==========逆向必备:
函JNItrace是一个基于Frida框架的Hook jni方法的库。https://github.com/chame1eon/jnitrace
jnitrace -l libbili.so tv.danmaku.bili --ignore-vm
加密函数定位:
https://github.com/lasting-yang/frida_hook_libart.git
dump 脚本修复加密so
https://github.com/lasting-yang/frida_dump
frida hook模板:
so :https://blog.csdn.net/weixin_38927522/article/details/122124012
java:
https://blog.csdn.net/weixin_38927522/article/details/120025814
遍历so方法:
https://blog.csdn.net/weixin_38927522/article/details/120033269
hook 常见算法
https://blog.csdn.net/weixin_38927522/article/details/120025814
下面上unidbg-42位sig3:
packagecom.ks;importcapstone.Capstone;importcom.github.unidbg.AndroidEmulator;importcom.github.unidbg.Emulator;importcom.github.unidbg.Module;importcom.github.unidbg.Symbol;importcom.github.unidbg.arm.ARM;importcom.github.unidbg.arm.HookStatus;importcom.github.unidbg.arm.backend.Backend;importcom.github.unidbg.arm.backend.BlockHook;importcom.github.unidbg.arm.context.RegisterContext;importcom.github.unidbg.debugger.BreakPointCallback;importcom.github.unidbg.file.FileResult;importcom.github.unidbg.file.IOResolver;importcom.github.unidbg.file.linux.AndroidFileIO;importcom.github.unidbg.hook.HookContext;importcom.github.unidbg.hook.ReplaceCallback;importcom.github.unidbg.hook.xhook.IxHook;importcom.github.unidbg.linux.android.AndroidEmulatorBuilder;importcom.github.unidbg.linux.android.AndroidResolver;importcom.github.unidbg.linux.android.XHookImpl;importcom.github.unidbg.linux.android.dvm.*;importcom.github.unidbg.linux.android.dvm.api.AssetManager;importcom.github.unidbg.linux.android.dvm.array.ArrayObject;importcom.github.unidbg.linux.android.dvm.wrapper.DvmBoolean;importcom.github.unidbg.linux.android.dvm.wrapper.DvmInteger;importcom.github.unidbg.linux.file.SimpleFileIO;importcom.github.unidbg.memory.Memory;importcom.github.unidbg.memory.MemoryBlock;importcom.github.unidbg.pointer.UnidbgPointer;importcom.github.unidbg.spi.SyscallHandler;importcom.github.unidbg.utils.Inspector;importcom.github.unidbg.virtualmodule.android.AndroidModule;importcom.github.unidbg.virtualmodule.android.JniGraphics;importcom.sun.jna.Pointer;importorg.apache.commons.codec.DecoderException;importorg.apache.commons.codec.binary.Hex;importunicorn.ArmConst;importunicorn.Unicorn;importjava.io.File;importjava.io.FileNotFoundException;importjava.io.FileOutputStream;importjava.io.PrintStream;importjava.nio.charset.StandardCharsets;importjava.util.ArrayList;importjava.util.Arrays;importjava.util.Collection;importjava.util.List;publicclass kwsgmain extendsAbstractJniimplementsIOResolver{privatefinalAndroidEmulator emulator;privatefinalVM vm;privatefinalModulemodule;privateint count =0;privateboolean exist;privateBlockHook blockHook;kwsgmain(){// 创建模拟器实例
emulator =AndroidEmulatorBuilder.for32Bit().build();// 模拟器的内存操作接口finalMemory memory = emulator.getMemory();// 设置系统类库解析
memory.setLibraryResolver(newAndroidResolver(23));// 创建Android虚拟机
vm = emulator.createDalvikVM(newFile("unidbg-android/src/test/resources/ks/kuaishou7.5.30.14527.apk"));newJniGraphics(emulator, vm).register(memory);// 虚拟libandroid.sonewAndroidModule(emulator, vm).register(memory);
vm.setJni(this);SyscallHandler<AndroidFileIO> handler = emulator.getSyscallHandler();
