几款好用的指纹识别工具
在web渗透过程中,对站点进行指纹探测识别非常重要,了解网站所用的web框架或者cms可以为后续的渗透提供思路和突破口
这篇文章主要用于总结几款我平时工作中经常使用的指纹识别工具
一.whatweb
whatweb是kali自带的一款指纹识别工具,使用方法简单,功能强大
whatweb -h
WhatWeb - Next generation web scanner version 0.5.5.
Developed by Andrew Horton (urbanadventurer)and Brendan Coles (bcoles).
Homepage: https://www.morningstarsecurity.com/research/whatweb
Usage: whatweb [options]<URLs>
TARGET SELECTION:<TARGETs> Enter URLs, hostnames, IP addresses, filenames or
IP ranges in CIDR, x.x.x-x,or x.x.x.x-x.x.x.x
format.--input-file=FILE,-i Read targets from a file. You can pipe
hostnames or URLs directly with-i /dev/stdin.
TARGET MODIFICATION:--url-prefix Add a prefix to target URLs.--url-suffix Add a suffix to target URLs.--url-pattern Insert the targets into a URL.
e.g. example.com/%insert%/robots.txt
AGGRESSION:
The aggression level controls the trade-off between speed/stealth and
reliability.--aggression,-a=LEVEL Set the aggression level. Default:1.1. Stealthy Makes one HTTP request per target and also
follows redirects.3. Aggressive If a level 1 plugin is matched, additional
requests will be made.4. Heavy Makes a lot of HTTP requests per target. URLs
fromall plugins are attempted.
HTTP OPTIONS:--user-agent,-U=AGENT Identify as AGENT instead of WhatWeb/0.5.5.--header,-H Add an HTTP header. eg "Foo:Bar". Specifying a
default header will replace it. Specifying an
empty value, e.g."User-Agent:" will remove it.--follow-redirect=WHEN Control when to follow redirects. WHEN may be
`never', `http-only', `meta-only', `same-site',or `always'. Default: always.--max-redirects=NUM Maximum number of redirects. Default:10.
AUTHENTICATION:--user,-u=<user:password> HTTP basic authentication.--cookie,-c=COOKIES Use cookies, e.g.'name=value; name2=value2'.--cookie-jar=FILE Read cookies from a file.
PROXY:--proxy <hostname[:port]> Set proxy hostname and port.
Default:8080.--proxy-user <username:password> Set proxy user and password.
PLUGINS:--list-plugins,-l List all plugins.--info-plugins,-I=[SEARCH] List all plugins with detailed information.
Optionally search with keywords in a comma
delimited list.--search-plugins=STRING Search plugins for a keyword.--plugins,-p=LIST Select plugins. LIST is a comma delimited set
of selected plugins. Default isall.
Each element can be a directory,fileor plugin
name and can optionally have a modifier,+/-.
Examples:+/tmp/moo.rb,+/tmp/foo.rb
title,md5,+./plugins-disabled/./plugins-disabled,-md5
-p +is a shortcut for-p +plugins-disabled.--grep,-g=STRING|REGEXP Search for STRING or a Regular Expression. Shows
only the results that match.
Examples:--grep "hello"--grep "/he[l]*o/"--custom-plugin=DEFINITION Define a custom plugin named Custom-Plugin,
Examples:":text=>'powered by abc'"":version=>/powered[ ]?by ab[0-9]/"":ghdb=>'intitle:abc \"powered by abc\"'"":md5=>'8666257030b94d3bdb46e05945f60b42'""{:text=>'powered by abc'}"--dorks=PLUGIN List Google dorks for the selected plugin.
OUTPUT:--verbose,-v Verbose output includes plugin descriptions.
Use twice for debugging.--colour,--color=WHEN control whether colour is used. WHEN may be
`never', `always',or `auto'.--quiet,-q Do not display brief logging to STDOUT.--no-errors Suppress error messages.
LOGGING:--log-brief=FILE Log brief, one-line output.--log-verbose=FILE Log verbose output.--log-errors=FILE Log errors.--log-xml=FILE Log XML format.--log-json=FILE Log JSON format.--log-sql=FILE Log SQL INSERT statements.--log-sql-create=FILE Create SQL database tables.--log-json-verbose=FILE Log JSON Verbose format.--log-magictree=FILE Log MagicTree XML format.--log-object=FILE Log Ruby object inspection format.--log-mongo-database Name of the MongoDB database.--log-mongo-collection Name of the MongoDB collection.
Default: whatweb.--log-mongo-host MongoDB hostname or IP address.
