第一题:爬虫协议
1.1 题目描述:
小兰同学在开发网站时了解到一个爬虫协议,该协议指网站可建立一个特别的txt文件来告诉搜索引擎哪些页面可以抓取,哪些不可以抓取,而搜索引擎则通过读取该txt文件来识别这个页面是否允许被抓取,爬虫协议并不是一个规范而只是约定俗成的,所以不能保证网站的隐私。
1.2 题目界面:
打开题目网址
1.3 解题步骤:
1):尝试访问robots.txt文件
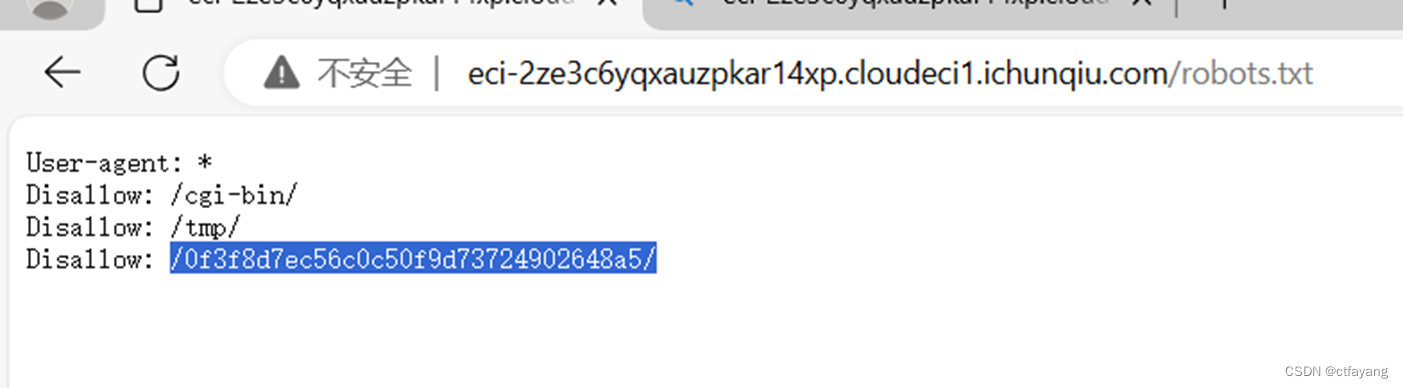
2):尝试访问0f3f8d7ec56c0c50f9d73724902648a5
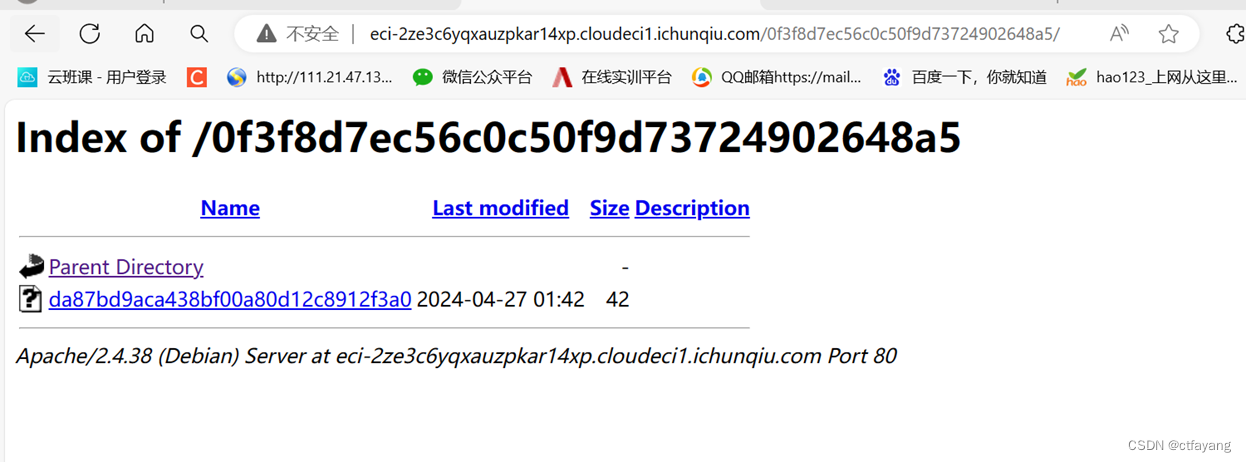
3):尝试访问0f3f8d7ec56c0c50f9d73724902648a5/da87bd9aca438bf00a80d12c8912f3a0
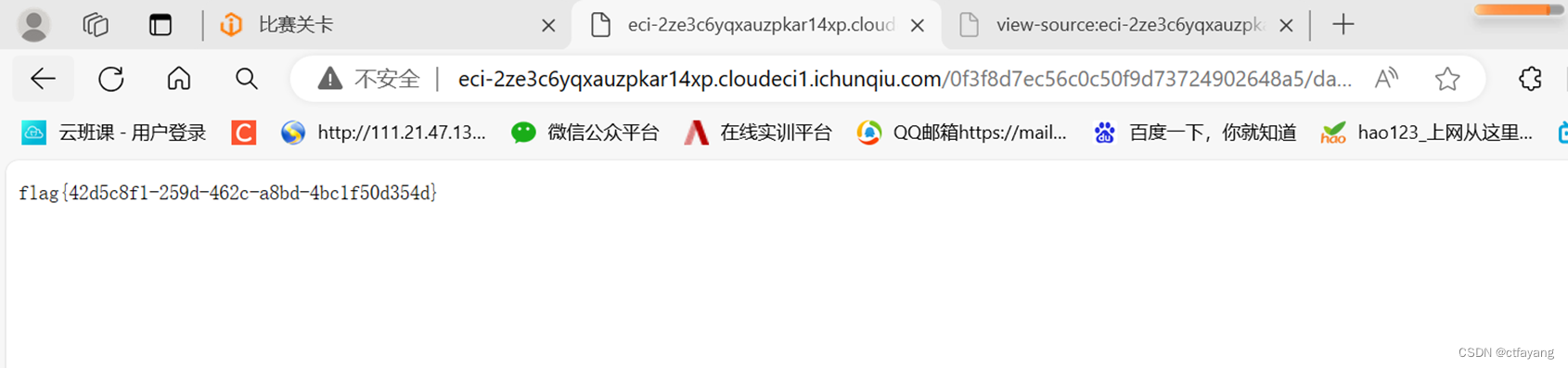
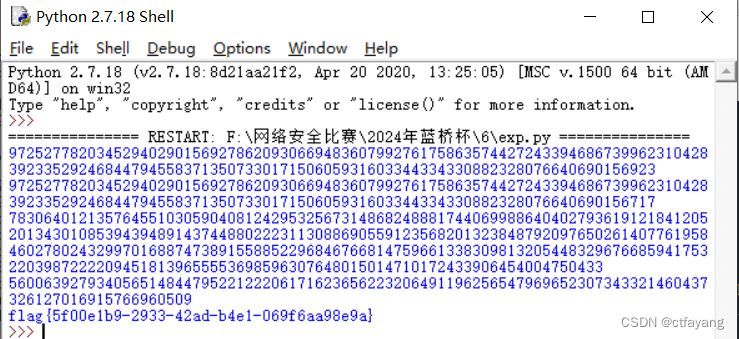
4):得到flag{42d5c8f1-259d-462c-a8bd-4bc1f50d354d}
第二题:流量分析
2.1 解题步骤:
1):用wireshark打开题目所给文件
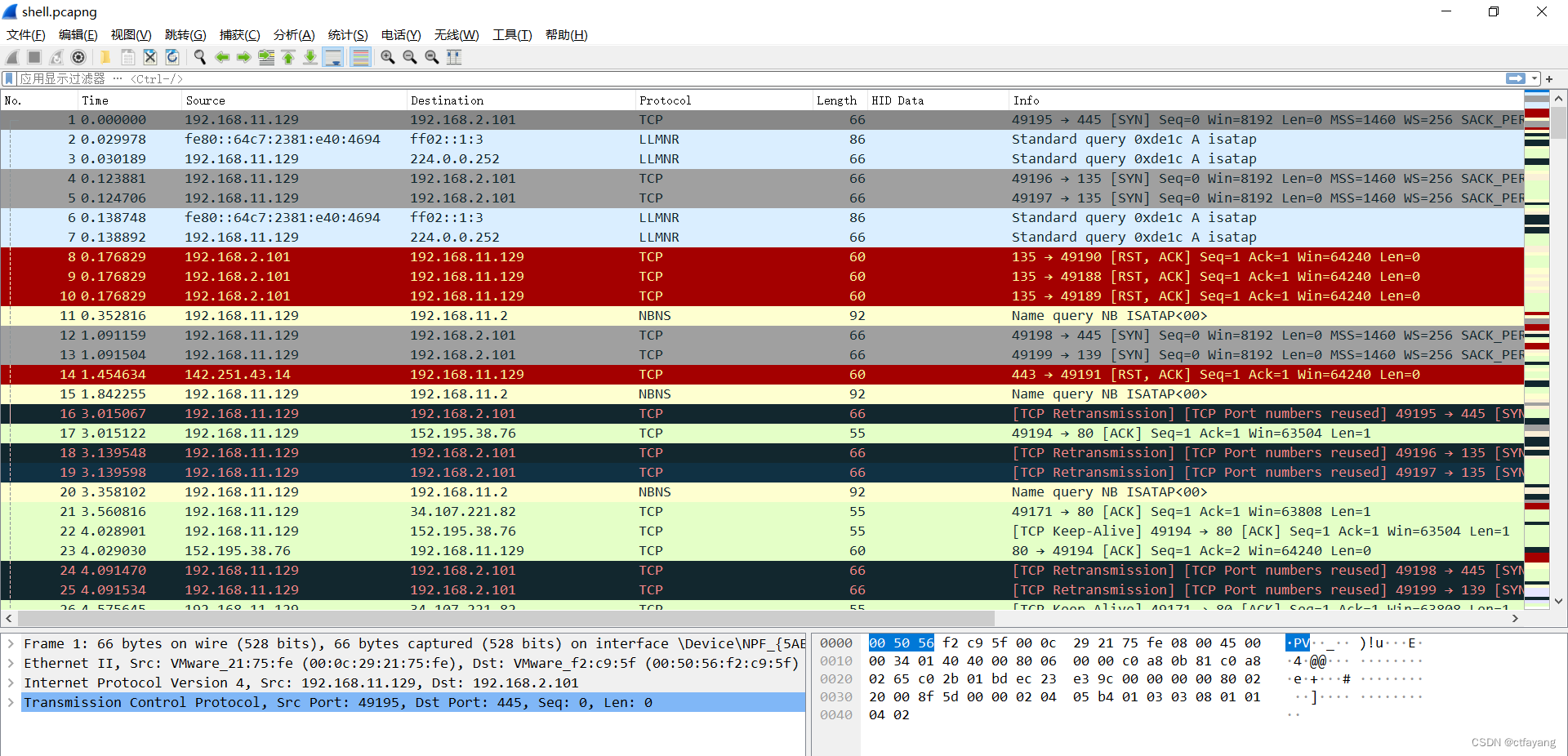
2):导出对象
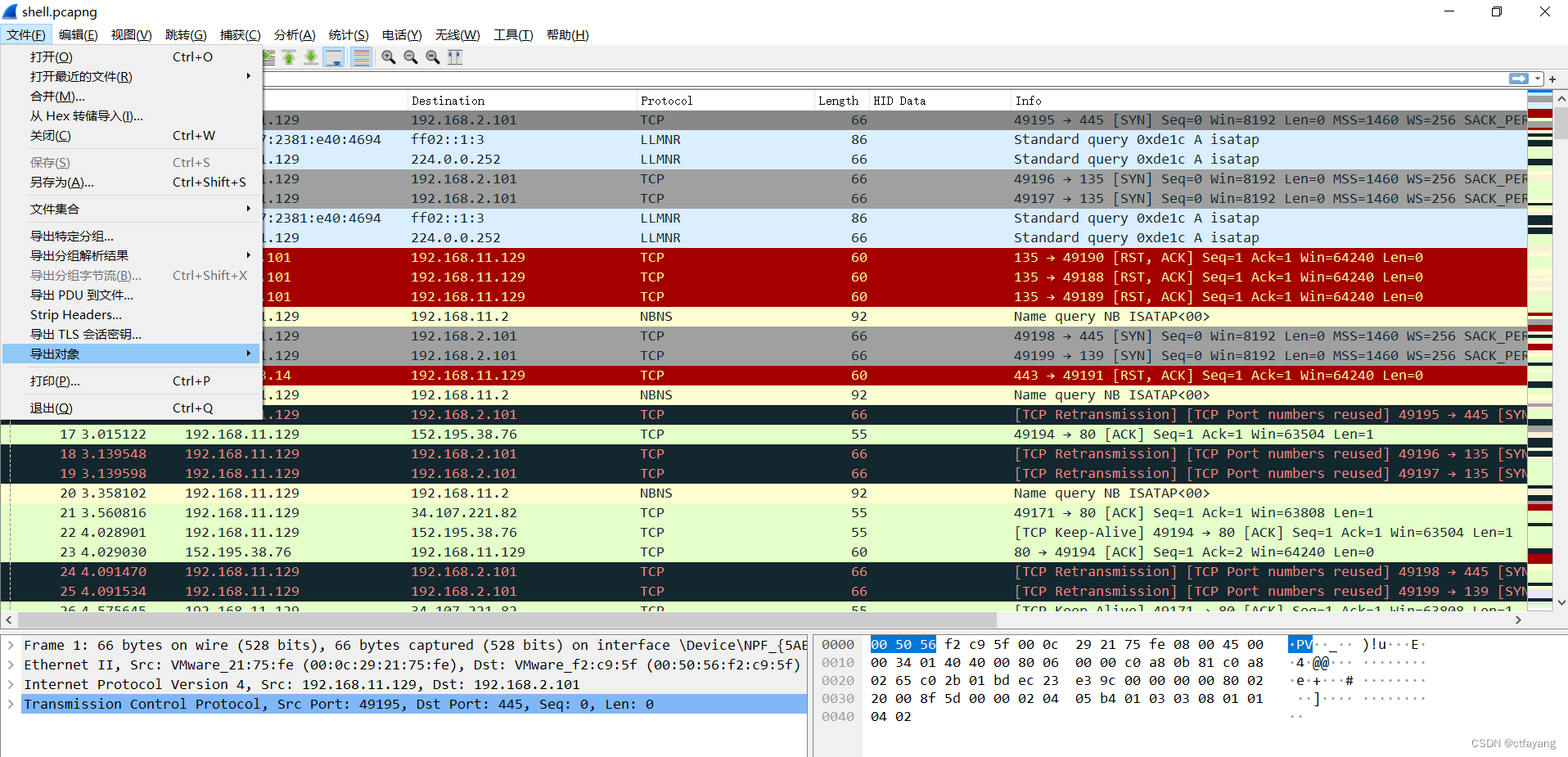
3):选择HTTP对象导出
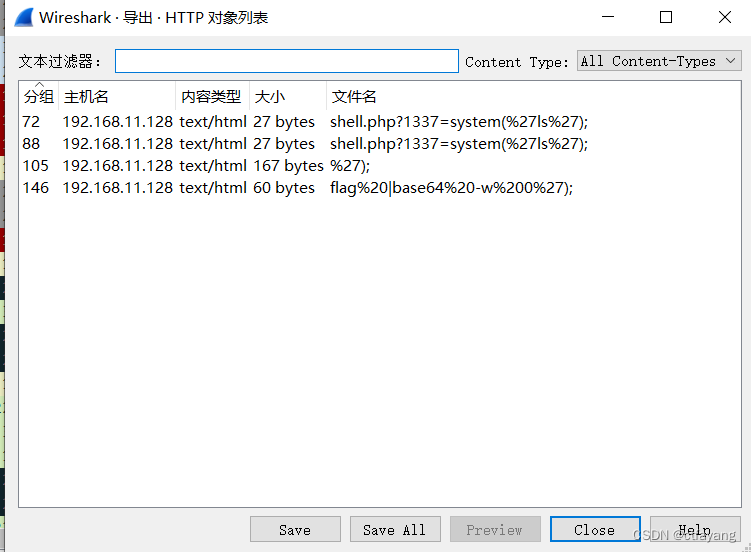
4):用记事本打开flag%20%7cbase64%20-w%200%27);文件
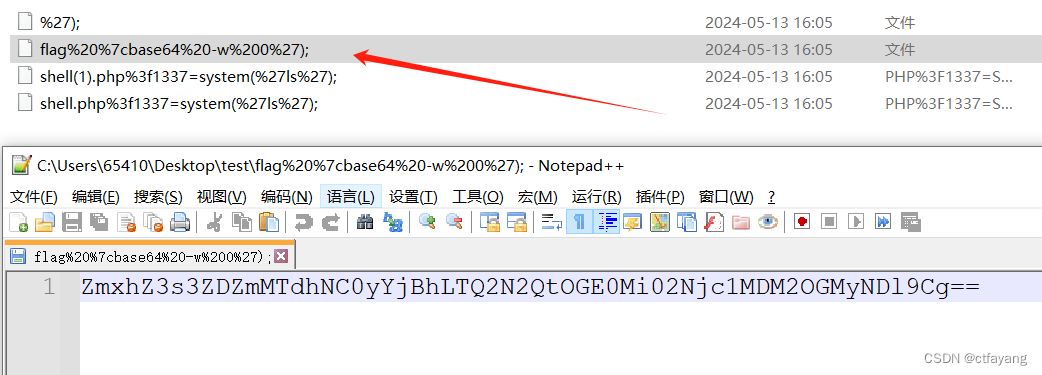
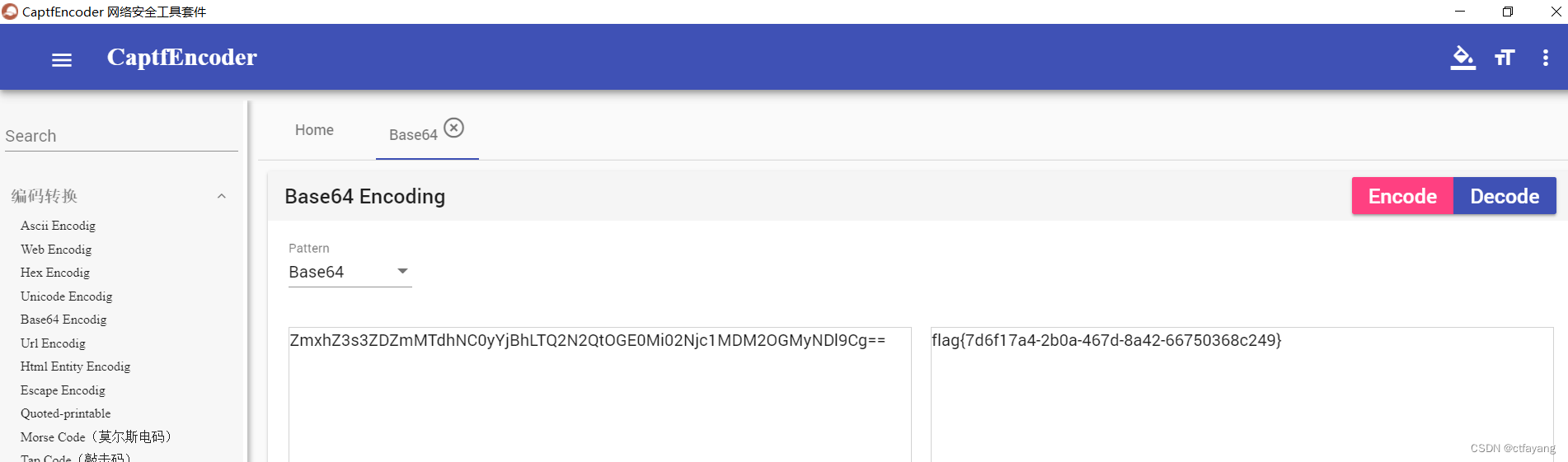
5):base64解密文件内容ZmxhZ3s3ZDZmMTdhNC0yYjBhLTQ2N2QtOGE0Mi02Njc1MDM2OGMyNDl9Cg==得到flag{7d6f17a4-2b0a-467d-8a42-66750368c249}
第三题:AES加密
3.1 题目界面:

3.2 解题步骤:
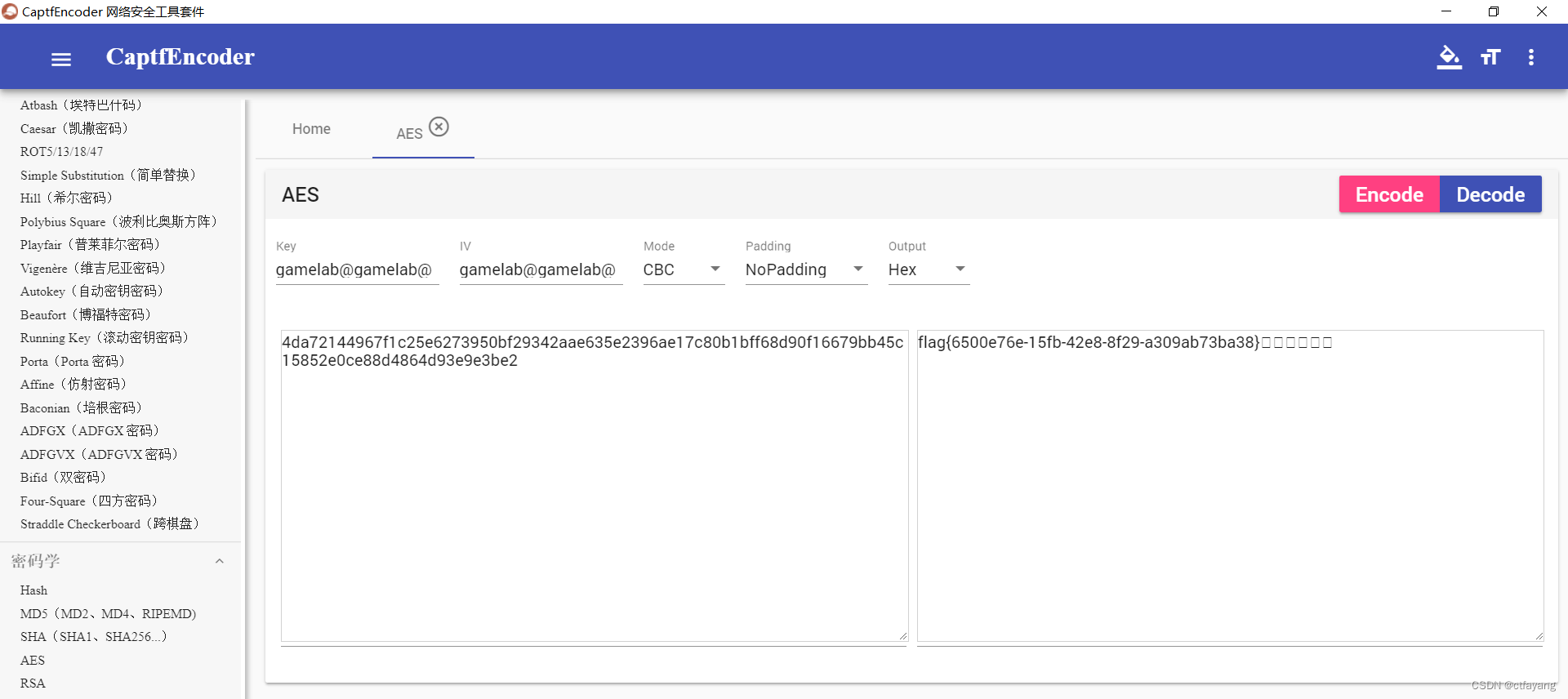
1):分析得出:题目界面已经告诉我们采用的是AES加密,并且告诉我们key是gamelab@gamelab@,IV是gamelab@gamelab@,Mode是CBC模式,输出为Hex十六进制4da72144967f1c25e6273950bf29342aae635e2396ae17c80b1bff68d90f16679bb45c15852e0ce88d4864d93e9e3be2
2):打开解密工具cc(CyberChef),输入key,IV,Mode以及密文,点击decode解密得到flag{6500e76e-15fb-42e8-8f29-a309ab73ba38}
第四题:RSA加密
4.1 题目文件为task.py,文件代码内容如下所示:

