效果如图:
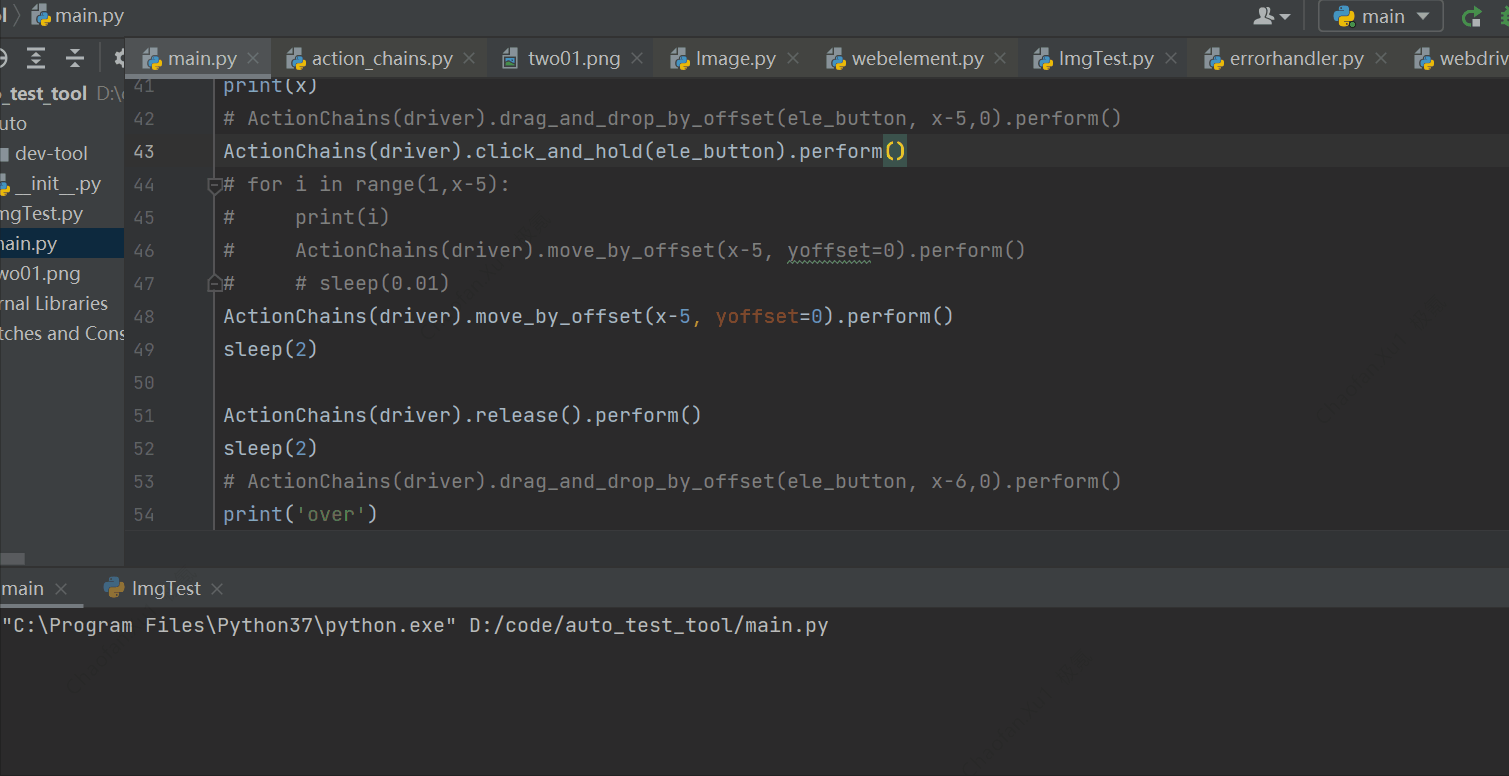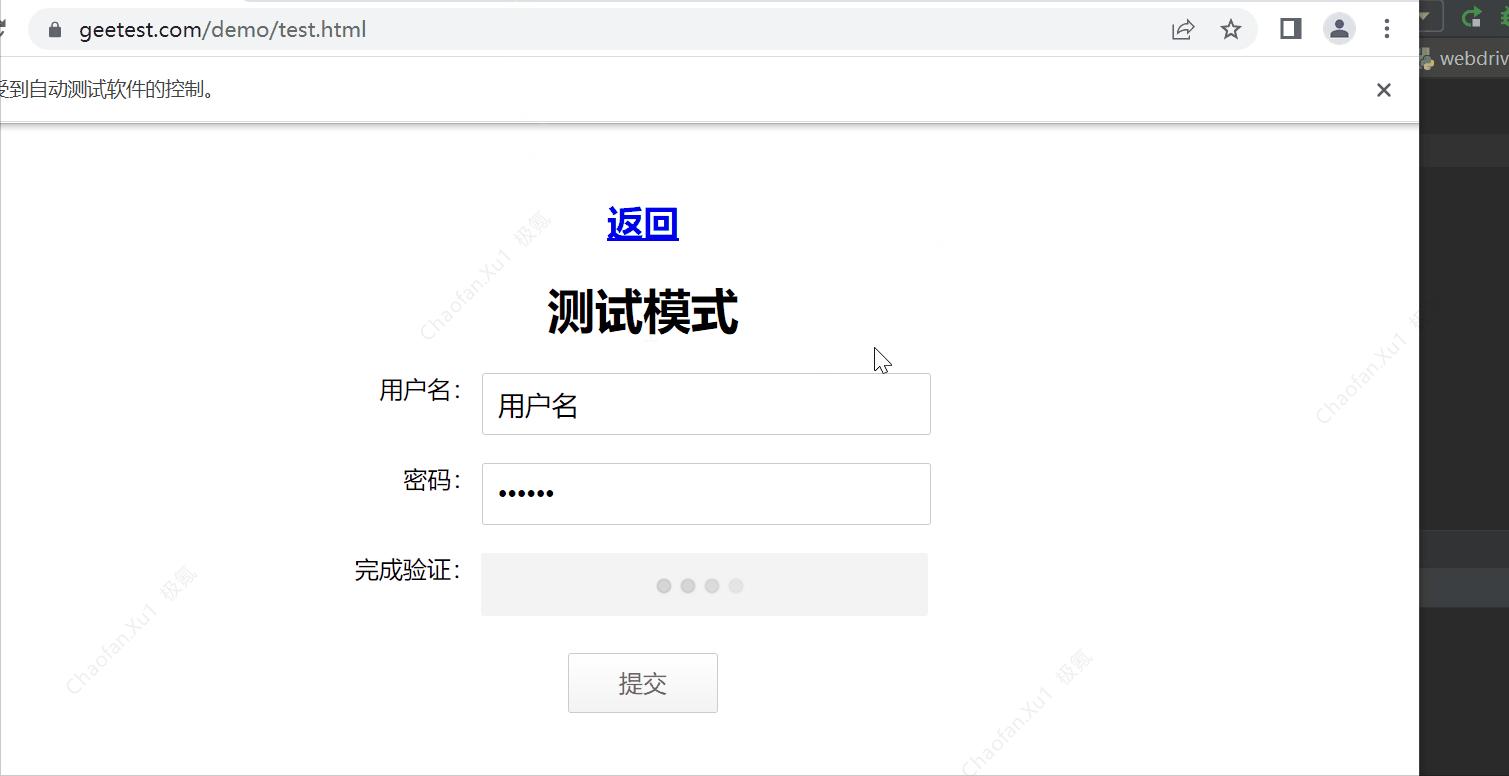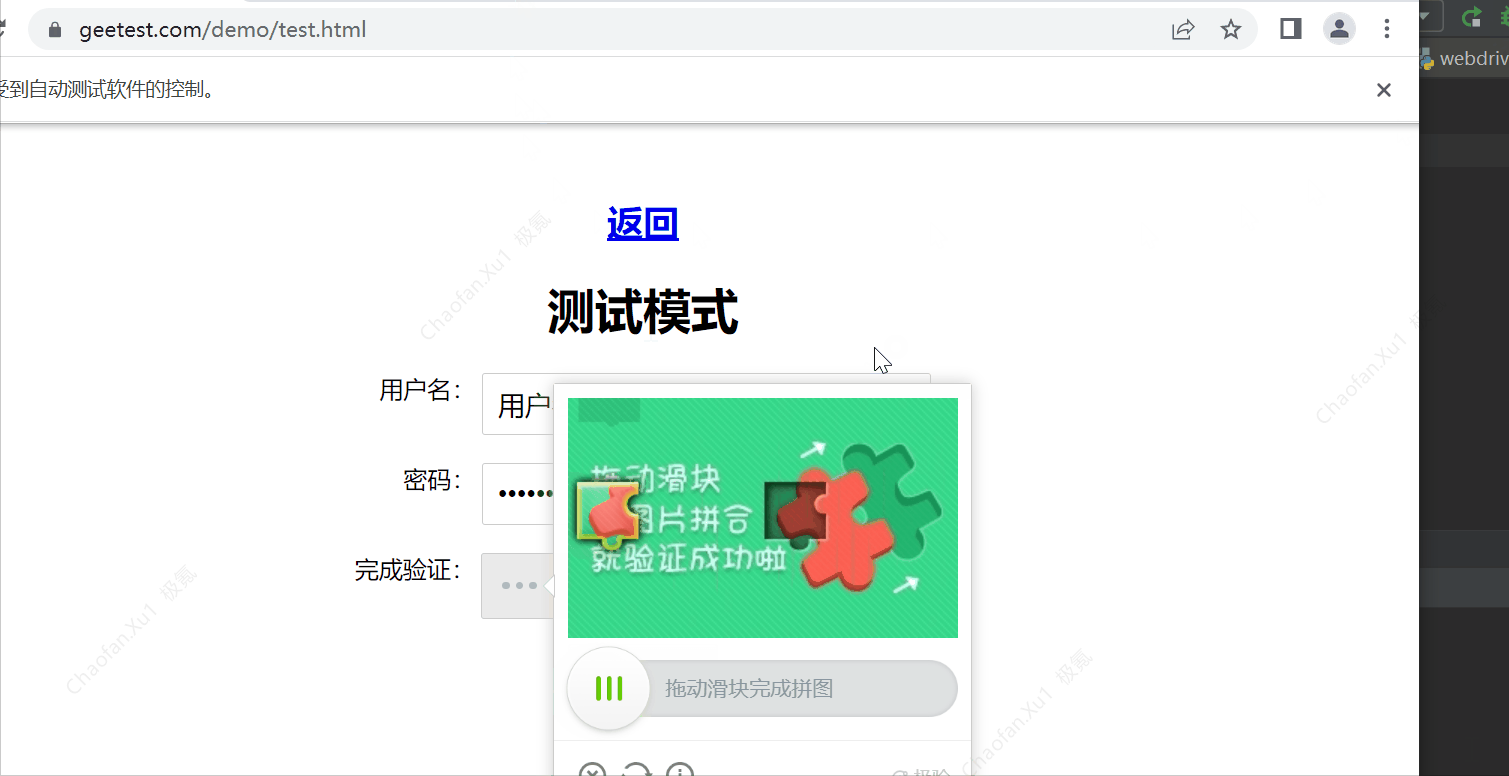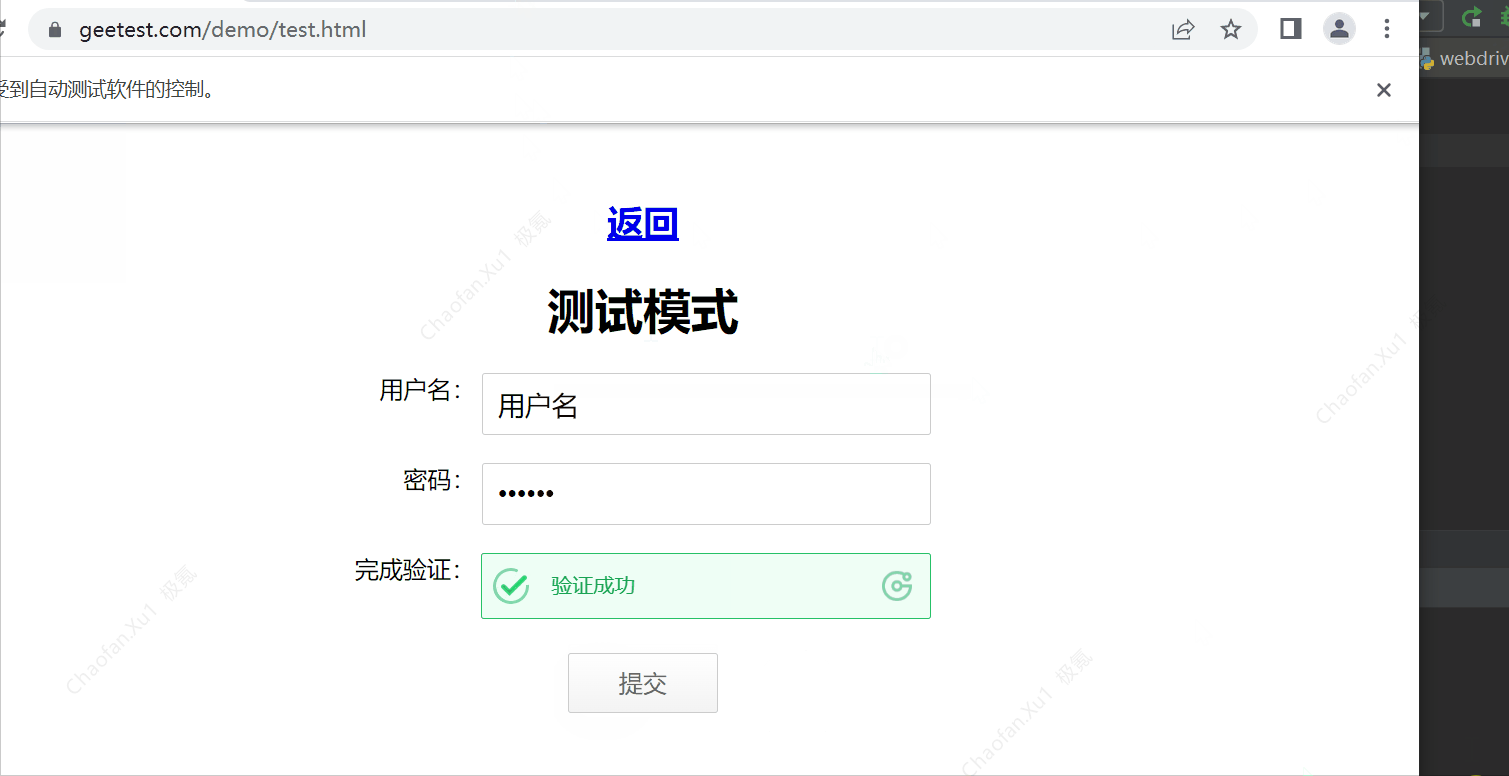
处理思路:
1.打开滑动验证页面,这个用selenium一步一步走过去
2.将滑动验证码的整个图片保存下来
3.对图片的像素点进行分析,发现拼图处像素特征如下:
1).阴影起点处rgb的第一个值为0
2).阴影处的rgb三个值相加大部分小于某个临界值(minPix=400)
3).拼图阴影大小约为40x35
基于此,设计遇到rgb第一个值为0(出于某些考虑,代码出设计为5)的情况,这对后续40x35的像素进行分析,如哦rgb相加<400,则计数.最后计数像素点符合规则的>40*35-mixCnt(容错值),则认为找到了阴影的起点.如果没找到x,则有五次机会刷新图片重找.
简易实现如下:
from time import sleep
from PIL import Image