handler.addIOResolver(this);DalvikModule dm = vm.loadLibrary("kwsgmain",true);// 加载好的 libhookinunidbg.so对应为一个模块module= dm.getModule();// 执行JNIOnLoad(如果有的话)
dm.callJNI_OnLoad(emulator);}publicstaticvoidmain(String[] args){long t1 =System.currentTimeMillis();
kwsgmain demo =newkwsgmain();
demo.patchjni();
demo.hookonegetstring();
demo.callInit();
demo.hooktimebyunicorn();// demo.searchFirstExist();
demo.get_NS_sig3();long t2 =System.currentTimeMillis();System.out.println(t2 - t1);}publicvoidsearchFirstExist(){
blockHook =newBlockHook(){@OverridepublicvoidhookBlock(Backend backend,long address,int size,Object user){byte[] data ="3160299949da77953e6b310241e248e1c1be64c6e4".getBytes(StandardCharsets.UTF_8);if(data.length >0){
exist =searchStack(data);}if(exist){System.out.println("fuckIt!");// emulator.attach().debug();
blockHook.detach();}}@OverridepublicvoidonAttach(Unicorn.UnHook unHook){}@Overridepublicvoiddetach(){}};// emulator.getBackend().hook_add_new(blockHook ,module.base, module.base+module.size, null);
emulator.getBackend().hook_add_new(blockHook ,1,0,null);}privatebooleansearchStack(byte[] data){UnidbgPointer stack = emulator.getContext().getStackPointer();Backend backend = emulator.getBackend();Collection<Pointer> pointers =searchMemory(backend, stack.toUIntPeer(), emulator.getMemory().getStackBase(), data);if(pointers.size()>0){returntrue;}returnfalse;}privateCollection<Pointer>searchMemory(Backend backend,long start,long end,byte[] data){List<Pointer> pointers =newArrayList<>();for(long i = start, m = end - data.length; i < m; i++){byte[] oneByte = backend.mem_read(i,1);if(data[0]!= oneByte[0]){continue;}if(Arrays.equals(data, backend.mem_read(i, data.length))){
pointers.add(UnidbgPointer.pointer(emulator, i));
i +=(data.length -1);}}return pointers;}publicvoidtraceNatives(){PrintStream traceStream =null;try{// 保存文件String traceFile ="unidbg-android/src/test/resources/traceFunctions.txt";
traceStream =newPrintStream(newFileOutputStream(traceFile),true);}catch(FileNotFoundException e){
e.printStackTrace();}finalPrintStream finalTraceStream = traceStream;
emulator.getBackend().hook_add_new(newBlockHook(){@OverridepublicvoidhookBlock(Backend backend,long address,int size,Object user){System.out.println(size);// Symbol symbol = module.findClosestSymbolByAddress(address, true);//// if(Math.abs(symbol.getAddress() - address) < 2){// System.out.println("call:"+symbol.getName());// }if(size>8){Capstone.CsInsn[] insns = emulator.disassemble(address,4,0);if(insns[0].mnemonic.equals("push")){int level = emulator.getUnwinder().depth();assert finalTraceStream !=null;for(int i =0; i < level ; i++){
finalTraceStream.print(" | ");}
finalTraceStream.println(" "+"sub_"+Integer.toHexString((int)(address-module.base))+" ");}}}@OverridepublicvoidonAttach(Unicorn.UnHook unHook){}@Overridepublicvoiddetach(){}},module.base,module.base+module.size,0);}@OverridepublicFileResultresolve(Emulator emulator,String pathname,int oflags){System.out.println("fuck path:"+pathname);if(pathname.equals("/data/app/com.smile.gifmaker-oyRnT1esU1Pf5iDY6JKtjA==/base.apk")){returnFileResult.success(newSimpleFileIO(oflags,newFile("unidbg-android/src/test/resources/ks/kuaishou7.5.30.14527.apk"), pathname));};returnnull;}publicvoidcallInit(){List<Object> list =newArrayList<>(10);