from Crypto.Util.number import *
from gmpy2 import *
flag = b'xxx'
m = bytes_to_long(flag)
p = getPrime(512)
q = next_prime(p)
e = 65537
n = p * q
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
d1 = d % q
d2 = d % p
c = pow(m, e, n)
print(n)
print(d1)
print(d2)
print(c)
# 94581028682900113123648734937784634645486813867065294159875516514520556881461611966096883566806571691879115766917833117123695776131443081658364855087575006641022211136751071900710589699171982563753011439999297865781908255529833932820965169382130385236359802696280004495552191520878864368741633686036192501791
# 4218387668018915625720266396593862419917073471510522718205354605765842130260156168132376152403329034145938741283222306099114824746204800218811277063324566
# 9600627113582853774131075212313403348273644858279673841760714353580493485117716382652419880115319186763984899736188607228846934836782353387850747253170850
# 36423517465893675519815622861961872192784685202298519340922692662559402449554596309518386263035128551037586034375613936036935256444185038640625700728791201299960866688949056632874866621825012134973285965672502404517179243752689740766636653543223559495428281042737266438408338914031484466542505299050233075829
4.2 解题步骤:
1):分析得出:我们得知道这个算法的原理,就是现在p,q是两个素数Q,而且他俩在素数序列里面就是一前一后的关系。所以我们要把他俩的乘积开根号得到的结果一定是在p,q之间的一个数字,(而且一定不是素数,因为p,q就是紧邻的两个素数)。那我们找这个开方出来的数字的下一个素数,一定是q,因此我们再让n/q就可以得到两个素数。
