
内核级别的内存读写可用于绕过各类驱动保护,从而达到强制读写对端内存的目的,本人闲暇之余封装了一个驱动级的内核读写接口,使用此接口可实现对远程字节,字节集,整数,浮点数,多级偏移读写等。
项目地址:GitHub LyMemory
一款完全免费的内核级内存读写工具,可强制读写任意应用层进程内存数据,驱动工具目前支持读写整数,字节,字节集,单精度浮点数,双精度浮点数,多级偏移读写,取模块地址,分配远程内存等功能,读写效率高,速度快,兼容性好,使用时需自己签名或在测试模式下。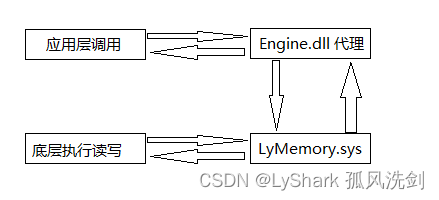
如下将简单介绍该内核读写工具各类API接口是如何调用的,鉴于驱动读写商业价值较大故暂时不放出源码(后期考虑)。
驱动读写首先要看的就是驱动支持的控制信号,如下是我封装的几个驱动控制器。
// 通用读写系列#defineIOCTL_IO_ReadProcessMemory0x801#defineIOCTL_IO_WriteProcessMemory0x802#defineIOCTL_IO_ReadDeviationIntMemory0x803#defineIOCTL_IO_WriteDeviationIntMemory0x804#defineIOCTL_IO_ReadProcessMemoryByte0x805#defineIOCTL_IO_WriteProcessMemoryByte0x806// 全局读写系列#defineIOCTL_IO_SetPIDCTL_CODE(FILE_DEVICE_UNKNOWN,0x807, METHOD_BUFFERED, FILE_ANY_ACCESS)#defineIOCTL_IO_ReadMemoryCTL_CODE(FILE_DEVICE_UNKNOWN,0x808, METHOD_BUFFERED, FILE_ANY_ACCESS)#defineIOCTL_IO_WriteMemoryCTL_CODE(FILE_DEVICE_UNKNOWN,0x809, METHOD_BUFFERED, FILE_ANY_ACCESS)// 模块操作系列#defineIOCTL_IO_GetModuleAddressCTL_CODE(FILE_DEVICE_UNKNOWN,0x810, METHOD_BUFFERED, FILE_ANY_ACCESS)#defineIOCTL_IO_GetProcessIDCTL_CODE(FILE_DEVICE_UNKNOWN,0x811, METHOD_BUFFERED, FILE_ANY_ACCESS)#defineIOCTL_IO_GetSystemRoutineAddrCTL_CODE(FILE_DEVICE_UNKNOWN,0x812, METHOD_BUFFERED, FILE_ANY_ACCESS)#defineIOCTL_IO_CreateAllocMemoryCTL_CODE(FILE_DEVICE_UNKNOWN,0x813, METHOD_BUFFERED, FILE_ANY_ACCESS)#defineIOCTL_IO_RemoveAllocMemoryCTL_CODE(FILE_DEVICE_UNKNOWN,0x814, METHOD_BUFFERED, FILE_ANY_ACCESS)// 版本升级后的新功能 2022-09-24#defineIOCTL_IO_ReadDeviationMemory0x815
内核驱动读写类库在2022年9月24日升级了功能,函数列表功能一览。
传统读写函数是每次都会附加到进程中,这种方式效率较低,但也还是可以使用的。
// 读内存字节
BYTE ReadProcessMemoryByte(DWORD Pid, ULONG64 Address)// 写内存字节
BOOL WriteProcessMemoryByte(DWORD Pid, ULONG64 Address, BYTE bytef)// 读内存32位整数型
DWORD ReadProcessMemoryInt32(DWORD Pid, ULONG64 Address)// 读内存64位整数型
DWORD ReadProcessMemoryInt64(DWORD Pid, ULONG64 Address)// 写内存32位整数型
BOOL WriteProcessMemoryInt32(DWORD Pid, ULONG64 Address, DWORD write)// 写内存64位整数型
BOOL WriteProcessMemoryInt64(DWORD Pid, ULONG64 Address, DWORD write)// 读内存单精度浮点数
FLOAT ReadProcessMemoryFloat(DWORD Pid, ULONG64 Address)// 读内存双精度浮点数