list.add(vm.getJNIEnv());// 第一个参数是envDvmObject<?> thiz = vm.resolveClass("com/kuaishou/android/security/mainplugin/JNICLibrary").newObject(null);
list.add(vm.addLocalObject(thiz));// 第二个参数,实例方法是jobject,静态方法是jclass,直接填0,一般用不到。DvmObject<?> context = vm.resolveClass("com/yxcorp/gifshow/App").newObject(null);// context
vm.addLocalObject(context);
list.add(10412);//参数1StringObject appkey =newStringObject(vm,"d7b7d042-d4f2-4012-be60-d97ff2429c17");
vm.addLocalObject(appkey);
list.add(vm.addLocalObject(newArrayObject(null, appkey,null,null,context,null,null)));// 直接通过地址调用Number[] numbers =module.callFunction(emulator,0xc085, list.toArray());DvmObject<?> object = vm.getObject(numbers[0].intValue());String result =(String) object.getValue();System.out.println("result:"+result);}publicStringget_NS_sig3(){System.out.println("sig3 start");List<Object> list =newArrayList<>(10);
list.add(vm.getJNIEnv());// 第一个参数是envDvmObject<?> thiz = vm.resolveClass("com/kuaishou/android/security/mainplugin/JNICLibrary").newObject(null);
list.add(vm.addLocalObject(thiz));// 第二个参数,实例方法是jobject,静态方法是jclass,直接填0,一般用不到。DvmObject<?> context = vm.resolveClass("com/yxcorp/gifshow/App").newObject(null);// context
vm.addLocalObject(context);
list.add(10405);//参数1StringObject urlObj =newStringObject(vm,"/rest/n/user/profile/v2d85e8c937c4fe2749404cfa5cf474534");
vm.addLocalObject(urlObj);ArrayObject arrayObject =newArrayObject(urlObj);StringObject appkey =newStringObject(vm,"d7b7d042-d4f2-4012-be60-d97ff2429c17");
vm.addLocalObject(appkey);DvmInteger intergetobj =DvmInteger.valueOf(vm,-1);
vm.addLocalObject(intergetobj);DvmBoolean boolobj =DvmBoolean.valueOf(vm,false);
vm.addLocalObject(boolobj);
list.add(vm.addLocalObject(newArrayObject(arrayObject, appkey,intergetobj,boolobj,context,null,boolobj)));// 直接通过地址调用Number[] numbers =module.callFunction(emulator,0xc085, list.toArray());DvmObject<?> object = vm.getObject(numbers[0].intValue());String result =(String) object.getValue();System.out.println("result:"+result);return result;}@OverridepublicDvmObject<?>callObjectMethodV(BaseVM vm,DvmObject<?> dvmObject,String signature,VaList vaList){switch(signature){case"com/yxcorp/gifshow/App->getPackageCodePath()Ljava/lang/String;":{returnnewStringObject(vm,"/data/app/com.smile.gifmaker-oyRnT1esU1Pf5iDY6JKtjA==/base.apk");}case"com/yxcorp/gifshow/App->getAssets()Landroid/content/res/AssetManager;":{returnnewAssetManager(vm, signature);}case"com/yxcorp/gifshow/App->getPackageName()Ljava/lang/String;":{returnnewStringObject(vm,"com.smile.gifmaker");}case"com/yxcorp/gifshow/App->getPackageManager()Landroid/content/pm/PackageManager;":{return vm.resolveClass("android/content/pm/PackageManager").newObject(null);}}returnsuper.callObjectMethodV(vm, dvmObject, signature, vaList);}@OverridepublicintgetStaticIntField(BaseVM vm,DvmClass dvmClass,String signature){switch(signature){case"android/content/pm/PackageManager->GET_SIGNATURES:I":{return64;}}returnsuper.getStaticIntField(vm, dvmClass, signature);}@OverridepublicvoidcallStaticVoidMethodV(BaseVM vm,DvmClass dvmClass,String signature,VaList vaList){switch(signature){case"com/kuaishou/android/security/kfree/ExceptionProxy->nativeReport(ILjava/lang/String;)V":{return;}}super.callStaticVoidMethodV(vm, dvmClass, signature, vaList);}publicvoidhookonegetstring(){