2):解法一,得到flag{5f00e1b9-2933-42ad-b4e1-069f6aa98e9a}:
import gmpy2
import sympy
# import Cryptodome.Util.number
from Crypto.Util.number import *
import binascii
n=94581028682900113123648734937784634645486813867065294159875516514520556881461611966096883566806571691879115766917833117123695776131443081658364855087575006641022211136751071900710589699171982563753011439999297865781908255529833932820965169382130385236359802696280004495552191520878864368741633686036192501791
x=gmpy2.iroot(n,2)[0]# 取第0个元素,也就是第一个元素
p=sympy.nextprime(x)
q=n//p
e=65537
d=gmpy2.invert(e,(p-1)*(q-1))
print(p)
print(q)
print(d)
c=36423517465893675519815622861961872192784685202298519340922692662559402449554596309518386263035128551037586034375613936036935256444185038640625700728791201299960866688949056632874866621825012134973285965672502404517179243752689740766636653543223559495428281042737266438408338914031484466542505299050233075829
m=pow(c,d,n)
print(m)
print(long_to_bytes(m))
3):解法二,直接yafu分解n,得到p,q的值,然后计算得到flag。
第五题:DWT盲水印
5.1 题目文件如下所示:

5.2 解题步骤:
1):破解orign压缩包:打开压缩包发现压缩包里面的serect.txt是密码字典,未加密,可以解压出来,然后用serect.txt字典破解压缩包orign.zip,得到a.png也就是原始图片。
2):打开lose.py分析发现为DWT盲水印代码:
class WaterMarkDWT:
def __init__(self, origin: str, watermark: str, key: int, weight: list):
self.key = key
self.img = cv2.imread(origin)
self.mark = cv2.imread(watermark)
