仅做学习交流,如有侵犯联系必删。
目录
前言
一篇酷狗app安卓逆向的文章,难度适中。
样本: 酷狗app v10.8.8
工具: jadx、Pixel3 安卓10、frida、charles
小伙伴可以跟着一起做做
提示:以下是本篇文章正文内容,下面案例可供参考
一、抓包待分析参数
1.1 charles抓包-音乐评论接口
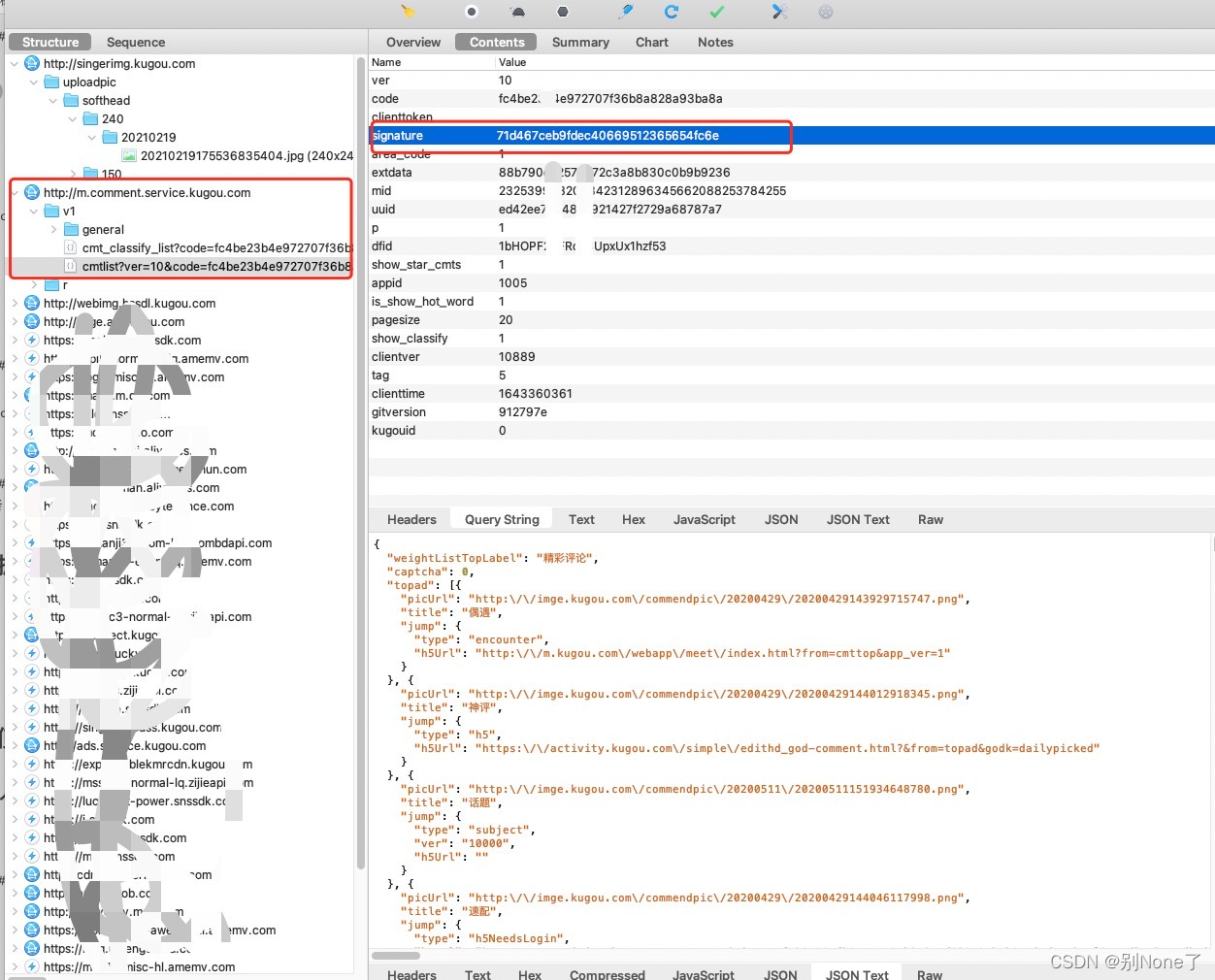
可以看到signature参数,用apipost模拟请求下试试
1.2 模拟请求

1.3 查壳
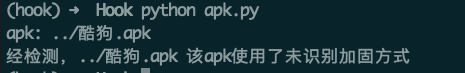
二、分析
2.1 packageName

package=“com.kugou.android” 接下来hook需要用到
2.2 搜索关键词

hashMap.put(“signature”,com.kugou.android.ads.feev4.a.a(sb.toString())); 相当可疑了 我们点进去看下