emulator.attach().addBreakPoint(module.base +0x166d2,newBreakPointCallback(){@OverridepublicbooleanonHit(Emulator<?> emulator,long address){String input ="d7b7d042-d4f2-4012-be60-d97ff2429c17";MemoryBlock replaceBlock = emulator.getMemory().malloc(input.length(),true);
replaceBlock.getPointer().write(input.getBytes(StandardCharsets.UTF_8));// 修改r0为指向新字符串的新指针
emulator.getBackend().reg_write(ArmConst.UC_ARM_REG_R0, replaceBlock.getPointer().peer);
emulator.getBackend().reg_write(ArmConst.UC_ARM_REG_PC, address +3);returntrue;}});}@OverridepublicDvmObject<?>getStaticObjectField(BaseVM vm,DvmClass dvmClass,String signature){switch(signature){case"android/app/ActivityThread->sPackageManager:Landroid/content/pm/IPackageManager;":{return vm.resolveClass("android/content/pm/IPackageManager", vm.resolveClass("java/lang/Object")).newObject(signature);}}returnsuper.getStaticObjectField(vm, dvmClass, signature);}@OverridepublicbooleancallBooleanMethodV(BaseVM vm,DvmObject<?> dvmObject,String signature,VaList vaList){switch(signature){case"java/lang/Boolean->booleanValue()Z":{// return (boolean) dvmObject.getValue();returnfalse;}}returnsuper.callBooleanMethodV(vm, dvmObject, signature, vaList);}publicvoidHooktime(){IxHook xHook =XHookImpl.getInstance(emulator);System.out.println("start hookZz");// 加载xHook,支持Import hook,文档看https://github.com/iqiyi/xHook
xHook.register("libkwsgmain.so","gettimeofday",newReplaceCallback(){UnidbgPointer pointer1 =null;@OverridepublicHookStatusonCall(Emulator<?> emulator,HookContext context,long originFunction){
pointer1 = context.getPointerArg(0);// String str = pointer.getString(0);System.out.println("fuck time in libc");// context.push(str);returnHookStatus.RET(emulator, originFunction);}@OverridepublicvoidpostCall(Emulator<?> emulator,HookContext context){// Pointer pointer = context.getPointerArg(0);if(pointer1 !=null){// 这里把 时间写死byte[] buf ={(byte)0x91,(byte)0x50,(byte)0xc4,(byte)0x5f,(byte)0x15,(byte)0x97,(byte)0x09,(byte)0x00};
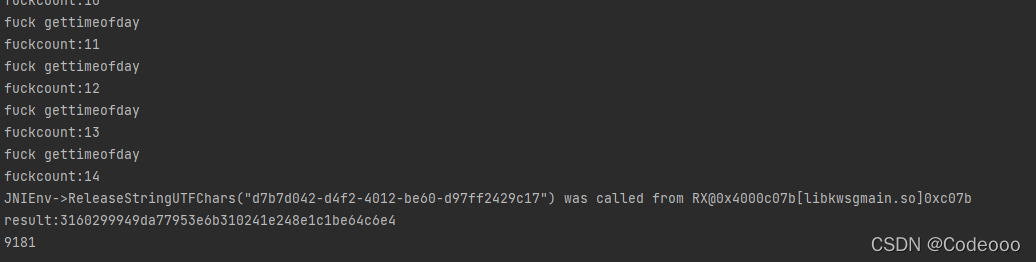
pointer1.write(0,buf,0,8);}// ByteBuffer tv_sec = pointer1.getByteBuffer(0,8);// System.out.println("gettimeofday Ok"); // + context.pop() ); // + ", ret=" + context.getIntArg(0));}},false);}//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef897c 4b 54 92 61 4e 7c 01 00 KT.aN|..//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef897c 4b 54 92 61 d0 80 01 00 KT.a....//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef897c 4b 54 92 61 dd 84 01 00 KT.a....//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef897c 4b 54 92 61 f1 88 01 00 KT.a....//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef897c 4b 54 92 61 a4 8c 01 00 KT.a....//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef8f80 4b 54 92 61 9d 90 01 00 KT.a....//fucktime:0x6192544b//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef8f80 4b 54 92 61 5c 98 01 00 KT.a\...//fucktime: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF//beef8f80 4b 54 92 61 47 9c 01 00 KT.aG...//call_native result:3160299949da77953e6b310241e248e1c1be64c6e4publicvoidhooktimebyunicorn(){