self.coef = weight
def arnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = (i + b * j) % r
y = (a * i + (a * b + 1) * j) % c
p[x, y] = img[i, j]
return p
def deArnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = ((a * b + 1) * i - b * j) % r
y = (-a * i + j) % c
p[x, y] = img[i, j]
return p
def get(self, size: tuple = (1200, 1200), flag: int = None):
img = cv2.resize(self.img, size)
img1 = cv2.cvtColor(img, cv2.COLOR_RGB2GRAY)
img2 = cv2.cvtColor(self.mark, cv2.COLOR_RGB2GRAY)
c = pywt.wavedec2(img2, 'db2', level=3)
[cl, (cH3, cV3, cD3), (cH2, cV2, cD2), (cH1, cV1, cD1)] = c
d = pywt.wavedec2(img1, 'db2', level=3)
[dl, (dH3, dV3, dD3), (dH2, dV2, dD2), (dH1, dV1, dD1)] = d
a1, a2, a3, a4 = self.coef
ca1 = (cl - dl) * a1
ch1 = (cH3 - dH3) * a2
cv1 = (cV3 - dV3) * a3
cd1 = (cD3 - dD3) * a4
waterImg = pywt.waverec2([ca1, (ch1, cv1, cd1)], 'db2')
waterImg = np.array(waterImg, np.uint8)
waterImg = self.deArnold(waterImg)
kernel = np.ones((3, 3), np.uint8)
if flag == 0:
waterImg = cv2.erode(waterImg, kernel)
elif flag == 1:
waterImg = cv2.dilate(waterImg, kernel)
cv2.imwrite('水印.png', waterImg)
return waterImg
if __name__ == '__main__':
img = 'a.png'
k = 20
xs = [0.2, 0.2, 0.5, 0.4]
W1 = WaterMarkDWT(img, waterImg, k, xs)
3):编写exp.py得到flag.png:
import cv2
import pywt
import numpy as np
class WaterMarkDWT:
def __init__(self, origin: str, watermark: str, key: int, weight: list):
self.key = key
self.img = cv2.imread(origin)
self.mark = cv2.imread(watermark)
self.coef = weight
def arnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = (i + b * j) % r
y = (a * i + (a * b + 1) * j) % c
p[x, y] = img[i, j]
return p
def deArnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = ((a * b + 1) * i - b * j) % r
y = (-a * i + j) % c
p[x, y] = img[i, j]
return p
def get(self, size: tuple = (1200, 1200), flag: int = None):
img = cv2.resize(self.img, size)
img1 = cv2.cvtColor(img, cv2.COLOR_RGB2GRAY)
img2 = cv2.cvtColor(self.mark, cv2.COLOR_RGB2GRAY)
c = pywt.wavedec2(img2, 'db2', level=3)
[cl, (cH3, cV3, cD3), (cH2, cV2, cD2), (cH1, cV1, cD1)] = c
d = pywt.wavedec2(img1, 'db2', level=3)
[dl, (dH3, dV3, dD3), (dH2, dV2, dD2), (dH1, dV1, dD1)] = d
a1, a2, a3, a4 = self.coef
ca1 = (cl - dl) * a1
ch1 = (cH3 - dH3) * a2
cv1 = (cV3 - dV3) * a3
cd1 = (cD3 - dD3) * a4
waterImg = pywt.waverec2([ca1, (ch1, cv1, cd1)], 'db2')
waterImg = np.array(waterImg, np.uint8)
waterImg = self.deArnold(waterImg)
kernel = np.ones((3, 3), np.uint8)
if flag == 0:
waterImg = cv2.erode(waterImg, kernel)
elif flag == 1:
waterImg = cv2.dilate(waterImg, kernel)
cv2.imwrite('水印.png', waterImg)
return waterImg
if __name__ == '__main__':
img = 'a.png'
newImg='newImg.png'
k = 20
#xs = [0.2, 0.2, 0.5, 0.4]
