设备清单:1台PC、2台路由器(AR2220)、1台防火墙(USG6000V)
试验拓扑: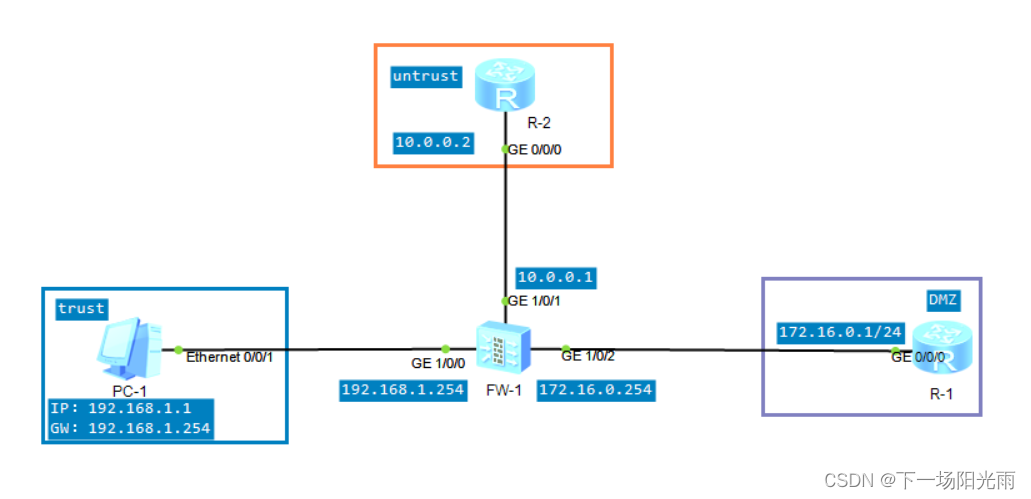 实验目的:实现trust、untrust、local、dmz区域互通。PC可以ping通R-1和R-2。
实验目的:实现trust、untrust、local、dmz区域互通。PC可以ping通R-1和R-2。
试验说明:PC在trust内、R-2在untrust内、R-1在dmz内。ip地址见拓扑。
配置开始:
R1的IP地址:
<R1>dis ip in br
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 172.16.0.1/24 up up
GigabitEthernet0/0/1 unassigned down down
NULL0 unassigned up up(s)
R2的IP地址:
<R2>dis ip in br
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 10.0.0.2/24 up up
GigabitEthernet0/0/1 unassigned down down
NULL0 unassigned up up(s)
FW的IP地址: 华为防火墙默认账号/密码:admin/Admin@123 登录后要修改密码。
<FW>dis ip in br
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 192.168.0.1/24 down down
GigabitEthernet1/0/0 192.168.1.254/24 up up
GigabitEthernet1/0/1 10.0.0.1/24 up up
GigabitEthernet1/0/2 172.16.0.1/24 up up
接着 在FW中将接口划入对应的区域:
[FW]firewall zone trust
[FW-zone-trust]add interface GigabitEthernet 1/0/0
[FW]firewall zone untrust
[FW-zone-untrust]add interface GigabitEthernet 1/0/1
[FW]firewall zone dmz
[FW-zone-dmz]add interface GigabitEthernet 1/0/2
配置防火墙
[FW]int g 1/0/0
[FW-GigabitEthernet1/0/0]service-manage ping permit
[FW-GigabitEthernet1/0/0]q
[FW]security-policy
[FW-policy-security]rule name ping
[FW-policy-security-rule-ping]source-zone local untrust trust dmz
[FW-policy-security-rule-ping]destination-zone local untrust trust dmz
//本意是让防护墙的区域互通,所以不做其他策略!
//工作中不建议这样配置!!!