代码如下
publicstatic Map<String, Object>a(Context context, JSONObject jSONObject){
HashMap hashMap =newHashMap();
hashMap.put("dfid", com.kugou.common.q.b.a().dq());
hashMap.put("appid", com.kugou.android.b.c.d());
hashMap.put("mid", br.j(context));
hashMap.put("uuid", com.kugou.common.q.b.a().ak());
hashMap.put("clientver", Integer.valueOf(d.a(context)));
hashMap.put("clienttime", Long.valueOf(System.currentTimeMillis()/1000));
String a2 = com.kugou.android.ads.feev4.a.a(hashMap);
StringBuilder sb =newStringBuilder();
sb.append(a2);
sb.append(jSONObject == null ?"": jSONObject.toString());
hashMap.put("signature", com.kugou.android.ads.feev4.a.a(sb.toString()));return hashMap;}
可以看到定义hashMap put(“dfid”) put(“appid”)等等
String a2 = com.kugou.android.ads.feev4.a.a(hashMap);
StringBuilder.append(a2),
hook下a2的值
2.3 a2追踪hook
com.kugou.android.ads.feev4.a.a(hashMap);
jadx代码如下:
publicstatic String a(Map<String, Object> map){if(map == null || map.isEmpty()){return"";}
ArrayList<String> arrayList =newArrayList(map.keySet());
Collections.sort(arrayList);
StringBuilder sb =newStringBuilder();for(String str : arrayList){if(!TextUtils.isEmpty(str)){
sb.append(str);
sb.append(ContainerUtils.KEY_VALUE_DELIMITER);
sb.append(map.get(str));}}return sb.toString();}
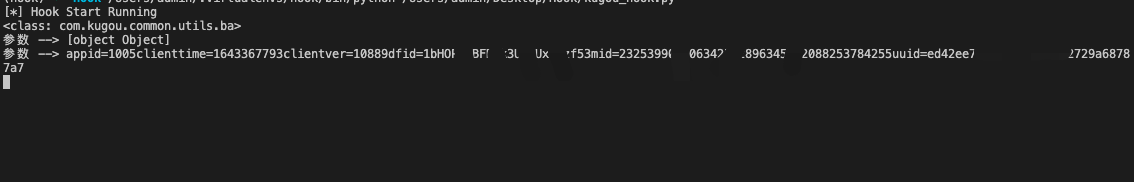
参数 --> [object Object]
参数 --> appid=1005clienttime=秒级时间戳clientver=10889dfid=xxmid=xxuuid=xx
hook代码如下:
import frida, sys
def on_message(message, data):if message['type']=='send':print("[*] {0}".format(message['payload']))else:print(message)
jscode_hook ="""
Java.perform(function(){
var a2_class = Java.use("com.kugou.android.ads.feev4.a")
a2_class.a.overload('java.util.Map').implementation = function (m){
console.log("参数 --> "+m)
var result = this.a(m)
console.log("参数 --> "+result1)return result
}})"""
process = frida.get_usb_device().attach('com.kugou.android')
script = process.create_script(jscode_hook)
script.on('message', on_message)print('[*] Hook Start Running')
script.load()
sys.stdin.read()
a2 = "appid=1005clienttime=秒级时间戳clientver=10889dfid=xxmid=xxuuid=xx"
接着往下分析 hashMap.put(“signature”, com.kugou.android.ads.feev4.a.a(sb.toString()));点进去看下a()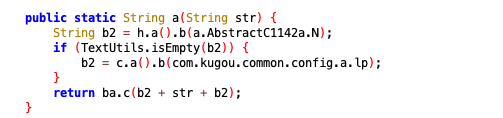
2.4 b2追踪hook
String b2 = h.a().b(a.AbstractC1142a.N);
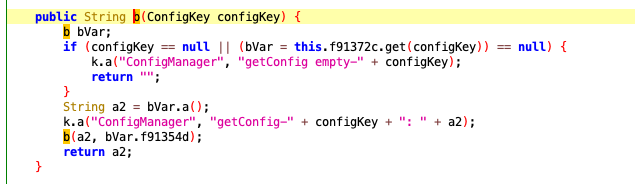
返回了b2的值 hook看看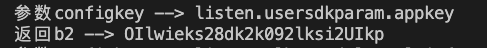
b2 = “OIlwieks28dk2k092lksi2UIkp”
return ba.c(b2 + str + b2);
2.5 hook 加密函数
hook代码如下:
import frida, sys
def on_message(message, data):if message['type']=='send':print("[*] {0}".format(message['payload']))else:print(message)
jscode_hook ="""
Java.perform(function(){
var sign_class = Java.use("com.kugou.common.utils.ba");
console.log(sign_class);if(sign_class != undefined){
sign_class.b.overload('java.lang.String').implementation = function (str){
console.log("参数: ==> : "+ str);
var res = sign_class.b(str);
console.log("解密结果: ==> "+ res);return res;}}})"""
process = frida.get_usb_device().attach('com.kugou.android')
script = process.create_script(jscode_hook)
script.on('message', on_message)print('[*] Hook Start Running')
script.load()
sys.stdin.read()
hook结果:
params: OIlwieks28dk2k092lksi2UIkpappid=1005clienttime=1643368936clientver=10889dfid=1bHOPF2BFRqk3UpxUx1hzf53mid=232539908206342312896345662088253784255uuid=ed42ee74c48dd921427f2729a68787a7{“plat”:0,“channel”:“287”,“operator”:7,“networktype”:2,“userid”:0,“vip_type”:65530,“m_type”:0,“tags”:"{}",“device”:{“phonebrand”:“google”,“sysmodel”:“Pixel%203”,“osversion”:“10”,“boot_time”:“ae3d80cd-0450-415a-ab64-814b54c1dd6e”,“os_update_time”:“441644.63333339”,“width”:1080,“height”:2028},“song”:{“hash”:“ce388811b08b3327c388e2b0ed1f2d30”,“albumid”:0,“album_audio_id”:339101224},“mode”:“normal”}OIlwieks28dk2k092lksi2UIkp
结果: ca66b35e1581e9494f52cbec986816eb 32位 试下是不是md5
运气很好signature是参数进行拼接处理后的md5结果
总结
大家感兴趣的可以跟着做下
代码就不放了准备过年啦
祝小伙伴们虎年虎虎生威
版权归原作者 别None了 所有, 如有侵权,请联系我们删除。