coef=[5,5,2,2.5]
#waterImg='flag.png'
W1 = WaterMarkDWT(img, newImg, k, coef)
waterimg=W1.get()

第六题:Reverse逆向RC4
6.1 题目文件rc4.exe如下所示:

6.2 解题步骤:
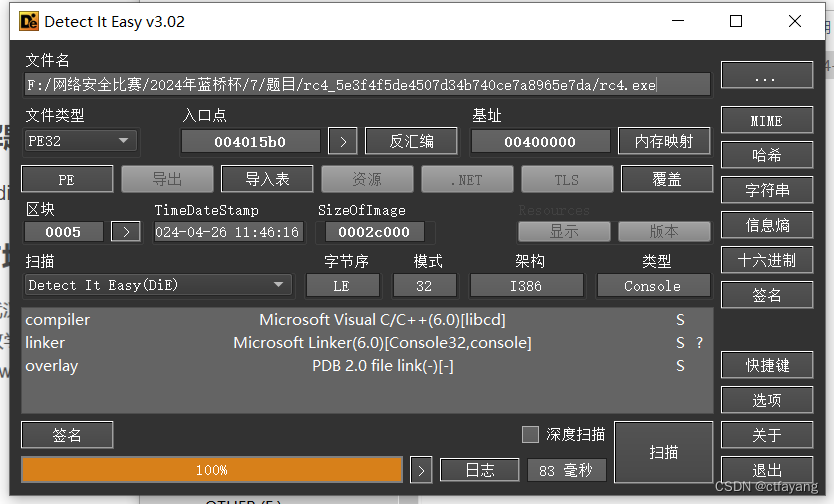
1):die检测无壳,32位程序。
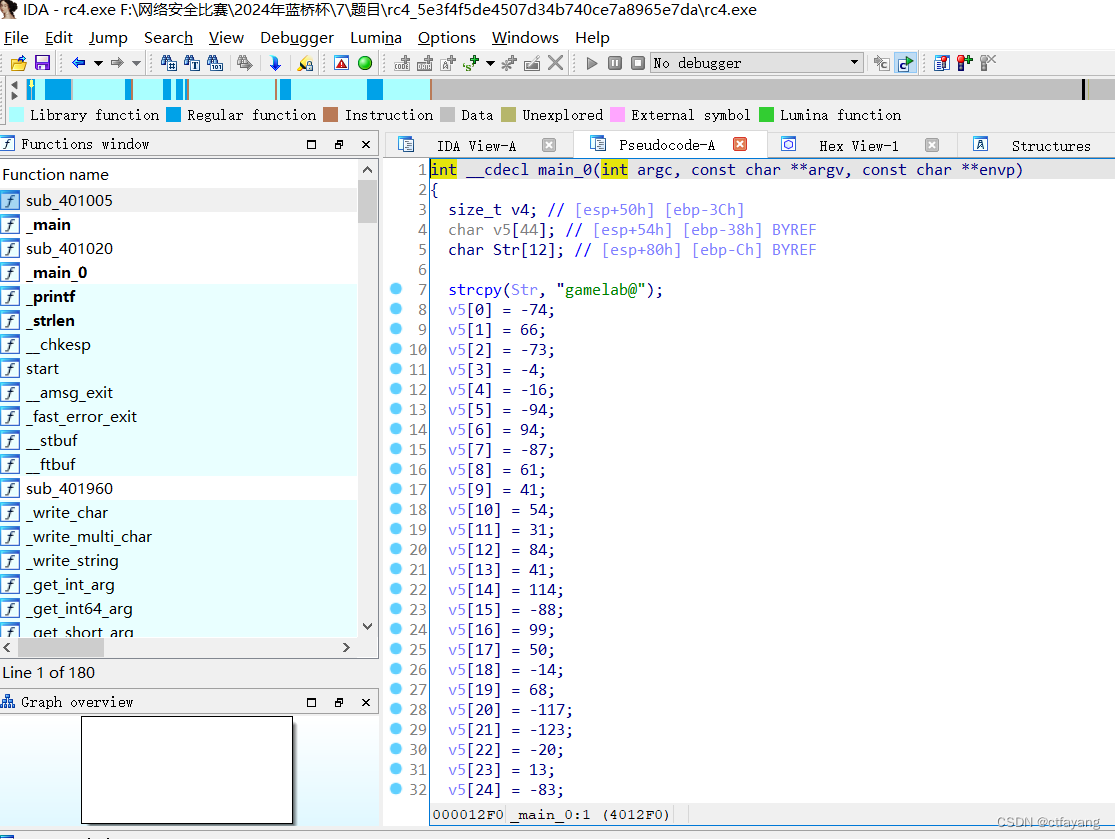
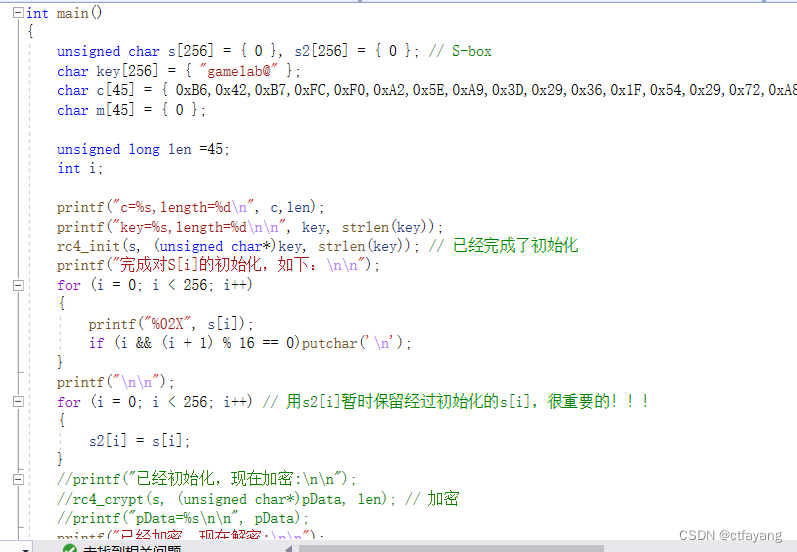
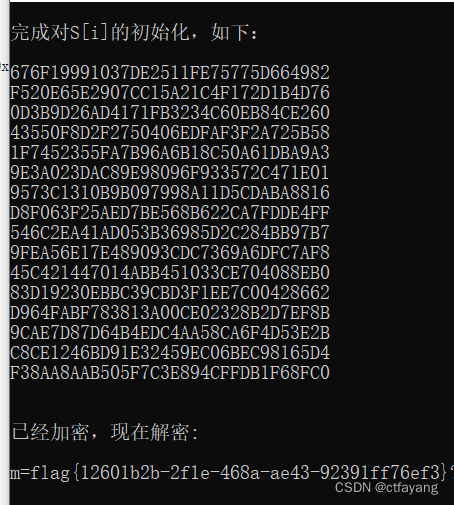
2):用IDA32打开,发现key为gamelab@,提取数组v5进行RC4解密得到flag。
第七题:ECDSA椭圆曲线数字签名算法
7.1 题目代码如下所示:
import ecdsa
import random
def ecdsa_test(dA,k):
sk = ecdsa.SigningKey.from_secret_exponent(
secexp=dA,
curve=ecdsa.SECP256k1
)
sig1 = sk.sign(data=b'Hi.', k=k).hex()
sig2 = sk.sign(data=b'hello.', k=k).hex()
r1 = int(sig1[:64], 16)
s1 = int(sig1[64:], 16)
s2 = int(sig2[64:], 16)
return r1,s1,s2
if __name__ == '__main__':
n = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
a = random.randint(0,n)
flag = 'flag{' + str(a) + "}"
b = random.randint(0,n)
print(ecdsa_test(a,b))
# (4690192503304946823926998585663150874421527890534303129755098666293734606680, 111157363347893999914897601390136910031659525525419989250638426589503279490788, 74486305819584508240056247318325239805160339288252987178597122489325719901254)
7.2 代码分析:
椭圆曲线数字签名算法,它利用椭圆曲线密码学(ECC)对数字签名算法(DSA)进行模拟,其安全性基于椭圆曲线离散对数问题。但是当某些数值相同时会出现一些安全问题。
分析代码可以看出,存在随机数重复使用。具体来说,这段代码中签名的过程中使用了相同的随机数 k 来对不同的消息进行签名。这种情况下,可以通过分析两个相同 k 值对应的消息签名来恢复私钥 dA。