DOUBLE ReadProcessMemoryDouble(DWORD Pid, ULONG64 Address)// 写内存单精度浮点数
BOOL WriteProcessMemoryFloat(DWORD Pid, ULONG64 Address, FLOAT write)// 写内存双精度浮点数
BOOL WriteProcessMemoryDouble(DWORD Pid, ULONG64 Address, DOUBLE write)// 读多级偏移32位整数型
INT32 ReadProcessDeviationInt32(ProcessDeviationIntMemory *read_offset_struct)// 读多级偏移64位整数型
INT64 ReadProcessDeviationInt64(ProcessDeviationIntMemory *read_offset_struct)// 写多级偏移32位整数型
BOOL WriteProcessDeviationInt32(ProcessDeviationIntMemory *write_offset_struct)// 写多级偏移64位整数型
BOOL WriteProcessDeviationInt64(ProcessDeviationIntMemory *write_offset_struct)// 读多级偏移32位内存地址
DWORD ReadDeviationMemory32(ProcessDeviationMemory *read_offset_struct)// 读多级偏移64位内存地址
DWORD64 ReadDeviationMemory64(ProcessDeviationMemory *read_offset_struct)// 读多级偏移字节型
BYTE ReadDeviationByte(ProcessDeviationMemory *read_offset_struct)// 读多级偏移单精度浮点数
FLOAT ReadDeviationFloat(ProcessDeviationMemory *read_offset_struct)// 写多级偏移字节型
BOOL WriteDeviationByte(ProcessDeviationMemory *write_offset_struct,BYTE write_byte)// 写多级偏移单精度浮点数
BOOL WriteDeviationFloat(ProcessDeviationMemory *write_offset_struct,FLOAT write_float)
全局读写函数封装相对于传统驱动读写,虽然也传入PID但本质上可以
SetPid
只设置一次PID即可实现后续直接读写内存。
// 设置全局进程PID
BOOL SetPid(DWORD Pid)// 全局读内存
BOOL Read(DWORD pid, ULONG64 address, T* ret)// 全局写内存
BOOL Write(DWORD pid, ULONG64 address, T data)// 读内存DWORDvoidReadMemoryDWORD(DWORD pid, ULONG64 addre, DWORD * ret)// 读内存DWORD64voidReadMemoryDWORD64(DWORD pid, ULONG64 addre, DWORD64 * ret)// 读内存字节voidReadMemoryBytes(DWORD pid, ULONG64 addre, BYTE **ret, DWORD sizes)// 读内存浮点数voidReadMemoryFloat(DWORD pid, ULONG64 addre,float* ret)// 读内存双精度浮点数voidReadMemoryDouble(DWORD pid, ULONG64 addre,double* ret)// 写内存字节voidWriteMemoryBytes(DWORD pid, ULONG64 addre, BYTE * data, DWORD sizes)// 写内存DWORDvoidWriteMemoryDWORD(DWORD pid, ULONG64 addre, DWORD ret)// 写内存DWORD64voidWriteMemoryDWORD64(DWORD pid, ULONG64 addre, DWORD64 ret)// 写内存浮点数voidWriteMemoryFloat(DWORD pid, ULONG64 addre,float ret)// 写内存双精度浮点数voidWriteMemoryDouble(DWORD pid, ULONG64 addre,double ret)// 驱动读取进程模块基地址