emulator.attach().addBreakPoint(module.findSymbolByName("gettimeofday",true).getAddress(),newBreakPointCallback(){UnidbgPointer pointer1 =null;@OverridepublicbooleanonHit(Emulator<?> emulator,long address){finalRegisterContext registerContext = emulator.getContext();
pointer1 = registerContext.getPointerArg(0);finalUnidbgPointer blr = registerContext.getLRPointer();
emulator.attach().addBreakPoint(blr.peer,newBreakPointCallback(){@OverridepublicbooleanonHit(Emulator<?> emulator,long address){byte[] buf;String moduleName = emulator.getMemory().findModuleByAddress(registerContext.getLRPointer().peer).name;if(moduleName.equals("libkwsgmain.so")){System.out.println("fuck gettimeofday");
count ++;System.out.println("fuckcount:"+count);switch(count){case1:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,0x56,0x5d,0x01,0x00};break;}case2:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xad,0x63,0x01,0x00};break;}case3:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xbb,0x68,0x01,0x00};break;}case4:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0x9f,0x6e,0x01,0x00};break;}case5:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xd6,0x72,0x01,0x00};break;}case6:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,0x54,0x78,0x01,0x00};break;}case7:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,0x4e,0x7c,0x01,0x00};break;}case8:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xd0,(byte)0x80,0x01,0x00};break;}case9:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xdd,(byte)0x84,0x01,0x00};break;}case10:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xf1,(byte)0x88,0x01,0x00};break;}case11:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0xa4,(byte)0x8c,0x01,0x00};break;}case12:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,(byte)0x9d,(byte)0x90,0x01,0x00};break;}case13:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,0x5c,(byte)0x98,0x01,0x00};break;}case14:{
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,0x47,(byte)0x9c,0x01,0x00};break;}default:thrownewIllegalStateException("Unexpected value: "+ count);}}else{// 0x6192544b
buf =newbyte[]{0x4b,0x54,(byte)0x92,0x61,0,0,0,0};}
pointer1.write(0,buf,0,8);returntrue;}});returntrue;}});}publicvoidhookmemmove(){
emulator.attach().addBreakPoint(module.findSymbolByName("memmove",true).getAddress(),newBreakPointCallback(){@OverridepublicbooleanonHit(Emulator<?> emulator,long address){RegisterContext context = emulator.getContext();Pointer dest = context.getPointerArg(0);Pointer src = context.getPointerArg(1);int length = context.getIntArg(2);Inspector.inspect(src.getByteArray(0, length),"memmove src="+ src);returntrue;}});// void *memcpy(void *str1, const void *str2, size_t n)Symbol memcpySymbol =module.findSymbolByName("memcpy");
emulator.attach().addBreakPoint(memcpySymbol.getAddress(),newBreakPointCallback(){RegisterContext context = emulator.getContext();@OverridepublicbooleanonHit(Emulator<?> emulator,long address){System.out.print("call memcpy");UnidbgPointer srcAddress = context.getPointerArg(1);int length = context.getIntArg(2);Inspector.inspect(srcAddress.getByteArray(0, length),"source:"+srcAddress);returntrue;}});}publicvoidpatchjni(){// movs r0,0byte[] patchCode ={0x00,0x20};
emulator.getBackend().mem_write(module.base +0x33BDE, patchCode);}}