Default:0.0.0.0.--log-mongo-username MongoDB username. Default: nil.--log-mongo-password MongoDB password. Default: nil.--log-elastic-index Name of the index to store results. Default: whatweb
--log-elastic-host Host:port of the elastic http interface. Default:127.0.0.1:9200
PERFORMANCE & STABILITY:--max-threads,-t Number of simultaneous threads. Default:25.--open-timeout Time in seconds. Default:15.--read-timeout Time in seconds. Default:30.--wait=SECONDS Wait SECONDS between connections.
This is useful when using a single thread.
HELP & MISCELLANEOUS:--short-help Short usage help.--help,-h Complete usage help.--debug Raise errors in plugins.--version Display version information.
EXAMPLE USAGE:* Scan example.com../whatweb example.com
* Scan reddit.com slashdot.org with verbose plugin descriptions../whatweb -v reddit.com slashdot.org
* An aggressive scan of wired.com detects the exact version of WordPress../whatweb -a 3 www.wired.com
* Scan the local network quickly and suppress errors.
whatweb --no-errors 192.168.0.0/24* Scan the local network for https websites.
whatweb --no-errors --url-prefix https://192.168.0.0/24* Scan for crossdomain policies in the Alexa Top 1000../whatweb -i plugin-development/alexa-top-100.txt \
--url-suffix /crossdomain.xml -p crossdomain_xml
以上是该工具使用的主要参数说明以及使用示例,具体使用方法不再意义说明,对百度站点进行简单的探测

二.Ehole
这款工具是在平时渗透中无意发现的,效果非常好。
首先附上其github项目地址
https://github.com/EdgeSecurityTeam/Ehole
(1)关于该工具的介绍
EHole是一款对资产中重点系统指纹识别的工具,在红队作战中,信息收集是必不可少的环节,如何才能从大量的资产中提取有用的系统(如OA、VPN、Weblogic…)。EHole旨在帮助红队人员在信息收集期间能够快速从C段、大量杂乱的资产中精准定位到易被攻击的系统,从而实施进一步攻击。
这款工具是棱角安全社区联合出品,配合其漏洞总结,非常好用
https://forum.ywhack.com/bountytips.php?Vulnerability
该社区对常见web漏洞以及利用方法做了一个全面而详细的总结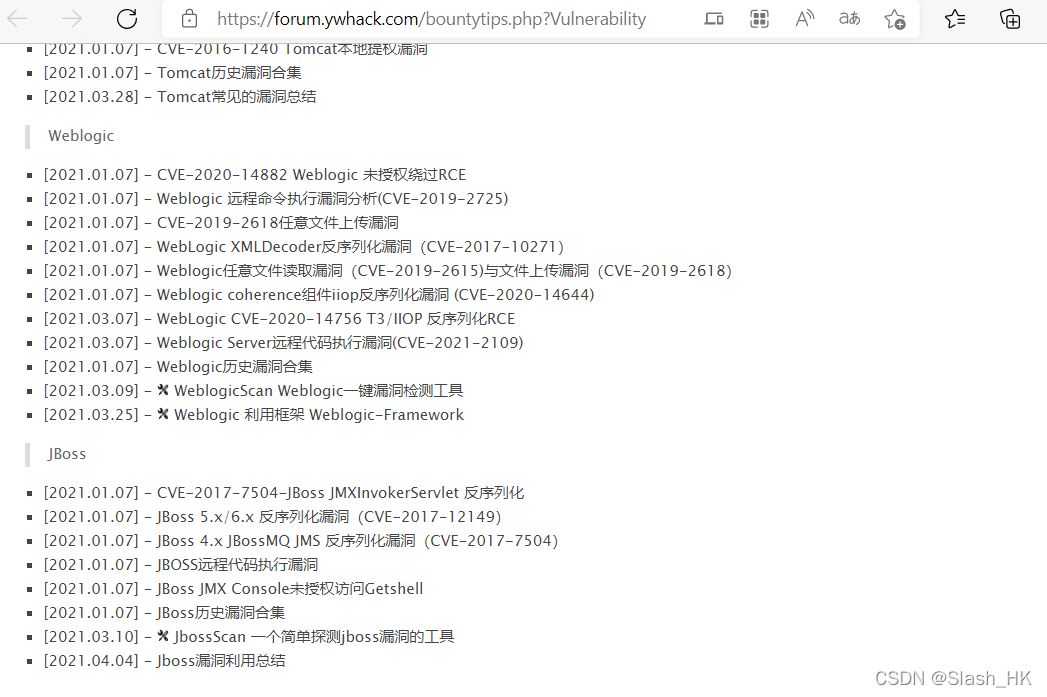
(2)部署工具到本地
将该工具部署到本地,有两种方式,一种是通过git下载然后使用go编译,第二种方式是直接下载作者给出的release版本,有windows和Linux各个平台版本。
git clone https://github.com/EdgeSecurityTeam/Ehole
Cloning into 'Ehole'...