DWORD64 GetModuleAddress(DWORD pid, std::string dllname)// 根据进程名称获取进程PID
DWORD GetProcessID(std::string procname)// 获取系统函数内存地址
DWORD64 GetSystemRoutineAddress(std::string funcname)// 在对端分配内存空间
DWORD64 CreateRemoteMemory(DWORD length)// 销毁对端内存
DWORD DeleteRemoteMemory(DWORD64 address, DWORD length)
内核读/写字节集: 对远端指定内存地址出读写字节集数组,该功能可用于强制代码注入等。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){// 驱动类
cDrvCtrl DriveControl;// 安装驱动
DriveControl.InstallAndRun();// 内存读字节集
BYTE buffer[8]={0};
BYTE* bufferPtr = buffer;// 读
DriveControl.ReadMemoryBytes(2564,0x7713639c,&bufferPtr,sizeof(buffer));for(int x =0; x <8; x++){printf("读取字节: 0x%x \n", buffer[x]);}// 卸载驱动
DriveControl.RemoveAndStop();system("pause");return0;}
内核读取字节集效果如下:
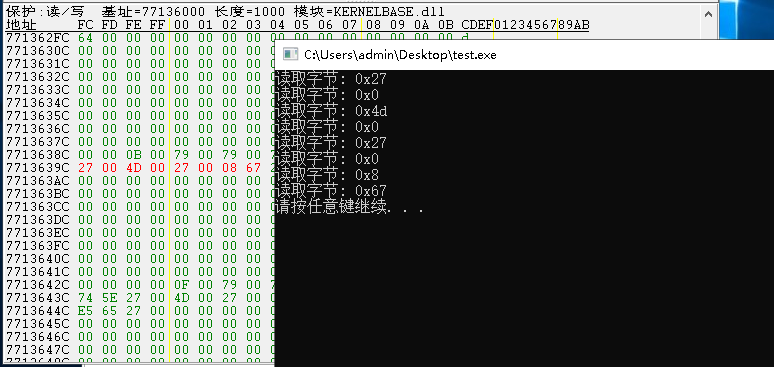
与读取对应的一个函数是写入,写入代码如下。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){// 驱动类
cDrvCtrl DriveControl;// 安装驱动
DriveControl.InstallAndRun();// 写内存字节集
BYTE writebuff[8]={0x90,0x90,0x90,0x90,0x90,0x90,0x90,0x90};
DriveControl.WriteMemoryBytes(2564,0x7713639c, writebuff,sizeof(writebuff));// 卸载驱动
DriveControl.RemoveAndStop();system("pause");return0;}
写入后再次查看内存会发现已经变更了。
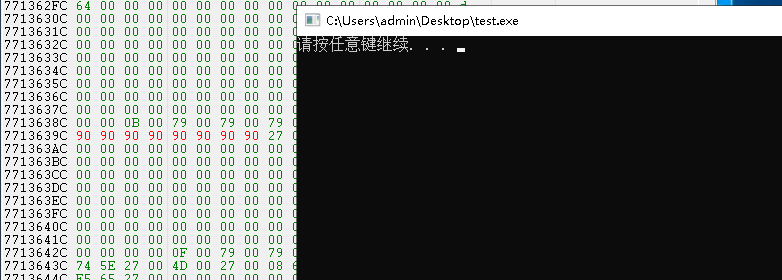
读写内核数值类型: 数值类型包括了,整数,64位整数,浮点数,双精度浮点等类型。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){// 驱动类
cDrvCtrl DriveControl;// 安装驱动
DriveControl.InstallAndRun();
DWORD data;
DWORD64 data64;
FLOAT floats;
DOUBLE doubles;// 读DWORD
DriveControl.ReadMemoryDWORD(2564,0x771362fc,&data);printf("dword = %d \n", data);// 读DWORD64
DriveControl.ReadMemoryDWORD64(2564,0x771362fc,&data64);printf("dword = %d \n", data);printf("dword = %d \n", data+4);// 读取Float
DriveControl.ReadMemoryFloat(2564,0x771362fc,&floats);printf("float = %f \n", floats);// 读double
DriveControl.ReadMemoryDouble(2564,0x771362fc,&doubles);printf("double = %f \n", doubles);// 卸载驱动
DriveControl.RemoveAndStop();system("pause");return0;}
读数值类型效果:
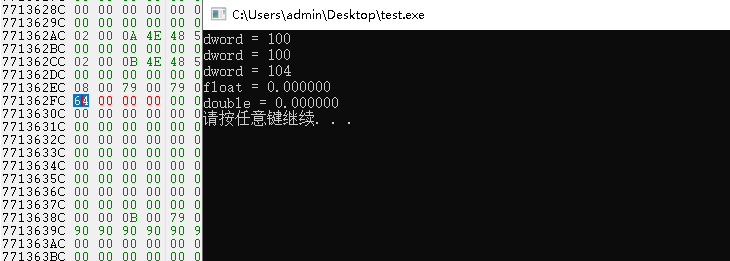
驱动写数值类型与读取类似,这里给出如何应用的案例。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){// 驱动类
cDrvCtrl DriveControl;// 安装驱动
DriveControl.InstallAndRun();
DWORD data;
DWORD64 data64;