48位sig3:
packagecom.ks910;importcom.github.unidbg.AndroidEmulator;importcom.github.unidbg.Emulator;importcom.github.unidbg.Module;importcom.github.unidbg.arm.backend.BlockHook;importcom.github.unidbg.debugger.BreakPointCallback;importcom.github.unidbg.file.FileResult;importcom.github.unidbg.file.IOResolver;importcom.github.unidbg.file.linux.AndroidFileIO;importcom.github.unidbg.linux.android.AndroidEmulatorBuilder;importcom.github.unidbg.linux.android.AndroidResolver;importcom.github.unidbg.linux.android.dvm.*;importcom.github.unidbg.linux.android.dvm.api.AssetManager;importcom.github.unidbg.linux.android.dvm.array.ArrayObject;importcom.github.unidbg.linux.android.dvm.wrapper.DvmBoolean;importcom.github.unidbg.linux.android.dvm.wrapper.DvmInteger;importcom.github.unidbg.memory.Memory;importcom.github.unidbg.memory.MemoryBlock;importcom.github.unidbg.spi.SyscallHandler;importcom.github.unidbg.virtualmodule.android.AndroidModule;importcom.github.unidbg.virtualmodule.android.JniGraphics;importunicorn.ArmConst;importjava.io.File;importjava.nio.charset.StandardCharsets;importjava.util.ArrayList;importjava.util.List;publicclass kwsgmain910 extendsAbstractJniimplementsIOResolver{privatefinalAndroidEmulator emulator;privatefinalVM vm;privatefinalModulemodule;kwsgmain910(){// 创建模拟器实例
emulator =AndroidEmulatorBuilder.for32Bit().build();// 模拟器的内存操作接口finalMemory memory = emulator.getMemory();// 设置系统类库解析
memory.setLibraryResolver(newAndroidResolver(23));// 创建Android虚拟机
vm = emulator.createDalvikVM(newFile("unidbg-android/src/test/resources/ks910/ks910.apk"));newJniGraphics(emulator, vm).register(memory);newAndroidModule(emulator, vm).register(memory);
vm.setJni(this);SyscallHandler<AndroidFileIO> handler = emulator.getSyscallHandler();
handler.addIOResolver(this);DalvikModule dm = vm.loadLibrary("kwsgmain",true);// 加载好的 libhookinunidbg.so对应为一个模块module= dm.getModule();// 执行JNIOnLoad(如果有的话)
dm.callJNI_OnLoad(emulator);}publicstaticvoidmain(String[] args){
kwsgmain910 demo =newkwsgmain910();
demo.hookonegetstring();
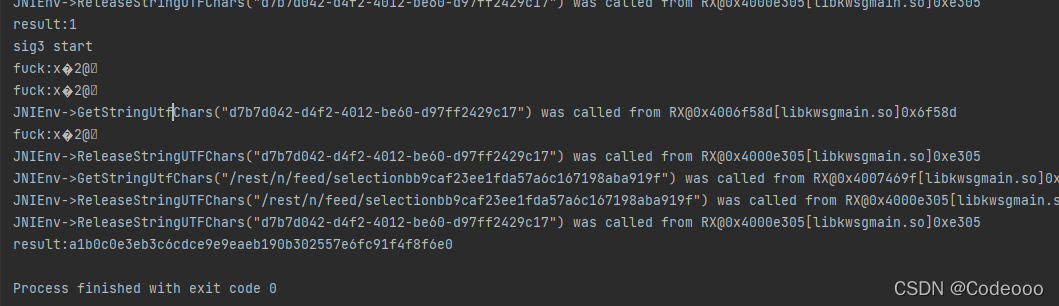
demo.callInit();
demo.get_NS_sig3();}@OverridepublicFileResultresolve(Emulator emulator,String pathname,int oflags){System.out.println("fuck:"+pathname);returnnull;}publicvoidcallInit(){List<Object> list =newArrayList<>(10);
list.add(vm.getJNIEnv());// 第一个参数是envDvmObject<?> thiz = vm.resolveClass("com/kuaishou/android/security/internal/dispatch/JNICLibrary").newObject(null);
list.add(vm.addLocalObject(thiz));// 第二个参数,实例方法是jobject,静态方法是jclass,直接填0,一般用不到。DvmObject<?> context = vm.resolveClass("com/yxcorp/gifshow/App").newObject(null);// context
vm.addLocalObject(context);
list.add(10412);//参数1StringObject appkey =newStringObject(vm,"d7b7d042-d4f2-4012-be60-d97ff2429c17");
vm.addLocalObject(appkey);