在 ECDSA 中,每次签名过程中都会使用一个随机数 k,以确保生成唯一的签名。然而,如果相同的随机数 k 被重复使用来对不同的消息进行签名,攻击者就有可能通过数学分析和推导计算出私钥 dA。
7.3 exp代码:
import sympy
from hashlib import sha1
from Cryptodome.Util.number import long_to_bytes , bytes_to_long
def calculate_private_key(r1, s1, s2, h1, h2, n):
# 计算k值
k = ((h1 - h2) * sympy.mod_inverse(s1 - s2, n)) % n
# 计算私钥dA
dA = (sympy.mod_inverse(r1, n) * (k * s1 - h1)) % n
return dA
if __name__ == "__main__":
# 定义椭圆曲线的参数
n = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
# 签名中的r1, s1, s2值
r1 = 4690192503304946823926998585663150874421527890534303129755098666293734606680
s1 = 111157363347893999914897601390136910031659525525419989250638426589503279490788
s2 = 74486305819584508240056247318325239805160339288252987178597122489325719901254
h1 = bytes_to_long(sha1(b'Hi.').digest())
h2 = bytes_to_long(sha1(b'hello.').digest())
private_key = calculate_private_key(r1, s1, s2, h1, h2, n)
print(f'flag{{{private_key}}}')
获得flag{40355055231406097504270940121798355439363616832290875140843417522164091270174}
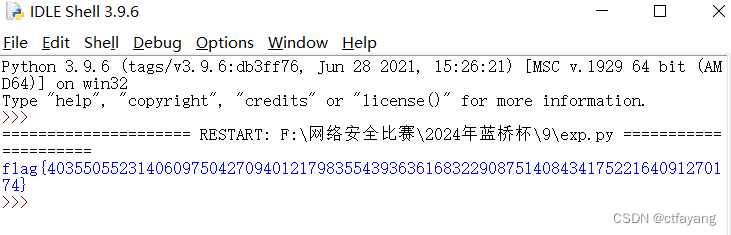
第八题:Reverse逆向xxtea
8.1 题目描述如下:
Flag被使用了算法分成若干个小块,每个块使用相同的加密解密方法,但这个算法是对称加密,请分析密文并还原。
8.2 题目文件happytime
8.3 解题步骤
1):die检测无壳,64位程序。

2):拖进IDA分析。
printf输出提示信息Let’s have a drink,pay your answer(flag):,read在键盘读取flag输入,重要的关键函数是cry加密函数,接受v5和输入的flag,这里的11应该是flag被分割成了11组,最后一个循环比较加密后的flag和V6,刚好和上面v6数组对应:

3):根据cry函数的特征,可以判定这是XXTEA加密无疑,找到其中的DELTA,密文(main函数中的v6),和key(前面main函数的V5),即可编写脚本解密(输出的时候注意大小端序):

#include <stdbool.h>
#include <stdio.h>
#define MX (((z >> 5) ^ (y << 2)) + ((y >> 3) ^ (z << 4)) ^ (sum ^ y) + (k[(p & 3) ^ e] ^ z))
bool btea(unsigned int *v, int n, unsigned int *k)
{
unsigned int z = v[n - 1], y = v[0], sum = 0, e, DELTA = 0x61C88647;
unsigned int p, q;
if (n > 1)
{ /* enCoding Part */
q = 415 / n + 114;
while (q-- > 0)
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < (n - 1); p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
}
return 0;
}
else if (n < -1)
{ /* Decoding Part */
n = -n;
q = 415 / n + 114;
sum = -q * DELTA;
while (sum != 0)
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum += DELTA;
}
return 0;
}
return 1;
}
int main()
{
unsigned int v[11] = {0x480AC20C, 0xCE9037F2, 0x8C212018, 0xE92A18D, 0xA4035274, 0x2473AAB1, 0xA9EFDB58, 0xA52CC5C8, 0xE432CB51, 0xD04E9223, 0x6FD07093}, key[4] = {0x79696755, 0x67346F6C, 0x69231231, 0x5F674231};
int n = 11; // n为要加密的数据个数
btea(v, -n, key); // 取正为加密,取负为解密
char *p = (char *)v;
for (int i = 0; i < 44; i++)
{
printf("%c", *p);
p++;
}
return 0;
}
//flag{efccf8f0-0c97-12ec-82e0-0c9d9242e335}
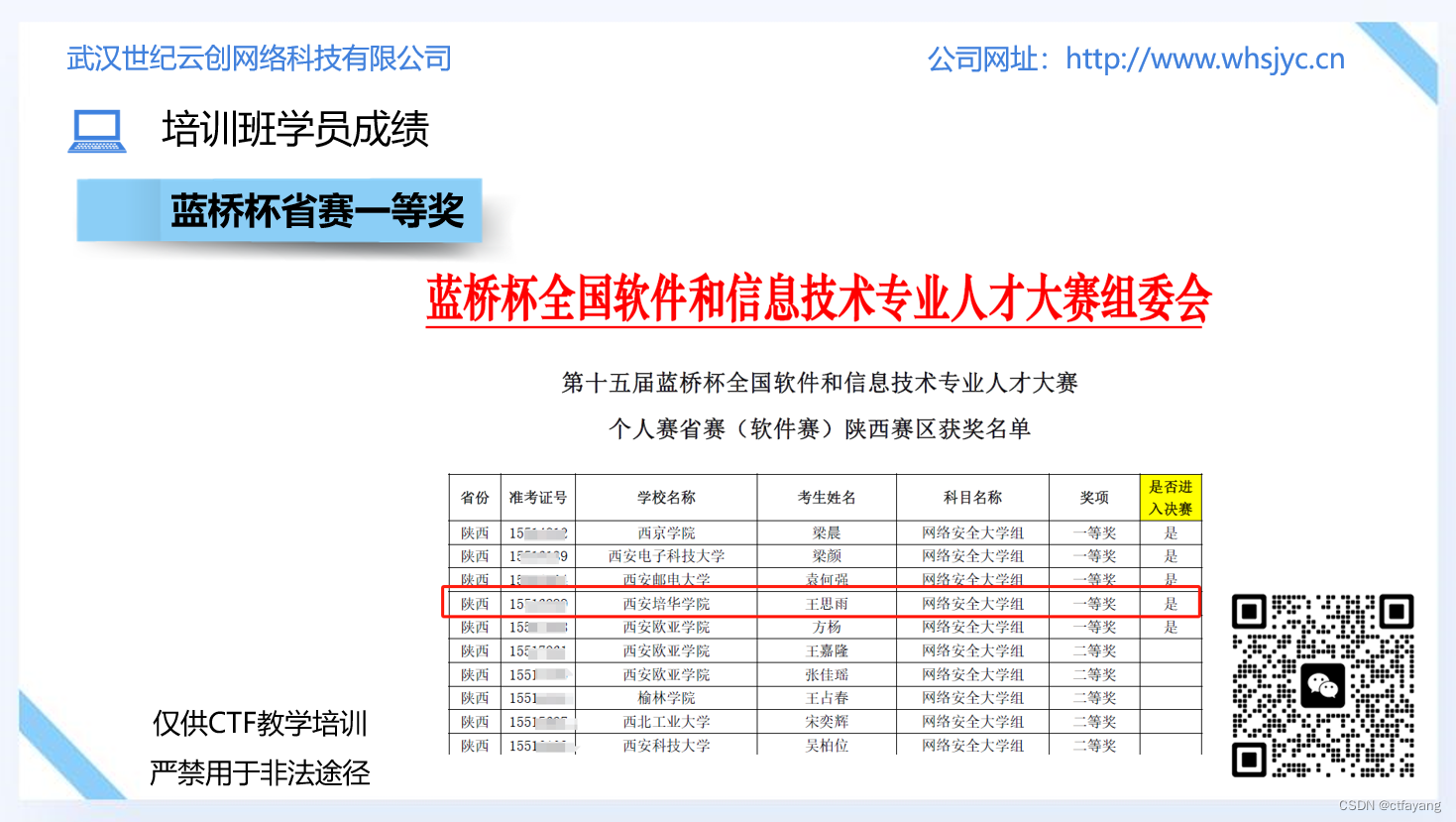
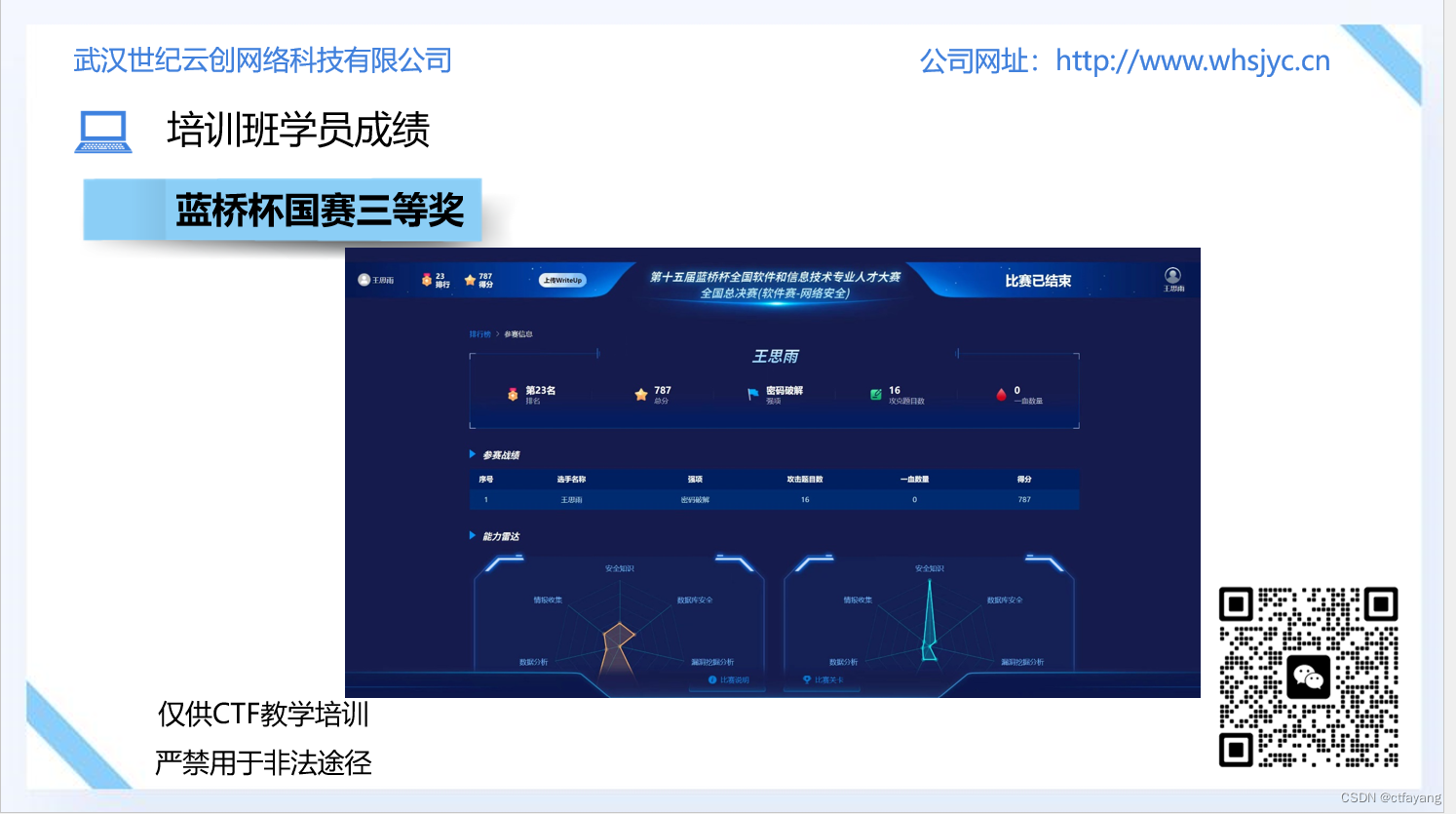
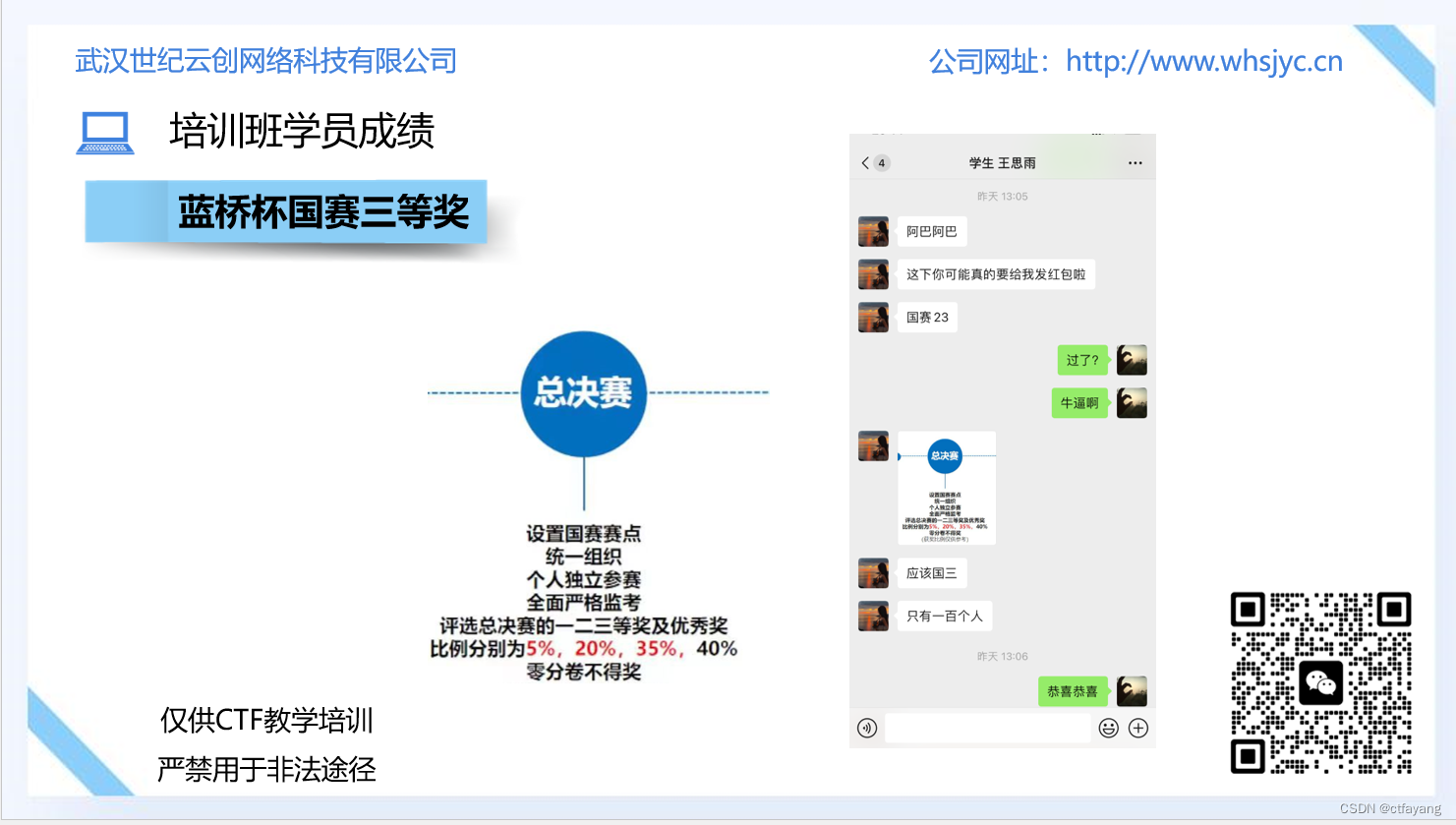
恭喜CTF培训班的王思雨同学获得2024年蓝桥杯省赛一等奖,国赛三等奖的成绩。
版权归原作者 ctfayang 所有, 如有侵权,请联系我们删除。