FLOAT floats;
DOUBLE doubles;// 写DWORD
DriveControl.WriteMemoryDWORD(2564,0x771362fc,100);// 写DWORD64
DriveControl.WriteMemoryDWORD64(2564,0x771362fc,100);// 写Float
DriveControl.WriteMemoryFloat(2564,0x771362fc,10.5);// 写double
DriveControl.WriteMemoryDouble(2564,0x771362fc,100.5);// 卸载驱动
DriveControl.RemoveAndStop();system("pause");return0;}
结构体版读整数: 传递结构体解析参数读取。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){// 驱动类
cDrvCtrl DriveControl;// 安装驱动
DriveControl.InstallAndRun();// 写
ProcessIntMemory write_struct;
write_struct.pid =6348;// 指定Pid
write_struct.address =0x748c405c;// 地址
write_struct.bytes_toread =4;// 写入长度4字节
write_struct.data =999;// 写入数据
DriveControl.IoControl(0x802,&write_struct,sizeof(write_struct),0,0,0);// 读
ProcessIntMemory read_struct;
read_struct.pid =6348;// 指定Pid
read_struct.address =0x748c405c;// 地址
read_struct.bytes_toread =2;// 读取长度4字节
read_struct.data =0;// 读取的数据
DriveControl.IoControl(0x801,&read_struct,sizeof(read_struct),&read_struct,sizeof(read_struct),0);
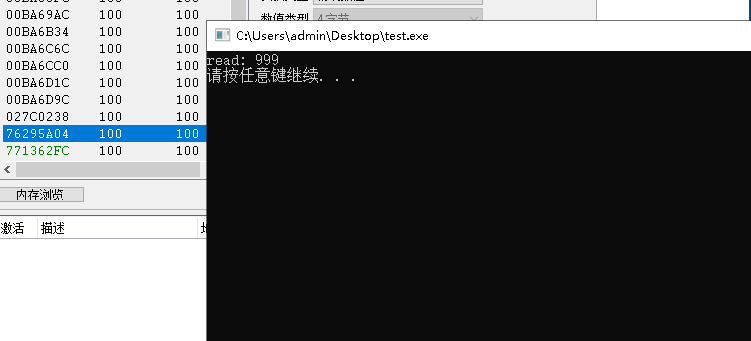
std::cout <<"read: "<<(int)read_struct.data << std::endl;// 卸载驱动
DriveControl.RemoveAndStop();system("pause");return0;}
结构版本与类内函数调用方式不同,结构板需要手动调用控制器。
结构版读写字节集: 同理与整数读写一致,需要调用控制器,传入控制信号以及结构体。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){// 驱动类
cDrvCtrl DriveControl;// 安装驱动
DriveControl.InstallAndRun();// 写
ProcessByteMemory write_byte_struct;
write_byte_struct.pid =6348;
write_byte_struct.base_address =0x76295a04;
write_byte_struct.OpCode ={0x90};
DriveControl.IoControl(0x806,&write_byte_struct,sizeof(write_byte_struct),0,0,0);// 读
ProcessByteMemory read_byte_struct;
BYTE read_byte =0;for(int x =0; x <10; x++){
read_byte_struct.pid =6348;// 指定Pid
read_byte_struct.base_address =0x76295a04+ x;// 地址
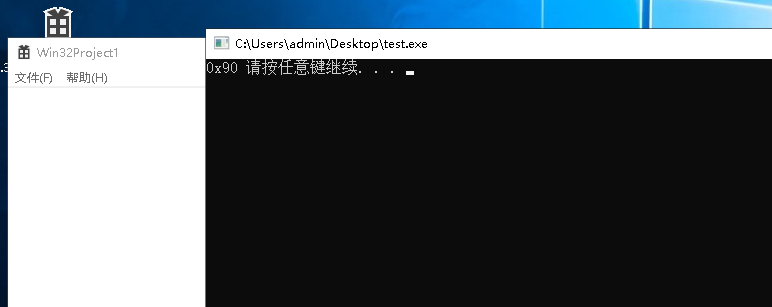
DriveControl.IoControl(0x805,&read_byte_struct,sizeof(read_byte_struct),&read_byte,sizeof(read_byte),0);if(read_byte ==0){break;}printf("0x%02X ", read_byte);}// 卸载驱动
DriveControl.RemoveAndStop();system("pause");return0;}
写入后在读取,效果如下:
结构版多级偏移读写: 针对整数型读写的封装,增加了多级偏移读写机制。读写多级偏移整数型(最大32级)