list.add(vm.addLocalObject(newArrayObject(null, appkey,null,null,context,null,null)));// 直接通过地址调用Number[] numbers =module.callFunction(emulator,0x53129, list.toArray());DvmObject<?> object = vm.getObject(numbers[0].intValue());String result =(String) object.getValue();System.out.println("result:"+result);}@OverridepublicDvmObject<?>callObjectMethodV(BaseVM vm,DvmObject<?> dvmObject,String signature,VaList vaList){switch(signature){case"com/yxcorp/gifshow/App->getPackageCodePath()Ljava/lang/String;":{returnnewStringObject(vm,"/data/app/com.smile.gifmaker-oyRnT1esU1Pf5iDY6JKtjA==/base.apk");}case"com/yxcorp/gifshow/App->getAssets()Landroid/content/res/AssetManager;":{returnnewAssetManager(vm, signature);}case"com/yxcorp/gifshow/App->getPackageName()Ljava/lang/String;":{returnnewStringObject(vm,"com.smile.gifmaker");}case"com/yxcorp/gifshow/App->getPackageManager()Landroid/content/pm/PackageManager;":{return vm.resolveClass("android/content/pm/PackageManager").newObject(null);}}returnsuper.callObjectMethodV(vm, dvmObject, signature, vaList);}@OverridepublicintgetStaticIntField(BaseVM vm,DvmClass dvmClass,String signature){switch(signature){case"android/content/pm/PackageManager->GET_SIGNATURES:I":{return64;}}returnsuper.getStaticIntField(vm, dvmClass, signature);}publicvoidhookonegetstring(){
emulator.attach().addBreakPoint(module.base +0x690de,newBreakPointCallback(){@OverridepublicbooleanonHit(Emulator<?> emulator,long address){String input ="d7b7d042-d4f2-4012-be60-d97ff2429c17";MemoryBlock replaceBlock = emulator.getMemory().malloc(input.length(),true);
replaceBlock.getPointer().write(input.getBytes(StandardCharsets.UTF_8));// 修改r0为指向新字符串的新指针
emulator.getBackend().reg_write(ArmConst.UC_ARM_REG_R0, replaceBlock.getPointer().peer);
emulator.getBackend().reg_write(ArmConst.UC_ARM_REG_PC, address +3);returntrue;}});}publicStringget_NS_sig3(){System.out.println("sig3 start");List<Object> list =newArrayList<>(10);
list.add(vm.getJNIEnv());// 第一个参数是envDvmObject<?> thiz = vm.resolveClass("com/kuaishou/android/security/mainplugin/JNICLibrary").newObject(null);
list.add(vm.addLocalObject(thiz));// 第二个参数,实例方法是jobject,静态方法是jclass,直接填0,一般用不到。DvmObject<?> context = vm.resolveClass("com/yxcorp/gifshow/App").newObject(null);// context
vm.addLocalObject(context);
list.add(10418);//参数1StringObject urlObj =newStringObject(vm,"/rest/n/feed/selectionbb9caf23ee1fda57a6c167198aba919f");
vm.addLocalObject(urlObj);ArrayObject arrayObject =newArrayObject(urlObj);StringObject appkey =newStringObject(vm,"d7b7d042-d4f2-4012-be60-d97ff2429c17");
vm.addLocalObject(appkey);DvmInteger intergetobj =DvmInteger.valueOf(vm,-1);
vm.addLocalObject(intergetobj);DvmBoolean boolobj =DvmBoolean.valueOf(vm,false);
vm.addLocalObject(boolobj);
list.add(vm.addLocalObject(newArrayObject(arrayObject, appkey,intergetobj,boolobj,context,null,boolobj)));// 直接通过地址调用Number[] numbers =module.callFunction(emulator,0x53129, list.toArray());DvmObject<?> object = vm.getObject(numbers[0].intValue());String result =(String) object.getValue();System.out.println("result:"+result);return result;}@OverridepublicvoidcallStaticVoidMethodV(BaseVM vm,DvmClass dvmClass,String signature,VaList vaList){switch(signature){case"com/kuaishou/android/security/internal/common/ExceptionProxy->nativeReport(ILjava/lang/String;)V":{return;}}super.callStaticVoidMethodV(vm, dvmClass, signature, vaList);}@OverridepublicbooleancallBooleanMethodV(BaseVM vm,DvmObject<?> dvmObject,String signature,VaList vaList){switch(signature){case"java/lang/Boolean->booleanValue()Z":{// return (boolean) dvmObject.getValue();returnfalse;}}returnsuper.callBooleanMethodV(vm, dvmObject, signature, vaList);}}
版权归原作者 Codeoooo 所有, 如有侵权,请联系我们删除。