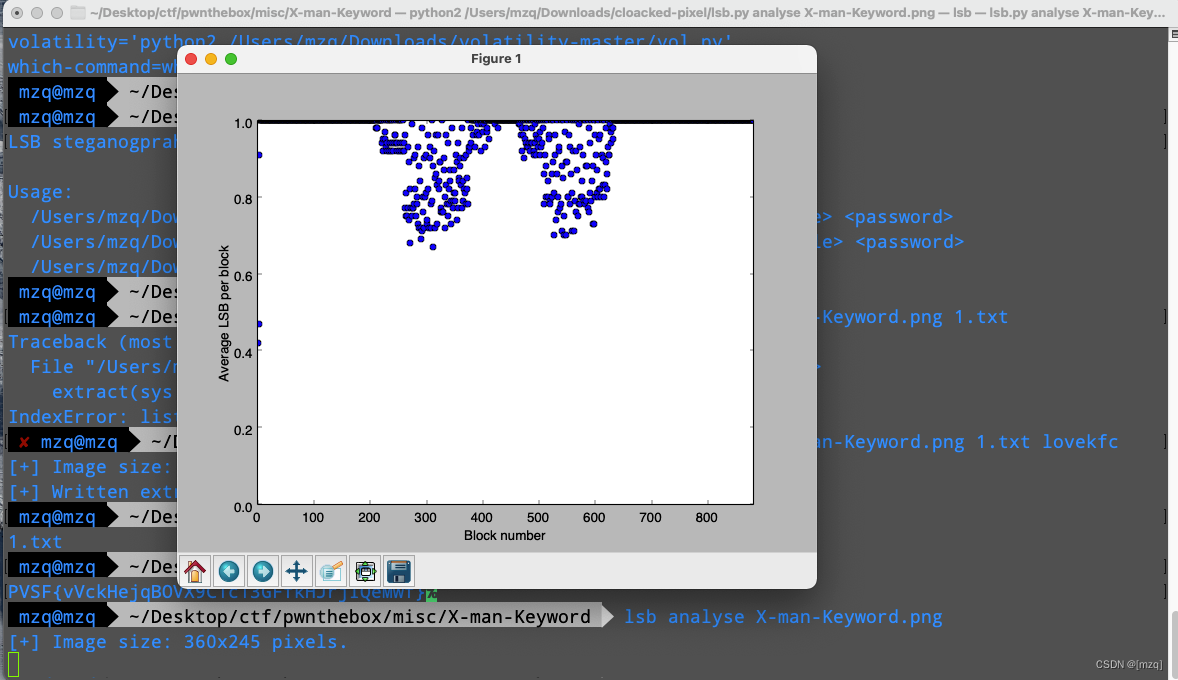
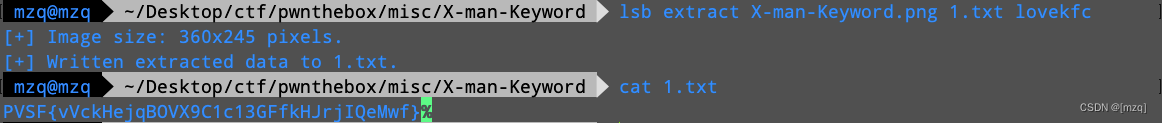
lsb extract X-man-Keyword.png 1.txt lovekfc
import string
enc ='PVSF{vVckHejqBOVX9C1c13GFfkHJrjIQeMwf}'
grid ='LOVEKFC'+'ABDGHIJMNPQRSTUWXY'
flag =''for i in enc:if i in string.ascii_lowercase:
index = grid.lower().index(i)
flag += string.ascii_lowercase[index]continueif i in string.ascii_uppercase:
index = grid.upper().index(i)
flag += string.ascii_uppercase[index]continue
flag += i
print(flag)