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();// 读
ProcessDeviationIntMemory read_offset_struct;
read_offset_struct.pid =1468;// 进程PID
read_offset_struct.base_address =0x601660;// 基地址
read_offset_struct.offset_len =4;// 偏移长度
read_offset_struct.data =0;// 读入的数据
read_offset_struct.offset[0]=0x18;// 一级偏移
read_offset_struct.offset[1]=0x0;// 二级偏移
read_offset_struct.offset[2]=0x14;
read_offset_struct.offset[3]=0x0c;
DriveControl.IoControl(0x803,&read_offset_struct,sizeof(read_offset_struct),&read_offset_struct,sizeof(read_offset_struct),0);
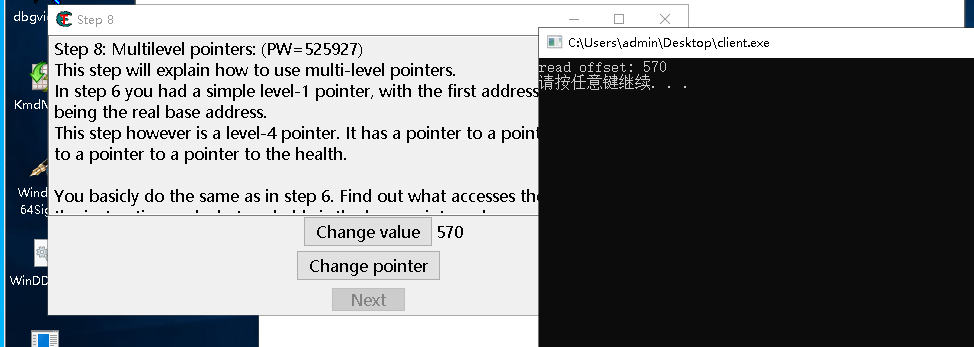
std::cout <<"read offset: "<< read_offset_struct.data << std::endl;
DriveControl.RemoveAndStop();system("pause");return0;}
读取结果:
内核读取模块基地址: 内核中强制读取指定进程中模块的基地址。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
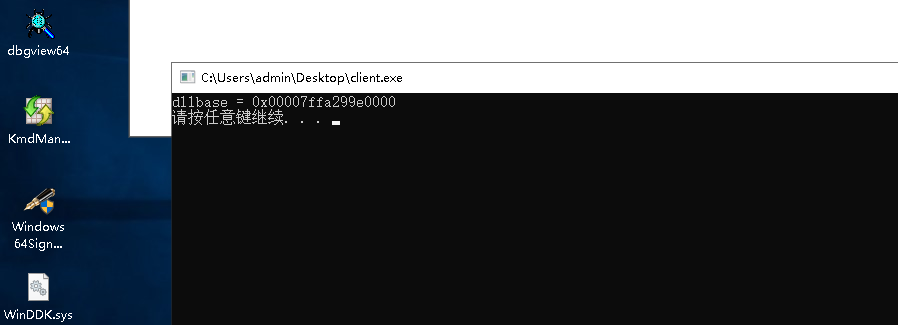
DWORD64 dllbase = DriveControl.GetModuleAddress(952,"user32.dll");printf("dllbase = 0x%016I64x \n", dllbase);
DriveControl.RemoveAndStop();system("pause");return0;}
读取效果如下:
根据进程名得到进程PID: 传入进程名,获取到该进程的PID序号。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
DWORD pid = DriveControl.GetProcessID("dbgview64.exe");printf("进程PID: %d \n", pid);
DriveControl.RemoveAndStop();system("pause");return0;}
效果如下:
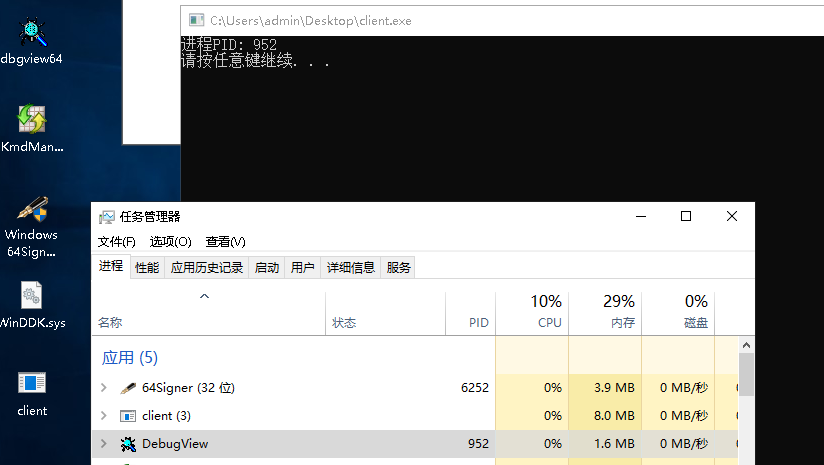
获取系统函数内存地址: 获取SSDT内核函数的内存地址。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
DWORD64 addr = DriveControl.GetSystemRoutineAddress("NtReadFile");printf("模块地址: 0x%016I64x \n", addr);
DriveControl.RemoveAndStop();system("pause");return0;}
效果如下:
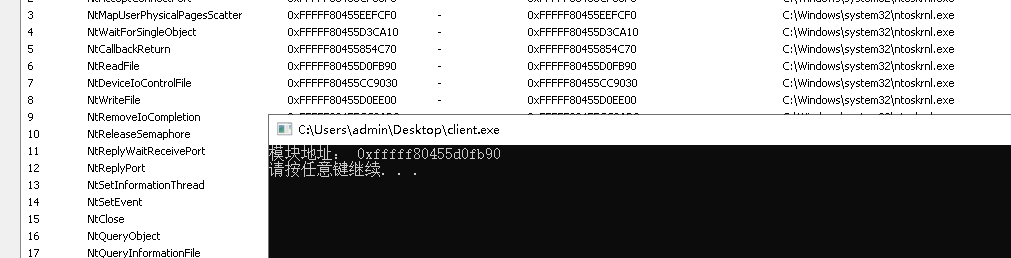
开辟释放堆空间: 在对端内存中开辟,或者释放堆空间,带有读写执行属性。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();// 设置全局PID
DriveControl.SetPid(952);// 开辟空间
DWORD64 ref = DriveControl.CreateRemoteMemory(1024);printf("create = %x \n", ref);
DWORD del_flag = DriveControl.DeleteRemoteMemory(ref,1024);printf("del flag = %d \n", del_flag);
DriveControl.RemoveAndStop();system("pause");return0;}
效果如下:
驱动级DLL注入: 注入DLL功能是驱动注入的一个功能,同样使用该控制器控制。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#pragmacomment(lib,"user32.lib")#pragmacomment(lib,"advapi32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();// 注入DLL到程序,支持32位与64位注入