remote: Enumerating objects:76, done.
remote: Counting objects:100%(76/76), done.
remote: Compressing objects:100%(60/60), done.
remote: Total 76(delta 17), reused 46(delta 11), pack-reused 0
Receiving objects:100%(76/76),1.58 MiB |111.00 KiB/s, done.
Resolving deltas:100%(17/17), done.
通过git下载然后使用go命令进行编译
go build
如果觉得麻烦可以找到作者给出的release版本进行下载
这里我下载的是linux版本到kali,然后解压缩
unzip ehole
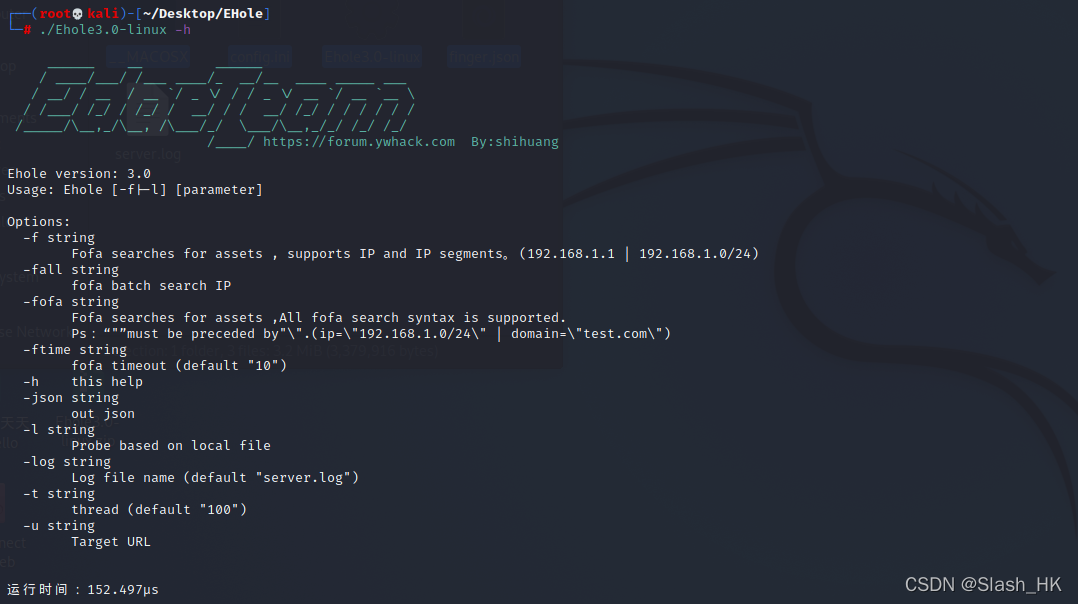
这里给出常用的几种扫描探测方法
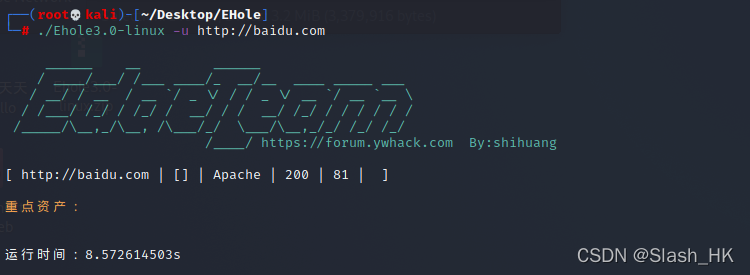
1../ehole -l url.txt //url地址需要带上协议,每行一个,用于批量扫描
2../ehole -f 192.168.80.1/24//支持单ip扫描或者ip段扫描,支持fofa接口,但是需要配置fofa邮箱和密钥
3../ehole -l url.txt -json test.json //结果输出到json文件中
网站指纹探测方法和工具其实相对来说比较多,但配合自己的使用习惯,多积累几款趁手的工具也不失为一种可取的方式。能够极大的提高自己的前期信息收集能力。
版权归原作者 Slash_HK 所有, 如有侵权,请联系我们删除。