append
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=3&diff=medium&id=132
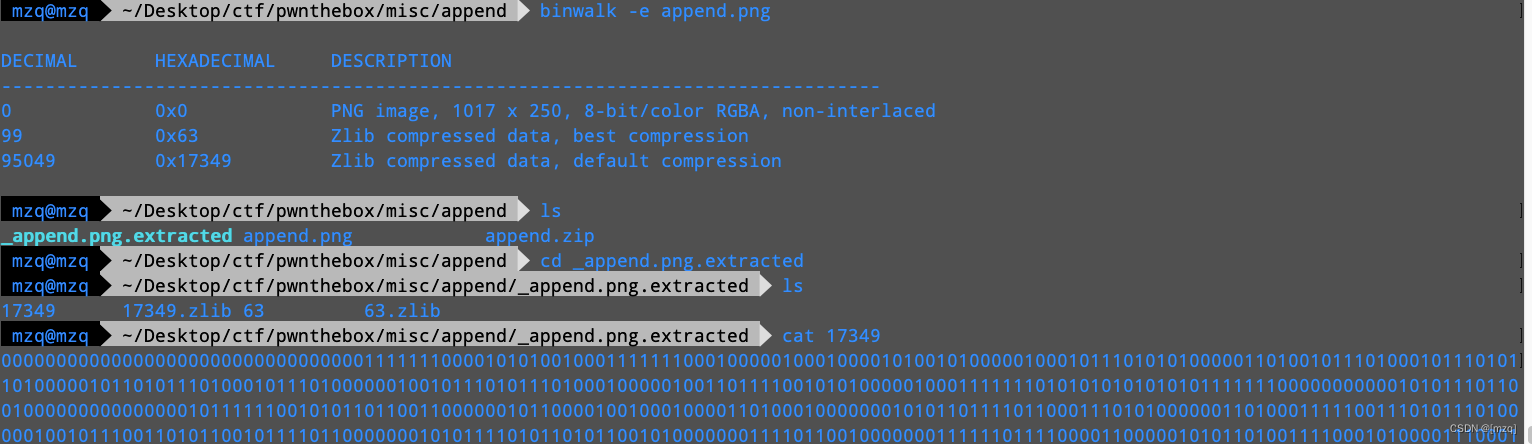
binwalk分解出一些数据,把其中的二进制数据转换成图片
exp
1import PIL
2from PIL import Image
345max=326 img = Image.new('RGB',(max,max))7str='0000000000000000000000000000000001111111000010101001000111111100010000010001000010100101000001000101110101010000011010010111010 00101110101101000001011010111010001011101000000100101110101110100010000010011011110010101000001000111111101010101010101011111110000000 