DriveControl.InjectDll("dbgview64.exe","c://test1.dll");
DriveControl.RemoveAndStop();system("pause");return0;}
效果如下:
传统模式读写封装: 传统模式读写封装函数可对整数,浮点数,字节进行灵活读写。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
DWORD ref = DriveControl.ReadProcessMemoryInt32(6056,0x003AF4CC);printf("驱动读取:value = %d \n", ref);
DWORD64 dref = DriveControl.ReadProcessMemoryInt64(6056,0x003AF4CC);printf("驱动读取:value64 = %d \n", dref);
FLOAT float_ref = DriveControl.ReadProcessMemoryFloat(6056,0x01A1BC90);printf("驱动读取:value = %f \n", float_ref);
FLOAT double_ref = DriveControl.ReadProcessMemoryDouble(6056,0x01A1BC90);printf("驱动读取:value = %f \n", double_ref);
BYTE byf = DriveControl.ReadProcessMemoryByte(6056,0x01A1BC90);printf("驱动读取:value = %x \n", byf);for(size_t i =0; i <10; i++){
BYTE byf1 = DriveControl.ReadProcessMemoryByte(6056,0x01A1BC90+ i);printf("驱动读取:value = %x \n", byf1);}system("pause");return0;}
读取效果如下:
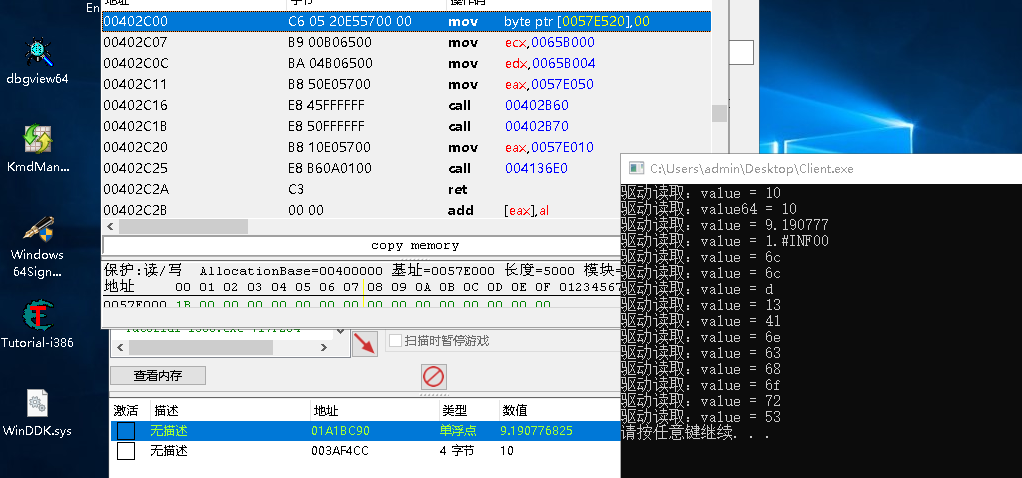
写入功能与读取一致,这里以读写整数为案例。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();// 写出9999
DriveControl.WriteProcessMemoryInt32(6056,0x003AF4CC,9999);// 读取测试
DWORD ref = DriveControl.ReadProcessMemoryInt32(6056,0x003AF4CC);printf("驱动读取:value = %d \n", ref);system("pause");return0;}
写出效果如下:
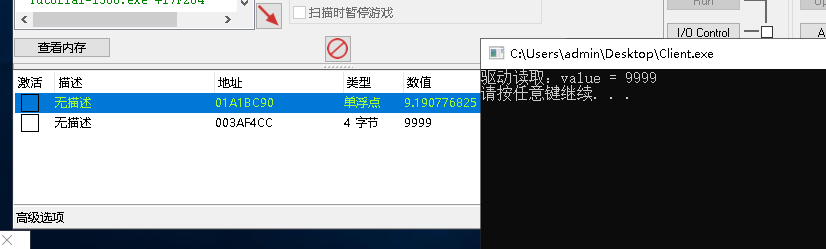
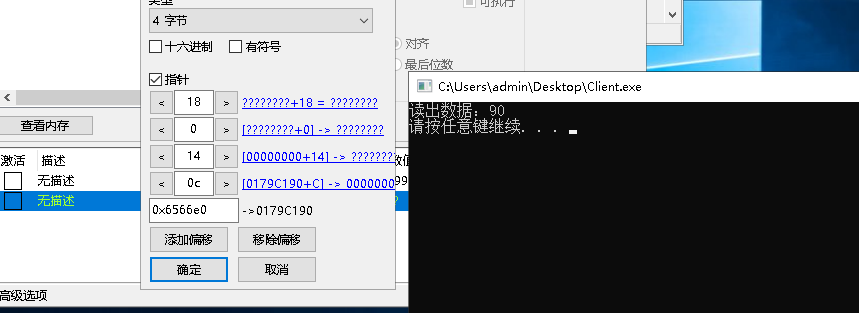
内存多级偏移读写: 此功能并不是读写偏移中的数据,而是通过基地址计算出动态地址的一个函数,后续的读写可以自定义操作。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
ProcessDeviationMemory read_offset_struct ={0};
read_offset_struct.pid =3124;// 进程PID
read_offset_struct.base_address =0x6566e0;// 基地址
read_offset_struct.offset_len =4;// 偏移长度
read_offset_struct.data =0;// 读入的数据
read_offset_struct.offset[0]=0x18;// 一级偏移
read_offset_struct.offset[1]=0x0;// 二级偏移
read_offset_struct.offset[2]=0x14;// 三级
read_offset_struct.offset[3]=0x0c;// 四级// 定位到动态地址
DWORD ref = DriveControl.ReadDeviationMemory32(&read_offset_struct);printf("计算出基地址:0x%x \n", ref);system("pause");return0;}
定位内存地址如下:
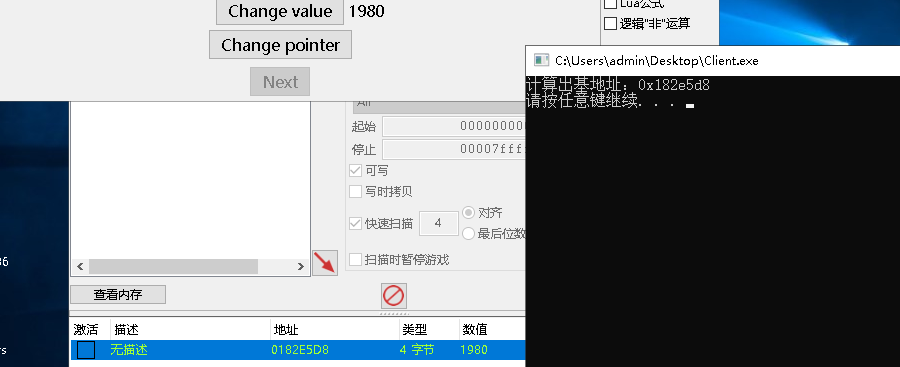