[FW-policy-security-rule-ping]service icmp
[FW-policy-security-rule-ping]action permit
[FW-policy-security-rule-ping]dis th
#
rule name ping
source-zone dmz
source-zone local
source-zone trust
source-zone untrust
destination-zone dmz
destination-zone local
destination-zone trust
destination-zone untrust
service icmp
action permit
#
return
测试防火墙直连:
[FW]ping 192.168.1.1 PING 192.168.1.1: 56 data bytes, press CTRL_C to break Reply from 192.168.1.1: bytes=56 Sequence=1 ttl=128 time=32 ms Reply from 192.168.1.1: bytes=56 Sequence=2 ttl=128 time=4 ms Reply from 192.168.1.1: bytes=56 Sequence=3 ttl=128 time=4 ms Reply from 192.168.1.1: bytes=56 Sequence=4 ttl=128 time=5 ms Reply from 192.168.1.1: bytes=56 Sequence=5 ttl=128 time=4 ms --- 192.168.1.1 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 4/9/32 ms [FW]ping 10.0.0.2 PING 10.0.0.2: 56 data bytes, press CTRL_C to break Reply from 10.0.0.2: bytes=56 Sequence=1 ttl=255 time=51 ms Reply from 10.0.0.2: bytes=56 Sequence=2 ttl=255 time=14 ms Reply from 10.0.0.2: bytes=56 Sequence=3 ttl=255 time=15 ms Reply from 10.0.0.2: bytes=56 Sequence=4 ttl=255 time=4 ms Reply from 10.0.0.2: bytes=56 Sequence=5 ttl=255 time=6 ms --- 10.0.0.2 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 4/18/51 ms [FW]ping 172.16.0.1 PING 172.16.0.1: 56 data bytes, press CTRL_C to break Reply from 172.16.0.1: bytes=56 Sequence=1 ttl=255 time=47 ms Reply from 172.16.0.1: bytes=56 Sequence=2 ttl=255 time=7 ms Reply from 172.16.0.1: bytes=56 Sequence=3 ttl=255 time=8 ms Reply from 172.16.0.1: bytes=56 Sequence=4 ttl=255 time=9 ms Reply from 172.16.0.1: bytes=56 Sequence=5 ttl=255 time=12 ms --- 172.16.0.1 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 7/16/47 ms
接着配置OSPF和OSPF防火墙策略:
[R1]ospf 1 router-id 1.1.1.1
[R1-ospf-1]area 0
[R1-ospf-1-area-0.0.0.0]network 172.16.0.1 0.0.0.0
[R2]ospf 1 router-id 2.2.2.2
[R2-ospf-1]area 0
[R2-ospf-1-area-0.0.0.0]network 10.0.0.2 0.0.0.0
[FW]ospf 1 router-id 3.3.3.3
[FW-ospf-1]area 0
[FW-ospf-1-area-0.0.0.0]network 192.168.1.254 0.0.0.0
[FW-ospf-1-area-0.0.0.0]network 10.0.0.1 0.0.0.0
[FW-ospf-1-area-0.0.0.0]network 172.16.0.254 0.0.0.0
查看邻居是否建立:
[FW-ospf-1-area-0.0.0.0]dis ospf peer brief
OSPF Process 1 with Router ID 3.3.3.3
Peer Statistic Information
----------------------------------------------------------------------------
Area Id Interface Neighbor id State
0.0.0.0 GigabitEthernet1/0/1 2.2.2.2 Full
0.0.0.0 GigabitEthernet1/0/2 1.1.1.1 Full
----------------------------------------------------------------------------
接下来配置防火墙的OSPF策略:
[FW]security-policy
[FW-policy-security]rule name OSPF
[FW-policy-security-rule-OSPF]service ospf
[FW-policy-security-rule-OSPF]source-zone local dmz untrust
[FW-policy-security-rule-OSPF]destination-zone dmz local untrust
[FW-policy-security-rule-OSPF]action permit
[FW-policy-security-rule-OSPF]dis th
#
rule name OSPF
source-zone dmz
source-zone local
source-zone untrust
destination-zone dmz
destination-zone local
destination-zone untrust
service ospf
action permit
#
return
最后测试PC是否能ping通路由器:
PC>ping 10.0.0.2
Ping 10.0.0.2: 32 data bytes, Press Ctrl_C to break
From 10.0.0.2: bytes=32 seq=1 ttl=254 time=31 ms
From 10.0.0.2: bytes=32 seq=2 ttl=254 time=16 ms
--- 10.0.0.2 ping statistics ---
2 packet(s) transmitted
2 packet(s) received
0.00% packet loss
round-trip min/avg/max = 16/23/31 ms
PC>ping 172.16.0.1
Ping 172.16.0.1: 32 data bytes, Press Ctrl_C to break
From 172.16.0.1: bytes=32 seq=1 ttl=254 time=16 ms
From 172.16.0.1: bytes=32 seq=2 ttl=254 time=15 ms
From 172.16.0.1: bytes=32 seq=3 ttl=254 time=16 ms
--- 172.16.0.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 0/12/16 ms
PC>
试验结束,仅以此来记录本人HCIE-Datacom备考中涉及的知识点,不用作任何教学。突发奇想,想做一个自己的博客,就这样开始了,之前的试验会慢慢补齐。请理性观看,如有错误希望指正!
版权归原作者 下一场阳光雨 所有, 如有侵权,请联系我们删除。