from selenium import webdriver
from selenium.webdriver import ActionChains
from selenium.webdriver.common.by import By
driver = webdriver.Chrome()
driver.get('https://www.geetest.com/demo/test.html')
sleep(5)
img_ck = driver.find_element(by=By.XPATH, value="//div[@class='geetest_radar_tip']")
img_ck.click()
sleep(2)
def findX(rangeX=40, rangeY=35, mixPix=400, mixCnt=300):
img_save = driver.find_element(by=By.XPATH, value="//canvas[@class='geetest_canvas_bg geetest_absolute']")
a = img_save.screenshot_as_png # 截取后直接是二进制,无括号
with open("two01.png", mode="wb") as f:
f.write(a)
im = Image.open("two01.png")
for y in range(im.size[1]):
for x in range(im.size[0]):
pix = im.getpixel((x, y))
cnt = 0
if pix[0] < 5:
for i in range(0, rangeX):
for j in range(0, rangeY):
if x + i < im.size[0] and y + j < im.size[1]:
pixT = im.getpixel((x + i, y + j))
if pixT[0] + pixT[1] + pixT[2] < mixPix:
cnt = cnt + 1
if cnt > 40 * 35 - mixCnt:
return x
x = findX()
print(x)
cnt = 0
while x is None and cnt<5:
print('x not found try again '+ str(cnt))
refresh = driver.find_element(by=By.XPATH, value="//a[@class='geetest_refresh_1']")
refresh.click()
x = findX()
cnt = cnt+1
sleep(2)
ele_button = driver.find_element(by=By.XPATH, value="//div[@class='geetest_slider_button']")
ActionChains(driver).click_and_hold(ele_button).perform()
ActionChains(driver).move_by_offset(x - 5, yoffset=0).perform()
sleep(1)
ActionChains(driver).release().perform()
print('over')
while True:
sleep(1000)
版权归原作者 蔷薇思绪 所有, 如有侵权,请联系我们删除。