内存整数多级偏移读写: 一个简单的案例实现对内存整数型偏移读写。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();// 写入内存偏移地址
ProcessDeviationIntMemory write_offset_struct ={0};
write_offset_struct.pid =3124;// 进程PID
write_offset_struct.base_address =0x6566e0;// 基地址
write_offset_struct.offset_len =4;// 偏移长度
write_offset_struct.data =999;// 读入的数据
write_offset_struct.offset[0]=0x18;// 一级偏移
write_offset_struct.offset[1]=0x0;// 二级偏移
write_offset_struct.offset[2]=0x14;
write_offset_struct.offset[3]=0x0c;// 写出
DriveControl.WriteProcessDeviationInt32(&write_offset_struct);// 读取写入后的地址
ProcessDeviationIntMemory read_offset_struct ={0};
read_offset_struct.pid =3124;// 进程PID
read_offset_struct.base_address =0x6566e0;// 基地址
read_offset_struct.offset_len =4;// 偏移长度
read_offset_struct.data =0;// 读入的数据
read_offset_struct.offset[0]=0x18;// 一级偏移
read_offset_struct.offset[1]=0x0;// 二级偏移
read_offset_struct.offset[2]=0x14;
read_offset_struct.offset[3]=0x0c;// 读入偏移整数
DWORD ref = DriveControl.ReadProcessDeviationInt32(&read_offset_struct);printf("当前偏移内的数据:%d \n", ref);system("pause");return0;}
读写效果如下:
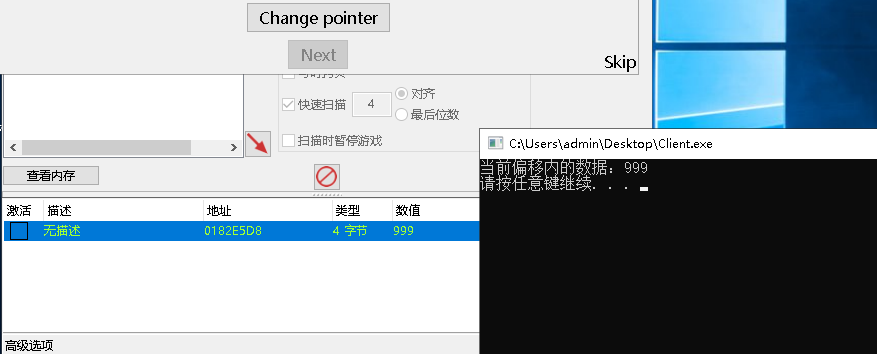
读取多级偏移字节型: 读取偏移数据内的字节数据,可循环多次读写。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
ProcessDeviationMemory read_offset_struct ={0};
read_offset_struct.pid =3124;// 进程PID
read_offset_struct.base_address =0x6566e0;// 基地址
read_offset_struct.offset_len =4;// 偏移长度
read_offset_struct.data =0;// 读入的数据
read_offset_struct.offset[0]=0x18;// 一级偏移
read_offset_struct.offset[1]=0x0;// 二级偏移
read_offset_struct.offset[2]=0x14;
read_offset_struct.offset[3]=0x0c;// 读取多级偏移字节
DWORD ref = DriveControl.ReadDeviationByte(&read_offset_struct);printf("%x \n", ref);for(size_t i =0; i <10; i++){
read_offset_struct.pid =3124;// 进程PID
read_offset_struct.base_address =0x6566e0+ i;// 基地址
read_offset_struct.offset_len =4;// 偏移长度
read_offset_struct.data =0;// 读入的数据
read_offset_struct.offset[0]=0x18;// 一级偏移
read_offset_struct.offset[1]=0x0;// 二级偏移
read_offset_struct.offset[2]=0x14;
read_offset_struct.offset[3]=0x0c;// 读取多级偏移字节
DWORD ref = DriveControl.ReadDeviationByte(&read_offset_struct);printf("%x ", ref);}system("pause");return0;}