00001010111011001000000000000000101111110010101101100110000001011000010010001000011010001000000010101101111011000111010100000011010001 11110011101011101000001001011100110101100101111011000000010101111010110101100101000000011110110010000000111111011110000110000010101101 00111100010100001110001110011101001100010111000010011001011111100010100000100000111000110001011100011001110010000101110110011111100111 00001010001110011100010011011011111001100000000000100101011011100011100000111111101110001000001010101110001000001001011011010010001110 00001011101011110001001011111101100010111010011000110111101001110000101110100100100000011010101000001000001001110110110011100101100011 111110010000100001110100100000000000000000000000000000000000000000000000000000000000000000000'8 i =09for y inrange(0,max):10for x inrange(0,max):11if(str[i]=='1'):12 img.putpixel([x,y],(0,0,0))13else:14 img.putpixel([x,y],(255,255,255))15 i +=11617 img.show()
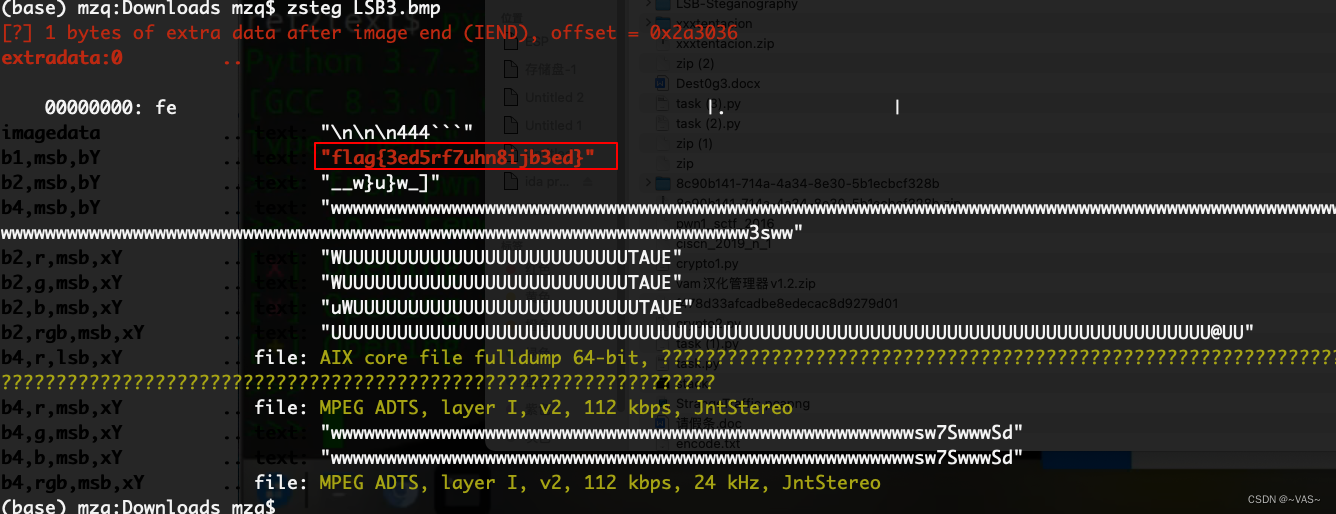
LSB3
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=3&diff=medium&id=182
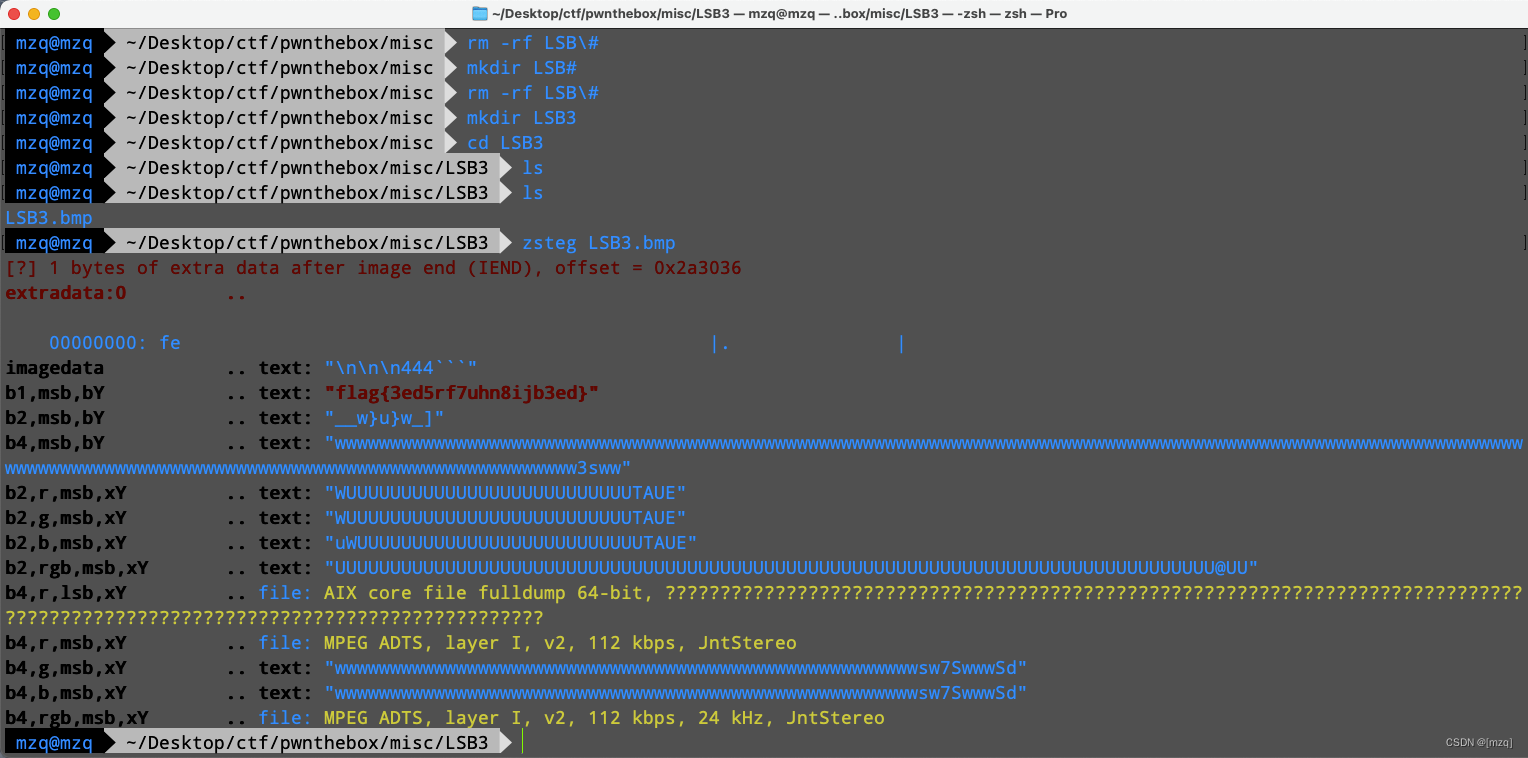
lsb签到题,直接zsteg一把硕
lsb2
题目地址 : https://ce.pwnthebox.com/challenges?page=2&diff=easy&keynote=2&id=137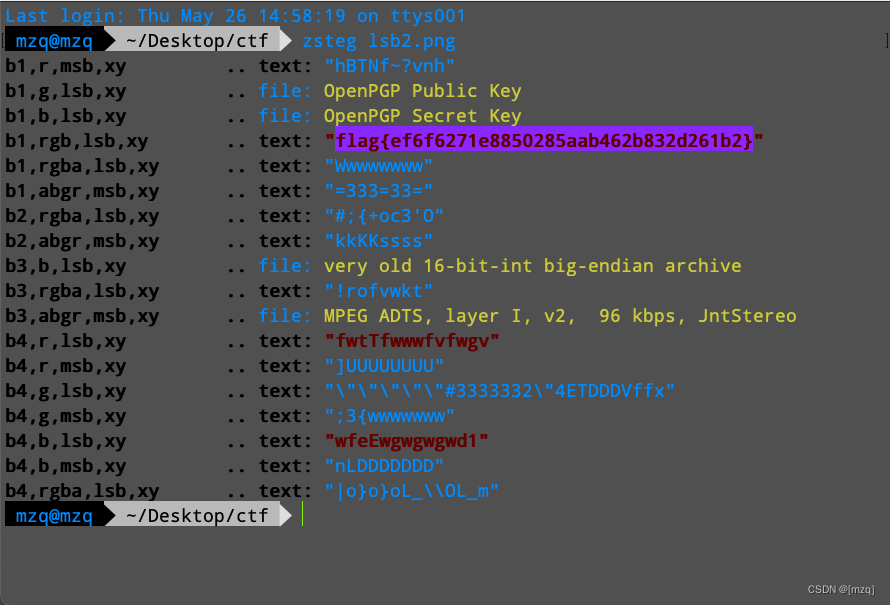
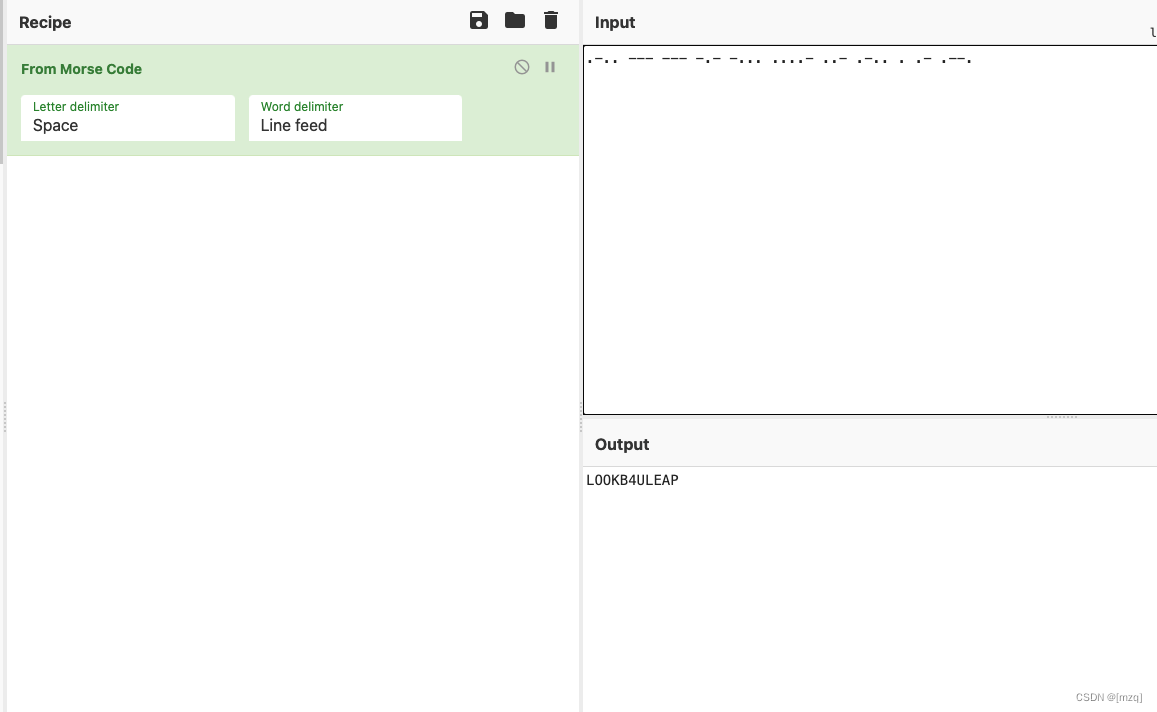
Follow The White Rabbit
题目地址 : https://ce.pwnthebox.com/challenges?type=1&page=4&id=1897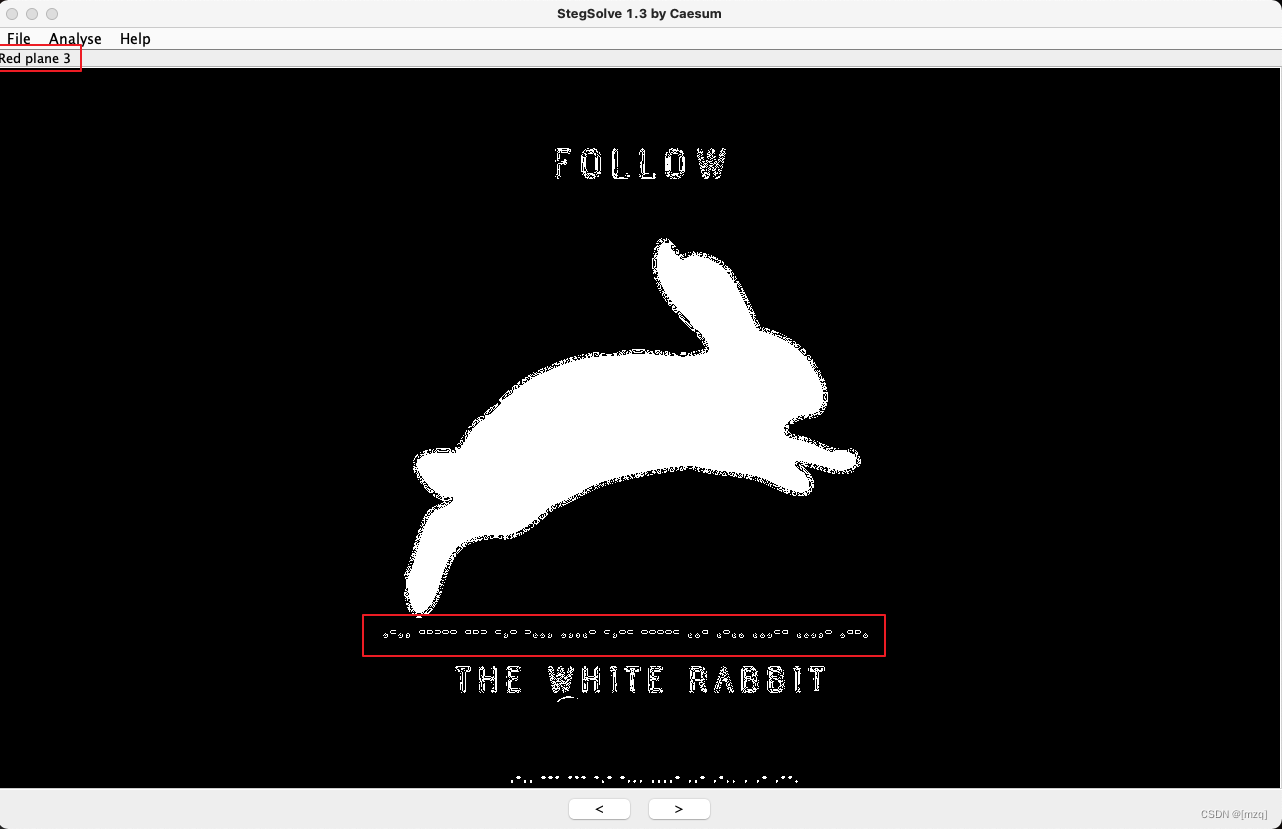
版权归原作者 [mzq] 所有, 如有侵权,请联系我们删除。