开始分析
拿到的是一个pyc文件,反编译回py文件即可查看源码
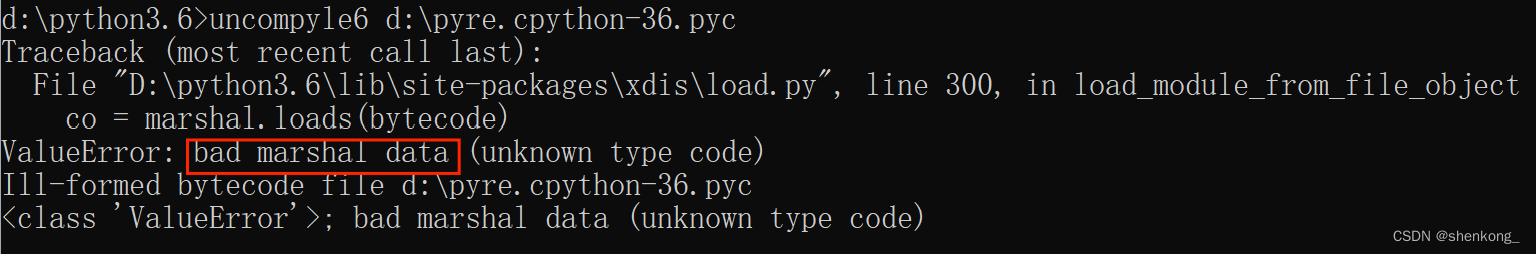
反编译出错,百度后了解到是文件头有问题,可以自行编译一个pyc文件,按照该正常文件头修改所给文件头即可
自行编译pyc文件
根据文件名得到编译环境为python3.6,所以执行下面的代码也应在python3.6下
#代码开头需导入py_compile
import py_compile
#随意写正确的python代码即可
def print_hi(name):
print(f'Hi, {name}')
if __name__ == '__main__':
print_hi('PyCharm')
# 最后调用该函数进行编译操作,单引号中是保存路径
py_compile.compile(r'D:\py_project')
使用WinHex修改文件头
pyc文件头占文件最开始的16字节,所以只需修改第一行即可
错误头
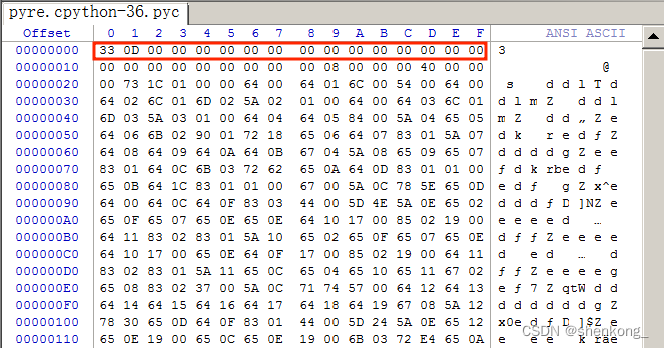
正确头
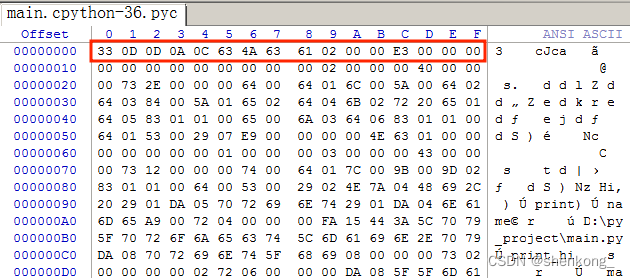
修改完毕后再次反编译,得到源码如下
# uncompyle6 version 3.8.0
# Python bytecode 3.6 (3379)
# Decompiled from: Python 3.6.0 (v3.6.0:41df79263a11, Dec 23 2016, 08:06:12) [MSC v.1900 64 bit (AMD64)]
# Embedded file name: pyre.py
# Compiled at: 2022-10-15 15:36:44
# Size of source mod 2**32: 609 bytes
from ctypes import *
from Crypto.Util.number import bytes_to_long
from Crypto.Util.number import long_to_bytes
def encrypt(v, k):
v0 = c_uint32(v[0])
v1 = c_uint32(v[1])
sum1 = c_uint32(0)
delta = 195935983
for i in range(32):
v0.value += (v1.value << 4 ^ v1.value >> 7) + v1.value ^ sum1.value + k[(sum1.value & 3)]
sum1.value += delta
v1.value += (v0.value << 4 ^ v0.value >> 7) + v0.value ^ sum1.value + k[(sum1.value >> 9 & 3)]
return (
v0.value, v1.value)
if __name__ == '__main__':
flag = input('please input your flag:')
k = [255, 187, 51, 68]
if len(flag) != 32:
print('wrong!')
exit(-1)
a = []
for i in range(0, 32, 8):
v1 = bytes_to_long(bytes(flag[i:i + 4], 'ascii'))
v2 = bytes_to_long(bytes(flag[i + 4:i + 8], 'ascii'))
a += encrypt([v1, v2], k)
enc = [
4006073346, 2582197823, 2235293281, 558171287, 2425328816, 1715140098, 986348143, 1948615354]
for i in range(8):
if enc[i] != a[i]:
print('wrong!')
exit(-1)
print('flag is flag{%s}' % flag)
# okay decompiling d:\pyre.cpython-36.pyc
逆向代码
根据反编译得到的源码写出逆向代码
#include<stdio.h>
#define u_int unsigned int
int main()
{
u_int enc[] = { 4006073346, 2582197823, 2235293281, 558171287,
2425328816, 1715140098, 986348143, 1948615354 };
u_int k[] = { 255, 187, 51, 68 };
for (int i = 0; i < 8; i += 2)
{
u_int delta = 195935983;
u_int s1 = delta * 32;
for (int j = 0; j < 32; j++)
{
enc[i + 1] -= (enc[i] << 4 ^ enc[i] >> 7) + enc[i] ^ s1 + k[s1 >> 9 & 3];
s1 -= delta;
enc[i] -= (enc[i + 1] << 4 ^ enc[i + 1] >> 7) + enc[i + 1] ^ s1 + k[s1 & 3];
}
}
char flag[32] = { 0 };
for (int i = 0; i < 8; i++)
{
flag[4 * i] = enc[i] >> 24;
flag[4 * i + 1] = (enc[i] >> 16) ^ 0xFF000000;
flag[4 * i + 2] = (enc[i] >> 8) ^ 0xFF000000;
flag[4 * i + 3] = enc[i] ^ 0xFF000000;
}
for (int i = 0; i < 32; i++)
{
printf("%c", flag[i]);
}
}
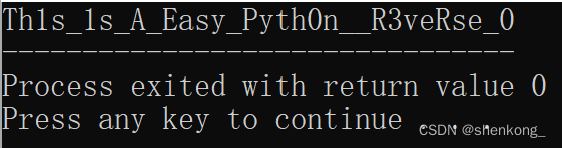
运行得到flag
版权归原作者 shenkong_ 所有, 如有侵权,请联系我们删除。