读取效果如下:
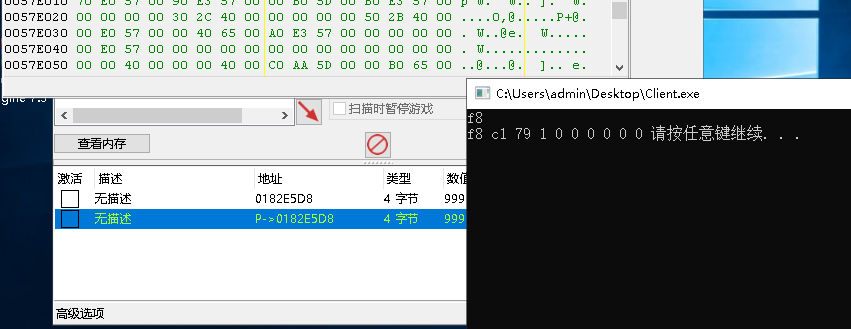
写入多级偏移字节型: 如读取一致,传入偏移,以及写出的字节即可替代目标字节。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
ProcessDeviationMemory write ={0};
write.pid =3124;// 进程PID
write.base_address =0x6566e0;// 基地址
write.offset_len =4;// 偏移长度
write.data =0;// 读入的数据
write.offset[0]=0x18;// 一级偏移
write.offset[1]=0x0;// 二级偏移
write.offset[2]=0x14;
write.offset[3]=0x0c;// 写内存字节
DriveControl.WriteDeviationByte(&write,0x90);
ProcessDeviationMemory read_offset_struct ={0};
read_offset_struct.pid =3124;// 进程PID
read_offset_struct.base_address =0x6566e0;// 基地址
read_offset_struct.offset_len =4;// 偏移长度
read_offset_struct.data =0;// 读入的数据
read_offset_struct.offset[0]=0x18;// 一级偏移
read_offset_struct.offset[1]=0x0;// 二级偏移
read_offset_struct.offset[2]=0x14;
read_offset_struct.offset[3]=0x0c;// 读取多级偏移字节
BYTE ref = DriveControl.ReadDeviationByte(&read_offset_struct);printf("读出数据:%x \n", ref);system("pause");return0;}
写出后,原始指针失效:
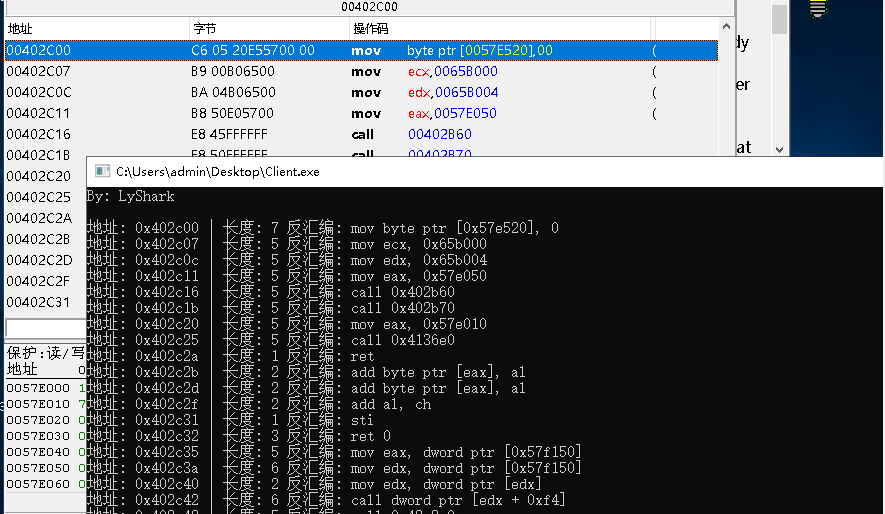
读取字节并反汇编: 运用反汇编引擎可实现对读出字节反汇编输出。
#define_CRT_SECURE_NO_WARNINGS#include<iostream>#include<Windows.h>#include<LyMemoryKernel.h>#include<inttypes.h>#include<capstone/capstone.h>#pragmacomment(lib,"capstone32.lib")intmain(int argc,char*argv[]){
cDrvCtrl DriveControl;
DriveControl.InstallAndRun();
BYTE arr[1024]={0};for(size_t i =0; i <1023; i++){
BYTE by = DriveControl.ReadProcessMemoryByte(3344,0x402c00+ i);
arr[i]= by;}
csh handle;
cs_insn *insn;size_t count;int size =1023;printf("By: LyShark \n\n");// 打开句柄if(cs_open(CS_ARCH_X86, CS_MODE_32,&handle)!= CS_ERR_OK){return0;}// 反汇编代码,地址从0x1000开始,返回总条数
count =cs_disasm(handle,(unsignedchar*)arr, size,0x402c00,0,&insn);if(count >0){size_t index;for(index =0; index < count; index++){for(int x =0; x < insn[index].size; x++){// printf("机器码: %d -> %02X \n", x, insn[index].bytes[x]);}printf("地址: 0x%"PRIx64" | 长度: %d 反汇编: %s %s \n", insn[index].address, insn[index].size, insn[index].mnemonic, insn[index].op_str);}cs_free(insn, count);}else{printf("反汇编返回长度为空 \n");}cs_close(&handle);system("pause");return0;}
反汇编效果:
版权归原作者 孤风洗剑 所有, 如有侵权,请联系我们删除。