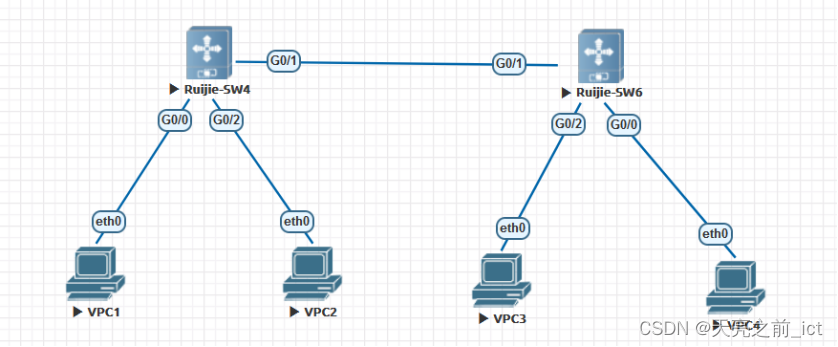
1、PC1的IP地址和mac地址做全局静态ARP绑定;
全局下:address-bind 192.168.1.1 mac(pc1)
G0/2:ip verify source port-security
arp-check
2、PC2的IP地址和MAC地址做全局IP+MAC绑定:
Address-bind 192.168.1.2 0050.7966.6807
Address-bind uplink g0/1
Address-bind binding-filter logging
Address-bind install
3、PC3所在的端口,做三层端口安全,且发现违例报文后将端口关闭,并发送trap消息﹔
G0/2:switchport port-security mac-address 144f.d7c0.79c3 vlan X 192.168.3.1
switchport port-security violation restrict
switchport port-security violation shutdown
4、PC4通过DHCP获取IP地址,通过配置实现防止终端私设IP地址和非法DHCP服务器接入的需求;
全局:IP DHCP snooping
上联dhcp服务器的接口:ip dhcp snooping trust
G0/0:ip verify source port-security
5、L1和L2连接终端的接口,全部启用单端口防环,违例动作为block端口,5分钟后自动恢复;
首先全局下开启rldp enable
所有连终端的端口:rldp port loop-detect block
errdisable recover interval 300
6、L1和L2全部接入终端的接口,启用防ARP欺骗功能和防网关ARP欺骗功能。
IP DHCP snooping已配置
所有连终端端口:anti-arp-spoofing ip 网关ip//防网关arp欺骗
Arp check//防arp欺骗
ip verify source port-security //ip source guard
版权归原作者 天亮之前_ict 所有, 如有侵权,请联系我们删除。