配套系列教学视频链接:
安卓系列教程之ROM系统开发-百问100ask
说明
系统:Android10.0
设备: FireFly RK3399 (ROC-RK3399-PC-PLUS)
前言
本章节重点介绍在Android源码中如何编译selinux模块, 以及如何查看编译日志
一, selinux编译方法
修改了*.te,可以选择模块编译,也可以全编译。
make selinux_policy
编译system/sepolicy/Android.mk中selinux_policy目标, 基本上也将Android.mk中大部分目标都编译了
mmma system/sepolicy
针对system/sepolicy/Android.mk所有目标文件进行编译
make precompiled_sepolicy
编译最终二进制文件precompiled_sepolicy,生成在
$(OUT_TARGET)/vendor/etc/selinux/precompiled_sepolicy
或者:$(OUT_TARGET)/odm/etc/selinux/precompiled_sepolicy
替换到板子即可
查看verbose日志
./prebuilts/build-tools/linux-x86/bin/ninja -v -f out/combined-rk3399_roc_pc_plus.ninja selinux_policy
日志会显示很多内容
操作例子:修改 device/rockchip/common/sepolicy/vendor/genfs_contexts
rk3399
genfscon sysfs /devices/platform/fe330000.sdhci u:object_r:sysfs_mmc:s0
genfscon sysfs /devices/platform/fe43000.sdhci u:object_r:sysfs_mmc:s0
修改完成之后,就可以执行make selinux_policy来编译
该命令默认终端不会输出太多显示日志, 可以查看verbose文件: vim out/verbose.log.gz,以下日志只是摘抄一部分日志:
[537/608] /bin/bash -c "m4 --fatal-warnings -D mls_num_sens=1 -D mls_num_cats=1024 -D target_build_variant=userdebug -D target_with_dexpreopt=true -D target_arch=arm64 -D target_with_asan=false -D target_with_native_coverage=false -D target_full_treble=true -D target_compatible_property=true -D target_exclude_build_test= -s system/sepolicy/reqd_mask/security_classes system/sepolicy/reqd_mask/initial_sids system/sepolicy/reqd_mask/access_vectors system/sepolicy/reqd_mask/mls_macros system/sepolicy/reqd_mask/mls_decl system/sepolicy/reqd_mask/mls system/sepolicy/reqd_mask/reqd_mask.te system/sepolicy/reqd_mask/roles_decl system/sepolicy/reqd_mask/roles system/sepolicy/reqd_mask/users system/sepolicy/reqd_mask/initial_sid_contexts > out/target/product/rk3399_roc_pc_plus/obj/ETC/sepolicy_neverallows_intermediates/reqd_policy_mask.conf"
[538/608] /bin/bash -c "ASAN_OPTIONS=detect_leaks=0 out/host/linux-x86/bin/checkpolicy -C -M -c 30 -o out/target/product/rk3399_roc_pc_plus/obj/ETC/sepolicy_neverallows_intermediates/reqd_policy_mask.cil
以上日志,可以参考上一章节简介编译流程,来看日志。
二, sepoliy文件编译的逻辑
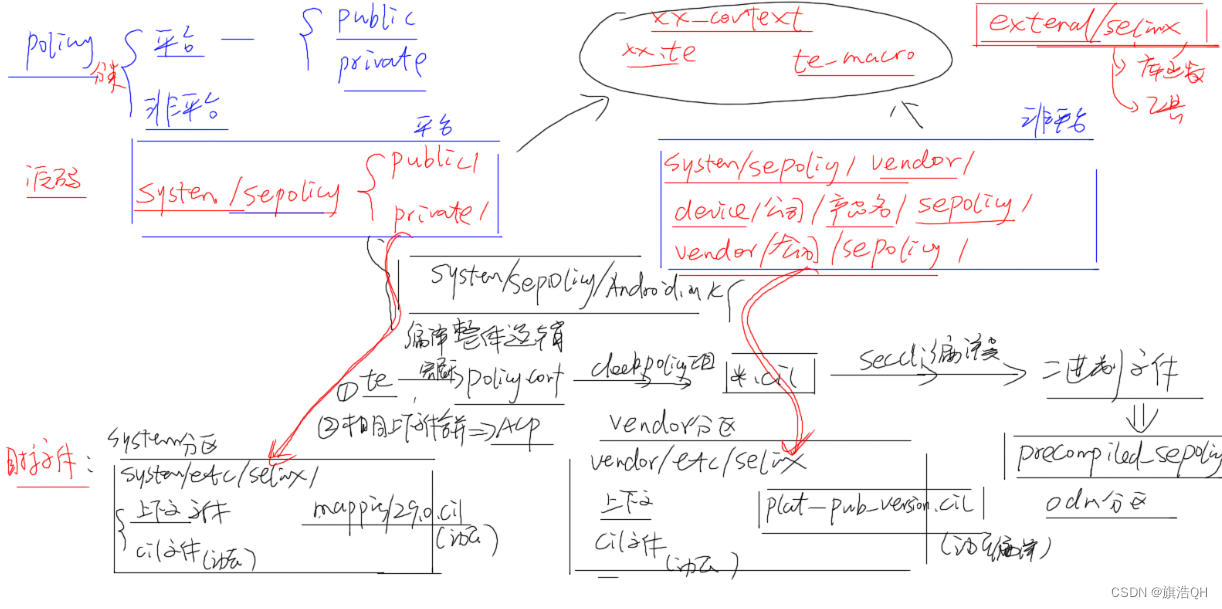
以上逻辑就是:平台的相关策略文件会被编译到system分区中的etc/selinux中, 非平台的策略文件会被编译到vendor, odm分区中的etc/selinux中。
三, 编译出来的中间文件
编译的时候, 会产生中间文件和目录, 通过查看中间文件目录里面的xx.tmp文件就知道最终目标是由那些源文件合并而来。如
out/target/product/rk3399_roc_pc_plus/obj/ETC/plat_file_contexts_intermediates/plat_file_contexts.tmp
#line 1 "system/sepolicy/private/file_contexts"
###########################################Root
/ u:object_r:rootfs:s0
Data files
/adb_keys u:object_r:adb_keys_file:s0
/build.prop u:object_r:rootfs:s0
/default.prop u:object_r:rootfs:s0
/fstab..* u:object_r:rootfs:s0
/init..* u:object_r:rootfs:s0
/res(/.)? u:object_r:rootfs:s0
/selinux_version u:object_r:rootfs:s0
/ueventd.. u:object_r:rootfs:s0
/verity_key u:object_r:rootfs:s0
.......#line 1 "device/rockchip/common/sepolicy/private/file_contexts"
file in /system
/system/bin/move_widevine_data.sh u:object_r:move-widevine-data-sh_exec:s0
#line 1 "out/target/product/rk3399_roc_pc_plus/obj/ETC/sectxfile_nl_intermediates/sectxfile_nl"#line 1 "system/sepolicy/private/file_contexts_overlayfs"
#############################Overlayfs support directories for userdebug/eng devices
/cache/overlay/(system|product)/upper u:object_r:system_file:s0
/cache/overlay/(vendor|odm)/upper u:object_r:vendor_file:s0
/cache/overlay/oem/upper u:object_r:vendor_file:s0
平台上下文中间文件:
ls out/target/product/rk3399_roc_pc_plus/obj/ETC/plat_
plat_file_contexts_intermediates/ plat_pub_versioned.cil_intermediates/
plat_file_contexts.recovery_intermediates/ plat_seapp_contexts_intermediates/
plat_hwservice_contexts_intermediates/ plat_seapp_neverallows_intermediates/
plat_mac_permissions.xml_intermediates/ plat_sepolicy_and_mapping.sha256_intermediates/
plat_mapping_file_intermediates/ plat_sepolicy.cil_intermediates/
plat_property_contexts_intermediates/ plat_sepolicy_vers.txt_intermediates/
plat_property_contexts.recovery_intermediates/ plat_service_contexts_intermediates/
厂商上下文中间文件:
ls out/target/product/rk3399_roc_pc_plus/obj/ETC/vendor_
vendor_file_contexts_intermediates/ vendor_property_contexts_intermediates/
vendor_file_contexts.recovery_intermediates/ vendor_property_contexts.recovery_intermediates/
vendor_hwservice_contexts_intermediates/ vendor_seapp_contexts_intermediates/
vendor_mac_permissions.xml_intermediates/ vendor_sepolicy.cil_intermediates/
生成的中间policy.conf文件:
find ./out/target/product/rk3399_roc_pc_plus/obj/ETC/ -name "*policy.conf"
./out/target/product/rk3399_roc_pc_plus/obj/ETC/treble_sepolicy_tests_26.0_intermediates/26.0_plat_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/general_sepolicy.conf_intermediates/general_sepolicy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/treble_sepolicy_tests_28.0_intermediates/28.0_plat_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/vendor_sepolicy.cil_intermediates/vendor_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/treble_sepolicy_tests_27.0_intermediates/27.0_plat_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/plat_sepolicy.cil_intermediates/plat_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/userdebug_plat_sepolicy.cil_intermediates/userdebug_plat_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/built_plat_sepolicy_intermediates/base_plat_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/built_plat_sepolicy_intermediates/base_plat_pub_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/sepolicy_neverallows_intermediates/plat_pub_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/sepolicy_neverallows_intermediates/pub_policy.conf
./out/target/product/rk3399_roc_pc_plus/obj/ETC/sepolicy_neverallows_intermediates/policy.conf
四, 编译出来的目标文件
平台分区安全策略目标文件
ls out/target/product/rk3399_roc_pc_plus/system/etc/selinux/
mapping #用于向后兼容的映射文件,源码也是cil类型, 最终会被用于动态编译
plat_mac_permissions.xml
plat_sepolicy_and_mapping.sha256
plat_file_contexts
plat_property_contexts
plat_sepolicy.cil #平台私有和公共的所有策略文件, 最终会被用于动态编译
plat_hwservice_contexts
plat_seapp_contexts
plat_service_contexts
Vendor分区安全策略目标文件:
ls out/target/product/rk3399_roc_pc_plus/product/etc/selinux/
plat_pub_versioned.cil #平台公共的type和attribut映射到vendor版本的类型和属性如typeattribute dev_type
# typeattributeset dev_type (device_29_0 audio_device_29_0 ...)vendor_hwservice_contexts
vendor_sepolicy.cil #vendor的公共和私有的所有策略文爱九年, 最终会被用于动态编译
plat_sepolicy_vers.txt #用于指示当前vendor 策略文件的版本
vendor_mac_permissions.xml
vndservice_contexts
selinux_denial_metadata
vendor_property_contexts
vendor_file_contexts
vendor_seapp_contexts
odm分区安全策略目标文件:
ls out/target/product/rk3399_roc_pc_plus/odm/etc/selinux/
precompiled_sepolicy //最终的二进制文件-会写入到内核中
precompiled_sepolicy.plat_sepolicy_and_mapping.sha256
precompiled_sepolicy.product_sepolicy_and_mapping.sha256
版权归原作者 旗浩QH 所有, 如有侵权,请联系我们删除。