1、响应头缺失
HTTP X-Permitted-Cross-Domain-Policies 响应头缺失
Nginx的nginx.conf中location下配置:
add_header X-Permitted-Cross-Domain-Policies value;
HTTP Referrer-Policy 响应头缺失
Nginx的nginx.conf中location下配置:
add_header 'Referrer-Policy' 'origin';
HTTP X-Content-Type-Options 响应头缺失
Nginx的nginx.conf中location下配置:
add_header X-Content-Type-Options nosniff;
HTTP X-Download-Options 响应头缺失
Nginx的nginx.conf中location下配置:
add_header X-Download-Options "noopen" always;
HTTP Content-Security-Policy 响应头缺失
Nginx的nginx.conf中location下配置:
add_header Content-Security-Policy "default-src 'self' * 'unsafe-inline' 'unsafe-eval' blob: data: ;";
点击劫持:缺少 X-Frame-Options 头
Nginx的nginx.conf中location下配置:
add_header X-Frame-Options SAMEORIGIN;
HTTP X-XSS-Protection 响应头缺失
Nginx的nginx.conf中location下配置:
add_header X-XSS-Protection 1;
2、set-cookies 属性缺失
set-Cookie 没有设置 secure 、HttpOnly属性
nginx.conf location 根据项目路径配置(实际就是把/替换为/; Secure; HttpOnly)
proxy_cookie_path / "/; Secure; HttpOnly";
负载也会产生一条set-cookies信息,upstream route后加上Secure HttpOnly
upstream portal{
sticky path=/hh name=hh_route Secure HttpOnly;
3、CSRF跨站域请求伪造攻击
控制referer来源,例如非192.168.41网段地址返回403错误
nginx.conf server 下配置
valid_referers none server_names 192.168.41.*;
if ($invalid_referer) {
return 403;
}
4、不安全的http请求方式漏洞
例如只允许get post请求,其他返回403
nginx.conf location 添加
if ($request_method !~* GET|POST) {
return 403;
}
5、版本号信息隐藏
nginx版本号信息隐藏
nginx.conf http 添加
server_tokens off;
应用服务版本号信息隐藏
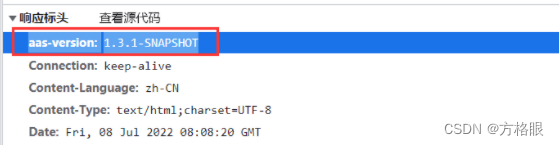
nginx.conf location 设置
proxy_hide_header aas-version;
** 6、请求头控制web访问**
例如只允许手机访问,则请求头Windows、Macintosh,直接返回404
nginx location 配置
set $flag 0;
if ($http_user_agent ~* "Windows" ) {
set $flag "1";
}
if ($http_user_agent ~* "Macintosh" ) {
set $flag "1";
}
if ($flag = "1"){
return 404;
}
版权归原作者 方格眼 所有, 如有侵权,请联系我们删除。